

Monthly Threat Review June 2023
QakBot remains a threat, DHL and Crypto Service MetaMask Brand Impersonation on the Rise
Introduction
The Monthly Threat Review by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Review focuses on data for the month of June.
Executive Summary
- The overall trend for June vs. May is a decrease in threats. That said, the number of more sophisticated malware campaigns increased.
- PDF usage as a payload delivery mechanism is up 1.4% over the previous month. Continued use by the Qakbot malware largely drives this.
- Despite Microsoft’s crackdown on Macros in Office products, using Word and Excel documents for payload delivery has increased. While the attack chain is more difficult now due to Microsoft’s changes, threat actors are successfully using cleverly crafted documents to trick users into copying suspicious files to the Office templates folder, where execution is then allowed.
- Mining and Entertainment continue to be the current most-targeted industry verticals.
- We have observed large increases in brand impersonation attacks for DHL, MetaMask, American Express, Strato, and LinkedIn.
- Multiple SQL injection vulnerabilities in the MOVEit file-transfer application from Progress Software have led to data breaches across countries and industry sectors. Rapid patching and mitigation are STRONGLY recommended.
- AI continues to be a sore spot for security and privacy across the industry. Compromised OpenAI accounts with logged prompt history could be a potential issue for organizations using privileged information within chat prompts.
- AI-enabled attacks are predicted to increase and eventually become the norm.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for June 2023 compared to May 2023.
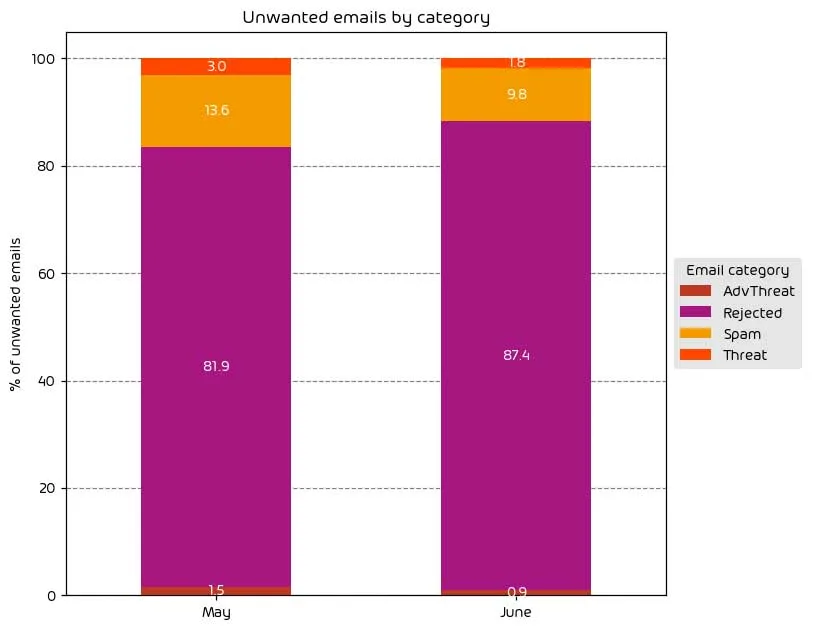
Overall amounts of traffic in the “Threat”, “AdvThreat”, and “Spam” categories were down for June, while the amount of traffic “Rejected” saw a 5.3% increase for the month.
As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the connection right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in attacks.
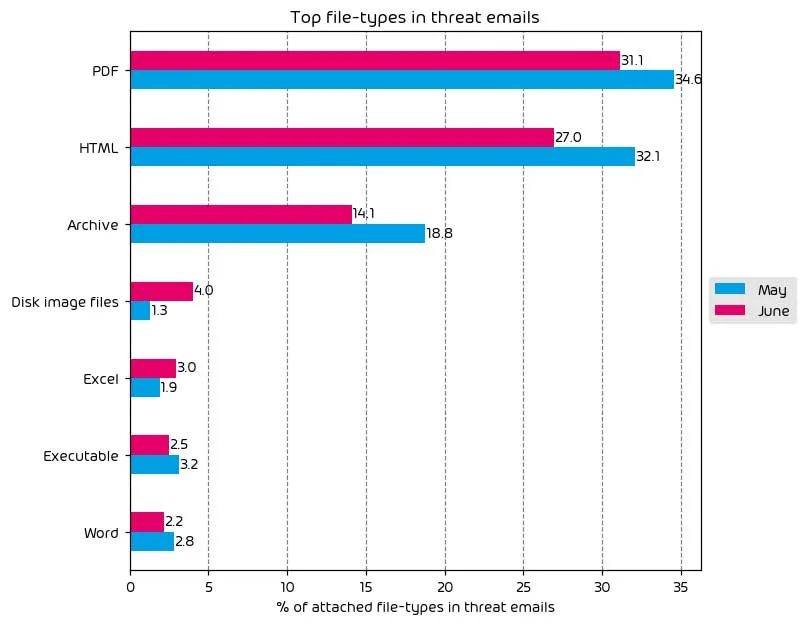
The re-emergence of Qakbot is seen as the primary driver behind the increase in PDF attachments over the last few months. As some other delivery mechanisms, such as DOCX (Word), have become more challenging, PDF remains a popular option for threat actors.
