

Phishing Technique Trends
Summary
The basic idea behind phishing has not changed since the 90s, however, the delivery tactics and techniques are constantly evolving. In this article we outline current trends in phishing techniques. These include abuse of legitimate file hosting services, geo-fencing, automatically loading the victims company and/or email provider logo on the phishing website and asking the victim for the password multiple times.
These tactics are aimed at evading detection and luring more victims into entering their login credentials into the phishing websites.
Background
Malicious actors use phishing emails to gain access to a victim’s login credentials by tricking the victim into voluntarily entering their password on a fake login form. The fake login is delivered via a phishing website. The phishing emails include the link to the phishing website.
Phishing as an attack technique is known since the 1980s. The name originates from a computer intrusion tool called AOHell, which included a “fisher” tool, that would spam AOL Instant Messaging users with the following message:
Hi, this is AOL Customer Service. We’re running a security check and need to verify your account. Please enter your username and password to continue.
The spelling of “phishing” with “ph” instead of “f” comes from an intentional misspelling used in 60s to 70s technology subculture slang. It originated from the term “phreak”, meaning a “phone freak”, which at the time was a hacking subculture slang term for people exploring and experimenting with early telephone networks. Thus the term phishing as we know it today was formed.
The essence of phishing has not changed much from the AOHell tool. Potential victims are contacted, under different pretexts to divulge their login credentials. However, the tactics and techniques with which the phishing emails are delivered have evolved. Hornetsecurity explains the current tactics and techniques used by current phishing attacks.
Analysis of current phishing technique trends
Most phishing emails contain a link to a phishing website featuring a fake login form. Though, a few exceptions exist, e.g., we previously reported on a phishing scheme that send the entire HTML source code of the phishing website attached to the phishing email1.
The emails use various different lures to get the victim to visit the link, e.g., by pretending a file can be downloaded via the link, as can be seen in the following example phishing email:
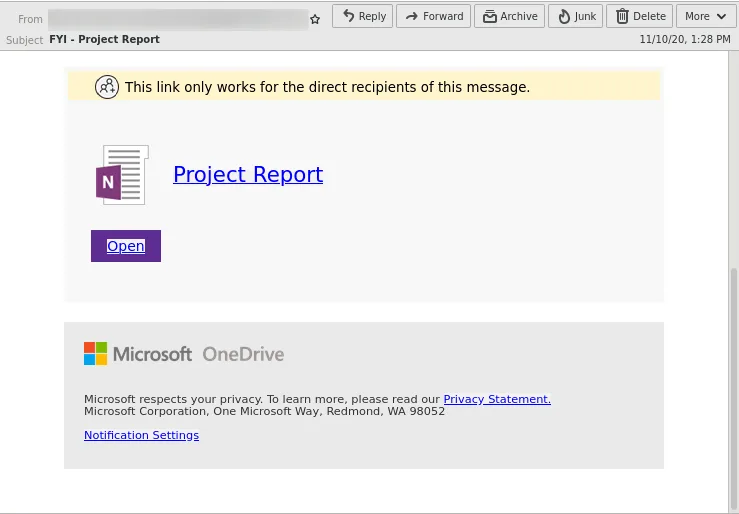
By visiting the link the potential victim is send to the phishing website.
In the following we will outline tactics and techniques that current phishing attacks use to evade detection and lure even cautious victims into their scam.
Abuse of legitimate file hosting services
Phishers host parts of their phishing kit on legitimate file hosting services to evade detection systems and to build trust with their victims. This way the link in the email will feature a domain name from a known legitimate service, trusted by millions of people.
