

Deep Dive on M365 Defender
The best way to protect a business of any size against cyber risks today is with an integrated suite of tools. Microsoft 365 Defender is one such service that we’ll look at in this article.
For many years, the conventional wisdom, especially in larger organizations, was to buy best-of-breed solutions for each area. So, you ended up with the “best” (defining the “best” solution is hard and changes quite quickly) email hygiene solution, the best anti-malware solution, the best firewall, etc.
And because none of them natively integrated with each other, and manual integration is hard and time-consuming, you ended up with multiple consoles and multiple data silos where low fidelity signals were ignored, while they could actually have told you about a breach in progress if you’d been able to correlate those individual low severity signals between each of the systems.
A way to solve this issue is via Security Orchestration and Automation Response (SOAR) solutions that act as a “glue” between each product. Another is to buy an already integrated suite of tools such as Microsoft 365 Defender. The promise is eXtended Detection and Response (XDR), which is an extension of Endpoint Detection and Response (EDR) to indicate that not only endpoints but all systems are included in the protection and response.
This guide will focus on M365 Defender and tell you everything you need to know about it.
Name changes
In late 2020, Microsoft changed the names of nearly all of their security products, so if you’re used to hearing about Advanced Threat Protection (ATP) or Microsoft Threat Protection (MTP), those have all been replaced.
There’s now Microsoft 365 Defender, which is the umbrella term for the Defenders in M365, as well as a unified console. There’s also Microsoft Defender for Identity (formerly Azure ATP), Microsoft Defender for Office 365 (formerly Office 365 Advanced Threat Protection), and Defender for Endpoint (formerly Microsoft Windows Defender, then Microsoft Defender).
These products all tie into Microsoft 365 Defender (M365D) and are commonly abbreviated MDI, MDO, and MDE. Microsoft’s Cloud App Security Broker (CASB) was renamed to Defender for Cloud Apps (MDCA?) at the Ignite conference in November 2021. It was previously known as Cloud App Security (MCAS). This makes a whole lot of sense, as it’s part of the Defender family and can feed logs into the unified console.
While not strictly a security product and not bearing the Defender moniker, Azure Active Directory (AAD) and its security features also tie strongly into Microsoft 365 Defender.
There’s also Azure Defender for your IaaS and PaaS workloads in Azure, which also changed its name at Ignite in November 2021 to Microsoft Defender for Cloud. Also, separate from all of these security products but eminently capable of working with all of them is Azure Sentinel – a cloud-based Security Information and Event Management (SIEM).
Meet the Defenders
We have deep-dive articles on MDI, MDO, and MDE here in the M365 Dojo, but understanding what each of them does is crucial to understanding how Microsoft 365 Defender ties them all together.
MDI or Microsoft Defender for Identity
MDI is a cloud-based service that monitors your on-premises Active Directory for specific indicators of compromised identities and attacker operations. Anytime an attacker gains a foothold in your organization, one of their first goals is to move laterally and elevate privileges, preferably reaching Domain Dominance. This last stage, where your entire on-premises identity infrastructure is completely under the criminal’s control, takes an average 48 hours.
MDI relies on agents on your Domain Controllers (DCs) or, if your security team can’t stomach that, a member server that receives forwarded event log data from each DC and catches network traffic using port mirroring. MDI will catch attacker activity during five phases: Reconnaissance, Compromised credentials, Lateral movement, Domain dominance, and Exfiltration.
Because MDI is laser-focused on AD (and AD Federation Services ADFS, after the Solarwinds attacks), it produces high-fidelity alerts with very specific data to catch and contain miscreants on your network. Examples of attacks detected include Account enumeration reconnaissance, AS-REP Roasting, Identity theft (pass-the-hash), Skeleton Key attack, Data exfiltration over SMB and many, many others.
MDO or Microsoft Defender for Office 365
MDO is all about providing advanced protection for your Office Online workloads. Incoming emails and attachments are scanned by Exchange Online Protection (EOP) AV engines to provide a base level of protection, and if an attachment has never been seen before, it’ll be opened in a VM and inspected for malicious behavior to try and catch zero-day attacks.
MDO also looks at every URL in emails to see if they lead to compromised sites that Microsoft is aware of. It also provides time-of-click scanning as attackers will frequently compromise a benign website, send out their emails with links that won’t raise flags as they’re delivered (since the site isn’t displaying malicious indications at this point), and then activate the malicious payload on the website.
By checking the link at the time of actually clicking on it, MDO can offer strong protection against malicious URLs. MDO comes in two flavors; plan 1 covers the above features, whereas plan 2 adds Threat Trackers (intelligence on current attacks in the wild), Threat Explorer (also known as Explorer, shows you recent threats in your tenant), Automated Investigation and Response (AIR) and Attack simulation training (to train your users to recognize phishing emails).