NOTE: If you would like to learn more about Qakbot and botnets, check out the Security Swarm Podcast episode below.
That said, attackers continue to find ways around Microsoft’s decision to disable macros in Office applications by default. This is usually done by a cleverly crafted header within the malicious document that is made to appear as a legit Office notification. The “notification” instructs the user to move the offending document to the Office templates folder and re-open it. This will typically allow the malicious code to run on the target system.
The difficulties in leveraging office documents for malicious purposes continue to drive the use of other file types for attacks, such as HTML, which use is still relatively high, and disk image files.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
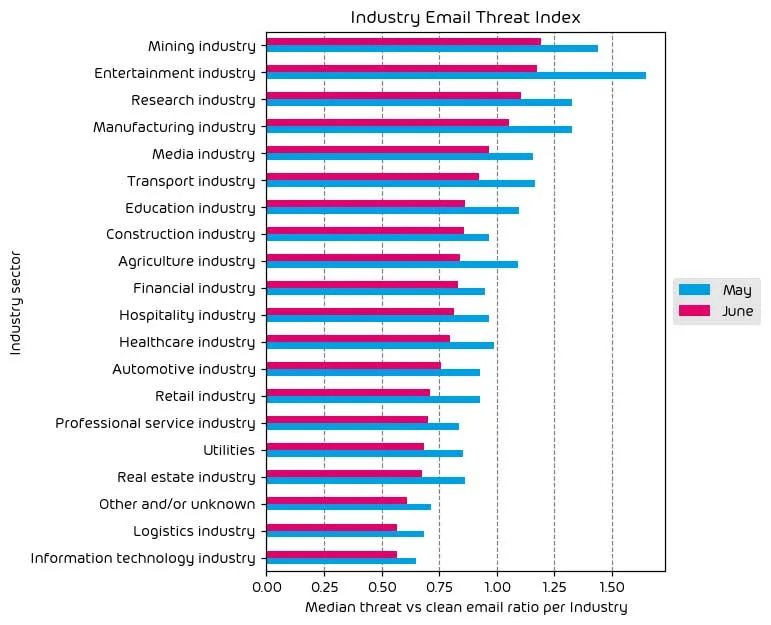
Overall, the threat is down across the board for June compared to May. This coincides with fewer malicious emails, as shown in the “Unwanted Emails by Category” section above. One potential reason could be that this is the start of the summer holiday season, and threat actors may assume that fewer people are in the office. In addition, fewer compromised devices abused for sending spam and threat emails are online. However, it is important to highlight that the number of more sophisticated malware campaigns, such as QakBot, increased.
Regarding the top targeted industry, the Mining and Entertainment verticals remain the most targeted sector for June, just as in May.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
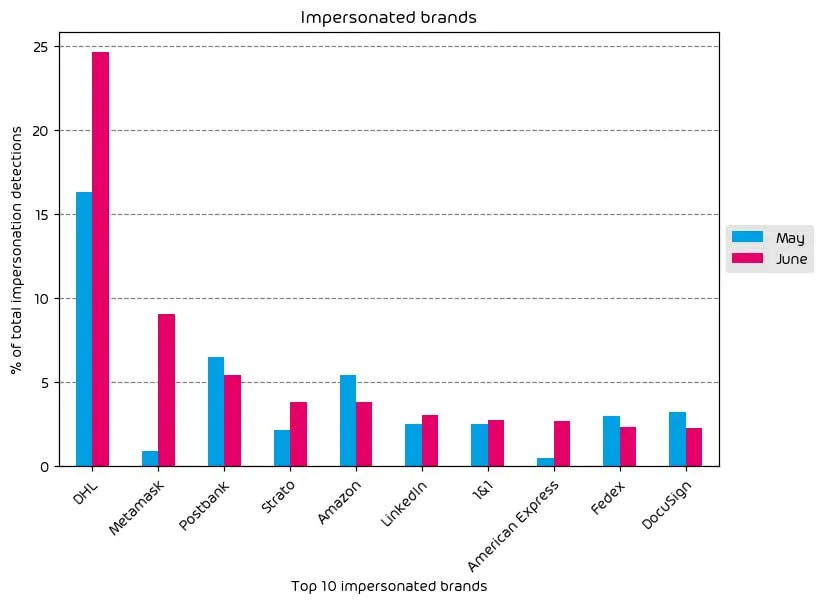
The biggest mover on this list for June is MetaMask, one of the largest crypto wallet providers. An extensive threat-actor campaign (June 27-29) targeted users of the MetaMask Cryptocurrency Wallet service. The goal was to impersonate the brand to access the victim’s crypto wallets and the funds within.
