

Cyber Security Facts You Wish You Knew Earlier
The world of cyber security facts is filled with surprises. Did you know that 95% of breaches are caused by human error? Or that 70%+ of attacks are financially motivated, with less than 5% coming from espionage? It might sound unusual, but these are some of the cybersecurity facts we wish we had known sooner.
In this article we’ll dive into interesting statistics to help us understand the cyber security facts shaping business approaches to security and what you can do to protect your organization.
Cyber Security Facts
If you had to guess which cyber-attack flavor cost businesses the most money globally, most people would have said ransomware. It’s in the news (although only the gigantic ones make mainstream news nowadays), and most people remember the Colonial Pipeline attack shutting down gas access for the Eastern seaboard of the US for several days.
That particular attack seems to have been the one bringing ransomware into everyone’s awareness. Up until last year, ransomware was however NOT the biggest cash cow for the criminals, it was Business Email Compromise (BEC), and only last year (according to FBI’s latest report) was BEC overtaken by financial fraud.
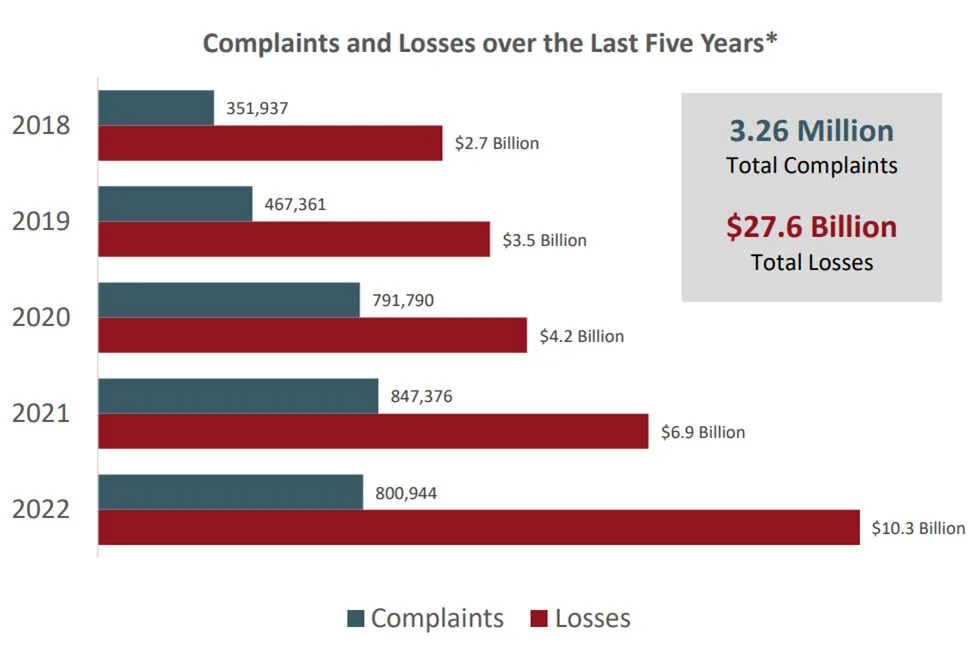
The total loss (of the reported statistics in the FBI report) for BEC was $2.7 billion in 2022, compared to $3.31 billion for financial fraud. The culprit here is clearly cryptocurrency scams, accounting for $907 million in 2021, and a whopping $2.57 billion in 2022. Total loss to all cybercrime in 2022 was $10.3 billion.
But those cyber security facts from the FBI are only the tip of the iceberg. Mandatory reporting is still far from ubiquitous globally so many crimes go unreported.
When a business falls victim to ransomware, the average cost of recovery is exceedingly high. In this scenario, simply paying the ransom won’t miraculously restore your systems to a functional state. Moreover, there’s no guarantee that the criminals will return your vital data.
How much are the bad guys making on ransomware? Chainalysis’s mid-2023 update indicates that they’ve extorted at least $449.1 million in the first half of 2023, and on track for about $898.6 million for the whole year.
