The Future of Ransomware
Ransomware has evolved from attacks on users to attacks on organizations. In the past, if your data was encrypted by ransomware, you could restore it from your backup. Today, this is no longer the case, as ransomware can also compromise our backups.
Today’s ransomware is sophisticated, it has building blocks and can change its behavior and attacks depending on the customer environment.
In this blog article, I will give you an overview of ransomware, the future of ransomware, and what impact it has on companies.
What is Ransomware?
Ransomware is a type of malware that encrypts data, virtual machines associated files, databases, and others. When it infiltrates the system, it encrypts the data and creates a .txt ransom note with instructions for the victim on how to make a payment and obtain the description key.
It is usually spread via phishing mails (look for QR code scams), social engineering, and other attack methods. Ransomware can attack various targets and their data, including Windows, Linux, MAC, VMWare, Hyper-V, Citrix, databases, and others.

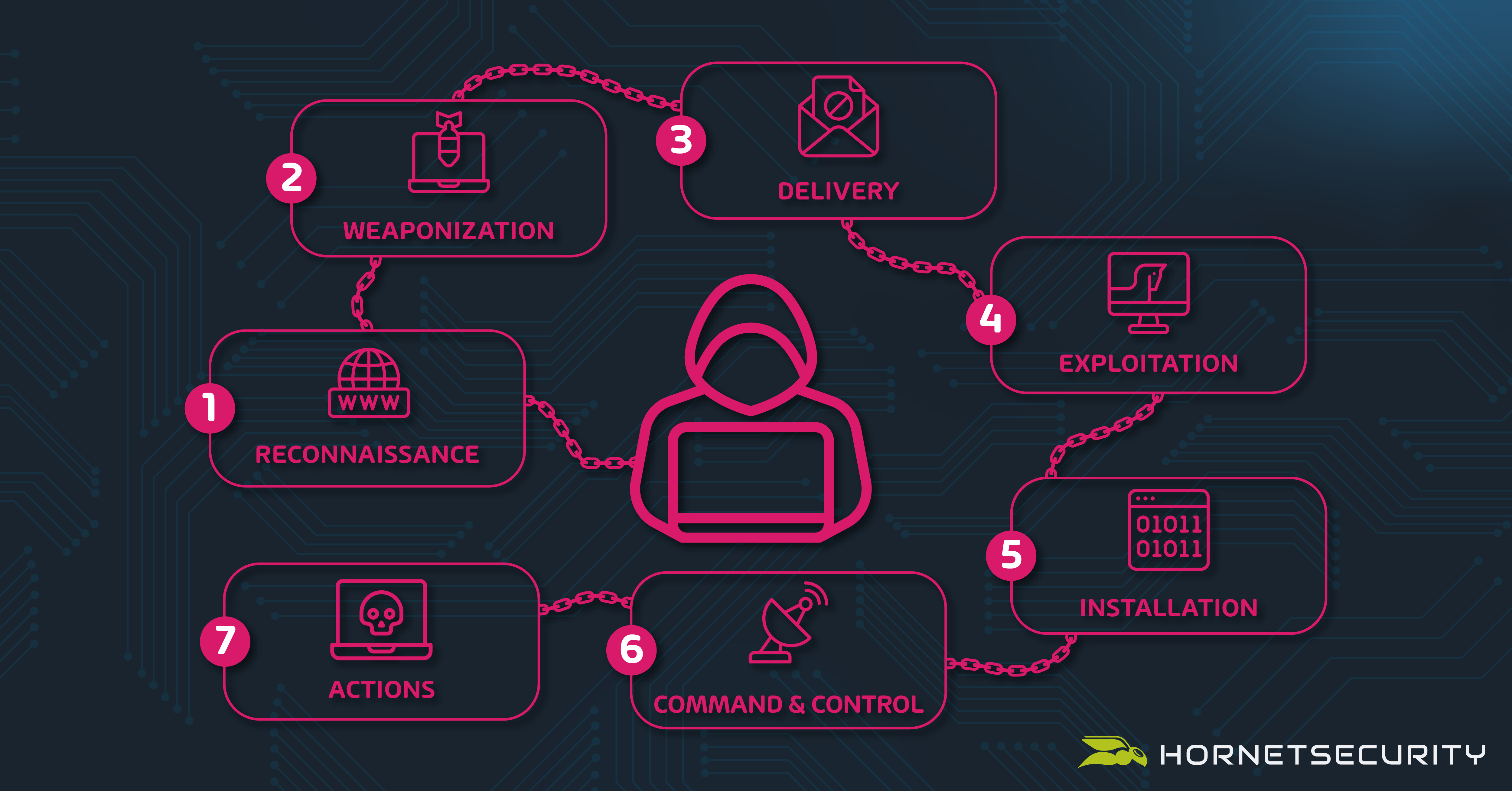
This is how ransomware works
It causes a lot of problems for SMBs, SMEs, governments, healthcare, and all other industries. If there is no operational business data, there is no business.
