Monthly Threat Report July 2024: Snowflake(s) in July
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of June 2024.
Executive Summary
- The Hornetsecurity Monthly Threat Report format is changing. See section below executive summary for more details.
- The amount of low-effort / high-volume email attacks increased for the month of June while other more targeted attacks decreased.
- Malicious HTML files were the top-used file type for the deliver of malicious payloads throughout the month. This was partially driven by a new “Pastejacking” campaign we observed sometime in June.
- The mining, entertainment, and manufacturing industries were the most targeted industries throughout the last month.
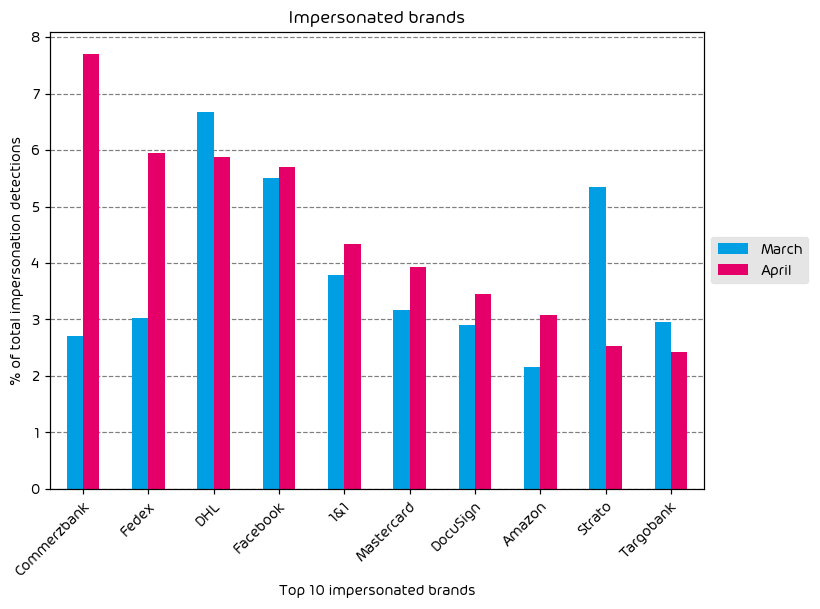
- Brand impersonations for the month are down with the most impersonated brands for the month being FedEx, Facebook, and DHL.
- The Cryptocurrency Wallet service MetaMask had a small campaign specifically targetting MetaMask users with brand impersonation attempts.
- Customers of Cloud Data Storage provider Snowflake have actively been targeted by threat actors in a campaign that has breached an estimated 165 organizations. It appears that Snowflake itself has not been breached in these cases.
- Change healthcare has finally announced news of what type of information was leaked as part of a significant ransomware attack earlier this year. The amount of leaked data is significant.
- Kaspersky has been banned by US federal authorities from conducting business in the country. After July 20th 2024, the sale of Kaspersky software in the US is not allowed
- The FBI has come into posession of a number of Lockbit decrypt keys. If your organization has been impacted by Lockbit and you’ve yet to gain access to your data, please see the below section on this topic.
An Update on This Report’s Format
If you’ve been a regular reader of this Monthly Threat Report you know that we commonly cover the changes in the email threat landscape. What we’ve identified over the last year of reporting on these statistics is that trends in email threats shift very subtlety unless there is a new emerging trend, vulnerability, attack-type, or threat-actor. With this in mind, we’ve decided to make a change to the way this report is formatted in the coming months as follows:
Statistical data points (email threat types, brand impersonations, threat file types, industry threat index) will be covered on a quarterly basis moving forward. Said statistical data will encompass the entire 3 months of a given fiscal quarter (Ex. Jan-Mar data will be presented in April). This means that statistical reports will be published in the months of:
- April (Q1 – January to March)
- July (Q2 – April to June)
- October (Q3 – July to September)
- January (Q4 – October to December)
NOTE: We also conduct an annual Hornetsecurity Cyber Security Report that does statistical analysis with annual data as opposed to Monthly/Quarterly.
