

Monthly Threat Report May 2024: Satya Nadella’s Statement on Security, and a New UK Law Impacting the Industry
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of April 2024.
Executive Summary
- Overall, email threats are down for the month, shown by a 3.5% percentage point increase in the number of clean emails. Remember though, even though email threats are lower this month, threats remain, and businesses should remain vigilant.
- PDFs were the most used file type for the delivery of malicious payloads in email attacks throughout the data period.
- We noted an increase in the use of Malicious Excel documents.
- The Mining, Media, and Hospitality industries were the top targeted verticals this month.
- Most impersonated brands this month were Commerzbank, Fedex, DHL, and Facebook.
- Microsoft’s CEO Satya Nadella has confirmed that the company will double down on security and focus on resolving security issues prior to working on new features.
- The UK’s Product Security and Telecommunications Infrastructure Act (PSTI) sets new guidelines regarding passwords, security best practices and more for IOT and consumer home devices. Said guidelines apply to anyone in the tech supply chain in the UK.
- Change Healthcare has confirmed that they did indeed pay a $22 Million USD ransom back in February.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for April 2024 compared to March 2024.
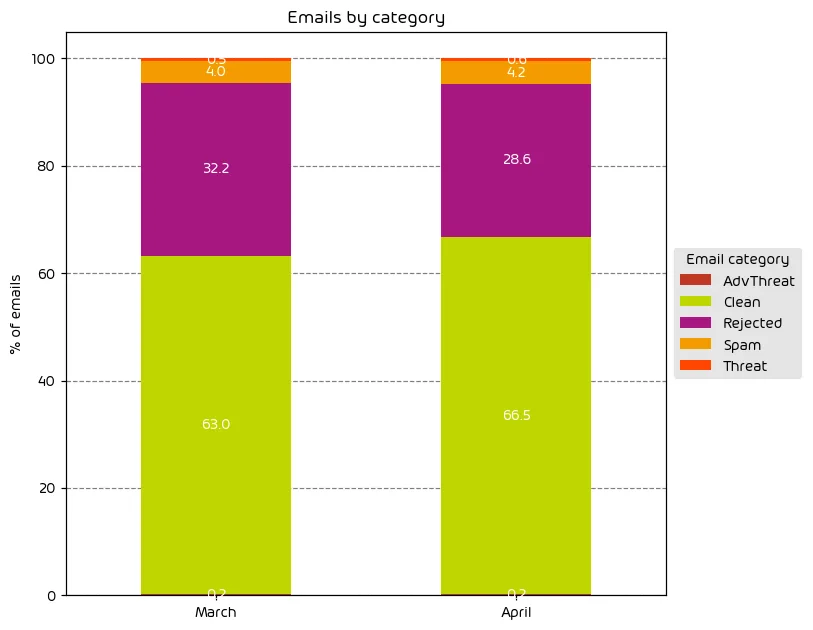
We observed a net-decrease in the amount of email-based threats overall throughout the data period with a 3.5% percentage-point increase in the amount of emails classified as “Clean”. That said we saw a very slight percentage-point increase in both the amount of “Spam” messages as well as those messages classified as “Threats”.
