

What is DMARC and How Does it Work?
Email is a critical tool for businesses and any amount of extended downtime can result in loss of revenue, loss of reputation and even legal woes. Hardly a day goes by, unfortunately, without a suspicious looking email making it into our Inbox. For some unlucky souls, this suspicious email is mistaken for something legitimate, they click that link and bad stuff happens. The industry nomenclature commonly used to describe this is Phishing, which can then also lead to Business Email Compromise (BEC), topics heavily covered by Hornetsecurity, some of which can be accessed here:
- Stay Alert for Phishing Scams This Holiday Season
- What Your Employees Need to Know About Phishing + Real-Life Examples
- Unmasking Phishing: Understanding the Insidious Threat to Your Organization
The theme you’ll find in the articles above is consistent and clear: the phishing and spoofing attacks are relentless and are on the rise. Businesses must remain vigilant and ensure they are using robust protection to detect and block these attacks.
What is DMARC?
We’ve established how critical email is to businesses and touched on the biggest threats they face. Let’s now shift to talk about the protection mechanisms used to mitigate these threats. Allow me to introduce a triumvirate of email authentication protocols, configured as DNS records, which can be used to protect against common BEC threats:
- DMARC (Domain-based Message Authentication, Reporting & Conformance)
- SPF (Sender Policy Framework)
- DKIM (DomainKeys Identified Mail)
Although this blog is about DMARC, it’s important to talk first about SPF and DKIM which are integral to how DMARC operates. SPF brings the ability for domain owners to specify which hosts are permitted to send email, on behalf of that domain. DKIM on the other hand uses public-key cryptography to provide an assurance that the message has not been tampered with in transit. DMARC (pronounced as “DMark”) uses a set of rules, referred to as “policies”, and based on checks performed by SPF or DKIM, effectively determines if an email is legitimate.
Working together
As I mentioned before, a DMARC policy assesses the results from the SPF and DKIM to decide whether to mark the email as genuine. This simplified representation shows how DMARC, SPF and DKIM work together:
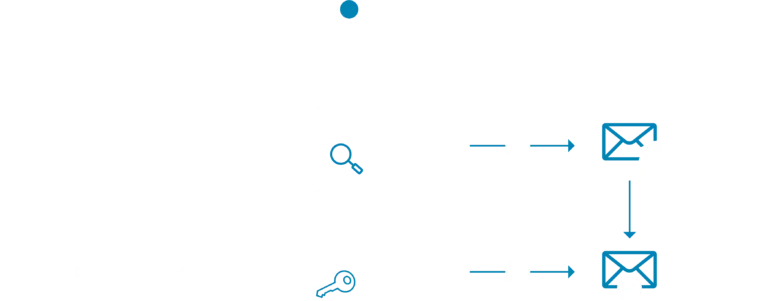
Let’s dive in to understand how this works in practice once a mail has been received and is assessed using the DMARC policy.
- SPF check – Provides domain-sender authenticity by verifying that the source domain in the message matches the “Return-Path” field.
- DKIM check – Uses public-key cryptography to validate the integrity and provide assurance that the message has not been tampered with.
DMARC take the results of these checks and uses them as inputs in a policy to assess and determine what action is taken. It’s important to note that while DMARC policies have three clearly defined actions for what should happen next, the actual decision may differ based on the nature of the business and its context. For example, if email delivery is critical to the business, the policy may be more lenient in how it treats emails which have not passed all checks. In other words, the sending organization configures their DMARC policy, but it’s up to the receiving businesses discretion whether to follow that policy or not.
Working in tandem with DKIM and SPF, DMARC enables companies to publish a DMARC policy into a DNS record, thus establishing a policy for how to handle emails that fail both SPF and DKIM.
Together, SPF and DKIM form the building blocks of DMARC. The DMARC record is a policy that tells a server how to process emails that are not easily managed by either DKIM and SPF. Once published, a DMARC record is published in a DNS and can be modified for adjustments. And that’s where things get difficult.
DMARC Policies
The DMARC Policy is where all the magic happens and where the DMARC decides how to treat messages depending on the results of the SPF and DKIM checks. Quick note that depending on several factors, the configuration of SPF and DKIM records can be quite complex. I won’t go into those details now, but further information about how to configure each can be found here:
I’m going to keep it at a relatively high level and focus on the three options available in the DMARC policy: None, Quarantine, or Reject.
| Option name | Action | Result |
| None | Take no action | The message is delivered |
| Quarantine | Mark as spam | The message is treated as spam |
| Reject | Block delivery | The message is not delivered |
The first option “None” is typically a good choice if the domain is newly acquired, and you want to establish a baseline to ensure emails are being delivered using DMARC. After that and depending on your infrastructure and business context, you might switch to mark messages as “Quarantine”. The “Reject” option will do exactly what it says on the tin.
It’s important to call out that a DMARC policy can still be used if either a SPF or DKIM record exists, but having both is better. This is especially important at a time when phishing emails pose significant threats to email security, comprehensively covered in this article about Phishing by Hornetsecurity.