The following example shows a phishing kit hosted on Google’s Firebase platform:
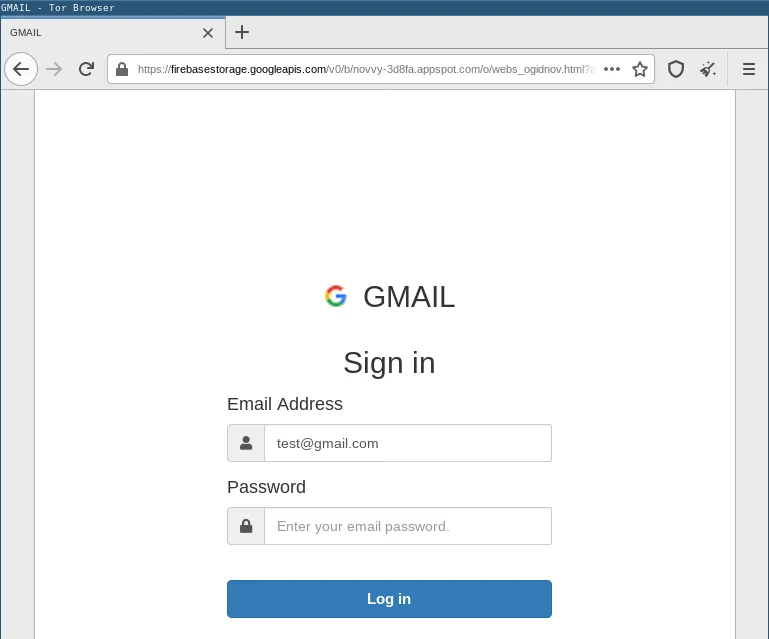
Abuse of file hosting services, such as Google Docs, Google Drive, Microsoft SharePoint and others, is nothing new. However, the number of phishing attacks relying on cloud storage providers has increased significantly.
The problem for potential victims is that some of these file hosting services sometimes do legitimately ask visitors to sign in to see the content. This means a potential victim is lured onto a website that they know will sometimes ask them to login, requiring high alertness to not fall for phishing scams using this tactic.
Because legitimate file hosting services are used by a lot of people for legitimate purposes their domains and URLs generally have a good reputation. This makes it hard to distinguish between emails containing legitimate file hosting service links or malicious ones.
Furthermore, some file hosting services use CAPTCHAs to prevent automatic retrieval of the hosted content, meaning automated security mechanisms can not scan the hosted content for malicious artifacts.
Ironically, we also sometimes find phishing for a particular vendor being hosted by that very same vendors infrastructure, e.g., the following phishing site impersonating Microsoft was hosted on Microsoft’s Azure platform:
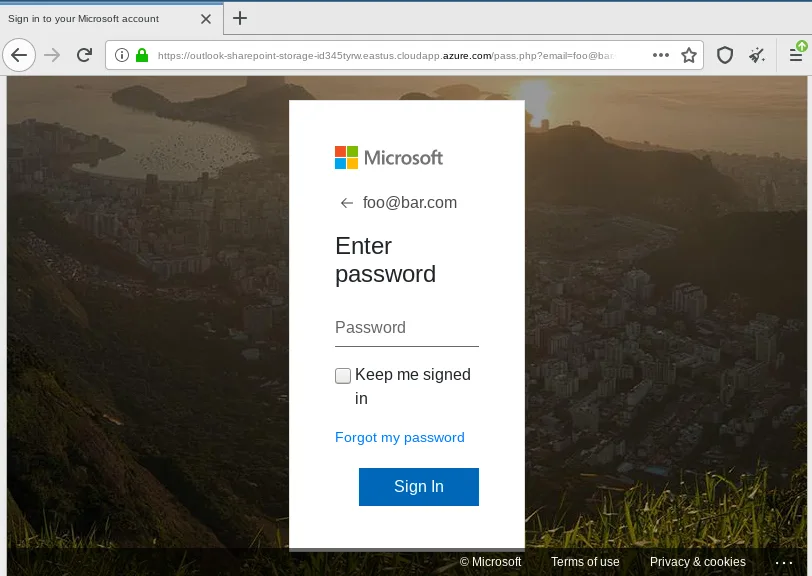
Access to the account needed to use these legitimate file hosting services is often obtain via the phishing activity itself, thus, creating a self-sustaining phishing machinery.
Redirection
In order to complicate analysis, malware actors often use multiple intermediate websites that redirect their victims to the final website controlled by the attackers. This way simply blocking the final phishing website is not enough, because in emails only the first redirect URL is visible. If attackers can manage to prevent automated scanning systems from following the redirects, e.g., combining this technique with geo-fencing or a CAPTCHA, then these automated systems will not detect that a victim will be redirected to a phishing site.