With that all said, this month’s monthly threat report happens to fall on our Q2 data report date and will be the last report to feature the monthly statistical comparison that we’ve done to date. Moving forward reports that do not fall on one of the quarterly months listed above will instead feature:
- Industry news commentary
- Threat analysis
- Industry predictions
- Recommended actions with regards to security events or incidents
- Emerging security technology guidance
We feel that this new format will bring readers the most value in this publication month-to-month.
Threat Overview
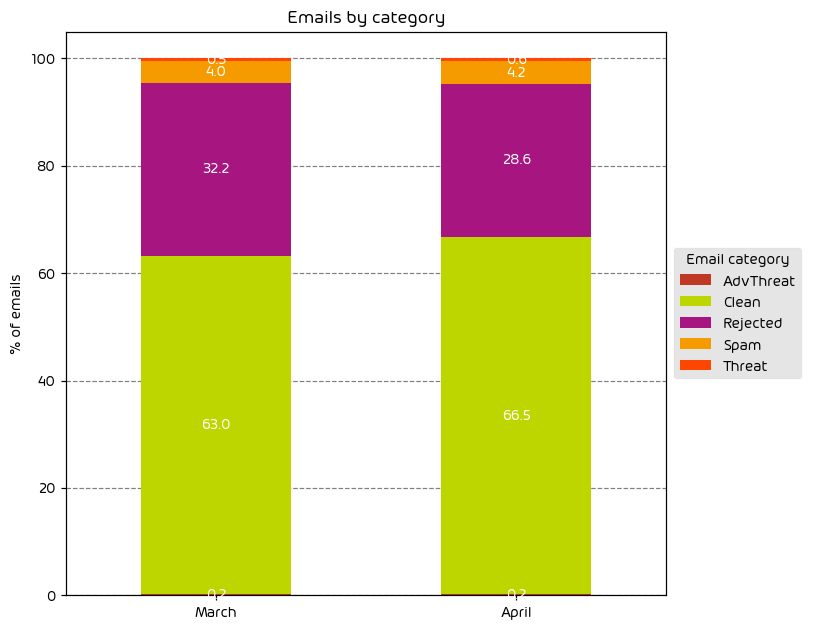