To really see an uplift for email security to combat email threats across the Internet, a wider adoption of these protection mechanisms is needed. The good news is that the trends are going in the right direction. Although introduced in 2012, dmarc.org. tracked the adoption of actively used records from 2016 to 2022 which included these findings:
- From a slow rise of configured DNS records starting in 2016, by 2019 the number of DMARC grew to approximately eighty thousand.
- Exponential growth with over three and a half million in June 2021 and almost six million as of April 2022.
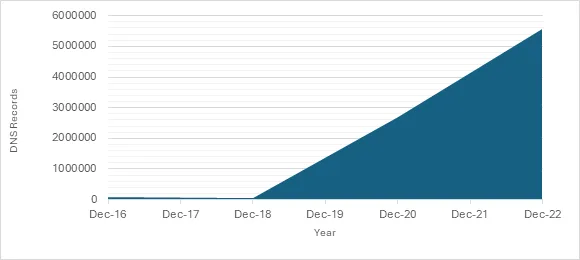
I think it’s safe to say the uptake will have only increased since the last recorded results. Particularly with Yahoo and Google leading the charge, announcing in late 2023 that from February 2024 the requirement for any service sending more than 5,000 messages a day to have a DMARC policy in place. This sent a clear signal that that the industry recognizes the importance of enhancing email security for everyone.
How DMARC Enhances Email Security
DMARC performs a critical function of validating email authenticity using the checks in SPF and DKIM, providing a two-way assurance for both the sender and recipient:
- The sending domain is assured that outbound emails will be delivered.
- The received email server is assured that the domain the emails are from is authorized to send them.
A comprised domain is a dangerous weapon malicious actors can use to launch their phishing and domain spoofing attacks, in which unauthorized emails are sent from the source email domain. This in turn creates additional attack vectors such as hosting malware on an otherwise legitimate domain, and deceiving victims into downloading malware. The risks of this are significantly reduced using the DMARC policy.
We’ve so far talked a lot about the preventative controls by DMARC, but what about its detective controls? You’ll be glad to know that the design of DMARC incorporates reporting and monitoring too! It provides two types of reports as well as continuous monitoring of email authentication issues in real time. Collectively these provide domain owners with powerful insights to help them identify potential security issues such as email spoofing, misconfigurations or unauthorized use of their domain.
These reports come in two flavors:
Aggregate report
A snapshot type report with insights and statistics which include results of how many emails passed or failed DKIM checks.
Forensic reports
Less common and used to troubleshoot specific authentication problems by providing detailed information.
Common threats mitigated by DMARC
We’ve discussed how DMARC can mitigate against threats like phishing and domain spoofing, but what about other crafty attacks by bad actors via email? For example, infecting user devices with malware using a spoofed email address. DMARC to the rescue! Spoofed emails will fail DMARC checks, flagged as malicious and dealt too accordingly.
What about non-technical threats like impacting a company’s brand and reputation? The ability to spoof a company domain can cause significant damage in several ways such as sending inappropriate, misleading or even fraudulent emails. Depending on the scale of these attacks, the trust in the company brand potentially built up over many years can be wiped out or significantly reduced. DMARC to the rescue! Domain owners can mitigate this threat by specifying what actions to take when an email fails the authentication checks.
Prevent DMARC Configuration Headaches with Hornetsecurity’s DMARC Manager
Setting up and maintaining DMARC, DKIM, and SPF policies can create a potentially large administrative overhead, especially if you’re managing this for large and complex organizations, managing many domains, multiple configurations, and potentially different requirements per domain.

You’ll be glad to hear that a solution for this is available in the form of DMARC Management Tools, also known simply as “DMARC Manager”. Hornetsecurity’s DMARC Manager is designed to safeguard your brand’s reputation by protecting your domains against email impersonation, phishing, and spoofing with intuitive DMARC, DKIM, and SPF Management features such as:
- A Domain Configurator
- Status dashboard
- Email senders analysis
- Failure Reports and Alerts
Are you unsure if your domain is at risk? Check out our free email security checker to analyze your domain’s SPF, DKIM, and DMARC settings.
Request a demo today and see how DMARC Manager safeguards your domains against email impersonation, phishing, and spoofing with intuitive management:
Conclusion
Businesses must act proactively in how they protect and safeguard their email communications from the threats posed by phishing and spoofing attacks. The DMARC email security protocol is a crucially important technology they can use, creating a policy that, together with SPF and DKIM, can determine which actions to take for an incoming email.
The adoption of DMARC is steadily rising, and recent requirements by key industry players is likely to keep driving that positive trend. To that end, businesses should already be developing a plan for implementing DMARC Manager. However, this should not be planned and implemented in isolation, instead forming part of their comprehensive email security strategy.
FAQ
DMARC enhances email security by validating email authenticity, reducing risks from phishing, spoofing, and malware attacks. It protects brand reputation and provides valuable insights through reporting and monitoring to identify authentication issues.
DMARC Manager by Hornetsecurity is an intuitive tool designed to simplify the implementation and management of DMARC, SPF, and DKIM policies. It helps protect your domains from phishing, spoofing, and email impersonation while safeguarding your brand reputation.
DMARC Manager minimizes administrative overhead and prevents configuration errors. It ensures email security by automating complex setups, enhancing domain protection, and enabling proactive threat management, making it ideal for businesses of all sizes.
