

How to Secure and Protect Backup Data
Multiple high-profile breaches have made everyone painfully aware of the need for data security. The theft of unencrypted backup tapes from a few major organizations widened the scope to include backup. Unfortunately, information technology departments have not done much to improve protection of cold data.
Since attackers typically target active data and online systems, technology professionals and data security firms focus efforts there. For many years, businesses have avoided compromise of backup systems more by luck than by effort. In the age of ransomware, that luck will run out in dramatic fashion.
Risk Analysis for Backup
Earlier articles in this series urged you to perform risk analysis for your production systems. If you did that, then you already know the importance of the various items that you back up. Most of that priority transfers directly to the backup copies.
However, treat all your backup data as a collective target. Large organizations often segregate data in backups because of time or capacity constraints, but many coalesce all of it into one place.
If you decide not to encrypt the backups of data that has no value to a thief, such as documents that you make available to the public for free, then an attacker may uncover a way to use it as a chink in your armor to get to your encrypted data.
As you think of risks to your backup data, remember one of the primary reasons that backup belongs to your disaster recovery solution: it can help your data to survive physical loss or damage to your production systems.
Geographical dispersion provides a direct answer to those concerns. A proper protection system places significant distance between at least some of your backup data and its home site.
Different geographical locations face unique threats. Coastal facilities must suffer through hurricanes. Heavily forested areas deal with more fires. Inland plains regions deal with tornadoes. Dense urban areas sometimes go through periods of destructive civil unrest or worse.
Think through how your business continuity system protects you from the realistic dangers that you face. Ransomware has added itself to the list of threats to your backup data. As their authors extend their intelligence and aggressiveness, they can interfere with your backup systems directly.
Ransomware risks to backup
Ransomware creates a unique challenge. Where traditional attacks try to steal or destroy your data, ransomware wants to prevent you from accessing it. Standard disaster recovery technique easily thwarted early ransomware. Administrators would simply wipe out the live system entirely and rebuild from the latest backup.
