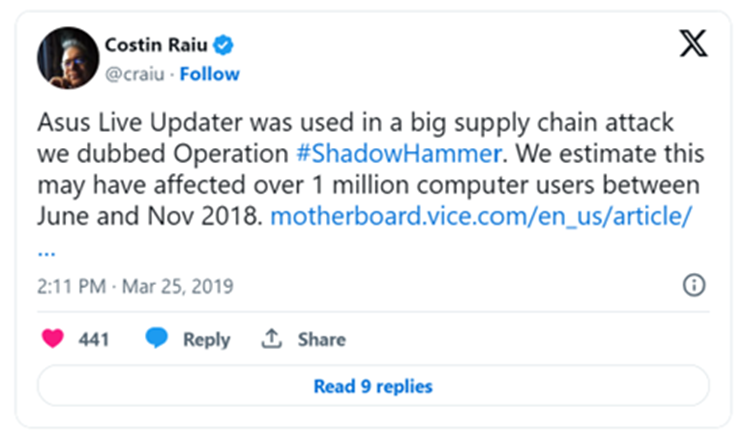
That report also focuses on cyber influence operations – misinformation and disinformation. You’ll find two approaches here, one disseminating false or misleading information, and the other simply flooding the information space with different stories, leading to an inability to even spot the true signal in the noise.
Another interesting cyber security statistics in the DDR looked at characteristics of organizations that suffered a ransomware attack. 68% of those business didn’t have an effective vulnerability and patch management process, 60% didn’t use Endpoint Detection and Response (EDR), 60% didn’t have a SIEM, 76% lacked an effective response plan, 44% didn’t have immutable backups, and 92% didn’t have an effective DLP solution.
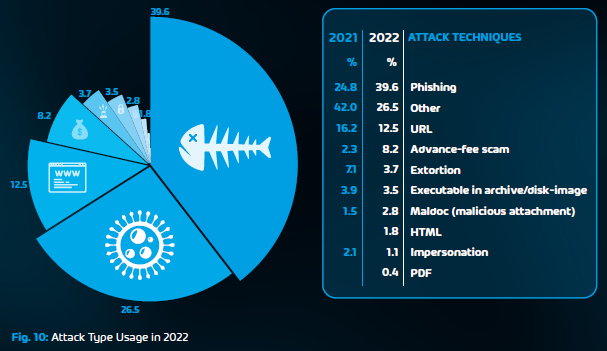
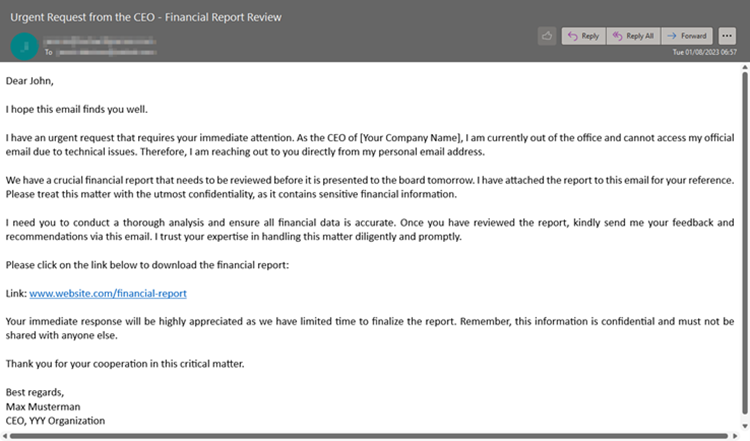
In our own 2022 survey we found that 1 in 20 companies had a ransomware attack, wherein 14.1% lost data, and 6.6% had to pay the ransom. The vector for initial breach was overwhelmingly email / phishing at 58.6%, followed by compromised endpoints at 16.4%. It’s crucial to combine a strong email security hygiene solution to keep most malicious emails out of users’ inboxes, with regular user training to not fall for the few that do end up in their inboxes.
An interesting find is that 86% of ransomware cases involve the threat of leaking the exfiltrated data. Often called double extortion, this combines encrypting the data in the first place, making it inaccessible to your business (unless you pay to get the decryption key), plus threatening to make the stolen data public.
There are even cases where attackers skip the encryption phase, and simply threaten to leak the data. How efficient this is a threat will vary between industries, the company that was breached and the nature of the data itself. Some businesses aren’t likely to pay, whereas others not only can’t afford to have the data leak, but they may also face legal and regulatory consequences if the data is made public.
Another interesting change we’ve seen recently is the shift from “brand name” ransomware actors, to smaller groups (it’s mostly the same people, with shifting loyalties) because those known names often end up on sanctions lists, particularly if they’re in Russia, disincentivizing businesses from paying in the first place.
The takeaway here is to apply a zero-trust approach to securing your business, verifying each connection and authentication. Also, applying policies to only allow connections from managed devices is a good idea, or at least enforce stricter policies for personal devices.