According to a Ransomware attacks survey, 14.1% of ransomware victims lost data, and 6.6% had to pay the ransom.

14.1% of ransomware victims lost data, 6.6% had to pay the ransom
If the victim does not pay, the ransomware group threatens to release the files piece by piece or to sell them to interested parties. In this way, they force the victim to pay.
Exploring the Evolution of Ransomware
Ransomware attacks are not a new development in the cyber world. OK, we may hear them more often because they have been very popular over the last decade.
The first version of ransomware dates back to 1989, when Joseph Popp, the author of the AIDS Trojan, distributed floppy disks in over 90 countries on behalf of the PC Cyborg Corporation.

Anyone who inserted the diskette into their PC was infected with malware.
The malware encrypted their files and demanded payment of $ 567 for the decryption key. Joseph Popp is known as the father of ransomware.
From 2005 to 2010, fake antivirus ransomware was very popular. This fake antivirus program detected a fake threat in the system and asked users to pay for the antivirus license to delete the threat. Payment was made by credit card and ranged from $ 20 to $ 100.
From 2010 to today, we have seen different types of ransomware attacks targeting different systems and industries. It’s not just about a single operating system, but anything that becomes a technological trend (hypervisors, hyper-converged infrastructure, cloud, IoT, IIoT, OT, etc.); quickly becomes a target for ransomware gangs.
In the recent ransomware attack on IxMetro PowerHost, a hosting provider from the US, the ransomware gang encrypted their VMware ESXi and virtual machines and demanded a payment of two bitcoins per affected customer, totaling about $ 140 million.
When IxMetro PowerHost realized that their data could no longer be used, they wanted to restore healthy copies from the backups.
However, that didn’t work well. Their backup was also encrypted.
This is the evolution of ransomware. It started very small and grew significantly, both in terms of damage caused and ransom demands ($ 567 in 1989, and $ 140 million in 2024).
Emerging Trends Shaping the Future of Ransomware
Technology is constantly changing. Ransomware would not be successful if it did not follow technological trends. According to various reports, the number of ransomware attacks doubled in 2022 compared to the previous year and increased by 130% in 2024.
So, ransomware is here to stay.
In this section, we will talk about trends that might determine the future of ransomware.
Tailored ransomware attacks
In the past, ransomware mainly targeted Windows due to its large market share. Today, with the growing market share of Linux, we can observe an increase in ransomware attacks against Linux as well. For instance, the first version of Monti ransomware only targeted Windows, while the newer version also can attack Linux distributions.
In the future, ransomware will be more tailored to different targets and industries. For example, we can see an increase in ransomware attacks on hospitals and pharmacies, transportation industries, financial institutions, education, and other industries.

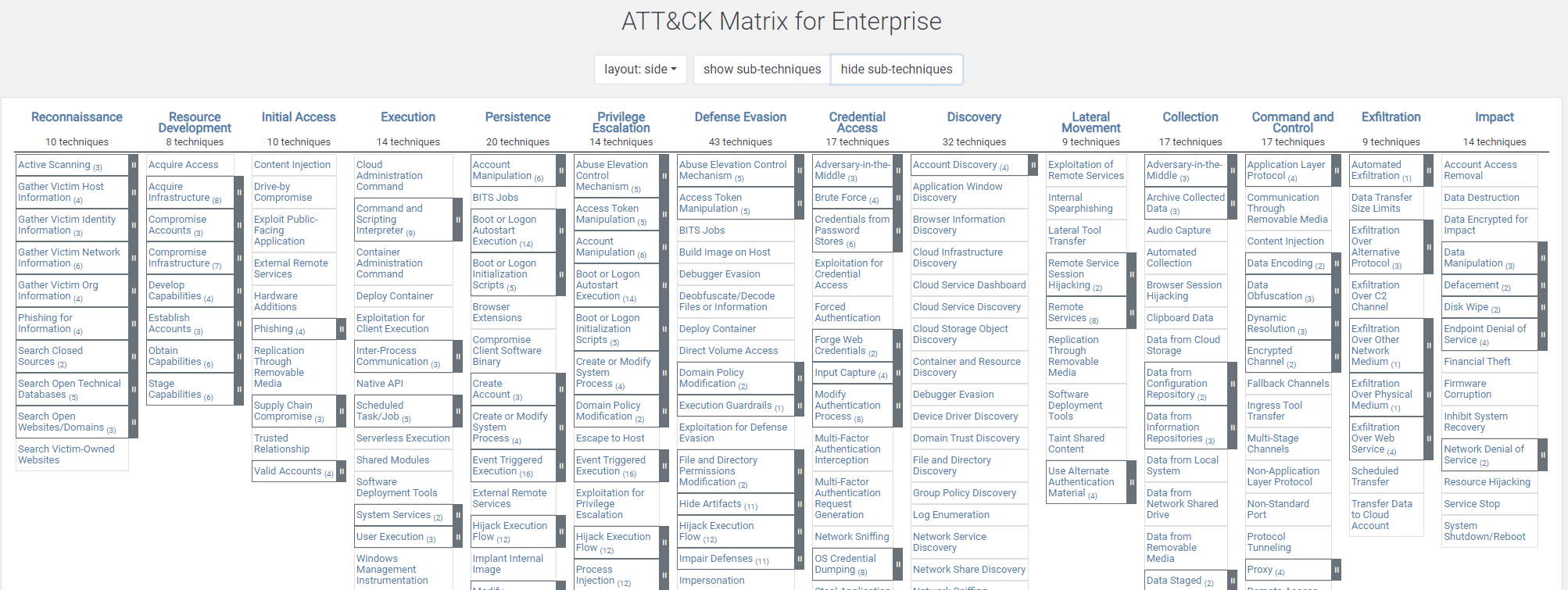
Industries targeted by ransomware
Additionally, we can see more ransomware attacks in this direction targeting PLCs (Programmable Logic Controllers) in OT networks. PLCs are often operated with Windows or Linux systems. A 10-minute downtime in production can lead to hundreds of thousands in financial losses.
Ransomware as a Service (RaaS)
Hacking used to require extensive knowledge and skills.
