

What Your Employees Need to Know About Phishing + Real-Life Examples
In this article, we’ll present a series of real-world phishing emails, with personal details altered or obfuscated to protect the innocent.
These are useful for training users to spot the clues that something is trying to trick them, so feel free to use these in your training materials.
Real-Life Phishing Examples
Let’s start with a classic, the Nigerian prince scam, also known as an advance-fee scam. These try to make victims believe that they are the recipients of a large amount of money (emotion trigger: greed), but to receive it, they must pay a fee (“transfer fee” or “handling fee”). Here’s a simple example:
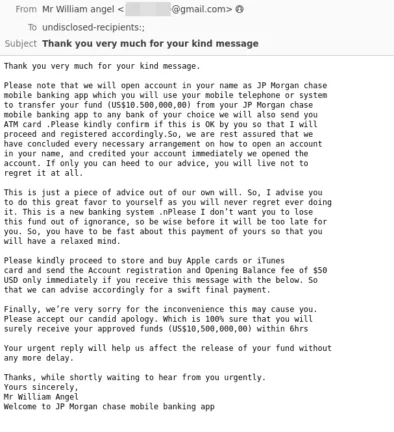
Note the use of gift cards – criminals can’t use the standard international bank transfer system (Swift) as their funds would be blocked very quickly, and asking normal users to transfer crypto currency is also a dead giveaway – thus, the gift card request, a very common tactic.
A second clue in this email is the poor use of grammar and English, which is always a sign of something fishy but will likely be less prevalent in the coming months as generative AI tools become commonplace. Does this email really sound like it would have been sent by someone at JP Morgan Chase bank with the last name Angel?
Next is the phishing category, starting with a spoofing email. Spoofing is using various techniques to make it appear as if the email is coming from one sender when, in fact, it’s sent from an attacker’s email address. In this example that’s American Express, amex.com. This email also employs the tactic of making the entire email into an image, to make it harder for anti-spam engines which analyze text. Having SPF and DMARC records in place will block this particular spoofing technique.
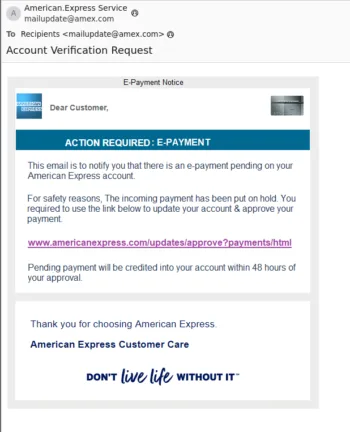
The link shown in the image isn’t the one that an unwary user will open if they click it, which is why it’s important to train users to hover over suspicious links before clicking them (which is easier on computers than on smartphones).
Humans, including security experts, are poor at identifying malicious URLs (because they were never designed to be an indication of trustworthiness), but the fact that the link text you’re seeing on the screen doesn’t match the actual link target is enough to know that it’s a scam.
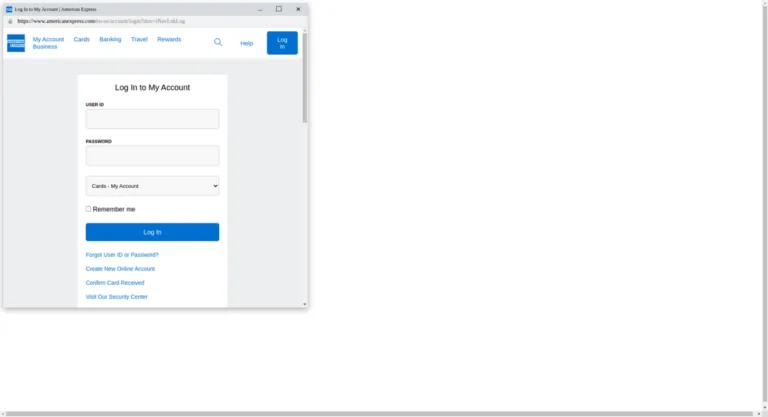
If you do click, you’re taken to a phishing page with a sign-in prompt, which looks like it’s an American express site.