MDE or Microsoft Defender for Endpoints
MDE, on the other hand, is a full-fledged EDR and anti-malware solution for your endpoints, including Windows, MacOS, Android, iOS, and Linux. On Windows, there’s no agent to deploy; it’s simply a matter of activating the bits already in the OS through onboarding, either with a script or Configuration Manager, Intune, or Group Policy at scale. Apart from local and cloud-based Machine Learning (ML) models to identify new threats, MDE also offers AIR and a complete Threat and Vulnerability Management (TVM) solution.
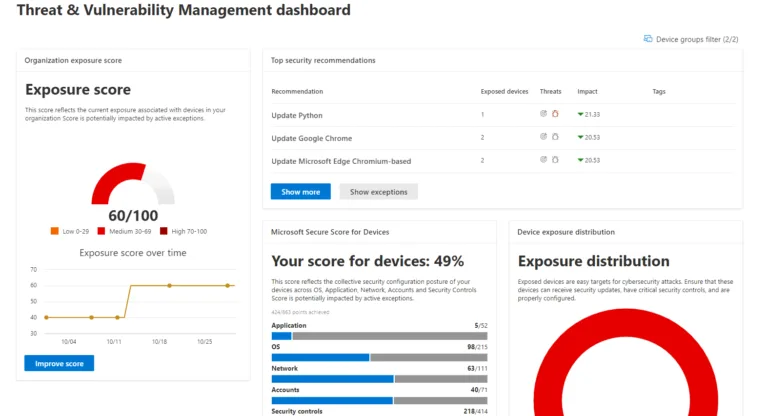
TVM inventories all software installed on your endpoints (Windows 8.1, 10 (1709+), 11 and Windows Server 2008R2+, MacOS, and Linux) and compares against known software vulnerabilities. Using signals such as the risk of the vulnerability being exploited, the number of devices in your organization where it’s installed, and the usage of the application, it’ll give you a prioritized list of programs to upgrade. As this is often a task for the endpoint/desktop team rather than the security team, there’s built-in functionality to create a task in Intune with links to the relevant upgrades, etc.
Until recently, there was only one version of MDE, but in August 2021, Microsoft announced a new version called Plan 1, while the full-featured version became Plan 2. Plan 1 brings Next-generation protection (anti-malware/virus), Attack surface reduction, Manual response actions, Centralized management, Security reports, and API access. Plan 2 adds Device discovery, TVM as above, AIR, Advanced hunting, full EDR, and Microsoft Threat Experts (MTE). This last one is a managed SOC service by Microsoft, which gives you two services: targeted attack notifications where analysts have identified an ongoing attack in your environment and access to experts on-demand to help your SOC if you need them.
At the Ignite 2021 conference, these two siblings (Plan 1 & Plan 2) were joined by a cousin, Microsoft Defender for Business, which will protect your Windows, macOS, iOS, and Android endpoints for up to 300 users in a business. Unlike Plan 1, it comes with TVM, AIR, and full EDR, so the only things that are missing are Linux support, MTE, and advanced hunting. It’ll be available as part of Microsoft 365 Business Premium or as a standalone license at $3 per user per month. It’ll also integrate with Microsoft 365 Lighthouse.
A common misunderstanding is between MDE and the built-in security features that every Windows 10 user can take advantage of Microsoft Defender Security Center and Microsoft Defender Antivirus. These basic protection features are used by MDE, but it adds many advanced features on top as outlined above.
There are good alternatives to Microsoft’s services; if you’re looking for email hygiene, archiving/journaling, zero-day protection, and email continuity even if Exchange Online is unavailable, plus optional backup, 365 Total Protection is excellent.
Microsoft 365 Defender
MDE used to have its own portal, separate from other security products (securitycenter.windows.com), and while it’s still there, it comes with a banner strongly suggesting redirecting users to the main M365 Defender portal (security.microsoft.com). MDI’s previous portal is completely retired, and its functionality was moved into the Defender for Cloud Apps portal quite some time ago. MDO is already housed in the M365 Defender portal. The work to integrate MDI into the main Microsoft 365 Defender portal is extensive and is likely to take some time. There’s more to the integration than just a single portal, although that’s a good start.
If you are using MCAS, you can integrate its telemetry into Microsoft 365 Defender.
First, there’s a unified alerts queue, so you’re not looking in one place for an email threat that might have snuck past your mail filtering and in another place for endpoints where that same email attachment might have been opened; it’s all in the same place. The same goes for the unified user page. A user account is an object in MDI (AD) but also an entity in MDO (has a mailbox, OneDrive for Business storage, etc.) and, of course, an object in MDE on whatever devices they’re logged in to.