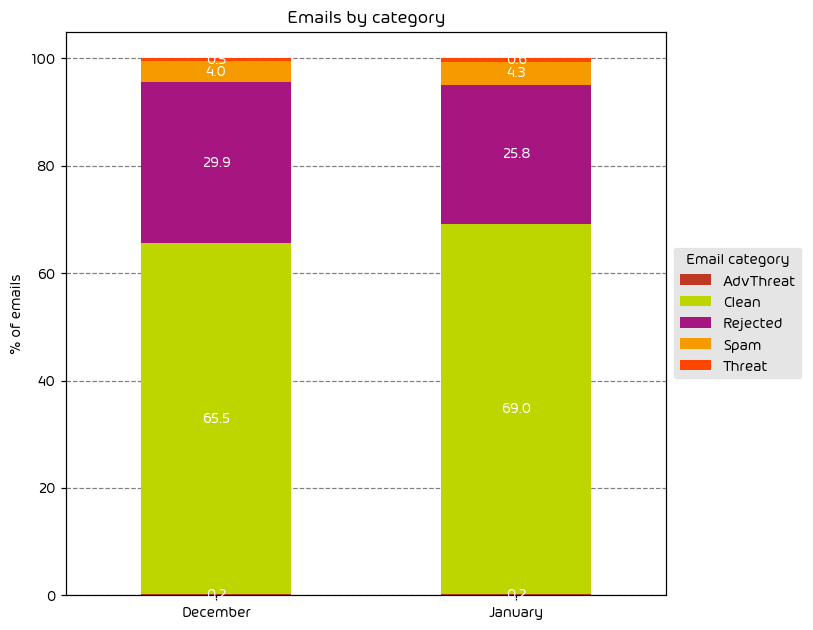
Unwanted Emails By Category
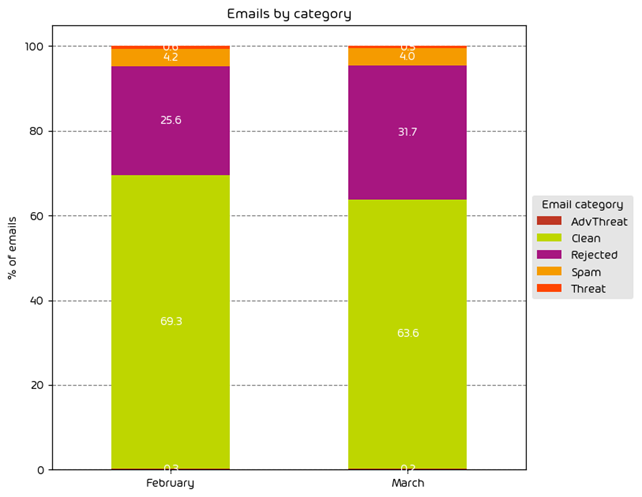
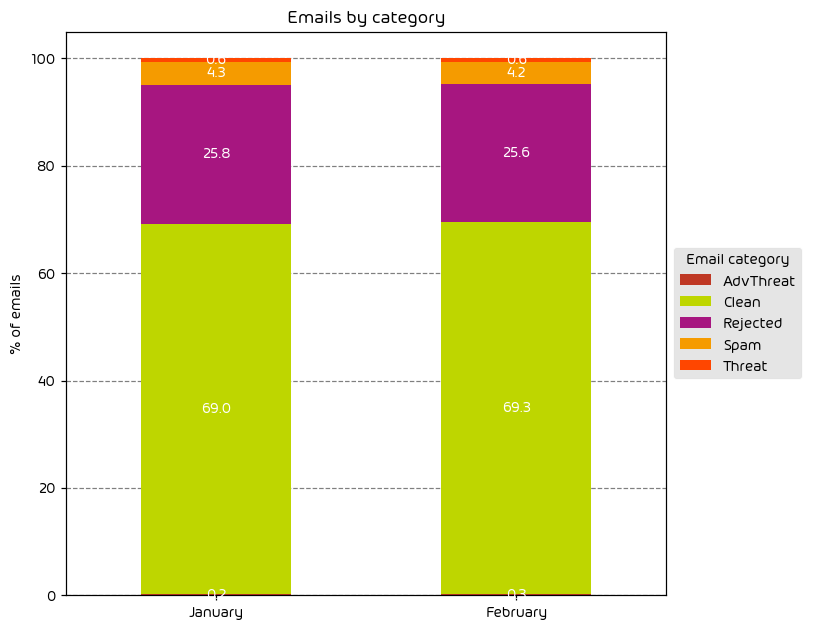
The following table shows the distribution of unwanted emails per category for June 2024 compared to May 2024.

During the June data period we observed a noted increase in the amount of low-effort email attacks as indicated by the 4.5 percentage point increase in “Rejected” emails. Other email threat types were down for the month. One possible reason for this is we’re now entering the summer months. Threat-actors know that there are fewer people in the office, and they themselves are likely looking