

Defending Your Organization Against Whaling Phishing
Do you hold a high-authority position within your organization, such as a C-level executive like CEO, CTO, CFO, CMO, and CLO? If so, this article is written to assist you in navigating through phishing attacks that target profiles of individuals in your role. It is called whaling phishing.
Phishing is one of the most common ways to spread malware by tricking people to open malicious URLs or attachments. It only takes a second of tiredness and unconscious clicking on the link or attachment within our inbox. At first glance, that link or attachment might seem legitimate, but what is behind it is often what puts our organizations in chaos.
In this article, we will discuss phishing attacks, with a focus on whaling attempts. We’ll cover how to identify them, how they operate, and the most effective methods to combat these attacks.
Let’s start by breaking down the fundamentals.
What Is a Phishing Attack?
Phishing is the malicious practice of tricking people into revealing sensitive personal or business information (credentials, credit cards, or similar). Attackers create or design phishing emails in such a way that they are challenging to distinguish from legitimate emails.
According to our research from 2023, phishing attacks remain number one on the list at 39.6%. It is very often combined with other malware such as HTML, URL, PDF, and executables.
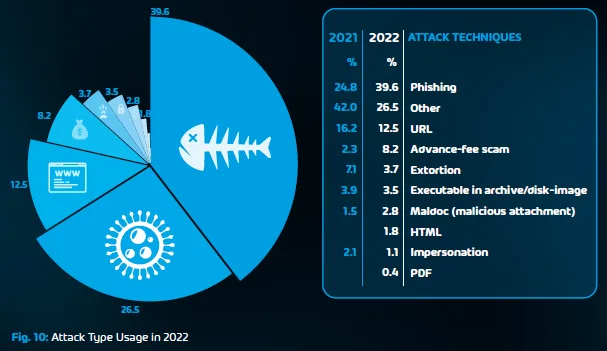
Also, according to Ransomware Attacks Survey 2022, nearly 6 in 10 ransomware attacks (58.6%) originated from malicious email or phishing attacks.
What are the types of phishing attacks?
There are different types of phishing attacks and their variations, but they all share one common goal: tricking us to open harmful links or attachments. The thing that sets them apart is how they spread and who they’re trying to target.
That includes spear phishing, whaling phishing, angler phishing, pharming, pop-up phishing, and others. Spear phishing and whaling phishing are about who the targets are. Spear phishing targets regular employees while whaling phishing targets high-profile employees, such as C-level executives.
What Is Whaling Phishing?
The whale is often seen as the king of the ocean, representing a symbol of high authority. In terms of phishing, a whale refers to C-level executives. C-level executives hold significant authority within an organization, and the metaphor draws a parallel between these powerful individuals and the whale in the ocean.
With their authority, C-level executives become targets for whaling attacks, which aim to deceive and exploit them due to their access to sensitive information and decision-making power. When the CEO asks for an urgent request from employees, they usually get it. Isn’t it?
There are two data breaches involving whaling phishing we would like to share with you. One happened at Seagate in 2016 when a group of hackers compromised the payrolls and tax information of approximately 10,000 current and former employees. In this case, the attackers targeted the HR department by impersonating a CEO.
The second attack occurred in 2016 during the FACC Cyber Heist, where attackers tricked the finance department into transferring almost 42 million € to their accounts. They used the same trick, impersonating a CEO. The money was never recovered. The CEO was fired.
How Whaling Phishing Is Distributed
As with any phishing attack, whaling phishing is distributed via email, SMS, and voice. Let’s explore them through real-world examples.
Email phishing
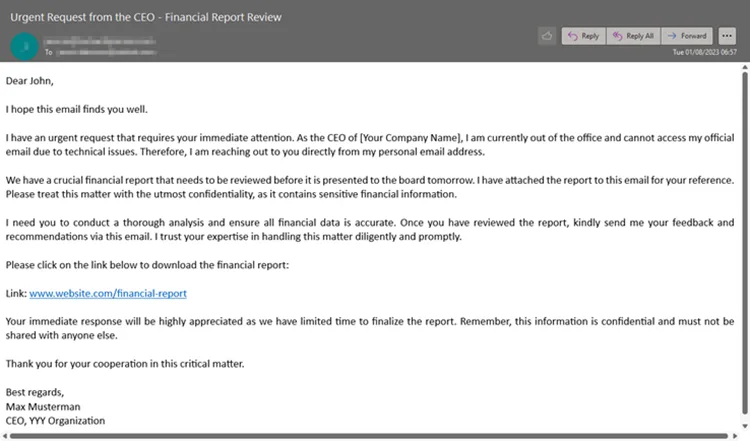
According to our Cyber Security Report 2023, email continues to be the primary mechanism of communication for many organizations, with 333.2 billion emails sent every day. That is exactly how whaling phishing attacks are being spread. Attackers create deceptive emails, pretending to be CxO, and ask you to share payroll, tax information, or the latest project plan.