In case of phishing emails, the redirects can be documents hosted on file hosting services, which provide the victim with another link to the final phishing page. The phishing page is then often pretending that the user must provide their login credentials to view the document they just clicked. This is a plausible lure, because after all the victim did click a link to view a document and it is common for fie hosting services to ask the user to login in order to access files.
This way the only observable URL in the phishing emails are the intermediate redirects.
The following example is a phishing redirection document hosted on OneDrive:
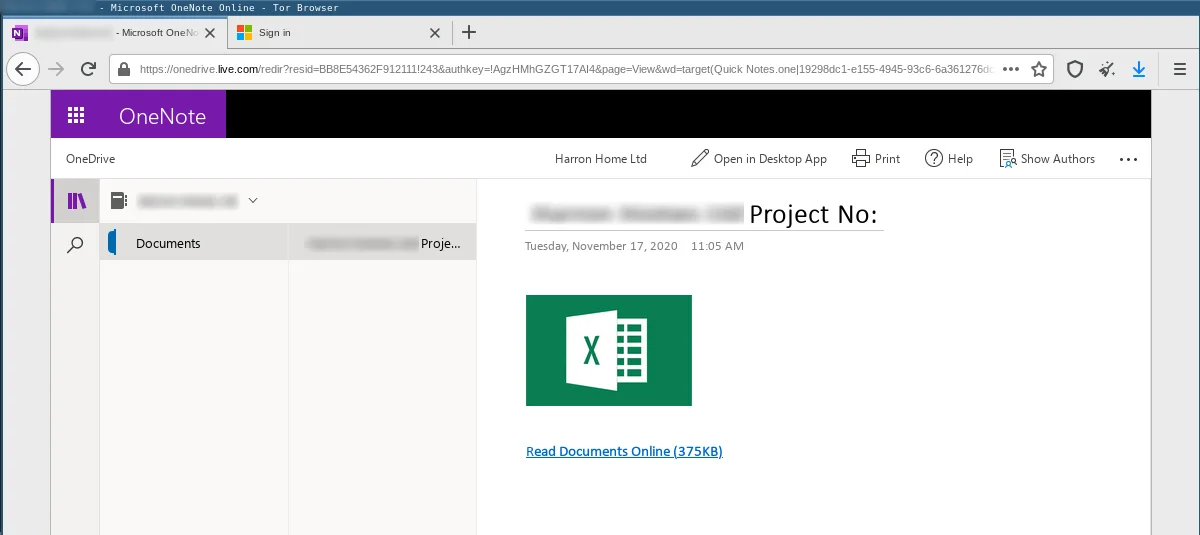
When the victim clicks on the allegedly linked document they are redirected to a phishing page impersonating the Microsoft SSO login page:
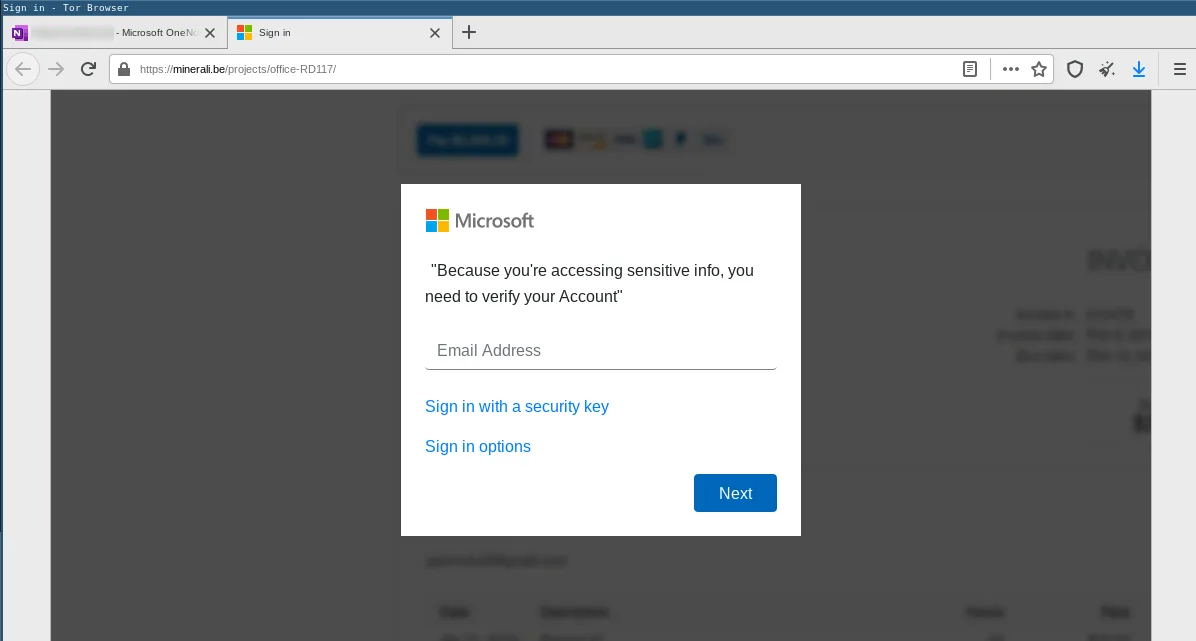