to take some time away from “the office”. As such, an easy way to make up the difference in targeted attacks is to increase the overall volume of malicious email on the web.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
|---|---|
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered |
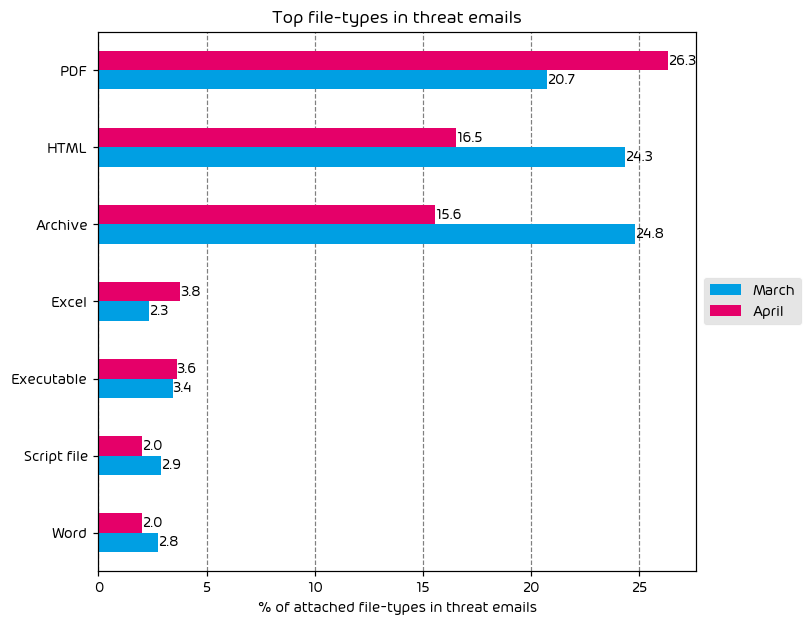
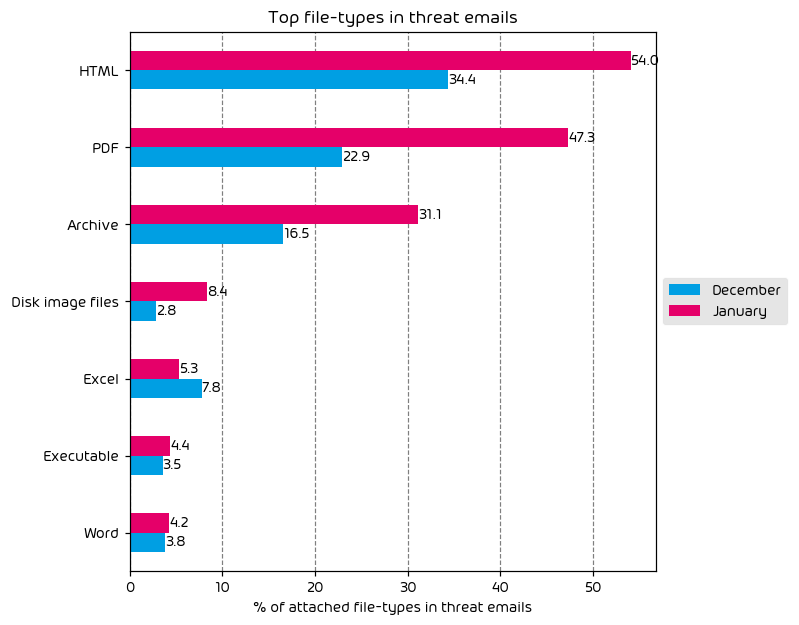
File Types Used in Email Attacks

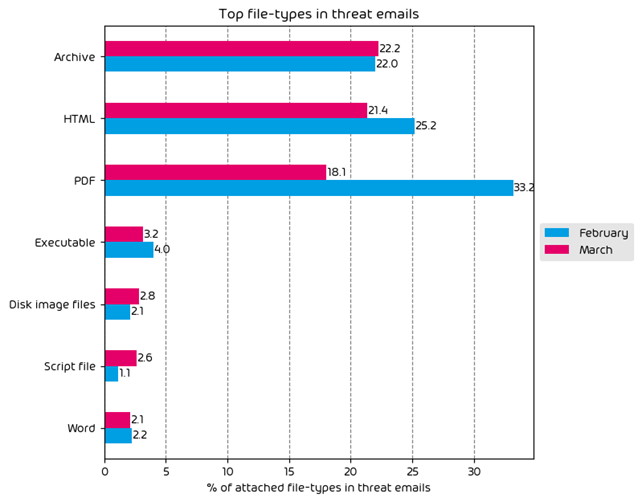
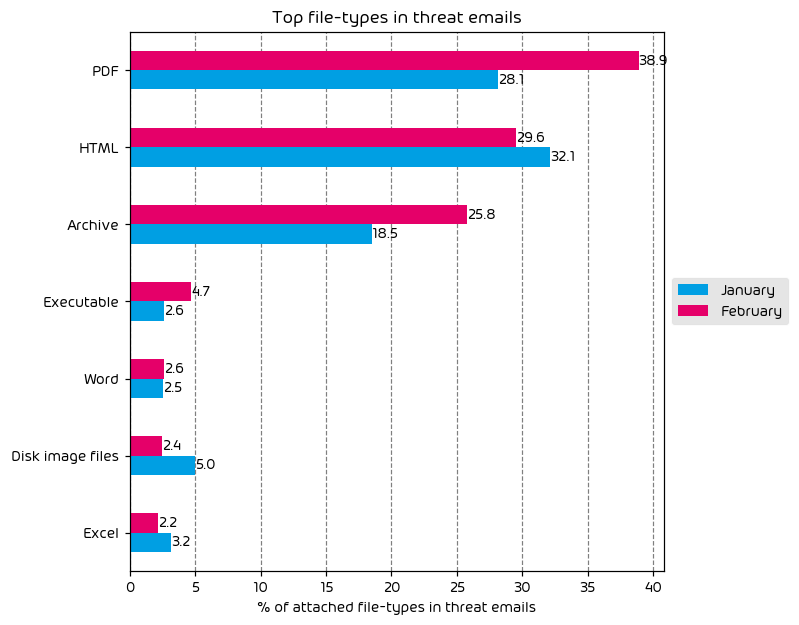
June saw an increase in the amount malicious HTML files being used in email attacks. HTML files, remaining at the top of the list have most recently