

Business Email Compromise (BEC)
A tried and tested form of attack with a new look
In this article, we look at how BEC attacks work, common attack types such as CEO fraud and vendor compromise, and the increasing financial damage they cause. We also discuss the risks to businesses of all sizes, and the best strategies to protect your organisation from falling victim to these attacks.
Table of Contents
What is Business Email compromise (BEC)?
Business Email Compromise (BEC) is characterized according to its different forms. In addition to compromising an employee’s email account, methods such as spear phishing or CEO fraud are also used, the latter being preferred by criminals for gaining access to confidential company information or money. Companies are often taken for six-, seven- or even eight-digit sums. This happened in 2016 at a well-known Nuremberg-based auto parts supplier, and the damage was about 40 million euros. (Source: Heise article from 08.16.2016)
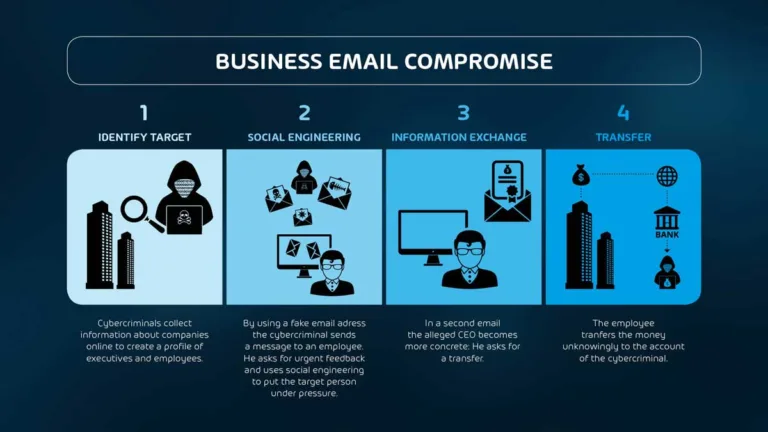
The approach of the BEC authors is almost always the same, with the difference that not only are seemingly credible emails used, but ever more malware is added to the attacks.
BEC typically targets a single individual, usually someone who has influence within the organization or directly manages the budget. A successful attack relies on the targeted individual engaging with a seemingly legitimate email from an internal supervisor or colleague, or an external partner or vendor, and either clicking a link or providing login credentials to the perpetrator.
Business email compromise is on the rise
According to the latest FBI figures, email fraud has risen in recent months. In fact, the total damage caused to businesses by cybercriminals in the past five years has been more than $5.3 billion. This represents an increase of more than 2.3 percent. (Source: FBI Statement of 05.04.2017 on Business Email Compromise)
Germany’s BKA warns about cybercriminals causing damages in the hundreds of millions. In 2016 alone, the official figures cite around 83,000 such incidents (source: Cybercrime Bundeslagebild 2016). However, the true figure is likely to be much higher. Worse still is the fear that an incident of this type can lead companies to have an impact on the outside world.
Between 2019 and 2021, the FBI reported that global exposed losses from BEC attacks increased by 65 percent. This equates to $43 billion in losses in less than three years. Naturally, the financial losses of a successful BEC attack are what drive most organizations to take preventative action.
Often overlooked consequences include damaged consumer trust, as well as a diminished brand reputation. When word gets out that your company’s security posture isn’t adequate, prospective clients won’t hesitate to look elsewhere for assistance.
Common BEC Attack Types
- Gift card fraud
The hacker asks an employee to purchase gift cards for staff or customers. Often, the hacker will ask for secrecy and direct the employee to send screenshots of the back of the gift cards, rather than the actual gift cards. - CEO fraud
One of the most expensive forms of business email compromise, this attack involves CEO or executive impersonation. The hacker will ask for secrecy and urge the employee to take some kind of financial action, often requesting a wire transfer of a large sum of money. - Vendor compromise
A hacker compromises a vendor’s account and then uses that account to phish or spear phish the vendor’s customers. This scheme allows hackers to receive quick payouts from victims who believe they are paying legitimate vendor invoices. - Tax fraud
A hacker typically impersonates an employee and reaches out to a member of an HR team, requesting a copy of a W2 or other income statement form.
Business Email Compromise Often Consists of an Additional Ransomware Attack
As already mentioned, the perpetrators mainly focus on financial goals. Depending on the attack pattern, the amount of money captured varies.
Perpetrators intelligently design their actions. In order to find out whether a company can be blackmailed or what the liquidity situation of the target company is, the ransom money is first blackmailed through a ransomware attack. If this attack turns out to be useful to the perpetrators, an additional spearfishing attack may follow. .
Business Email Compromise – It’s Not Just A Matter Company Size
Using Business Email Compromise (BEC), authors are not limited solely to attacking large companies because employees are often the target of attack. According to IT industry association Bitkom, 60% of Internet users are not aware of what polymorphic viruses are and that makes them a highly attractive target. (Source: Bitkom press release dated 05.12.2017)
And while 41% of Internet users who have been exposed to ransomware know the dangers of such an attack, they do not want to take active security measures. This shows that some knowledge is there, but its effect is minimized. After all, most people believe that it always affects others and that their own companies are unlikely to be the target of cybercriminals.
In reality, this assumption doesn’t take into account the number of unreported cases. Such information is rarely communicated to the public by the affected companies.
Furthermore, the perpetrators are no longer the technically clever individuals who want to earn a few extra bucks. Rather, it turns out this new breed of professional attackers choose cybercrime primarily because they consider it extremely lucrative. This applies in particular to Business Email Compromise (BEC).
What counts? Speed!
There are protection mechanisms that defend companies from a case as serious as this one. However, a firewall or an antivirus program is not one of them. Special forms of attack require specific defense mechanisms, which in such cases must take effect particularly quickly.
Especially those companies that are not very familiar with the implementation of security mechanisms of this type should consider the use of Managed Security Services. Outsourcing IT security is the magic word – because this is the only way to reduce the imbalance between the expertise of cybercriminals and the businesses they prey upon.
In order to minimize the likelihood of your organisation falling prone to business email compromise, educate your employees on BEC awareness and prevention. An effective cybersecurity awareness training program can help build a culture of cyber vigilance and risk mitigation.
On top of that, implementing anti-spear phishing solutions that use a core set of AI technologies like Natural Language Processing and sender spoofing algorithms can help safeguard against spear-phishing attacks and strengthen your front-line defenses.
Automated cloud-based processes and innovative technology that reliably protects businesses against complex cyberattacks – a solution offered by Hornetsecurity. With Advanced Threat Protection (ATP), we are able to sustainably contain Business Email Compromise (BEC). In this way, we protect our clients not only against CEO fraud, but also against ransomware attacks and phishing attacks.
Learn about HORNETSECURITY’S SERVICES
Interested in Related Topics?
Did you like our contribution to Business Email Compromise? Then other articles in our knowledge base might interest you as well! We help you learn more about cybersecurity related topics such as Emotet, Trojans, IT Security, Cryptolocker Ransomware, Phishing, GoBD, Cyber Kill Chain and Computer Worms.