Geo-fencing
Another technique to hinder analysis of the phishing websites is geo-fencing. To this end, the phishing website, or sometimes a simple upstream website redirecting the victim to a specific destination, will check the visitor’s IP address. Based on these checks victims whose IP address geo-locations are in the list of countries targeted by the specific phishing scam will get to see the phishing website, other requests are usually being forwarded to a benign website.
The following is an example of a phishing scam against Raiffeisen ELBA, an Austrian bank:
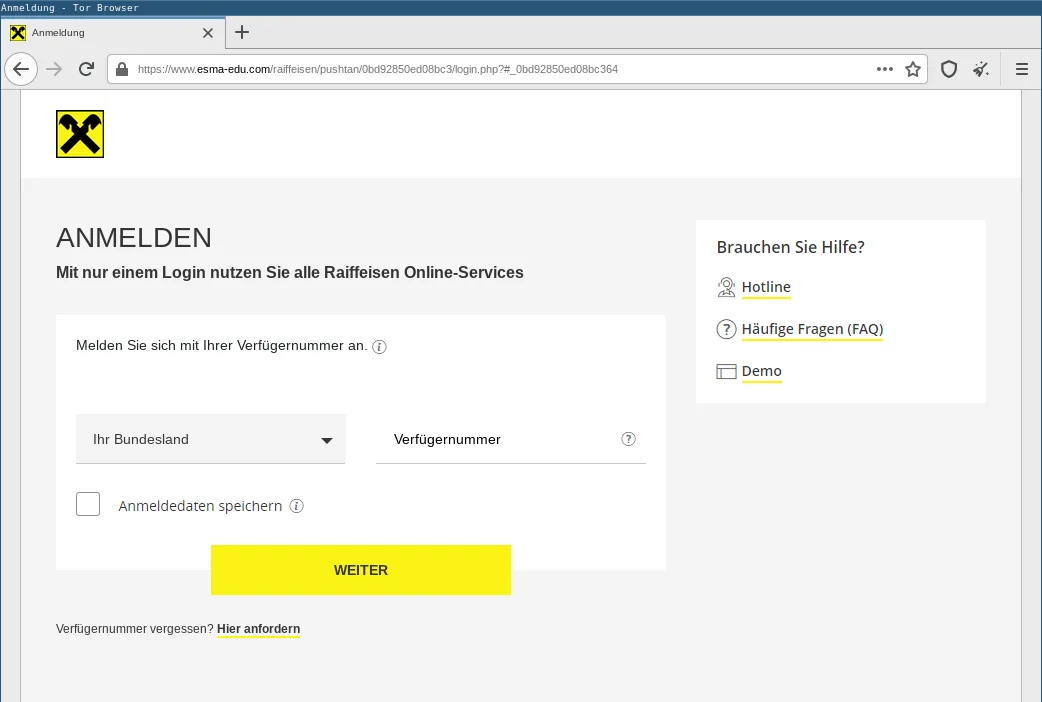
This phishing site is only available to visitors using an IP address geo-located in Austria. Any visitors from other countries are redirected to the legitimate Raiffeisen ELBA website. Hence, geo-fencing complicates automated analysis.
