

NIS2 Directive: Decoding its Significance and Implications
We all have been witnessing the growing threats associated with increasing digitalization and the number of cyberattacks.
As early as 2016, the European Union recognized that this was a major challenge for organizations and citizens and introduced NIS (Network and Information Security) security measures.
The idea was to improve the cybersecurity capabilities of networks and infrastructure systems in seven sectors, including energy, transport, banking, financial markets, healthcare, drinking water, and digital infrastructure.
As cybersecurity continues evolving, NIS EU legislation has had to be improved and security measures increased. For example, the Hornetsecurity Security Report, shows that phishing retains its top spot, accounting for 43.3% of email-based attacks.
In 2023, the European Union adopted the second version of the Network and Information Systems Directive (NIS2) and improved the security measures.
This article is about NIS2, what the regulation requires, a high-level overview of steps you should take now in your organization, and how Hornetsecurity’s various products can help you.
NIS vs NIS2
The main difference between NIS and NIS2 lies in the expanded industry sectors that are covered by NIS2, the adding of “teeth” in the form of sizeable fines, as well as the size of businesses that are in scope (see below).
NIS is aimed at essential services and providers of digital services. Essential services include the three sectors; water, transport, and energy, and digital services include cloud computing, marketplaces, and search engines.
With NIS2 legislation, the European Union expanded the scope and categorized it into essential entities and important service entities. Essential entities were already part of NIS, but NIS2 has expanded the scope of the sectors covered.
This means that more organizations in the European Union are subject to NIS2 requirements.
New in NIS2 are important service entities that cover additional areas.
Some of the industries that will now be affected by NIS2 as important service entities are healthcare, transport, finance, water supply, waste management, energy, digital infrastructure, and service providers, public electronic communications service providers, food industry, aerospace, postal and courier services, and public administration.
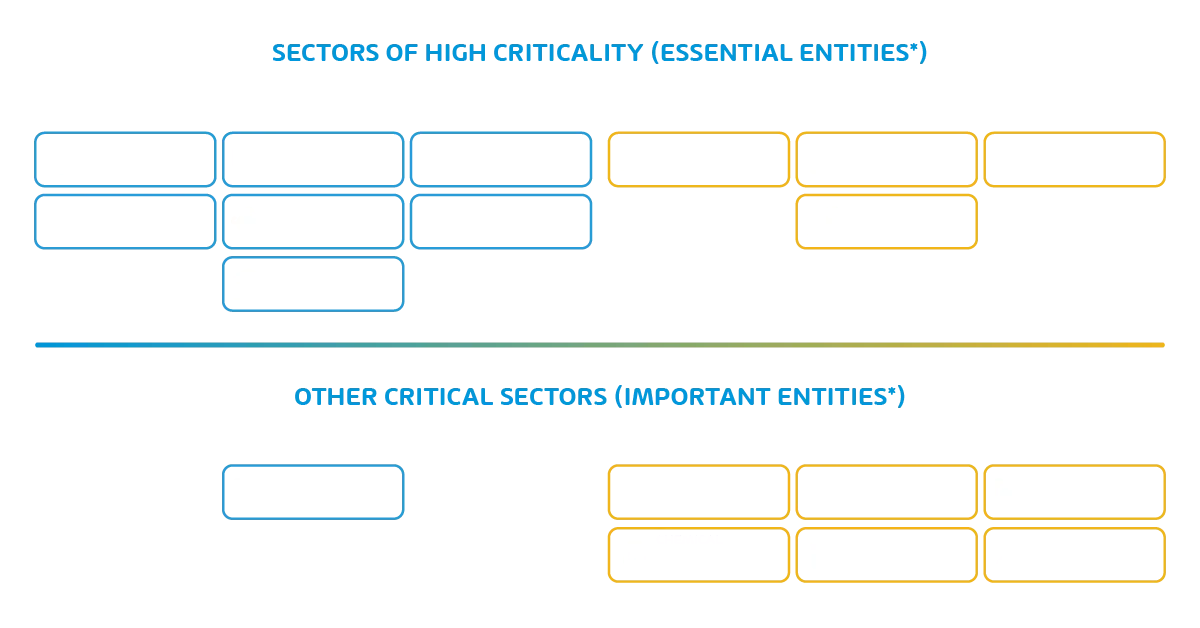
*Essential entities will be supervised pro-actively AND re-actively
*Important entities will only be supervised re-actively
**NIS2 sectors include both sectors already covered in NIS plus new added sectors
NIS2 legislation updates and modernizes the older framework and improves required resilience and incident response for private and public entities.