As ransomware proved itself a uniquely lucrative vector for malicious actors, it received greater development efforts. Where the initial iterations of this type of malware would try to spread following the techniques of viruses and worms, newer programs can specifically target backup software. If uncaught, they will encrypt all data that they can reach. Such a risk should influence your backup deployment.
Security by Redundancy
We use backup primarily because it makes a distinct copy of our live data. To solidify that protection, we need to have further redundancy within our backups. Each unique copy greatly reduces the odds of a permanent loss.
Protecting your backups with multiple tiers
Storage cost per terabyte continually declines as technology advances. You can take advantage of that to create backups of your backups. Whereas your rotation schemes and full backup scheduling schemes will prevent corruption of deduplicated data from causing overwhelming loss, they do little to protect data that only exists on a single backup.
You have several ways to address this problem:
- Multiple copies in separate locations made by your backup software
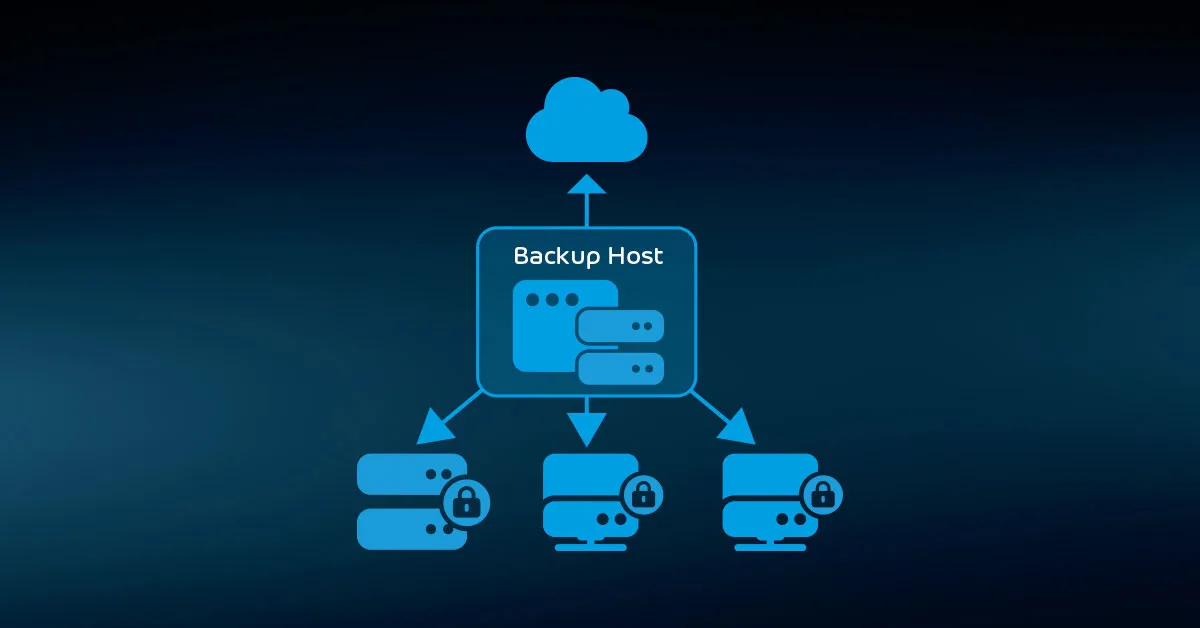
- Replication of backup data using built-in NAS/ SAN features
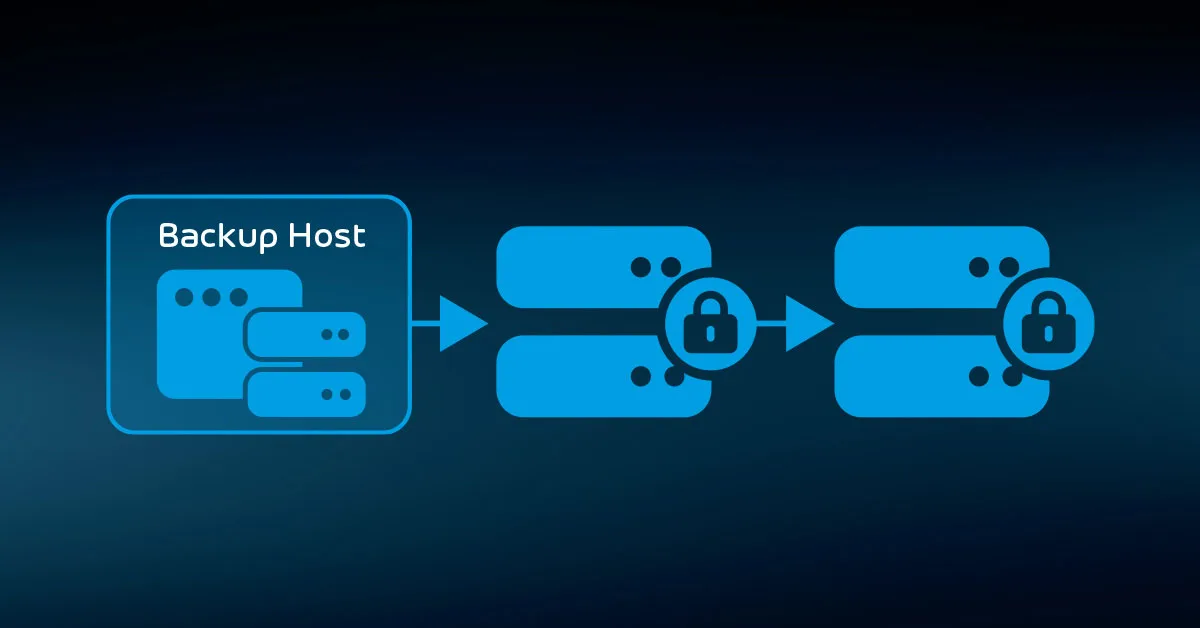
- Replication of backup data using external software
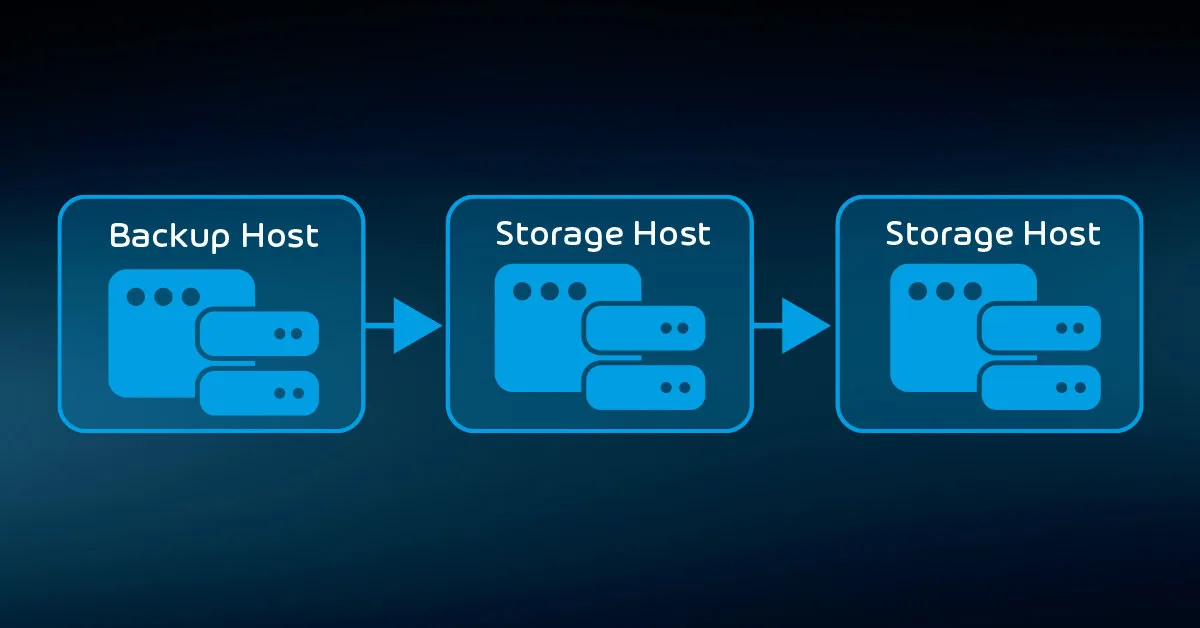
You can use multiple approaches as suits your needs and the technology available to you. For instance, you might have your backup software place its data on a NAS and then use a storage replication technology to copy it to another system.
An older solution, called disk-to-disk-to-tape, would use backup software to keep recent data on tapes and then transfer it to disk as it aged. Where possible, try to use the capabilities of your backup software. If someone needs to take over your deployment after your departure, you want them to leave them with the fewest complications possible.
While you retain control, you do not want a convoluted system that makes your maintenance activities difficult.
The role of retention and rotation policies in backup security
In and of themselves, retention policies do not impact redundancy. However, they do set how far you can stretch your media. If you have very long retention policies, then you will require more media capacity to achieve the same frequency of full backups.
Prefer to shorten your retention policy rather than sacrifice having sufficient full backups.
To make the most use of your backup media and storage space, you will establish a rotation practice to reuse it. If you have a tape-based system, then you might opt for a scheme that reuses some tapes but keeps others for long periods of time.