Adaptive lure logo
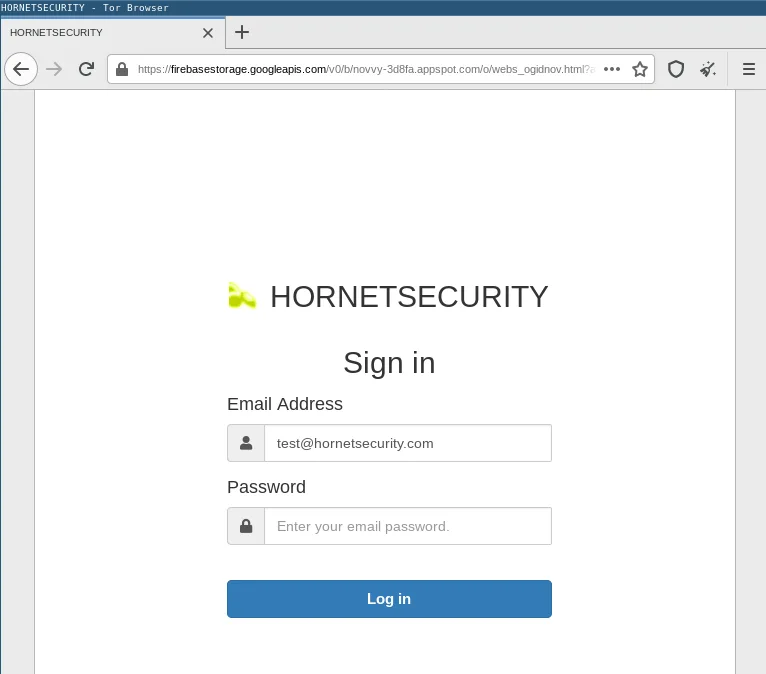
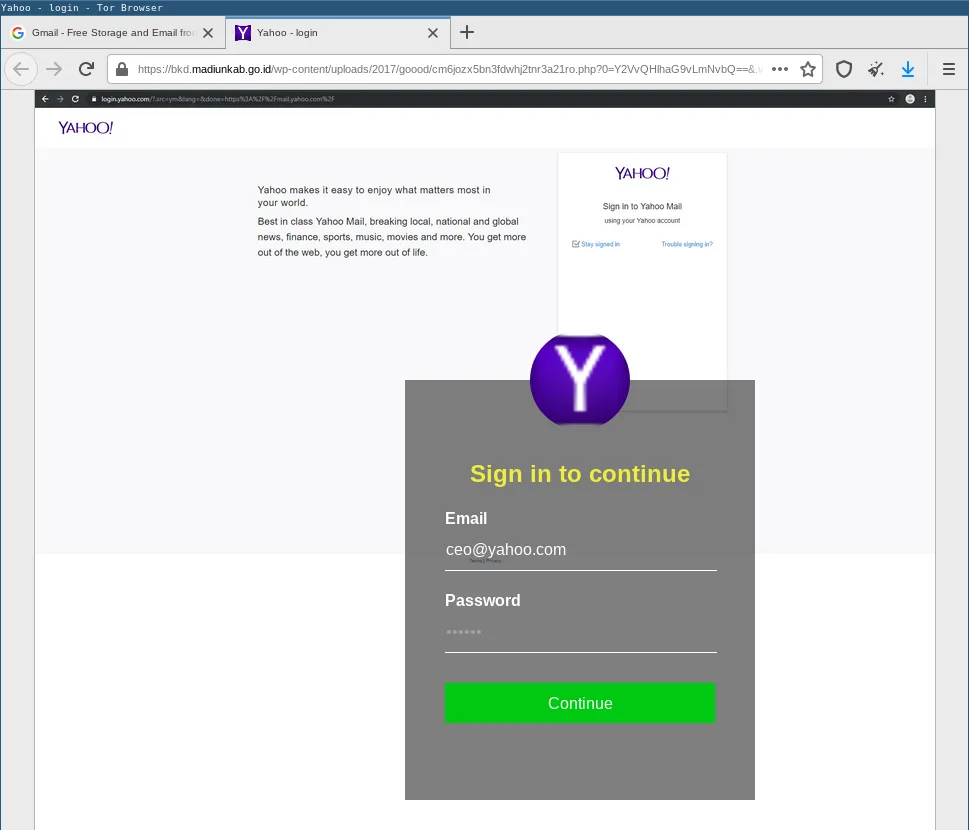
Some phishing websites do not impersonate a specific company or service. They rather adapt to the victim’s expectations. To this end, they will dynamically add company and/or service logos to their login form based on the victim’s email address.