Smishing (SMS Phishing)
Smishing (SMS Phishing) is a type of attack where attackers use SMS text messages to trick the victim. For example, attackers impersonate a CEO and ask the Finance representative to make important payments ASAP. Here is an example of an SMS Message.
“URGENT: Hey John – I’m in a meeting right now, and we need to make an important payment ASAP. Please reply with the company credit card details, including the CVV, so I can proceed. Thanks.”
Never do this. Your CEO would never ask you to send credit card details via SMS.
Vishing (Voice Phishing)
Vishing (Voice Phishing) is tricking people via phone. Here is one example.
Attacker (impersonating a CEO): Hello, this is Max Musterman, CEO of YYY organization. I am calling your (HR) department as I need your urgent assistance. May I know whom I am speaking to?
Employee (Victim): My name is John, working as an HR representative. How can I assist you?
Attacker (impersonating a CEO): We are analyzing the investments we make for salaries. As all systems are down, including email, I would like to ask you to send me the payroll report for all employees to my private email ([email protected]). Would that be okay for you, please?
Employee (Victim): Sure. You will have it soon in your inbox.
Why do you think the employee promptly shared details with the CEO in his private email?
In this voice phishing attack, the attacker gained access to legitimate information that the company had publicly disclosed. The company had a system outage due to a bandwidth issue, which they publicly shared with their customers. Taking advantage of this situation, the attacker successfully deceived the HR representative.
That was a social engineering and phishing attack!
There are also other variations of how phishing can be delivered, including QR code scams. Stay safe by reading more here: All You Need to Know About QR Code Scams.
How Whaling Phishing Attacks Work
There are three different phases in the phishing attack that are also applicable to the whaling attack.
- First, an attacker would do research about the potential target, his role in the company, and his relationship with other employees.
- Secondly, based on the data the attacker has found, he will create a tailored phishing email that looks like a legitimate email. Remember from the previous part, that is how HR and Finance departments from Seagate and FACC Cyber Heist were tricked.
- From there, the attacker will attempt to deceive and convince the target into clicking on the link or attachment to gain access to the system. Once the victim clicks on the link, the attacker will need to bypass security measures, inject a malicious payload, and ultimately steal data and sensitive information.
Examples of Whaling Attacks
When we examine the examples of whaling attacks, we can identify a few. The first one would be CEO Fraud, where the attacker impersonates the CEO and asks lower management to share sensitive information or make an urgent payment.
The second example could involve an impersonated board member. The attacker might send an email to the CEO and request sensitive information about projects, financial plans, growth strategies, or other business strategies.
Another type involves targeting vendors or partners. The attacker pretends to be a trusted partner with whom the organization regularly interacts and asks for the latest project plan, changes to the payment plan, account information, or similar details.
Some other examples may target the legal team, finance team, HR, marketing, IT department, executive assistant, and others.
Detecting a Whaling Attack
There are two crucial factors here. The first one is to have proper IT security tools and hardened systems that follow security best practices. The second factor is to have continuous security training, which will help CxOs recognize whaling phishing attacks and forward them to the IT team for analysis.
Here are some potential red flags that lead to suspicion:
Check the email address
Even if the name in the email address appears to be that of a CxO, upon closer examination, you may notice that the actual email address is different, indicating a possible phishing attempt. Also, keep an eye on the domain name; for example, @Company.com is not the same as @Company.net.
Check the email content
Have you ever received this kind of request before? Pay attention to the tone and language of the email. Are there any grammatical errors? All of these can be red flags.
Urgent actions are needed
Phishing, including whaling attacks, often employs urgency to pressure you into immediate action. Don’t fall for it; take your time to verify the request before proceeding.
Flag external emails
You can use security tools to flag external emails, giving you a heads-up that you should pay attention to. This helps against partner and vendor fraud.