These findings can be attributed to the end of tax season in some countries, including the US. During such times, threat actors will make use of target’s expectation to tax communications in their emails. With most people having finished their taxes, threat actors will be moving onto other targets.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
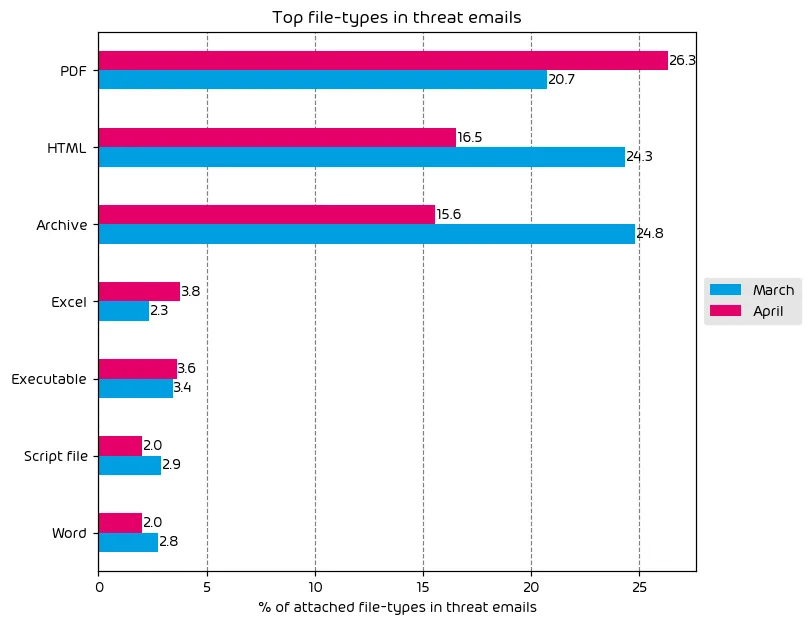
The top file types used this month for the delivery of malicious payloads within email attacks are PDF, HTML, and Archive files. While PDF usage spiked by threat actors, the other 2 usual offenders saw a reduction.
Also worth noting is a noted increase in the use of malicious excel documents. We’ve seen a massive decrease in attacks incorporating malicious office documents since Microsoft’s decision to block Office macros by default. That said, threat actors have found ways around this via social engineering. For example, the threat actor may format the spreadsheet in such a way that it appears to contain a legit Excel notification message that instructs the user to move the excel doc to the office templates folder, or it will walk them through enabling macros. Either option will allow the execution of the file’s malicious contents.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percentage values for all organizations within the same industry to form the industry’s final threat score.
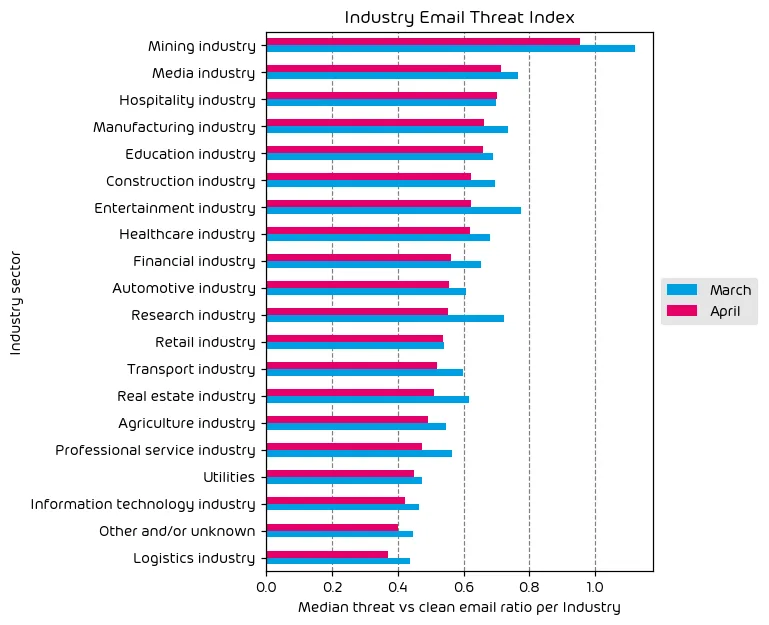
The Mining industry continues to top the list as the most targeted industry vertical for this month’s report. It’s worth noting that it’s common for some mining organizations to also conduct factory operations, so these organizations have to contend with not just mining-related difficulties, but the typical factory and manufacturing risk factors as well, so it’s not uncommon to see this vertical at, or near the top of the list.
The media industry continues to be targeted on a regular basis. These organizations are made popular targets for purposes of information gathering as well as for use in misinformation campaigns – a trend that we’re likely to see continue as we get closer to US elections.
