

DDoS Attack
What is a DDoS Attack & How do you protect yourself from it?
In this article, we explain how DDoS attacks work, their financial impact on businesses, and why mobile bot networks have made them even more dangerous. We also explore effective defence strategies to help organisations protect their infrastructure and avoid costly downtime.
What is a Denial-of-Service (DoS) Attack?
A denial-of-service (DoS) attack, also referred to as a mail bomb, uses a mass-mailing technique to overwhelm an email address in an effort to shut down a network. The DoS attack is carried out using botnets to flood a recipients’ inbox with millions of spam emails and block service for all users. While DoS attacks don’t typically result in compromised data, they’re fairly simple to carry out and can result in major headaches for companies on the receiving end of such attacks. Organizations can minimize their risk of a DoS attack by having highly sophisticated network infrastructure security.
The abbreviation DDoS stands for Distributed Denial of Service. A DDoS attack is a type of DoS attack in which several hijacked systems are used to carry out an attack against the target system. This differs from conventional DoS attacks, in which the attack is only carried out from a single system.
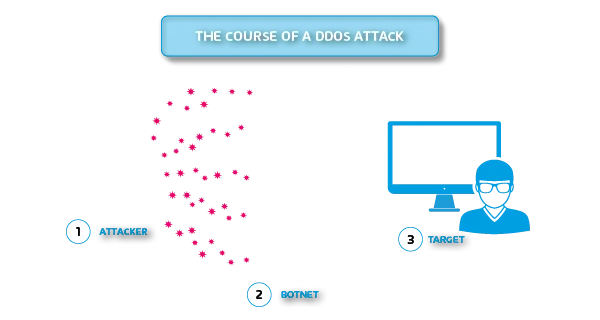
The number of excessive requests makes it difficult to identify or block every single attacker using an IP address. Due to high computing capacities, cybercriminals can carry out server requests in a much shorter time. This is ensured by the infiltrated bot network, which coordinates the attacks. The computer systems illegally brought under the control of the attacker receive appropriate commands via this route. Here the attacker uses a Trojan. This is used to control the bot network. A company’s mail server, for example, could be the target for a DDoS attack.
DDoS Attacks are on the Rise
According to the current status, the threat situation in the area of cybercrime shows an increasing tendency. Due to this fact, mechanisms that can detect and fend off a DDoS attack are of particular relevance in the field of IT security services. Appropriate security concepts must ensure that a DDoS attack is reliably detected and repelled. Possible weaknesses in companies often result from the fact that measures to combat DDoS attacks are not scalable.
With mail servers, for example, there is the possibility of implementing the Hornetsecurity email spam filter service for companies. This reliably recognizes the common forms of DDoS attacks. But how does the introduction of appropriate security mechanisms in the company work in general? Basically, it is important to first analyze the infrastructure in the company network. In the next step, a concrete action plan should be drawn up with regard to any server inquiries.
The introduction of a backup service is particularly important with regard to data security, whereby the question of the form in which a backup should be made remains to be clarified. This means, for example, whether a corresponding backup should be kept locally or whether an external cloud storage solution should be used by companies that specialize in data security. The effects that can result from a possible DDoS attack are very difficult to assess.
Professional cybercriminals are becoming more and more sophisticated in their endeavors. This applies in particular to the blocking of bandwidth and, at the same time, to the intensity of the DDoS attacks. Both together represent a security problem that should not be underestimated. The so-called Gbps attacks (gigabits per second) in the area of cybercriminality are increasingly becoming the focus of events. These are large-scale attacks that are characterized by even larger floods of data.
Mobile Bot Networks
Bot networks are now also appearing in a different form. For example, mobile devices infected with malware are repurposed as actors in a DDoS attack. Cyber criminals often have an easy time of it in this area. The problem can be traced back to the fact that mobility is increasingly finding its way into the corporate sector. This opens up further options for attackers to carry out their attacks.
The Financial Damage to Businesses
On closer inspection, this leads to additional financial expenditure. Here companies will inevitably have to adjust to higher costs in the coming years.
Of course, this primarily applies to the implementation of appropriate defense mechanisms. However, these are necessary preventive measures.
Ultimately, companies have the choice of arming themselves against cyber attacks in good time and investing in an appropriate security structure or dealing with the follow-up costs of a cyber attack.
Possible failures caused by a DDoS attack can lead to escalating costs for an affected company. These can arise, for example, through recourse claims from customers.
In addition, of course, the costs for legal disputes must also be listed, which are also difficult to estimate. The same applies to the loss of reputation that is regularly associated with such an attack.