been used in a new attack campaign utilizing “Pastejacking” which we reported on some weeks ago. In this attack a malicious HTML file is included in email and instructs the user that the “fix” for a perceived issue has been placed in their clipboard. The target is then instructed to open PowerShell (or similar) and paste the contents, ultimately leading to infection.
Most other threat filetypes saw a decrease when compared to previous months, with the exception of script files which saw a 1.8 percentage point increase.
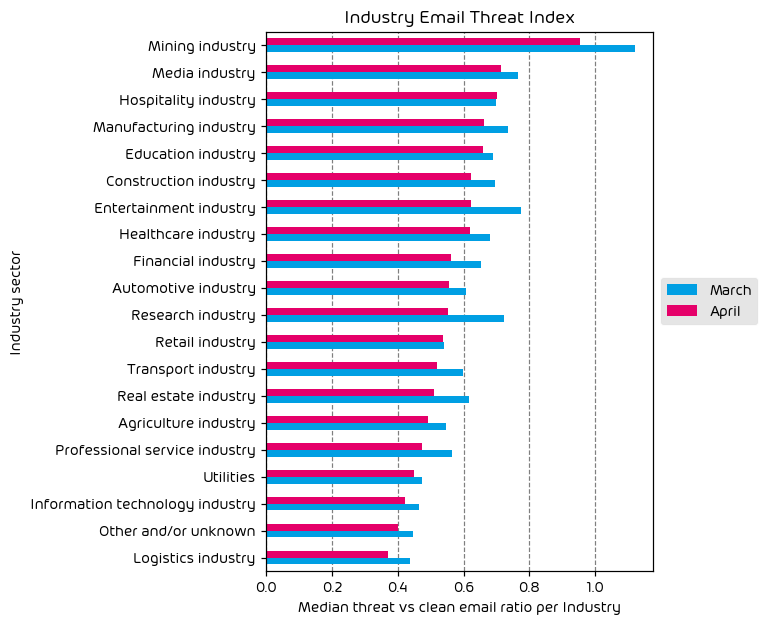
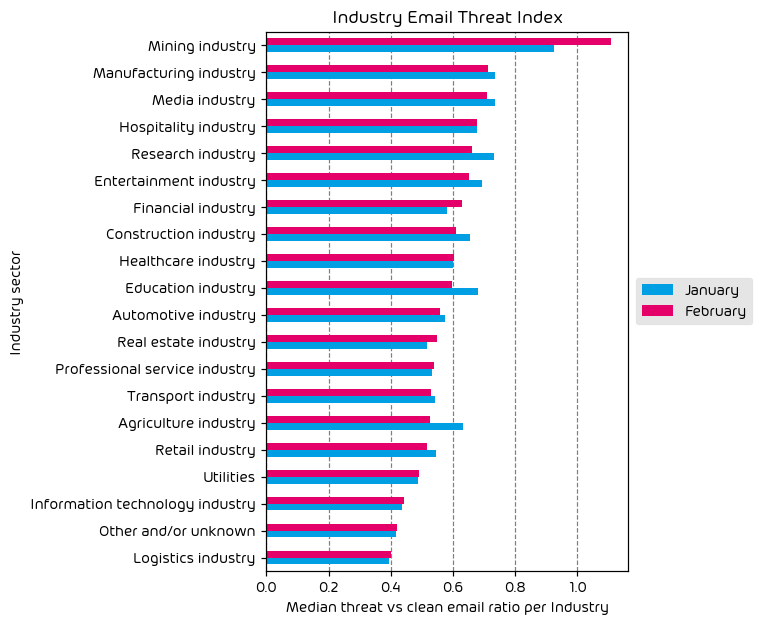
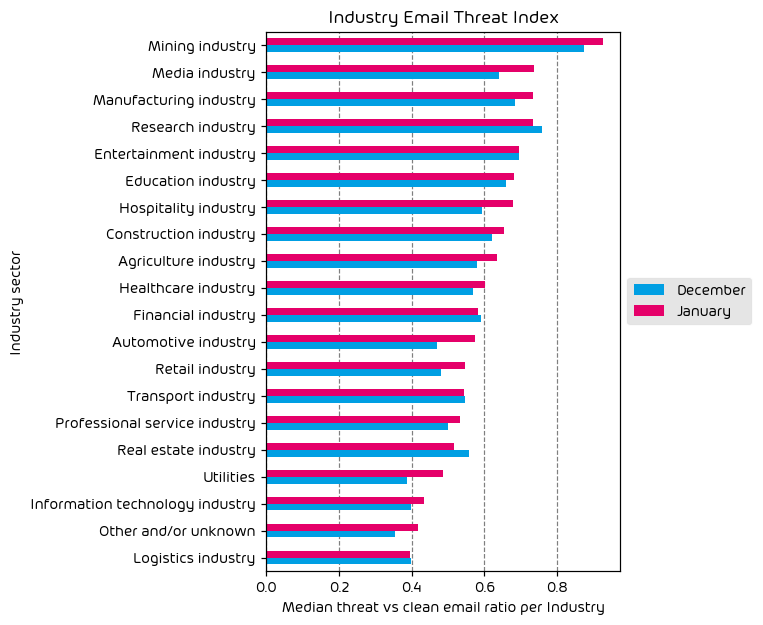