The unified investigation page is my favorite; the ability to see details of automated actions (AIR) along with options to investigate myself further is very powerful, especially as it spans all the different Defenders. By popular demand, an email entity page lets you investigate suspicious emails, including previewing them if they’re stored in an Exchange online mailbox.
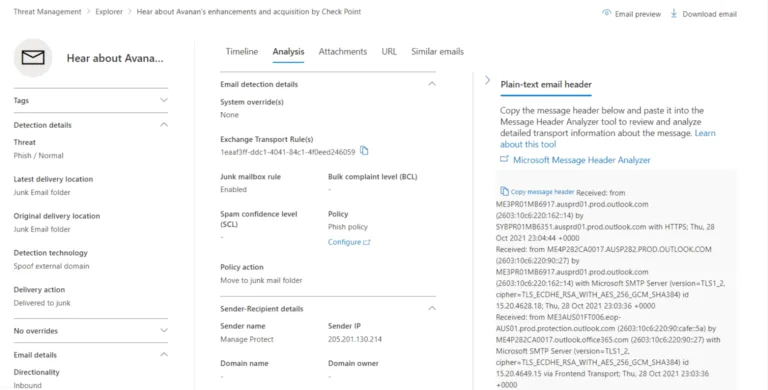
There are two ways of controlling access to M365 Defender data using RBAC, either using built-in Azure AD roles or, if you want to control access very granularly in a large environment, using Custom role access.
You don’t need to have all the different Defenders enabled to take advantage of the M365 Defender. As soon as you enable one workload, it works; as you add more services, more of the portal will light up.
Do you like to Hunt?
The coolest benefit of the integration, however, is the ability to do advanced hunting across all the data flowing into Microsoft 365 Defender. This is a sign of a mature security organization where it’s not all about dealing with alerts and incidents raised by the security systems but where there’s also time for an analyst to say, “I wonder if that attack against a company similar to us last week could have hit us too – let me grab the Indicators of Compromise (IOCs) and look through our logs.”
All Microsoft security products rely on Kusto Query Language (KQL) with a similar syntax to SQL for searching through large amounts of security log data and the ability to look in one query over email data (MDO), identity data (MDI), endpoint processes and actions (MDE) as well as third party cloud service logs (MCAS) is incredibly powerful.
There’s a new Advanced Hunting UI, which offers tabs for each query you’re working with and feedback on the performance of each query run.
Here, I’m looking to see if any suspicious PowerShell activity was launched within 30 minutes of a known malicious email being received in the last seven days.
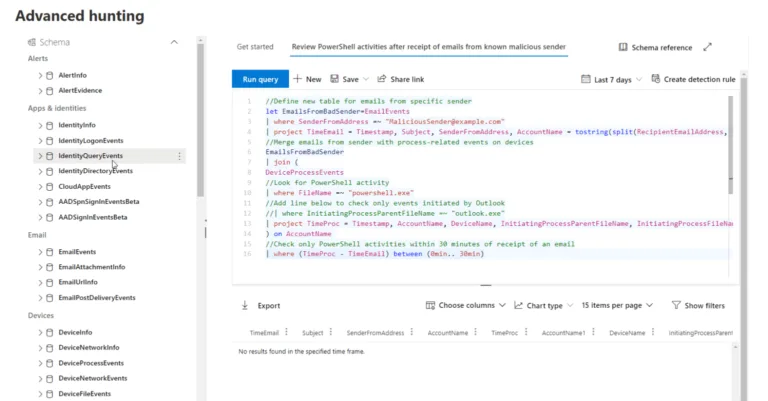
If you find events of interest during hunting, you can now use them to create an incident or add them as alerts to an existing incident. You can also bring in external data into hunting queries from lists of IP addresses, accounts, etc.
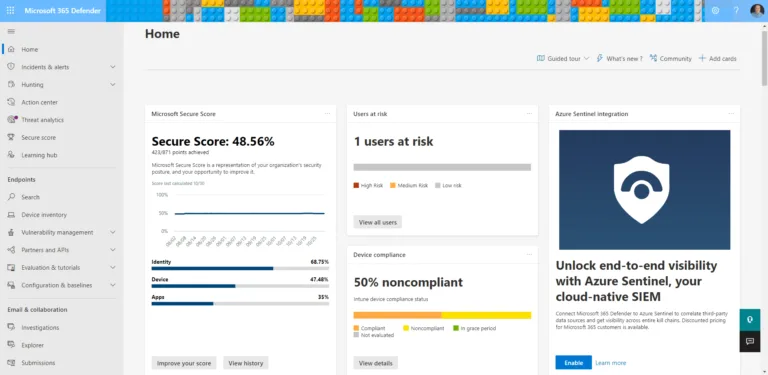
Microsoft 365 Defender also offers a Secure Score across identities, devices, and apps, giving you an overview of where you have strong controls in place and areas where you can improve your tenant’s overall security posture.