For example, if John Doe receives a phishing email in his mailbox test@example.com, the URL in the phishing email will contain this email address as an HTTP GET parameter. When visiting the phishing website via this link, the email address is automatically sent to the phishing kit via this GET parameter. The phishing website will then not only pre-fill the login form’s email field with this email address, but also obtain the favicon of the email address’ domain name using the following link provided by Google:
https://www.google.com/s2/favicons?domain=example.com
The favicon is then displayed above the fake login form as follows:
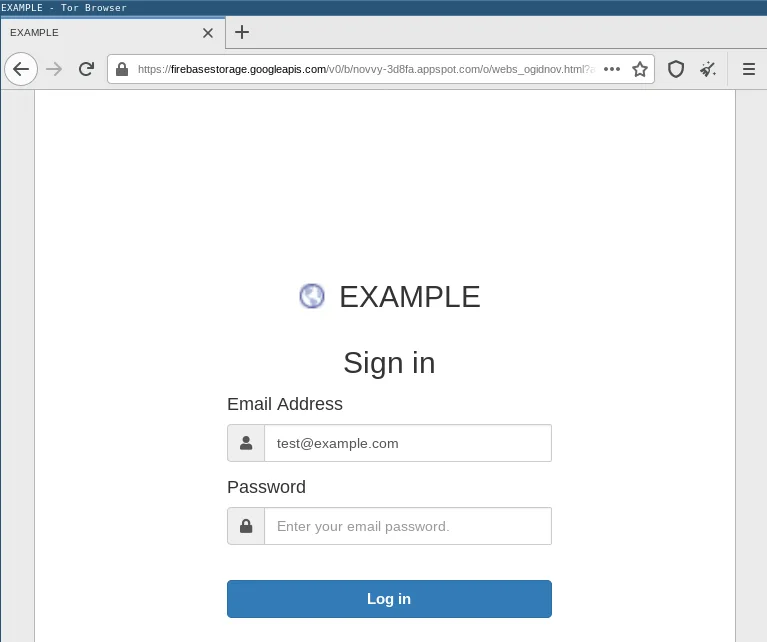
Because most domains also host websites with a favicon, this technique works against virtually all email domain names.