Industry Email Threat Index
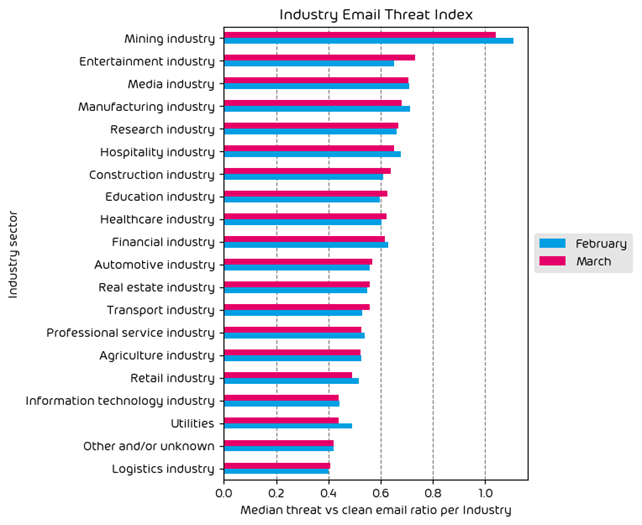
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.

Most targeted industries for the month included Mining, Entertainment, and Manufacturing. Nearly every industry vertical saw a decrease in attacks over this last month, with the exception of entertainment. It’s not difficult to see why. The entertainment space, which often includes online gambling, is ripe for scams and malicious actors. It’s an industry that we see often near the top of the list, and with the summer vacation months upon us, it’s a busy season for those organizations in the entertainment space.