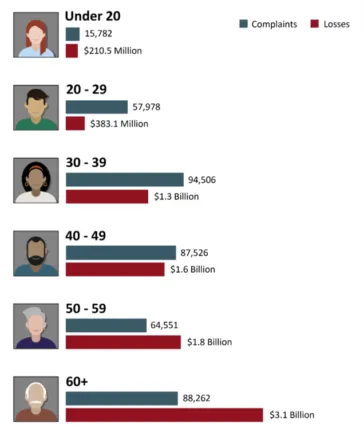
A scary cyber security fact in the FBI report is the age of the victims. The most targeted are the ones less likely to be familiar with technology and cyber security overall – the older generation.
Another surprising cyber security fact for many people is that your password doesn’t matter. For many years we’ve been advocating for long, complex passwords, that must be changed frequently. Turns out that all of that was misleading, and just incentivizes users to use the same password on every site (because who can remember a different password for each service), and then adding a number or month to the end when they are forced to change it.
This password re-use leads to considerable danger when a low security site, with no sensitive data, is breached, and the criminals then take those usernames and passwords and try them against your critical business services.
The solution here is moving away from passwords to passwordless, FIDO2 hardware keys or strong biometrics such as Windows Hello for Business. On the way to passwordless nirvana, make sure every user uses MFA, preferably with an app on their phone.
Barbarians at the gate
According to Verizon’s latest Data Breach Investigations Report (DBIR) 83% of breaches involved external actors. That means that slightly less than 1/5th of data breaches are insider jobs. This has been reflected in other reports and it’s a risk most businesses don’t take seriously enough. Having a strong insider risk program is crucial, and it needs to be based on more than just Data Loss Prevention (DLP) technical controls.
Remember, insider risks is a spectrum from someone inadvertently breaking a rule about emailing business data to a personal email address “to work at it over the weekend”, to inappropriate language, to harassment, to theft of intellectual property or sabotage.
A recent example is a UK IT security analyst whose company was hit by ransomware. He set up an email address that closely mimicked the attackers, and then changed the Bitcoin address for the ransom payment.
Insider risks are real, and your organization needs to have a good program in place to manage it.
Attributing attackers to specific countries isn’t always easy but it’s no surprise that the top four are Russia, China, Iran, North Korea according to Microsoft’s Digital Defense Report 2022.
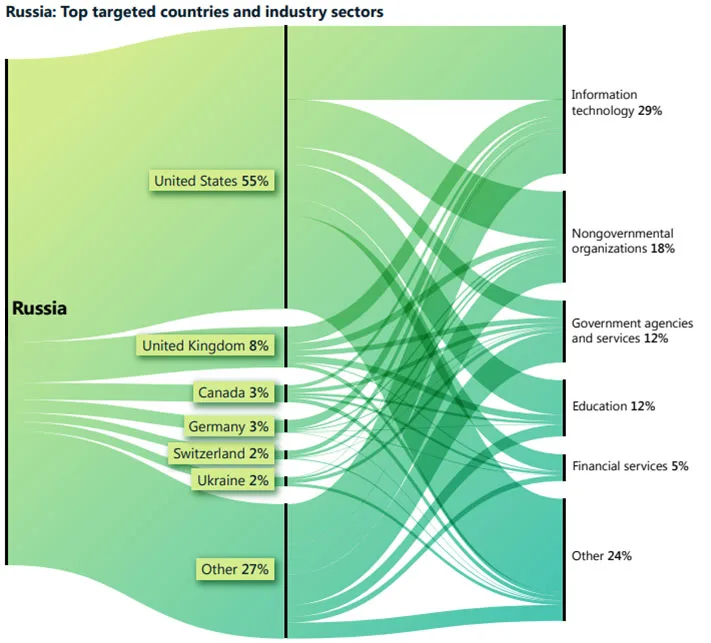
That report also focuses on cyber influence operations – misinformation and disinformation. You’ll find two approaches here, one disseminating false or misleading information, and the other simply flooding the information space with different stories, leading to an inability to even spot the true signal in the noise.
Another interesting cyber security statistics in the DDR looked at characteristics of organizations that suffered a ransomware attack. 68% of those business didn’t have an effective vulnerability and patch management process, 60% didn’t use Endpoint Detection and Response (EDR), 60% didn’t have a SIEM, 76% lacked an effective response plan, 44% didn’t have immutable backups, and 92% didn’t have an effective DLP solution.