Report whaling attempts
You should use tools to report whaling phishing emails to IT for further analysis. This helps enhance the infrastructure, create reports, and learn from new incidents.
Being aware of these red flags can help protect against whaling phishing attacks.
How to Protect Your Organization From Whaling Phishing With Hornetsecurity
Phishing is created and sent by malicious actors, but we often end up clicking on it due to human error. According to the World Economic Forum – The Global Risks Report 2022, 95% of all cybersecurity incidents are caused by human error. So, if we train CxOs and our end users, this number will definitely decrease. Do you agree?
Here at Hornetsecurity, we have developed a Security Awareness Service to help you train your CxOs on how to stay safe. Our system can assist you in creating realistic whaling phishing attacks for training purposes.
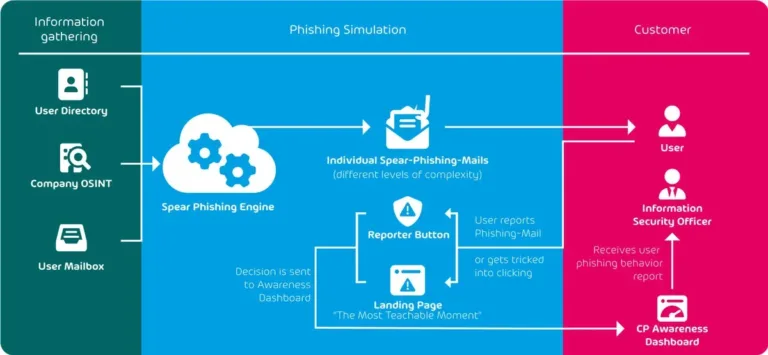
You can also use the awareness dashboard to track your CxOs’ progress. The awareness dashboard can be customized based on your organization’s needs, and it provides real-time monitoring, ESI reporting with history and forecasts. ESI stands for Employee Security Index and helps determine the level of security within the organization.
The Security Awareness Platform also includes a security hub with all learning materials to increase security awareness. It offers an evaluation of each user’s individual phishing simulation, a gamification approach, and learning content available in multiple languages.
For an overall look at cybersecurity risks gained from analyzing 25 billion emails, see our free Cyber Security Report 2023.
To properly protect your cyber environment, use Hornetsecurity Security Awareness Service to train your employees in deterring cyber threats and securing your critical data.
We work hard perpetually to give our customers confidence in their Spam & Malware Protection, Email Encryption, and Email Continuity strategies.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Wrap Up
Phishing attack is one of the most common techniques to trick people into opening harmful links or attachments. It has different variations, and one of them is whaling phishing. Whaling phishing targets profiles of high authority, including C-executives.
It is spread via email, SMS, and voice, and it sounds convincing since it comes from the higher levels in the organization. One of the best ways to prepare your CxO level against whaling phishing is to train them. You can do this by simulating whaling phishing attacks in Hornetsecurity.
This article explains phishing attacks with an emphasis on whaling attacks, discussing the various ways they are spread and how you can secure your data against them.
FAQ
Whaling represents a prevalent cyber-attack strategy wherein attackers employ sophisticated spear phishing techniques to target prominent and significant individuals, often aiming at top-tier (C-level) executives within an organization.
Spear phishing is a targeted cyber-attack that singles out a particular group of individuals. In contrast, whaling directs its efforts toward key executives within an organization. Spear phishing primarily aims to pilfer login credentials and sensitive information. On the other hand, Whaling sets its sights on acquiring confidential trade secrets capable of significantly impacting a company’s overall performance.
Here are the top three examples of whaling phishing:
Unencrypted Email Conversation Interception – Cybercriminals can seize and disrupt unencrypted email exchanges to redirect substantial bank transfers.
Malicious Meeting Invitation – Employing a deceptive tactic, attackers might arrange a fictitious meeting while embedding a malware link masked as a Zoom link.
Deceptive Payroll Data Request – Cyber attackers could pose as legitimate sources, requesting confidential payroll details for present and former employees, potentially leading to identity theft and fraud.
Also recognized as CEO fraud, whaling resembles phishing as it employs techniques like email and website spoofing. These tactics are utilized to deceive a target into carrying out particular actions, such as disclosing sensitive information or executing money transfers.
– Perform Security Awareness Training for employees
– Utilize Two-Factor Authentication (2FA)
– Email filtering and verification
– Validation of email addresses
– Exercise caution regarding urgency
– Implement Security Policies