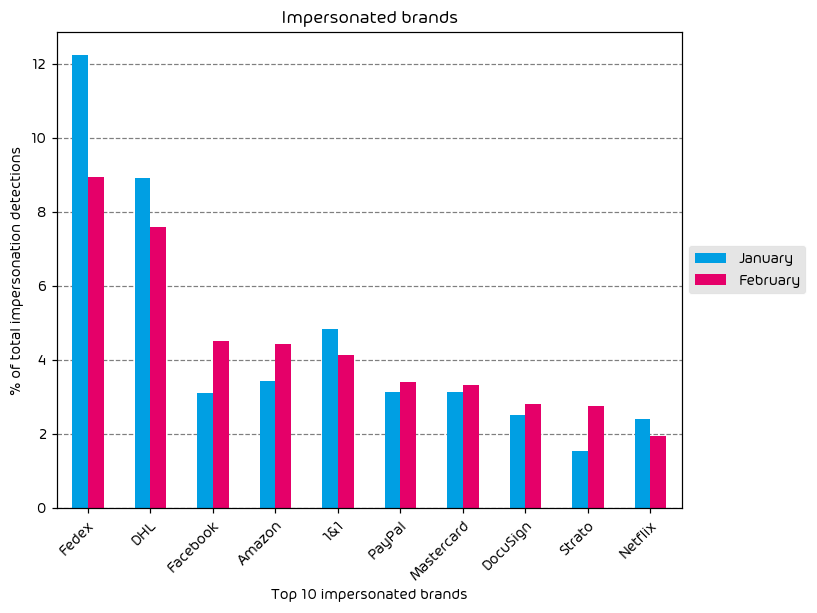
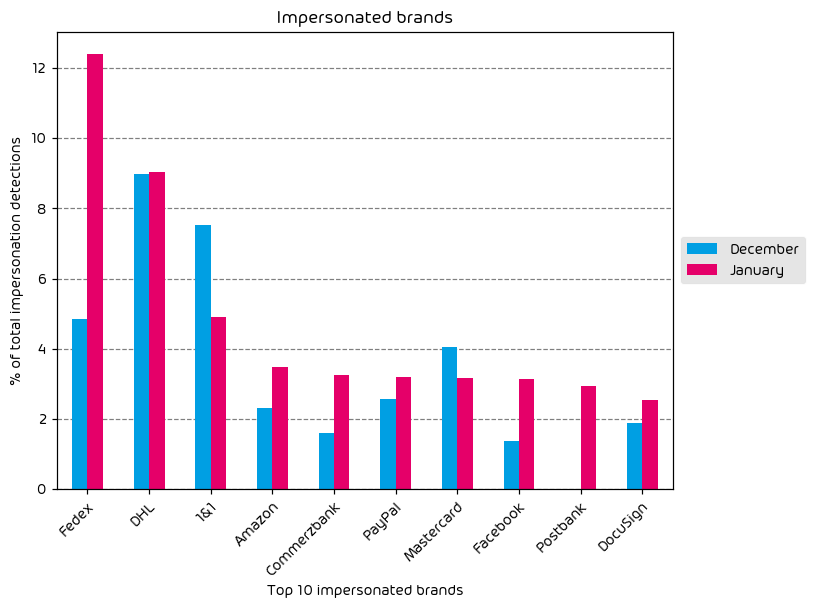
Impersonated Company Brands and Organizations

Brand impersonation attempts are down for the month of June. Nearly every brand in our top ten saw a decrease in impersonation activity with the exception of a small campaign that specifically targetted MetaMask users. MetaMask is a popular cryptocurrency wallet app. Threat actors will commonly impersonate these types of services in an attempt to gain access to the target’s wallet, and the cash contained therein.