If you use a disk-based system, then you might rotate through removable drives or periodically exclude some backups from deduplication. Utilize these techniques in a way that balances the economics of media consumption with the value of multiple full copies.
Rotation can really shine when you leverage it as protection against malware. If malware impacts your backup solution, then it will encrypt anything that the program touches. Only your offline media will remain safe.
You will need to exercise vigilance over your backup solution so that you can catch infections before one makes its way through your rotation.
Using Account Control to Protect Your Backups
Backup has a special role in your information technology environment, but it has the same foundational needs as all your other systems. So, you can apply common security practices to it. Start by creating a unique account to run backups and lock it down. Restrict its permissions to handling backup data.
If your backup application allows it, consider using different accounts in different contexts. Exercise restraint; do not make an unmanageable mess. Follow the same practices that you should for all vital service accounts:
- Maintain tight control over the account–treat it like a domain administrator account
- Place the account in an organizational unit that grants control to the fewest people possible
- Assign viable password rotation and complexity policies to the password
- Change the password immediately if anyone with access leaves the organization
- Use a properly secured password vault.
These practices cannot provide much protection against ransomware. If malware recognizes your backup program and attacks it, then you can mitigate the damage somewhat by disabling the special backup accounts. However, if malware has penetrated your organization to that point, then any such action will almost certainly come too late.
You must spend time properly securing accounts, but do not waste time trying to develop overly creative solutions that cause more burden for administrative staff than protection. Later sections of this article series explore ways to build an effective defense against backup-aware ransomware.
Encrypting Your Backup Data
You can easily reduce the risk of your data falling into the wrong hands by employing encryption. If someone steals a tape or cracks into your cloud account, they will not gain much if they find encrypted data for which they have no key. All modern backup software should natively include some form of encryption. Avoid any that does not.