RaaS platforms now allow cybercriminals to launch ransomware attacks with minimal technical expertise. These platforms are developed by ransomware gangs to speed up and automate the execution of ransomware attacks. RaaS recruiters recruit people on the internet and ask them to join the ransomware group and participate in the attack.
These platforms have a user-friendly interface, detailed user manuals, forums, and 24-hour support. It is a real (malicious) business method.
Some well-known RaaS platforms are Hive, DarkSide, Revil, Dharma and others.
We will see an increase in the usage of RaaS platforms.
Ransomware in the supply chain
Have you heard about the Solarwinds hack, one of the biggest cybersecurity breaches of the 21st century? Solarwinds provides network monitoring and management tools for IT infrastructures.
Here is what happened.
An attacker injected malware into SolarWinds’ software development process, specifically the Orion software updates. As soon as customers downloaded the update, they also downloaded and installed the malware on their systems.
Antivirus and security tools could not detect it. Attackers gained access to a network of over 30 thousand public and private customers. They had access to their data.
This was one of the biggest supply chain attacks in modern times.
Many products are dependent on third-party services which open a product across different layers. In the future, we will see more and more ransomware attacks delivered via supply chain.
Backup is under attack
When IxMetro PowerHost, a hosting provider from the US, realized their production machines and data were encrypted, they informed customers and started the restoration process.
However, very quickly, they realized backup copies were also encrypted.
Attacking backup copies is becoming a trend. If production and backup are encrypted, the victim has no choice but to pay the ransom, unless they have offsite backup copies and immutable technology in place.
Dark Web Auctions
Governments and security researchers recommend not paying a ransom. The idea behind this is to show ransomware gangs that their malicious activities are not profitable.
Nevertheless, ransomware groups have invested time and resources to hack the system and are looking for all possible ways to monetize their operations.
They have started exposing data on the dark web if the victim refuses to pay for the ransom. This provides them with additional income. We call it double extortion.
Whether the victim pays or not for the ransom, there is no guarantee that the data will not be sold to interested parties.
AI-Powered Ransomware
Today, Artificial intelligence (AI) is used everywhere. It is not strange that ransomware gangs would use it for malicious purposes. We can expect more AI-driven ransomware attacks on various targets and industries.
The National Cyber Security Center (NCSC) predicts that ransomware will benefit the most from AI in the next two years, alongside other cybersecurity attacks.
Ransomware attacks will be more effective and dangerous. AI-driven ransomware will help identify vulnerabilities in systems and adapt the behavior and each attack to the customer’s environment.
Sounds scary!
To respond to ransomware threats driven by AI, security vendors are developing AI-driven defense systems.
This is a game of offense and defense.
Preparing for the Future: Strategies Against Ransomware Attacks
If we look at the reports after the attack, we can see that the attack could have been prevented if stronger security measures had been taken.
Several strategies can help organizations prevent future ransomware attacks. The foundation of prevention is strong IT security measures.
First and foremost, it is important to keep all systems up to date. Systems that are not patched are the first point of attack.