Note the scroll bars however, it’s a webpage, made to look like a browser (within the real browser), which you can tell from the scroll bars on the right and at the bottom. Again, the actual domain that the victim is entering their credentials into isn’t the one shown on the page.
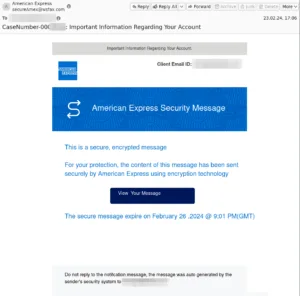
Another flavor is impersonation, the email below again purports to be from American Express, but the sender is secureAmex@wsfax.com, whilst the display name of the sender is “American Express”. This email isn’t about triggering greed, but rather concern about the “important information” relating to your account.
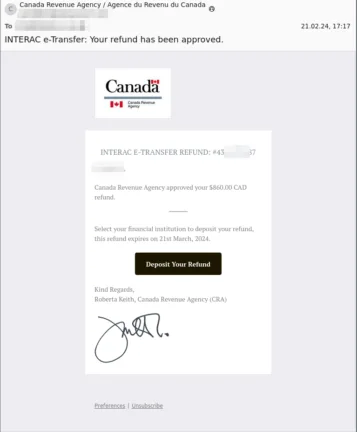
Here’s another one from Canada Revenue Agency / Agence du revenu du Canada, again with the actual sending email address being different. This one appeals to greed, with the promise of a refund, clicking the link leads to a credential harvesting page.
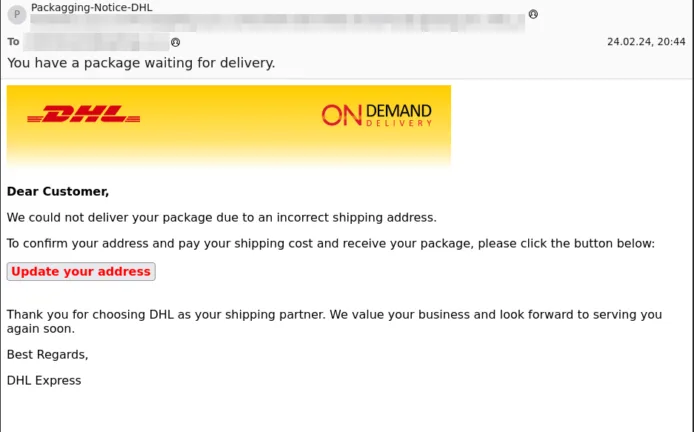
We have all become accustomed to receiving a lot of packages, and after the Covid-19 pandemic, it has become ubiquitous. In our data, DHL has been the leading company impersonated for a long time, but they were recently replaced by Fedex.
Here are two examples of DHL impersonation emails where the display name doesn’t match the sending email address, with links to click to “update your address”. Note the misspelt word “Packagging” as well as using “Hello Dear” as an introduction, unlikely from a shipping company.

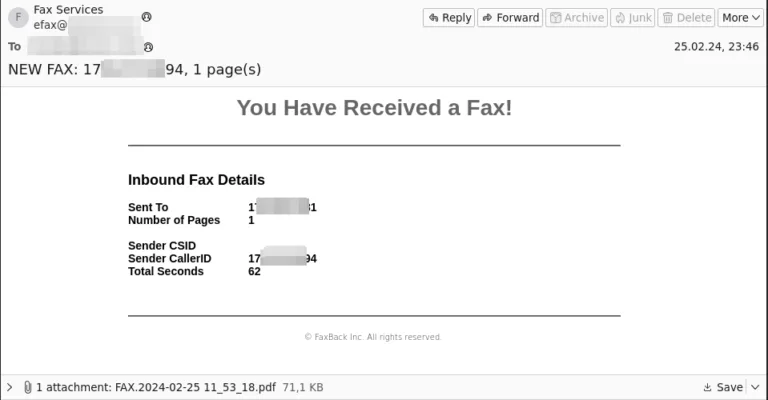
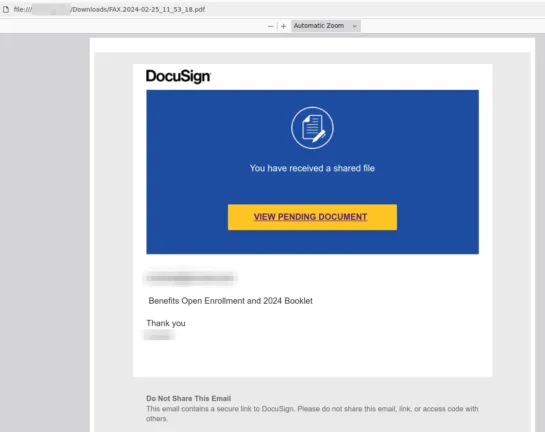
Phishing emails frequently use attachments to spring their trap; here’s one purporting to be from DocuSign.