For example, it works against popular freemail providers:

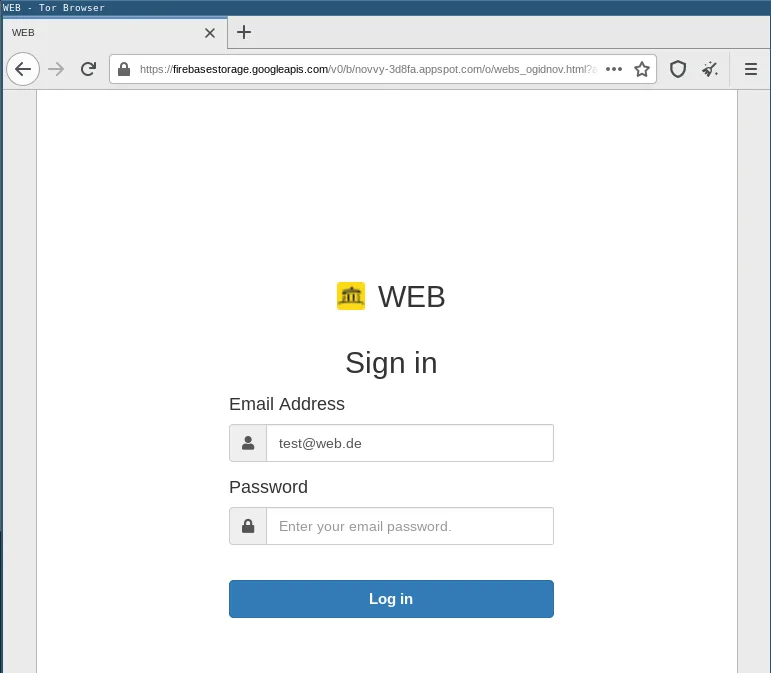
But it will also work against company domain names, as can be seen here, using our own domain name:
We also observed phishing kits that screenshot the website behind the victim’s email domain and display it as background image behind the fake login form:
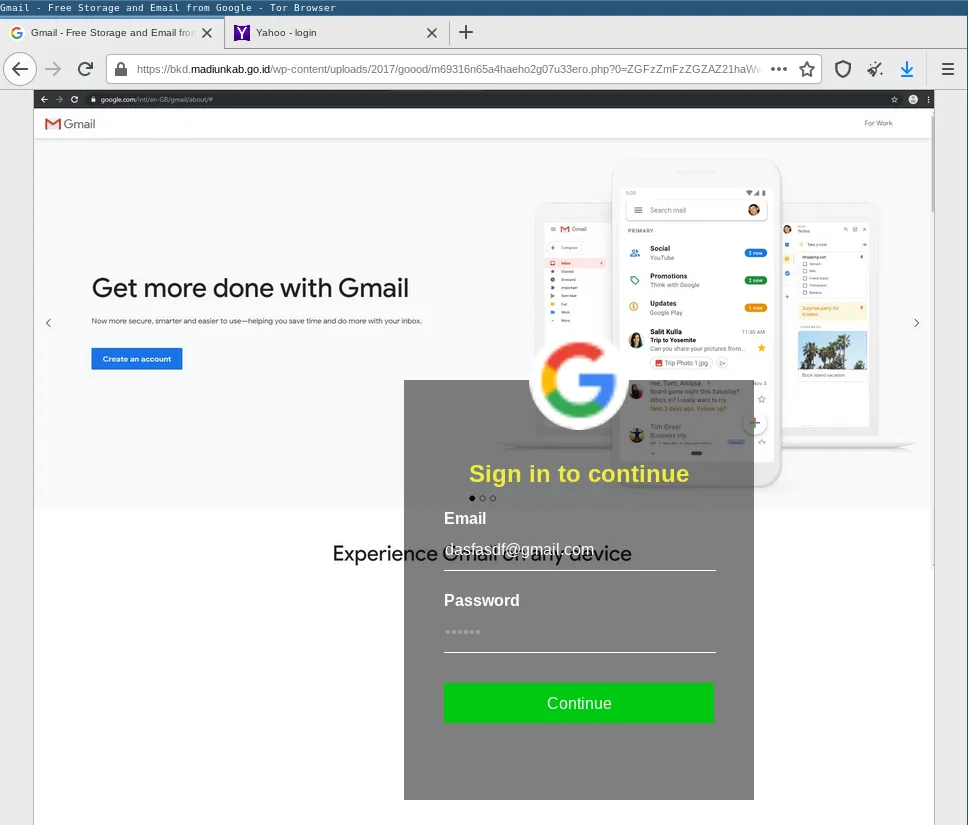
All these techniques help the attackers to make their phishing site appear more familiar to the victims.
Asking for the password multiple times
Modern phishing kits will ask the victim for the password multiple times. While this is nothing new and we have previously reported on this technique,1 we observe more and more phishing kits using this technique.
This technique is likely to workaround a protection scheme that some users have come up with to protect against phishing. Some users believe that phishing websites will always accept any password. Hence, you can spot a phishing website by entering a wrong password. A phishing website will accept the wrong password, while the legitimate site will reject it as incorrect. This assumption is, however, wrong.