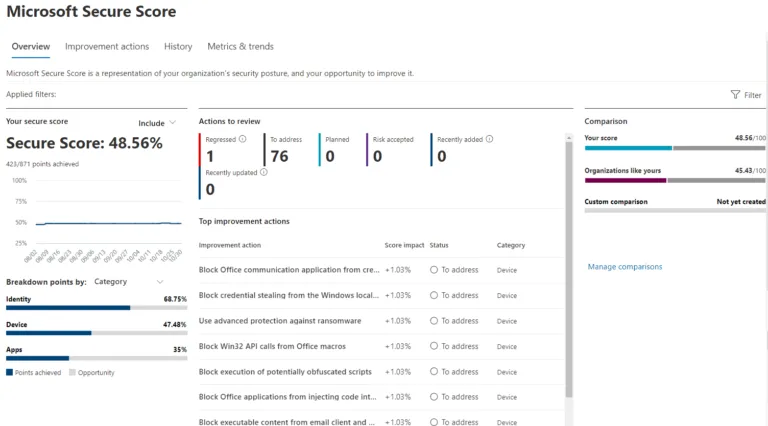
There’s also a unified view of Alerts and Incidents, actions taken by AIR, and reports for endpoints, emails, identity, and overall security.
Alternative Solutions
While Microsoft 365 Defender is a comprehensive security solution, it’s not the only game in town. There are many other providers that offer various solutions for email hygiene that integrate neatly with Exchange Online and provide features Microsoft doesn’t.
There are also services for email continuity (when Exchange Online is down), encryption of sensitive data, long-term archiving of emails for compliance, signature services, backup of Office 365 data, and many other EDR and XDR solutions on the market. One reason for choosing a different provider is the perceived conflict of interest when Microsoft is both providing the collaboration platform and the security services on top.
Furthermore, picking best-of-breed solutions for particular threats often provides strong protection as those third-party providers are solely focused on specializing in those areas. However, it’s crucial to ensure that these third-party solutions can integrate seamlessly with the rest of your security stack. Integration is key to achieving a cohesive and effective cybersecurity posture. It allows for streamlined operations, easier management, and a more unified response to threats.
In the context of Microsoft 365, this means ensuring that any chosen third-party solutions can work harmoniously with the suite’s native tools and services. This integration should not only be technical but also operational, allowing for a unified approach to threat detection, incident response, and overall security management.
While Microsoft 365 Defender is a robust and integrated security suite, the dynamic and evolving nature of cyber threats necessitates considering alternative solutions. These solutions should not only complement Microsoft’s offerings but also address specific security needs and integration requirements of an organization, ultimately enhancing the overall security posture and resilience against cyber threats.
Is Defender All you Need?
The power of an integrated suite that looks for malicious activity across email, identity, and endpoints is certainly appealing. There are a few things to keep in mind, however: Microsoft 365 Defender is focused on Microsoft 365 (it’s in the name), but most organizations have many other platforms and services to secure and monitor, which is where a SIEM like Azure Sentinel comes into play.
It can ingest data from Microsoft 365 Defender and many other Microsoft services, along with 100+ third-party data sources for a true single view of your digital estate. There’s also bi-directional synchronization between them, so if you close an incident in Microsoft 365 Defender, it closes in Azure Sentinel and vice versa. Log retention is only 30 days in Microsoft 365 Defender, whereas Azure Sentinel gives you 90 days for free, with several different options for storing security log data for longer.
However, and this should not be underestimated, most features in the Defender family require Microsoft 365 E5 licensing (or M365 E3 plus add-ons), which definitely is not cheap, especially in medium to large organizations. The price increase from E3 licensing to the required E5 is a big one and massively more expensive than assembling equivalent non-MS security solutions instead.
For example, Hornetsecurity’s 365 Total Protection Enterprise, which includes (amongst others) the equivalent security features, is currently priced at $4 per licence as opposed to $14 per user, per month for Microsoft’s security suite (calculated as the difference between Office365 E3 and Office365 E5 licencing from Microsoft.com).
Not only is it more affordable, but 365 Threat Protection Enterprise as a dedicated security service also offers greater overall email security than Microsoft can for example 10 year Email Archiving.
In conclusion, Microsoft 365 Defender is a robust one-stop shop for M365 security and as an integrated suite offers undeniable ease of use but lacks the cutting-edge protection provided by specialised third-party solutions and comes at a considerable cost.
Download a free trial of Hornetsecurity 365 Total Protection and try it out for yourself!