The PDF attachment, obviously not a scanned fax page, looks like a DocuSign document – clicking the link for View Pending Document will lead to a phishing page. The use of a DocuSign-looking page is appealing to the familiarity of the process. many of us are asked to electronically sign documents using DocuSign, so we’re less likely to be suspicious of this request.
As mentioned, QR codes have become very popular in phishing emails. There are two reasons for this: firstly, email hygiene solutions were slow to incorporate technology to spot these in emails, scanning the code, following the link, and inspecting the target web page for signs of maliciousness. Hornetsecurity has had QR code scanning in place since early 2023.
Secondly, and possibly the reason why we’re still seeing large volumes of malicious emails with QR codes, is that they move the attack from an often managed, locked down, secured computer endpoint, where most business users read their emails, to a personal smartphone with minimal protection.
Scanning a QR code with your smartphone is second nature for most of us, especially as their use in society is so common, and people don’t expect a bad result from doing it.
Here are three examples of phishing emails with QR codes as the link instead of the traditional weblink or button to lure a victim.
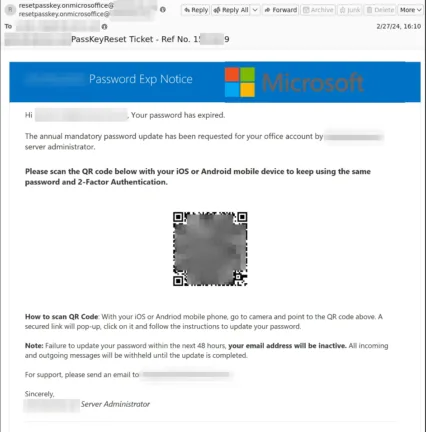
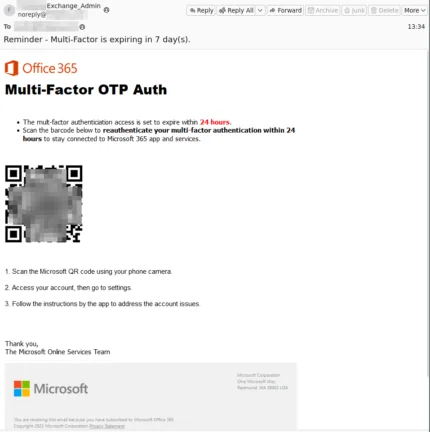
The urgency of this email, with the 24-hour deadline, is again creating a sense that the user must do something about this now or risk losing access and not being able to do their job.
Both of these are particularly insidious because the legitimate set-up process for MFA with Microsoft Entra ID, either with Microsoft’s Authenticator app or a third-party app, involves scanning a QR code. It’ll seem quite normal for end-users to scan a QR code again as part of MFA.
Key here is education of the business staff by the IT / security teams. If there are no legitimate business processes that involve scanning QR codes sent through emails, it is essential to inform everyone to avoid scanning any QR code that they receive in an email.
Additionally, it is recommended to follow up with Security Awareness training, including simulated phishing emails, to test staff and help them sharpen their instincts.
If you do have legitimate business processes that involve QR codes, look to see if they can be sent in some other way than via email, and if they can’t, clarify to everyone that this process does use QR codes, and here’s how that flow works, but don’t scan any outside of this procedure.
This last example introduces a wrinkle with the QR code being blue on a red background, no doubt to bypass email hygiene solutions (Hornetsecurity ATP isn’t fooled and caught these). Note the clumsy grammar “failure to secure your update Mailbox will lead to deactivation”.