Brand impersonation for DHL, American Express, Strato, LinkedIn, and 1&1 also saw a marked increase over the month compared to May. These all remain popular options for threat actors — especially shipping services such as DHL. With the increase in at-home deliveries in the last couple of years, threat actors know they have a high probability of landing a compelling “shipping email” into users’ mailboxes when they may be expecting a delivery.
Major Incidents and Industry Events
The current major concern in the industry continues to be the fallout from vulnerabilities in the popular file-transfer software MOVEit from Progress Software. While multiple vulnerabilities are at play, the most severe has been categorized as SQL injection attacks that enable privilege escalation and unauthorized access to environments. The most recent CVE for the MOVEit Transfer application is being tracked as CVE-2023-35708. If you use MOVEit and still need to apply the June 15th patch, it is STRONGLY recommended you block traffic to MOVEit via ports 80 and 443.
Despite the danger, many businesses are being caught off guard. There are several organizations that have been impacted by these vulnerabilities, including the New York City Department of Education, Schneider Electric, Siemens Electric, and 122 organizations in total, according to Ars Technica.
Other concerns in the industry continue to center around the use of AI, either via direct use by threat actors to launch AI-enabled attacks or in terms of privacy concerns. The Hacker News recently reported over 100k OpenAI accounts had been stolen and sold on the dark web. Remember that ChatGPT saves a log of all previous prompts and responses. Pair this with the news that there have been several instances of business employees inputting sensitive company data into AI services, and you have a recipe for disaster. Samsung recently fell victim to this problem.
Predictions for the Coming Months
While the industry hopes there will be no further fallout from the MOVEit zero-day vulnerability, we expect to hear from more casualties in the following days and weeks. Security researchers and threat actors may test attack patterns against the MOVEit zero-day vulnerability on other popular services to see if it can be applied. Consequently, we may see similar findings affecting other services in the near future as the vulnerability gains attention in the news.
We are also likely to see AI-enabled attacks continue to ramp up. With ChatGPT accounts readily available for purchase on the dark web, we will likely see threat actors continue to utilize it for assistance with attacks. On top of that, we are likely to see cases where sensitive data has been compromised due to stolen ChatGPT accounts and logged prompt data. Stolen sensitive data can be used not only for extortion but also for spearphishing attacks.
On top of all this, the usual threats persist. Qakbot will continue operations. It is uncertain what the current operational status of Emotet is, but it is possible that we could see it reemerge utilizing advanced delivery methods similar to those used by the QakBot malware. While not as heavily featured in the news as some of the other items mentioned above, the threat of these botnets remains nonetheless.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Andy Syrewicze, Security Evangelist, on AI-Enabled Attacks:
We continue to see cases where threat actors leverage AI for attacks, either for OSINT purposes or for automating a portion of the attack chain. While the doom and gloom of our new AI-fueled world have SOME genuine cause for concern, it’s important to remember that the blue team can also use AI. This includes training, log analysis, machine learning and natural language processing for defensive tools, and LOTS of other possibilities. The arms race between threat actors and blue teams will continue, and blue teams can use AI-powered defensive tools to keep up with threat-actor capabilities.
From Umut Alemdar, Head of Security Lab, on the QakBot malware:
The dynamic and rapidly evolving nature of the QakBot malware poses significant risks to businesses and organizations worldwide. The threat actors behind QakBot changed the delivery techniques multiple times this year to manage to bypass security solutions, and we expect to see more creative approaches in the second half of the year. Hence, investing in advanced protection systems augmented by AI and incident response tools is crucial for businesses today. Additionally, conducting regular cybersecurity awareness training for employees is paramount, as it significantly mitigates the risk of successful filter bypasses and safeguards your organization from costly breaches. A proactive, well-rounded approach to cybersecurity is the key to staying secure.
Monthly Recommendations
Given the current state of the landscape, what are our monthly recommendations?
- For starters, you can continue to use this monthly report to stay current on the latest email threats and communicate those most relevant to your user base. For example, if your organization uses DHL for regular shipments, communicate the risk of fraudulent DHL emails to the relevant team members.
- Train your users HEAVILY to scrutinize PDF, Word, and Excel files. We continue to see these files being used for the delivery of payloads. If a user sees one of these file types from an external source, they should be trained to be extra careful with such emails. That said, if you need help training your users along these lines and you are not already a Hornetsecurity customer, be sure to check out our Security Awareness Service for more information.
- If your organization uses MOVEit by Progress Software, we urge you to install the latest patches. If you still need to install the patches, block traffic to the service on ports 80 and 443 AT A MINIMUM until you can apply the patches. This vulnerability is being actively exploited in the wild, so do not wait.
- If your organization still needs to discuss how workers should or should not be using AI tools, you should do so ASAP and develop internal policies. Many organizations have lost the governance of sensitive company data when employees use said data inside of an AI prompt. This potential exposure point needs to be addressed with internal policies at a minimum.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.