Finally, the hospitality industry has moved up to third on our list of most targeted verticals. This can be attributed to the fact that we’re nearing vacation season for many countries, and threat-actors will look to capitalize on individuals making travel plans for the coming summer.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
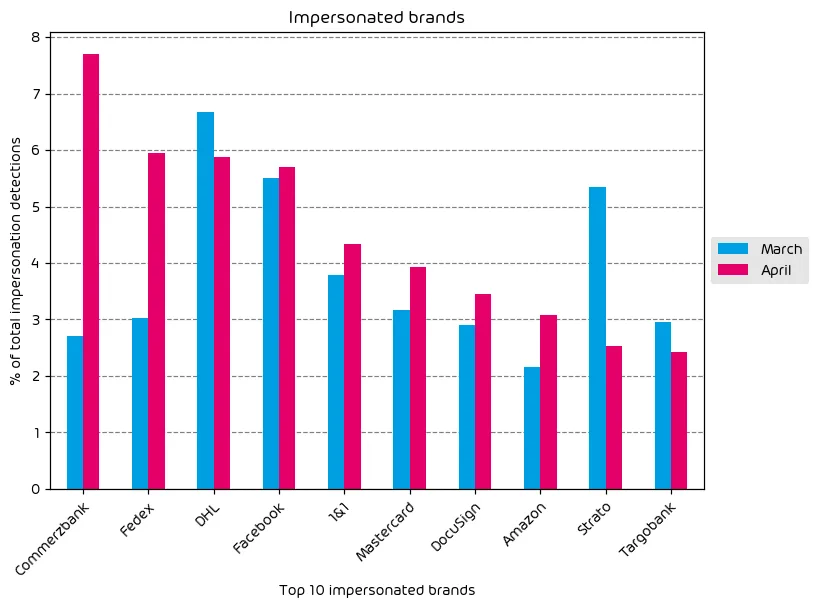
Our impersonated brands data this month shows some interesting findings. To start, we observed a massive impersonation campaign targeting the German financial entity Commerzbank. This campaign saw a large volume of impersonation attempts and is the most impersonated brand this month by a large margin. Also highly impersonated were Fedex, DHL, and Facebook. These are all common brands that are well known by consumers and widely trusted – making them perfect for use in impersonation scams.
With the tax season nearing its end, many are finalizing tax paperwork and arranging financial transactions. As such, we noted an increase in the amount of DocuSign and Mastercard brand impersonations as well.
Major Incidents and Industry Events
Satya and Microsoft Double Down on Security
We’ve discussed many of Microsoft’s major security lapses extensively both in this monthly report and on The Security Swarm Podcast. One thing that has been missing amongst the litany of security issues Microsoft has been dealing with is a clear sign from CEO Satya Nadella that the security lapses are being taken seriously and that resolution is being driven by senior leadership within the company. Well, that is exactly the message communicated by Satya Nadella in a recent Microsoft earnings call. This high-profile announcement is the first step needed for Microsoft to begin to restore some of the trust lost from past cybersecurity incidents.
The announcement has likely been driven by the recent US Cyber Safety Review Board’s (CSRB) investigation into the Storm-0558 breach last year. We’ve covered the Storm-0558 breach extensively via podcast and it’s very difficult to find anything untrue in the CSRB’s scathing report regarding the situation. In short, the CSRB found that the breach was preventable, and should not have happened.
We’ll continue to post updates here and via the podcast as more is learned. Time will tell if Microsoft follows through with the claim.
The UK’s Product Security and Telecommunications Infrastructure Act (PSTI)
It’s rare that good news is seen in the cybersecurity industry, and there are many the new PSTI law in the UK as a good thing for the industry. The Product Security and Telecommunications Infrastructure Act (PSTI), is a new law that was recently enacted in the UK, that focuses on a number of key initiatives. While there are several controls and regulations put into place as part of this act, three of the most high-profile ones are listed below in an abridged format:
Passwords
– Passwords must be unique per product; or capable of being defined by the user of the product.
Information on how to report security issues
– The manufacturer must provide information on how to report to them security issues about their product. The manufacturer must also provide information on the timescales within which an acknowledgment of the receipt of the report and status updates until the resolution of the reported security issues can be expected by person making the report.
Information on minimum security update periods
– Information on minimum security update periods must be published and made available to the consumer in a clear accessible and transparent manner. This must be the minimum length of time security updates will be provided along with an end date.