What is the difference between essential and important?
In addition to the extended sector, there are two other differences. Essential entities must meet the requirements of the supervisory authority, while important entities must meet the requirements of the ex-post supervisory authority.
The ex-post supervisory authority means that action will only be taken if the supervisory authority receives evidence of non-compliance.
Who is Affected by NIS2?
The NIS2 concerns organizations of very different sizes. In NIS, only medium-sized and large organizations were affected; in the NIS2, smaller organizations are now in scope.
This means that smaller organizations with a turnover of over €10 million+ or 50 employees+ must now also comply with the regulations.
NIS2: Four Key Areas
There are four key areas addressed in the NIS2 legislation. These include reporting obligations, risk management, management obligations and governance, and enforcement and sanctions.
Step one for you, however, is to carefully read the NIS2 Directive (which will be implemented as law in your EU country by October 2024) to ascertain whether your organization is covered by the expanded set of industries or not. If your business is in scope, you must start taking steps today to become compliant, and Hornetsecurity can help.
Second, like with any compliance regulation, start by:
- Identify risk factors to your ongoing operation.
- Document each of the risk factors.
- Plan mitigations for each risk.
- Gather proof for how these mitigations are implemented and verified.
Let’s look at each of the four key areas of NIS2.#
Reporting Obligations
If a company suspects a serious security incident, such as a data breach, unauthorized access, supply chain attack, and the like, it must report it within 24 hours. Then, within 72 hours, the company must provide a detailed assessment to the supervisory authority of the impact on its infrastructure and data.
The story doesn’t end there, however.
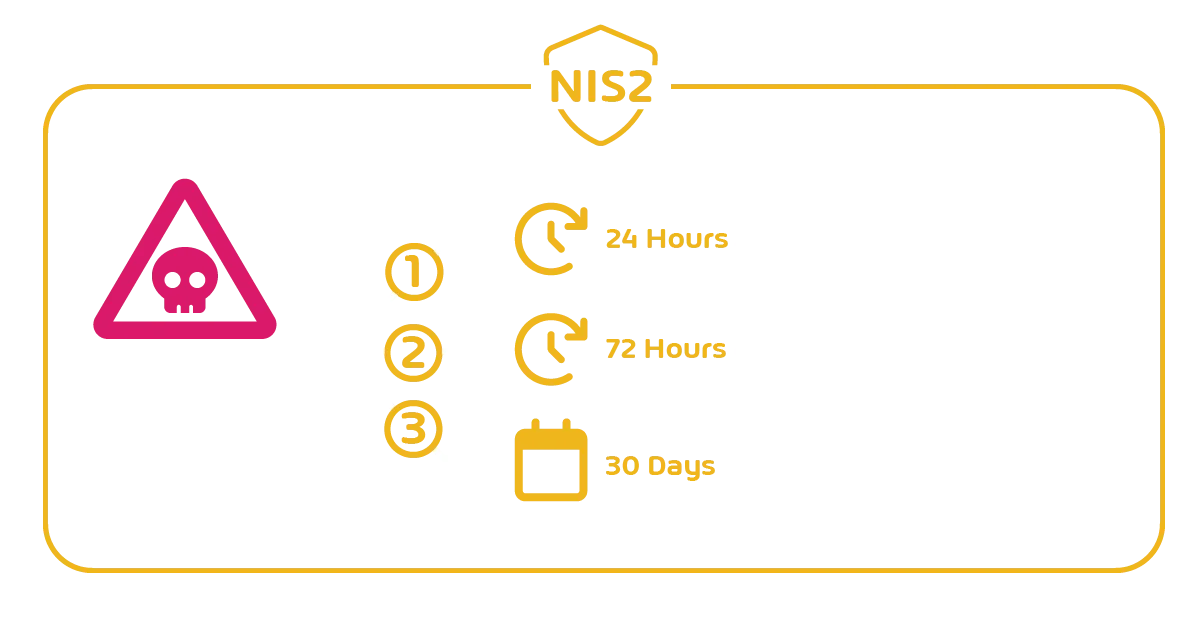
After the initial report is submitted within the first 24 hours, the company has one month to submit a final report to the supervisory authority. The final report should include full details of how the incident occurred, the impact it had on the company, and the actions taken by the organization.