Major Incidents and Industry Events
Data Breaches Impacting Snowflake Customers
Perhaps the largest news for the month of June was word of the multitude of attacks on Snowflake instances across the globe. Snowflake is an organization that offers data warehousing services along with data analysis and other cloud storage capabilities. Snowflake has many large customers that leverage its software, many of whom have been targeted in recent attacks – at least 165 to date (as of this writing).
With so many organizations affected, the logical conclusion is the question of whether the common vendor (Snowflake in this case) had been subject to a breach themselves. However, after an extensive investigation by Snowflake that included Mandiant, no vulnerability exists today in Snowflake systems. Instead, it appears that nearly every impacted organization was breached via stolen passwords which were then used to login to Snowflake Services. It’s also important to point out that according to Snowflake and Mandiant, the impacted Snowflake instances exhibited the following issues:
- Snowflake Instances did not have multi-factor authentication configured
- Credentials had not been rotated or updated
- Network allow lists had not been defined to only allow traffic from trusted sources
In each case, threat-actors were able to exfiltrate sensitive data and the list of impacted businesses is growing. Some of the known impacted organizations include:
- Santander
- Ticketmaster
- Advanced Auto Parts
- Neiman Marcus Group
- Pure Storage
- LendingTree
- Los Angeles Unified
Mandiant has released a Snowflake threat hunting guide for those that believe they’ve been impacted.
Update on Change Healthcare
As we’ve discussed in this report in previous months, Change Healthcare suffered a crippling ransomware attack earlier this year that impacted healthcare operations across the US. This prevented patients from receiving care in some cases, and even impacted medication refills, keeping people from critically needed medicine in some cases.
The human and health cost aside, what was not well known at the time, was the impact of data breach. That news came out in a recent announcement from the company. Impacted information potentially includes:
- Names
- Addresses
- Dates of Birth
- Phone Numbers
- Email addresses
- Social Security Numbers
- Drivers License Numbers
- Official Diagnoses
- Medications
- Test Results
- Imaging
- Treatment Plans
- Insurance Info
- Banking Info
The type of data involved is bad enough, but when you realize that Change Healthcare held the personal info on at least 1/3rd of US citizens, the scope of the breach becomes apparent VERY quickly.
Affected individuals will begin receiving notification of impact via mail in the coming weeks, according to the company.
Kaspersky Banned in the United States
Starting on July 20th 2024, Kaspersky Software is banned from conducting sales of its software within the United States. On top of that, Kaspersky is only allowed to provide updates to existing customers until September 29th 2024. This news is significant as it marks potentially the second time that a technology provider has been barred from doing business in the US. The other instance that comes to mind is the banning of Huawei back in 2022.
The FBI has Obtained Lockbit Decrypt Keys
A quick mention here – back in February the FBI, and international law enforcement agencies were successful in deeply crippling the Lockbit Ransomware operation. As part of that operation the FBI has gained access to a significant number of Lockbit decryption keys (7,000 approximately). If your organization has been impacted and you’re still working on getting access to your data. Please see the links listed above.
Predictions for the Coming Months
- Sophisticated and targeted email attacks are likely to stay lower throughout the summer. During the summer months we typically see an increase in low effort and easily spotted email-based threats.
- We’ll continue to see organizations (and individuals) impacted by the results of the ongoing attacks targeting Snowflake customers
- Threat actors seem to be having some success with the pastejacking technique we linked in the report above. As such, it’s probable that we’ll continue to see the method used in attacks in the near term.
Monthly Recommendations
- If you use Snowflake within your environment. Please take note of the guidance provided by Mandiant and make sure that you have MFA enabled within your environment.
- During the upcoming summer months, make sure your team members clearly communicate any absences clearly. Threat actors will often try to initiate attacks when they know certain individuals are outside of their normal routine and will try to capitalize on vacations as such.
- Educate your end users on the concept of PasteJacking. They should know to NOT blindly follow instructions from an online source, even if it looks legit.
- If you use Kaspersky software products within your organization and you’re based in the United States – make a plan now to migrate to another provider for those services.
- If you’re organization has been impacted by Lockbit and you’ve yet to gain access to your data, see the section above about how the FBI is now in possession of 7000 Lockbit Decryption keys.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.