How to Prevent Denial-of-Service Attacks
Time is of the essence in cybersecurity, but it’s in short supply for MSPs. If you’re spending all your time managing tools and investigating threats—both real and imagined—your margins are thinning.
The time you and your staff spend on cybersecurity tools is a good indicator of whether a tool is serving you or whether it is the other way around. For MSPs to be successful with managed security services, they need cybersecurity tools that are designed for MSPs. Such denial-of-service attacks require advanced technologies to provide the best protection.
DDoS Protection – How do companies protect themselves from DDoS Attacks?
Companies face a challenge. This particularly applies to those who have already been affected by a DDoS attack in the past. It is important to find a suitable IT security concept and implement appropriate countermeasures. What you have to pay attention to when making your choice is explained below.
1. Firewalls
It is recommended to use appropriate defense mechanisms. IPS and firewalls offer a certain level of protection, but these security measures are inadequate with regard to a DDoS attack, as this form of cybercrime is characterized by a certain degree of sophistication and can take place flexibly.
The security solutions already implemented in a company are often overridden by broadband attacks, which at the same time can block the entire network infrastructure. As a result, mail servers or websites are no longer available. A “worst case” to be taken seriously for every company.
For this reason, it should be in the interests of the company’s internal security officers to interpose a DDoS defense solution as a preliminary stage.
2. Protection Against Web Based Applications
A large number of processes in companies are based on web applications. They are now part of the standard repertoire of every company. This applies in particular to the processing of inquiries in customer support, the acceptance of new orders and the provision of interfaces for partners on websites. The constant maintenance of these network infrastructures is to be regarded as elementary here. After all, users expect a certain level of availability and security.
Even professional cyber criminals have recognized that core processes in companies are increasingly based on web applications. Attacks on applications are rarely found in practice, as this type of DDoS attacks is associated with a high level of technical effort; nevertheless, these are risks that are difficult to calculate. Appropriate protection is also often difficult. Such a successful DDoS attack can significantly restrict processes on servers, especially data transmission.
3. A Multi Level Security Strategy
In the case of smaller DDoS attacks, defense against attacks does not represent a major challenge. The situation is different if Denial of Services attacks are characterized by a large extent with unforeseeable effects. Here the existing firewall concepts in the company can quickly reach their limits. This applies to both the hardware and the software level.
Multiple-layer solutions are particularly suitable for such forms of attack. In principle, they serve to defend against scalable DDoS attacks.
4. Functionality of the Security Solution
The effective protection against DDoS attacks should start on several levels. This is the only way you as a company can reliably protect yourself from such attacks. Of course, this also applies to the core of the infrastructure of your own company network: Authentication, package, application and verification management are particularly common here. The control of the access levels through the specific definition of guidelines must also be taken into account.
5. Multilayered DDoS Defense
With regard to the implementation of sustainable DDoS attack protection, a differentiated approach is always advisable. Not only at the application level, but also in general terms, the preferred defense solution should recognize individually designed attack patterns and reliably counteract them. The calibration of such a system turns out to be a task that should not be underestimated in practice.
What is meant here is to make a specific distinction between legitimate inquiries and whether these are unauthorized. The latter are characterized by a not exactly low data volume and should be recognized and blocked in good time. This includes the mechanisms of IP filtering.
Protect your business with Hornetsecurity
As shown, risk management plays a significant role in DDoS defense. Timely action is advisable here. This is especially true when it comes to the security of internal company data. The network security of companies must fundamentally be understood as a dynamic process. A static, once implemented solution should be constantly questioned and adapted. Attack and behavior patterns from the area of cyber crime must be constantly monitored in order to be able to react to threats.
Hackers are able to tailor their DDoS attacks to the existing security barriers in a company. This is possible not least because of the scalability of the DDoS attacks. The target system can consequently be compromised by the cybercriminals. The introduction of appropriate countermeasures in advance is of great importance. This procedure ultimately serves to protect the company.
Hornetsecurity offers a sustainable security concept for the mail server sector, which effectively counteracts DDoS attacks and reliably deals with current threats and dangers.
Learn about HORNETSECURITY’S SERVICES
Interested in Related Topics?
Did you like our contribution to DDoS attacks? Then other articles in our knowledge base might interest you as well! We help you learn more about cybersecurity related topics such as Emotet, Trojans, IT Security, Cryptolocker Ransomware, Phishing, GoBD, Cyber Kill Chain and Computer Worms.