If you have had any experience with Incident Response (IR) in a cyber security situation, you know that 24 hours is a very challenging deadline. In the first few hours / days of a major breach, there’s a lot of heightened emotions and stress as you work to identify exactly what systems have been affected, where the initial foothold was established, if any sensitive personal or business data has been stolen, recover systems and start formulating a plan to evict the attackers. Especially for smaller organizations that may not have had experience with this, this will be a very challenging time.
One way to ensure compliance is to review your incident response plan, and make sure you have all lines of communication established.
Since you need to report to your supervisory authority, make sure to include how to do this in your incident response plan. If you’re a smaller organization where you may not have a dedicated incident response team, or even a cyber security team, make sure to establish commercial relationships with at least one incident response company, so that you can call on them quickly. You don’t want to be Googling who to call when the breach is in progress.
Don’t forget the additional details that are due within 72 hours, and the details needed for it – again prepare your organization with templates so that you’re ready for it.
Hornetsecurity’s 365 Total Protection Enterprise will help you here if the initial attack vector was email borne (which is the most common way), if it didn’t stop the attack, it can provide immutable retention of all emails in Archiving and email header analysis in Control Panel.
Risk Management
Risk management is a second area within the NIS2 legislation.
Risk management is the process of identifying, assessing, preventing, and mitigating potential risks that an organization may face. Article 21 of NIS2 legislation defines risk management measures to strengthen the security posture of the business.
They include the following:
Policies and procedures regarding the use of cryptography and, where appropriate, encryption. The use of cryptography and encryption helps to ensure the Confidentiality, Integrity, and Authenticity (CIA) of data. Hornetsecurity offers powerful, easy to use email encryption.
Policies and procedures to assess the effectiveness of cybersecurity risk-management measures. These policies and procedures help organizations follow a structured approach and manage improvements over time.
Incident handling covers the detection and prevention of cybersecurity incidents.
Business continuity means proper backup management, disaster recovery, and crisis management. This is obviously one of the main focuses of NIS2, ensuring that your organization can continue to provide service during a cyber security incident. Hornetsecurity offers an Email Continuity Service if an outage has impacted Exchange Online and our 365 Total Backup is a world class backup solution for Microsoft 365 workloads. VM Backup for on-premises workloads (Hyper-V and VMware) includes support for immutable storage (ensuring no one, neither attacker nor a malicious insider can tamper with your backups). Having a comprehensive, tested business continuity plan, supported by strong backup and recovery technology is the best way to ensure cyber resiliency – the ability to continue operating during an attack.
Supply chain security, including security aspects related to the relationships between each company and its direct suppliers or service providers. Do you remember the incidents in the SolarWinds supply chain attack? As recent breaches (Change Healthcare in the US for example) have shown us, the modern business landscape is a complex system of interconnectedness, and a small impact to a particular supplier can have a very large influence on the whole system if not properly planned for.
IT Security in network and information systems.
Cybersecurity training to train employees how to deal with various attacks that come via phishing and social engineering. Trained employees are one of the best cyber security measures. Our powerful Security Awareness Service educates your staff on cyber security risks on an ongoing basis, with very little management overhead for the IT department, all the while tracking employee behavior, only assigning follow up simulated phishing emails and training videos for staff who demonstrate , such as clicking on suspicious links, downloading and opening unauthorized attachments, or failing to recognize phishing and social engineering attempts.
Human Resources Security defines the protection of personal employee data.
Secured communication via voice, video, and text, but also secure communication in an emergency. You must assume during a breach that your normal communications channels may be compromised, and plan for alternatives. As you determine the scope of the compromise, if it looks like your source of identity (Active Directory / Entra ID / third-party) has been completely taken over, assume that any tool you normally use to communicate (on-premises phone system, Email, Teams, Slack, Zoom etc.) that rely on those identities is also compromised, and plan to use a different tool.
Authentication with multi-factor authentication and SSO (Single-Sign-On).
Access control helps to define least privilege permissions and the right RBAC (Role Based Access Control) to protect different resources.