Strategies against ransomware attacks
Regularly backing up critical data and workloads is extremely important. In the event of a failure, the data or the machine can be easily restored. Since ransomware can also attack backups, it is important to use immutable storage and immutable backup solutions. Immutable technology prevents ransomware from making changes (encrypting) to files.
Implement strong security measures from endpoints and networks to various servers. These measures include hosted and network firewalls, advanced threat detection, IDS (Intrusion Detection System), IPS (Intrusion Prevention System), incident response plans, encryption, and data security.
You should implement strong password policies and use multi-factor authentication.
All of this is important, but if you do not provide adequate security awareness training, you are at high risk. We strongly recommend that you continuously provide cybersecurity training to your employees and teach them how to prevent social engineering and phishing attacks.
We recently published Cyber Security Report 2024 with an in-depth analysis of analysis of the current cyber threat landscape based on real-world data.
What can trigger the change of the malicious business model?
Organizations and technology are prone to change. This happens due to market trends, government regulations, or simply a change in the business model.
To be effective in their malicious operations, ransomware gangs adapt their business model.
One of the questions is what can trigger a change in the cyber malicious business model.
Urgent call for cryptocurrency regulations
When ransomware infiltrates your network and systems, it attacks your data, encrypts it, and creates a .txt ransom note with instructions on how the victim can make the payment.
All payments are required in cryptocurrencies, mainly in Bitcoin.
Today, the spectrum of ransomware attacks is much broader, and ransomware groups are demanding more money.
And why? It offers them additional security and anonymity.
This is a challenge for governments and security vendors, as it prevents them from getting in and out of money transactions.
That means we need regulation for cryptocurrencies!
If governments were to introduce regulations for crypto-assets – and they are already looking into this – it would add regulation and control to the use of Bitcoin and other cryptocurrencies.
This would put ransomware groups in a tight spot as they would not be able to fund attacks with crypto assets.
When it comes to global crypto regulations, The International Organization of Securities Commissions has laid out its 18 recommendations for managing crypto assets.
In terms of regulations per country or region, the following countries have started the process: the European Union, Switzerland, the United Kingdom, Japan, India, the United Arab Emirates, South Africa, Singapore, the United States of America, and Canada.
Better law enforcement operations
Cybercriminals are prosecuted, but there is a lack of cross-jurisdictional takedowns of ransomware groups. In practical terms, this means that a ransomware group can operate from multiple countries, and prosecuting hackers from only one country would not be very effective.
What security researchers are calling for is better cross-jurisdictional cooperation between countries.
If legal action were taken against ransomware groups, these ransomware groups would probably have to leave the country and find another location.
To properly protect your cyber environment, use Hornetsecurity Security Awareness Service and Advanced Threat Protection to secure your critical data.
To keep up with the latest articles and practices, visit our Hornetsecurity blog now.
Conclusion
Ransomware is a type of malware that encrypts all kinds of data and asks the victim to pay a ransom to get their data back. If the victim does not want to pay, ransomware gangs expose the data piece by piece or sell it to interested parties on the dark web.
The father of ransomware, Joseph Popp, developed the first ransomware in 1989 and distributed it via a floppy disk. From 2005 to 2010, fake antivirus programs were very popular. Since then, ransomware has continued to emerge, targeting different infrastructures and industries.
Whenever a technology or market shifts to something else, ransomware gangs adapt their malicious business model and attack.
The future of ransomware will revolve around AI-driven attacks, more sophisticated ransomware attacks tailored to different targets and industries, more supply chain attacks, backup, double extortion, dark web auctions, and more.
To prevent this, we need to implement strong security measures from the endpoint to the servers and provide continuous cybersecurity training to employees.
Additionally, governments can help by improving cross-jurisdictional cooperation and preventing attacks through better laws. As cryptocurrencies are used to pay the ransom, regulation of crypto assets would also be beneficial.
This article looks at ransomware and some expectations for the future.
FAQ
Is ransomware going away?
Ransomware is one of the most popular and effective methods used by cybercriminals. According to different reports, ransomware is not going away; on the contrary, it is becoming increasingly sophisticated and dangerous.
What is the trend in ransomware?
Ransomware attacks are increasingly being tailored to different customer environments.
It no longer attacks a single operating system such as Windows but extends to all different operating systems, hypervisors, the cloud, telecommunications, healthcare, and other infrastructures and industries.
In addition, we can also see Ransomware as a Service (RaaS) becoming a trend. The usage of cryptocurrency is a norm since it provides anonymity.
Ransomware attacks are powered by AI which helps them to be more effective.
Is ransomware here to stay?
Considering that ransomware follows the technological trend, it is here to stay, becoming more sophisticated and dangerous for different infrastructures and industries.