The following shows a phishing kit asking the victim for the password three times:
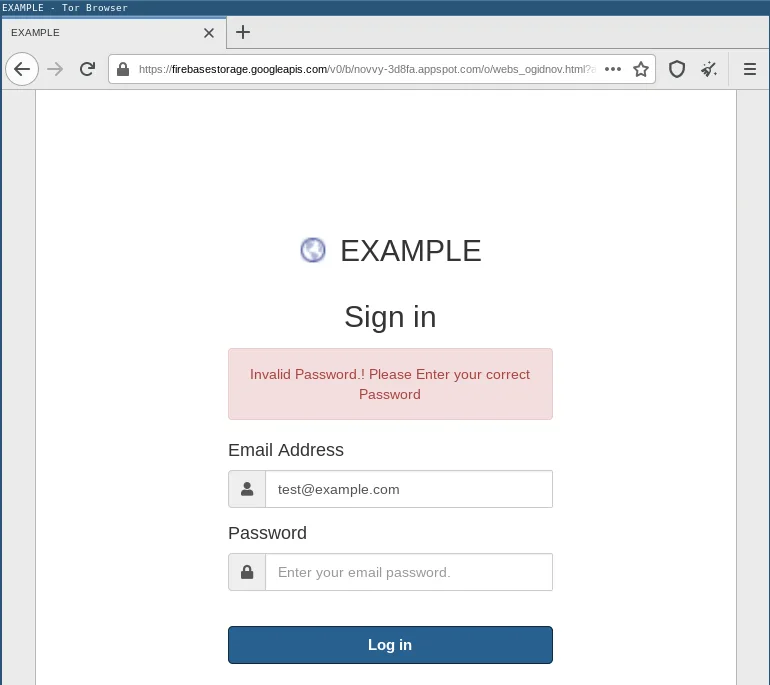
It does not matter what the victim enters, the entry is always rejected three times. Afterwards the victim is redirected to the website running on the domain name used in the email address. This is a good segue into the next tactic.
Transition to original website
Every good heist needs a good getaway. So does a good phishing kit. Ideally, after entering their login credentials the victims should not notice that they got phished and thus not change their login credentials. To this end, phishing kits usually redirect to the legitimate website they are faking. So in case the user was already logged in, they will assume they just logged in successfully. Another tactic is to redirect to a fake non-malicious document. The victim will then think they got the email by accident and it was not directed at them.
Self-sustaining phishing machinery
Last but not least, we observed several phishing campaigns that are self-sustaining. To this end, stolen login credentials will be used to send phishing emails from the victim’s account. We also observed stolen credentials being used to compromise Sharepoint accounts to host phishing infrastructure on them. While not directly observable, we are certain that stolen credentials are also used to place phishing infrastructure on legitimate file hosting services, using phishing victims’ accounts.
The time between account compromise and usage of the accounts was sometimes as short as several hours. However, most commonly stolen login credentials are usually used on the next phishing campaign. Hence, it is very important for victims, or even just potential victims, to quickly change their passwords if they have any suspicion that they may have entered their login credentials on a phishing site. This is because, while we observed some of the stolen credentials were used to perpetuate the phishing scam, other login credentials are likely used in further intrusions, such as ransomware attacks.
Conclusion and Countermeasure
While the basic idea behind phishing has not changed since the 90s, the tactics and techniques are constantly evolving. From the outlined techniques we can recommend the following countermeasures:
Users should not automatically trust known legitimate file hosting services, such as Google Docs, Microsoft SharePoint, OneDrive, etc., because they are abused to host malicious phishing infrastructure. Users should use password managers that only fill-in their login credentials on the appropriate login forms. To this end, password managers will usually check the domain name and thus prevent filling-in login credentials on logins forms hosted on impostor websites. But most importantly, users should activate 2FA wherever possible. We have seen phishing attacks featuring QR codes for 2FA banking apps. This means phishing actors are aware of 2FA and will try to obtain the 2FA codes where necessary and possible. Hence, a second factor with that can not be phished, like a U2F token, is preferred.
Last but not least, Hornetsecurity’s Spam Protection and Malware Protection filters and Hornetsecurity’s Advanced Threat Protection are also constantly improving to keep up with the lastest threats.