When you try the software, ensure that you understand how it implements encryption. If you intend to rely on an application’s deduplication and other storage saving features, run comparisons to determine how encryption impacts them. While encryption does greatly strengthen the security of your backups, do not rely on it alone. If someone steals an encrypted copy of your data, then they have a copy of your data. If your attacker has the expertise, time, and willingness, they will eventually break even the best ciphers with the longest keys.
We expect to have many years before anyone breaks through current cryptographic schemes, but we cannot know what vulnerabilities remain hidden or how imminent technological advances will impact code-breaking. Employ all available security measures.
Remember to take special care of the keys used to encrypt your backups. They represent the weakest links with this strategy. Use similar techniques to protect them to those that you implement for important account passwords.
Exploring Immutability
The data protection industry has renewed interest in “immutability”. To some, it might appear like a new concept. However, the fundamental intent and technology to achieve immutability has existed for a long time.
If you want to know the history, search for WORM (write once, read many) storage. However, the recent emphasis on immutability by backup solution vendors is not a mere ploy to sell more technology. WORM technology came into existence so long ago because administrators have always needed to protect the integrity of long-term storage. However, most historical threats to static data came from internal sources.
Innocent, accidental overwrites of media caused more damage than malicious attacks. The thing that brought immutability back into focus was the growing thoroughness of malware authors. Ransomware, in particular, has gained the ability to recognize and sabotage specific backup applications and technologies.
Attackers realize just as much as anyone that a restore can downgrade locked systems from an organization-ending catastrophe to an exasperating interruption. Those interruptions ruin days or even weeks for the targeted institution, but they don’t lead to ransom payments. So, threat actors attack backup systems along with the live environment.
Now, not only do you have to worry about reachable data, you also have to worry about it during backup and restore processes. Immutability helps to solve the problem of attacks on backup. Instead of forcing administrators to depend on defensive techniques and tools to safeguard data, immutability tools prevent all modifications to data. That block includes the backup software that created the backup.
Modern immutability solutions
Original WORM solutions used optical discs. Even today, nothing quite matches the permanence of using a laser to alter a material surface. Unfortunately, optical media lacks sufficient capacity for most applications today. To address that problem, vendors have produced multiple alternatives.
Most removable magnetic media has a write-protection mechanism. Tape has emerged as the last media standing in this field. Usually, an operator must physically move a sliding piece of plastic or break off a tab. Some manufacturers provide tape cartridges that can automatically switch to a write-protected state after the first write. Tape drives have their own physical mechanisms to detect write-protect status. Only someone with physical access can defeat or bypass these systems.
Some SAN vendors enable WORM facilities. Usage depends on the device’s architecture. Only someone with administrative access to the SAN can remove the protection.
Ransomware has motivated backup software vendors to innovate. Specifics vary between vendors, but most involve a collaboration between software and a cloud provider. For example, Hornetsecurity VM Backup V9 uses its existing cloud storage mechanism to integrate with cloud immutability offerings. Because policy determines immutability, even administrators cannot change data until the policy’s duration expires. This power gives us the same protection as the original optical WORM solutions without the capacity restrictions.
Isolating Your Backup Systems
Take steps to reduce the surface area of your backup. In some way, backup touches everything in your environment, but the reverse does not need to be true. Isolation techniques range from simple to highly complex; you will need to balance the risk of not employing a method against the effort of implementing it.
To properly protect your virtualization environment and all the data, use Hornetsecurity VM Backup to securely back up and replicate your virtual machine.
For complete guidance, get our comprehensive Backup Bible, which serves as your indispensable resource containing invaluable information on backup and disaster recovery.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
In an era dominated by the ever-evolving threat of ransomware, relying on luck to safeguard backup systems is no longer viable. The potential consequences of a compromise can be dire, leading to significant data loss and operational disruptions. Therefore, we at Hornetsecurity urge organizations to adopt a proactive approach in order to secure and protect backup data to ensure comprehensive data security.
FAQ
The only secure method you need to back up your virtual machine data is the comprehensive VM backup solution by Hornetsecurity. Get your trial version now: https://www.hornetsecurity.com/en/services/vm-backup/
Safeguarding your data with a strong security protocol is a wise move. One effective practice is the 3-2-1 backup rule, which entails having three copies of your data (including live data and two backups), utilizing two different storage media, and storing one copy offsite. A hybrid backup approach, combining local and cloud destinations, offers an excellent implementation of this rule effectively.
Data security refers to data protection from unauthorized access, use, change, disclosure, and destruction, including network, physical, and file security.