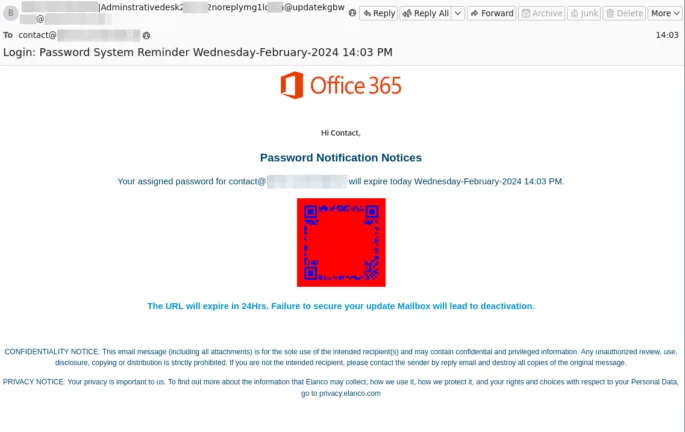
If you scan the QR code you’re taken to a credential harvesting page, gathering Microsoft login credentials.
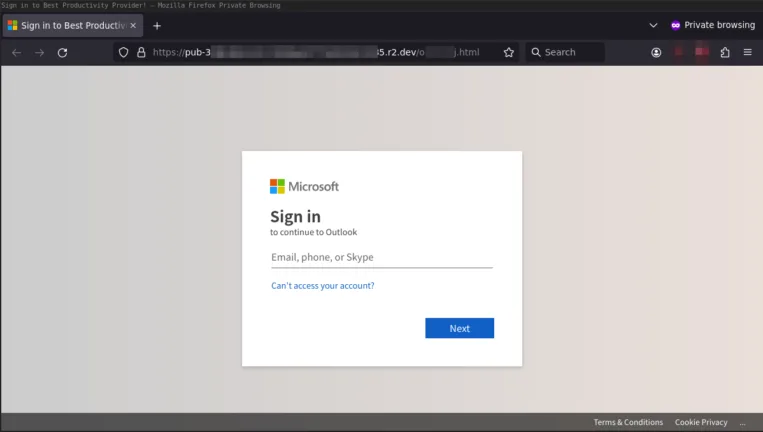
The key in all these examples to convey to your staff is to be aware of triggering emotions, unusual requests, unusual processes (this isn’t how I normally reset my password), bad spelling and grammar and for QR codes, don’t scan them unless it’s part of a known business process.
Enhance employee awareness and safeguard critical data by leveraging Hornetsecurity’s Security Awareness Service for comprehensive cyber threat education and protection.
We work hard perpetually to give our customers confidence in their Spam & Malware Protection and Advanced Threat Protection strategies.
Discover the latest in cybersecurity: How to Spot a Phishing Email in The Age of AI. Learn how AI fuels sophisticated phishing attacks and gain actionable insights to protect your business.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
In conclusion, understanding the tactics used in real-world phishing emails is crucial for individuals and organizations to protect against cyber threats.
By recognizing common red flags, practicing vigilance, and implementing robust security measures, individuals can defend themselves against phishing attacks, while organizations can fortify their defenses and mitigate the risk of data breaches and financial losses.
Stay informed, stay vigilant, and stay safe in the ever-evolving landscape of cybercrime.
FAQ
Phishing emails often exploit emotions like greed or urgency, feature poor grammar, and employ spoofing techniques to appear legitimate. They may contain suspicious links or attachments and often mimic trusted organizations to deceive recipients.
Individuals can protect themselves by being vigilant for red flags such as unusual requests, spelling and grammar errors, and unexpected links or attachments. They should verify the sender’s email address, hover over links to check their destination, and refrain from providing personal information unless absolutely certain of the sender’s legitimacy.
Organizations should implement comprehensive security awareness training to educate employees about phishing tactics and best practices for identifying and reporting suspicious emails. Additionally, they should deploy advanced email filtering and anti-phishing technologies, enforce email authentication protocols like SPF and DMARC, and regularly update security policies and procedures to adapt to evolving threats.