On the surface this appears to apply to only devices within the UK, but the bill states that the rules apply to anyone that is importing or selling applicable products within the UK. Failure to comply will cost offending organizations 10 million British Pounds or 4% of worldwide revenue (Highest of the two). So, not only does this law have far-reaching implications for the industry as a whole, it’s a law that has real teeth on it. It’s a sad fact that some vendors within the technology sector often drag their feet on following security best practices UNLESS made to do so by some outside force. This law does just that. It’s clear, we’re continuing to see the growing loss of patience of world governments where security breaches are concerned. This won’t be the last law of its kind we see.
The end results, however, will be a net positive. More secure devices – with more transparency for end customers. A win-win.
Change Healthcare Confirms Ransomware Payment
A short update on this particular point. In February, the Healthcare organization in the US known as Change Healthcare suffered a massive cyberattack that left the company crippled and unable to provide critical services to the US Healthcare industry. If you’d like more details on the attack, we discussed it in a recent episode of The Security Swarm Podcast We reported in previous monthly threat reports that it appeared that the change healthcare had paid the ransom. This was suspected as it was clear to blockchain experts that a large payment had been funneled through to known threat-actors.
Well, as of this month we have confirmation that Change Healthcare had indeed paid a $22 Million USD ransom to the threat actor group BlackCat. While it’s considered a bad practice to enable threat actor groups by paying up, this was far from a normal ransomware situation. Change Healthcare held a critical position in the US Healthcare industry, and with services down, clinics and pharmacies across the country were unable to process medical payments, issue prescription medication…and more. There was a very real and potentially dangerous human impact to this breach and is likely part of the reason for the staggering payment.
Predictions for the Coming Months
- It’s possible we’ll see a slower release cadence from Microsoft in the coming months as the company moves its focus to security issues. Many will see a slower cadence as a good thing, and better security from the cloud provider is only a net-increase for the industry.
- The UK’s PSTI Act may have taken device manufacturers by surprise. There was very little information in the news leading up to the law’s signing. In the short term we may see some organizations temporarily cease operations in the UK until they’re able to comply with the new guidelines. That said, any pause is likely to be short lived as most organizations will not want to leave the UK market to their competitors.
- Email-based trends are likely to continue a slight downward trend as we head towards the summer months.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Andy Syrewicze, Security Evangelist, on Good News in the Cybersecurity Space:
So frequently we have to discuss bad news in this report, and that goes with the territory, right? It’s not very often that we’re able to share good news about the industry, and so I was happy to see the news about Microsoft’s new commitment to security as well as the new law from the UK regarding device security standards. Both are a net benefit for the industry and will make us all more secure. My only complaint is the fact that vendors often need to be forced in some way to do the right thing with regards to security best practices. Positive changes like those we saw this month help set the trend in the right direction and make me hopeful for the future.
From Umut Alemdar, Head of Security Lab, on Increasing Security Threats:
While April brought positive cybersecurity developments, including Microsoft’s commitments and the UK’s PSTI Act, the threat landscape remains volatile. News of state-sponsored espionage reached alarming heights, with targeted attacks against European politicians revealing widespread security vulnerabilities in political organizations.
Furthermore, threat actors are increasingly weaponizing advanced AI language models to generate convincingly deceptive phishing emails, imitating trusted individuals. This tactic demands heightened vigilance, looking beyond basic errors and scrutinizing unusual requests or changes in tone. The threat group “Kimsuky” exemplifies this trend, using AI to craft attacks and optimize malicious operations within compromised systems using troubleshooting prompts.
With the escalating level of cybersecurity threats, we must no longer consider continuous security awareness training and cutting-edge cybersecurity defense mechanisms optional luxuries but essential elements of organizational resilience and preparedness.
Monthly Recommendations from the Hornetsecurity Security Lab
- Don’t be fooled by the slight decline in email-based threats. The rise of generative AI tools like ChatGPT has made crafting convincing and elusive phishing emails easier than ever. In our newly published eBook, “How to Spot Phishing in the Age of AI,” we provide crucial tips on how to protect yourself from such attacks and shed light on current threats.
- With May 2nd being world password day, be sure to review your organizations password practices. Update policies with current recommendations and continue to communicate good password hygiene to end users.
- If you have any IOT devices within your organization, now is a good time to verify that they aren’t using default password settings and that they are properly isolated from your core production environments.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.