In our own 2022 survey we found that 1 in 20 companies had a ransomware attack, wherein 14.1% lost data, and 6.6% had to pay the ransom. The vector for initial breach was overwhelmingly email / phishing at 58.6%, followed by compromised endpoints at 16.4%. It’s crucial to combine a strong email security hygiene solution to keep most malicious emails out of users’ inboxes, with regular user training to not fall for the few that do end up in their inboxes.
An interesting find is that 86% of ransomware cases involve the threat of leaking the exfiltrated data. Often called double extortion, this combines encrypting the data in the first place, making it inaccessible to your business (unless you pay to get the decryption key), plus threatening to make the stolen data public.
There are even cases where attackers skip the encryption phase, and simply threaten to leak the data. How efficient this is a threat will vary between industries, the company that was breached and the nature of the data itself. Some businesses aren’t likely to pay, whereas others not only can’t afford to have the data leak, but they may also face legal and regulatory consequences if the data is made public.
Another interesting change we’ve seen recently is the shift from “brand name” ransomware actors, to smaller groups (it’s mostly the same people, with shifting loyalties) because those known names often end up on sanctions lists, particularly if they’re in Russia, disincentivizing businesses from paying in the first place.
The takeaway here is to apply a zero-trust approach to securing your business, verifying each connection and authentication. Also, applying policies to only allow connections from managed devices is a good idea, or at least enforce stricter policies for personal devices.
How to Protect Yourself from Cyberattacks
Given the picture these “fun” cyber security facts paints, let’s see how you can protect your business.
Since the primary vector for the initial foothold are phishing emails, ensuring that as many of those as possible never reaches your users’ inboxes is vital – using a competent, cloud based (for swift updates), machine learning-based, email hygiene solution is step one. No protection will catch 100% of all emails however, and thus you need to train your users to spot suspicious emails – improving your “human firewalls”.
This training must be ongoing, an hour once a year is soon forgotten and results in very little behavioral change, phishing simulations on the other hand are much more impactful. These are mimicked phishing emails, but instead of a compromise when a user clicks the link or opens the attachment, they get a reminder of the risks and are then scheduled for short video trainings to spot the suspicious signs next time around.
A huge benefit of Hornetsecurity’s Security Awareness Service is that it automates the targeting, and scheduling of training based on each user’s Employee Security Index (ESI), relieving an already stretched IT team from the burden of scheduling simulations and training.
Next, consider adopting a Zero Trust approach to security:
- Verify explicitly
- Least privilege access
- Assume breach
In other words, check every authentication and connection against a policy engine – don’t assume that because the connection is on a trusted network, it’s safe. Once a user is connected to a service or data, they should only have the access they need.
Build your cyber security approach on the assumption that despite your great defenses and well trained “human firewalls”, sooner or later an attacker will get in. Have strong security tools in place for visibility so you can catch them before they get too far in your network.
Finally, don’t get complacent, secure is not a destination, it’s a never-ending journey, and eternal vigilance is the price of not being compromised.
For an overall look at cybersecurity risks gained from analyzing 25 billion emails, see our free Cyber Security Report 2023.
To properly protect and train your employees against cyber security threats, use Hornetsecurity Security Awareness Service as we work hard perpetually to give our customers confidence in their Spam & Malware Protection and Advanced Threat Protection strategies.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
That’s it, these are the well-known cyber security facts and cybersecurity statistics that you probably didn’t know.
Hopefully you found some interesting cyber security facts that you didn’t know here, as well as gained some insights into how to better protect your users against threats. Stay safe out there.
FAQ
Basically, 4000 new cyber attacks occur every day. Every 13 seconds, a company becomes a target of a ransomware attack, which can result in significant financial hardships, while 600,000 new malware instances are detected daily.
Here are the top three facts about cybersecurity:
About 95 percent of data breaches are directly the result of human errors.
A study called “Daily Trends and Origin of Computer-Focused Crimes” found that at least 1 Cyber-attack happens every 39 seconds.
Nearly 40 percent of the businesses in the UK have experienced an attack in the year 2023.
It’s early to give the proper answer, but still, AI will transform cybersecurity by enhancing threat detection, automating specific tasks, and delivering valuable insights. Yet, it is unlikely to replace the human factor in cybersecurity.