Asset management is a structured and secure approach to acquiring, tracking, maintaining, upgrading, and disposing of defective or no longer-needed physical assets (e.g. End-Of-Life devices) within an organization.
Use Hornetsecurity’s 365 Total Protection Compliance & Awareness for stronger supply chain security, relying on full support for SPF, DKIM and DMARC, along with our unique AI recipient validation to check that you’re really communicating with the right person. For network security our Advanced Threat Protection catches email attacks that others miss, we have MFA controls for accessing our Control Panel, and we have a powerful but easy to use Email Encryption service for secure email.
Most importantly, a huge risk in most Microsoft 365 environments is ungoverned SharePoint / OneDrive for Business / Teams document sharing. Our unique product, 365 Permission Manager lets you take back control over both internal and external sharing and ensure ongoing compliance with your policies, while still supporting collaboration and productivity.
Management Duties & Governance
Article 31 of the NIS2 Directive defines the responsibility of senior management and governance. They are responsible for assessing and monitoring risk management measures.
Furthermore, it is also the responsibility of senior management to enforce security best practices within the organization and provide regular security awareness training.
One powerful product from Hornetsecurity that really helps in this area is Security Awareness Service which not only regularly reminds staff of cyber security risks, but also is up to date with the very latest threats as our Security Lab identifies them, along with powerful reporting for the senior leadership.
Enforcement & Sanctions
According to Article 32 or the NIS2 directive, the supervisory authority can act if you do not follow or comply with the NIS2 regulations.
This includes conducting their own tests and investigations based on the evidence the organization provided after a cybersecurity incident. These tests include onsite inspections, random checks, regular audits, ad hoc audits, and others.
The supervisory authority may also request and inspect any data, documents, information, or potential evidence.
In case of non-compliance with NIS2 or failure to provide up-to-date information, the authorities may issue public warnings, monitor your activities, set deadlines, and withdraw your operating license or certification so that your company can no longer operate.
ISO 27001 and NIS2
ISO 27001 is an international standard for the management of information security in organizations. NIS2 defines cybersecurity measures to protect the private and public sectors. One of the common questions we receive is whether NIS2 is included in the ISO 27001 certification.
While there is a great deal of overlap between the two standards (as indeed there is with most cyber security regulations), compliance with one still means you have work to do to satisfy the other one.
NIS2 Implementation Deadline
The European Union has done its part. It has defined the NIS2 requirements and now it is up to the EU Member States to adopt and publish the measures. The deadline to make NIS2 measures applicable is October 17, 2024.
Furthermore, by the 17th of April 2025, EU Member States shall establish a list of essential and important entities. EU Member States shall keep the list of entities updated.
Understanding Penalties for Non-Compliance
Compliance with the NIS2 legislation is not optional but mandatory for the companies concerned. If companies do not comply with NIS2, there are three types of sanctions, including non-monetary remedies, administrative fines, and criminal sanctions. The supervisory authority is authorized to enforce any of these measures based on their evaluation of your organization.

Non-monetary remedies include compliance orders, security audit implementation orders, binding instructions, and notifications of threats to the companies’ customers. The same applies to essential and important businesses.

Administrative fines distinguish between essential and important entities. For essential entities, the fine is 10 million EUR or 2% of global annual revenue. For important entities, the fine is a bit lower, 7 million EUR or 1,4% of global annual revenue.

NIS2 enables EU member states to hold top management personally accountable for negligence in the event of security incidents. In this way, top management is subject to criminal sanctions. The EU member states can order that the cause and the person responsible be made public in the event of breaches, and they can prevent top management from working in management positions in the future.
Conclusion
In 2016, the European Union created NIS to increase cybersecurity and protect organizations from security incidents. 7 years later, in 2023, they adapted and increased the security measures and introduced NIS2.
Now, with NIS2, more organizations are subject to NIS2 requirements. There are four key areas covered by NIS2 including reporting, risk management, management and duties governance, and enforcement and sanctions. They define everything from policy, implementation, and responsibility to sanctions in the event of a breach.
If the NIS2 guidelines are not or only partially complied with, the EU member states are authorized to impose non-monetary, administrative fines, and criminal sanctions.
As we’ve shown in this article Hornetsecurity has a range of services and products to help your organization with compliance with many of the NIS2 requirements. Good luck on your compliance journey and if you need help – please reach out to our team:

