

Why and How to Transition from MSP to MSSP
If you’re running a Managed Service Provider (MSP), you’re aware of the shift in our industry, from IT support to cyber security maintenance.
I started my IT business in 1998 and back then it was all about helping clients get the computers to work, keeping them connected and fixing them when they broke. Internet was dialup (for SMBs), and security was slightly complex password requirements and an antivirus solution on the endpoints. Fast forward to today and the devices are much more reliable, networking is (mostly) easy, and the internet is speedy – but the proportion of cyber security work is ever increasing, both in volume and complexity, followed closely by regulations that clients must adhere to.
In this article we’ll look at the transition from MSP to MSSP, and why you should consider this, the spectrum of possible services that you can offer and pitfalls along the way, plus introduce great tools to help you along the way.
This isn’t something you can sleep on either, many MSPs have already taken this step or are considering it, you don’t want to be left behind.
What is an MSSP?
We’re all familiar with the value proposition of a Managed Service Provider (MSP) – for a monthly fee per device or per user they take care of your IT needs, providing scheduled maintenance and monitoring, a helpdesk and helps you implement IT systems to improve your business performance.
A Managed Security Service Provider (MSSP) on the other hand provides one or more of these cybersecurity services:
- Security event monitoring, either during business hours or 24×7. There’s a range of events monitored, and the depth of information gathered.
- Managed Detection and Response (MDR). Monitoring is great, but it’s even better when the MSSP responds to incidents, ranging from disabling accounts, forcing password resets, isolating devices and even full-blown Incident Response (IR) in cases of a successful breach.
- Threat hunting. Monitoring and MDR are reactive, relying on signals to alert you when something’s amiss, whereas proactive hunting digs through logs and evidence to catch novel attacks and other signs of intrusions that might have slipped by the alert rules. Sometimes these first three services are offered as a managed Security Operations Center (SOC).
- Penetration testing (pentest). Where an MSSP attempts to breach an environment, using similar techniques to real threat actors, and then using the resulting alerts and reports to improve defenses. (As a side note, you should use a different MSSP for your defense than for your pentests to get a true sense of how good your visibility and response is).
- Risk assessments of the organization’s overall security posture, identifying gaps and suggesting additional controls to mitigate these risks.
- Virtual Chief Information Security Officer (CISO) services. Many SMBs are too small to have a dedicated CIO or CISO and an MSSP can provide this function, tying in with the risk management service, plus provide strategy and future planning for the business in the area of IT and cyber security.
- Managed firewall. Leaving management of configuration and rules in your edge firewall(s) to an MSSP might make business sense, especially if they’re taking care of all the other security settings. Sometimes this can include web browsing security with managed DNS services and Secure Web Gateway services.
- Managed Virtual Private Network (VPN). This is where an MSSP manages a VPN for a business, again ensuring security and monitoring is in place. Future looking MSSPs might offer Zero Trust networking as an alternative to VPNs, using Secure Services Edge (SSE) solutions to mitigate the risks inherent in legacy VPN technology.
- Managed Vulnerability Management. This is the never-ending process of identifying missing patches and miss configurations across an IT estate, reporting on them, prioritizing remediation, patching and continuously reporting on the overall security posture of a business.
- Managed Identity and Access Management (IAM). Some MSSPs can manage your identities and privileges (authentication and authorization) for access to systems and services.
- End user and IT staff training. Cybersecurity is a rapidly shifting landscape, and you should train your end users to recognize social engineering attacks (via phishing emails, messaging apps or phone calls), plus keep your IT staff abreast of new threats – all of which an MSSP has the expertise to deliver.
- Regulatory compliance. The range and depth of regulations affecting different businesses is increasing worldwide, with different regions and countries having varying approaches to auditing, enforcement and legal liability. In Europe there’s GDPR and now NIS2, whereas health providers in the US for example must adhere to HIPAA. Different industry verticals and sizes of businesses are also treated differently. Having an MSSP with audit experience assisting with the time-consuming work of preparing for a regulation audit can be immensely helpful, especially for a business facing their first audit.
Of course, not all MSSPs offer all these services, nor might you want to outsource all of these to a third party, depending on your business. The benefits of an MSSP are that they have in-house expertise that might be difficult for a single business to build up and thus outsourcing can be cost effective. It allows you to focus on your core business and “leave security to the experts”.
A word of caution though, just like when you move workloads to a public cloud, there’s a shared responsibility model where some areas are still yours to look after, so while you can outsource the management of cybersecurity to a MSSP, the ultimate responsibility for it still resides with your organization.
Why transition from MSP to MSSP?
Depending on how you run your MSP and how much your services include security configuration, monitoring and response, you might look at the list above and say, “we already do some of this”. And that’s the reality for many MSPs today, there’s just so much basic cyber security required in a business of any size that you’ve probably already incorporated several of these services in your package.
Most MSPs today will:
- Deploy an Endpoint Detection and Response (EDR) tool on all endpoints. These are generally cloud based and provide a centralized console for alerts, incidents, endpoint / identity response actions, and often Threat Hunting capabilities.
- Manage email hygiene and security. The most prevalent vector for the first foothold attackers gets is still through phishing emails, thus providing strong email hygiene security is paramount.
- Manage IAM and identities, including Multi Factor Authentication (MFA) deployments.
- Forward looking MSPs are deploying eXtended Detection and Response (XDR) solutions that tie together email, endpoint (EDR), cloud apps and identity security into a single console, managing alerts across the whole IT estate. Some MSPs even deploy a Security Information and Event Management (SIEM) solution to extend the XDR platform to include third party log sources for increased visibility.
- Where on-premises firewalls are required, they’re generally managed by the MSP already, and if a cloud SWG is deployed, the MSP also configures the rules.
- For Zero Trust networking and VPNs these are also deployed and configured by the MSP.
Some MSPs include these as part of their package, without specifically calling it out, whereas others provide a basic IT package, with a security package on top. This isn’t always successful however, because if basic security isn’t included it’s only a matter of time until the cost of cleanup after a breach vastly exceeds the cost of it being included.
If you do start the transition from MSP to MSSP there are some considerable advantages such as stronger credibility in the market and increased revenue streams, plus the ability to remain the IT provider for your clients that “does it all”.
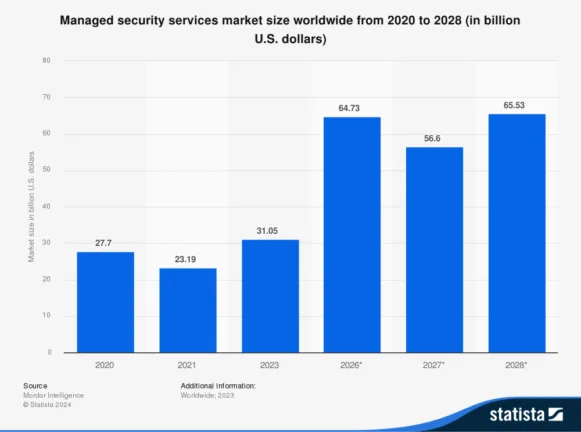
The security services market is growing globally and expected to double in the next few years.
Two Strategies for the Transition
Partnering with an MSSP
Thus, an MSP must decide on a strategy when it comes to cyber security management and pick a point on the gradient. On one end is the pure MSP approach, “we only do IT” and on the other end of the scale is the pure MSSP “we only do cyber security”. One option is to partner with an MSSP, and offer a combined package, where the MSP continues to manage all IT related tasks, and the partner MSSP provides a selection of the services outlined above.
There’s often resistance at MSPs to this with ideas along the line of “what if they poach our clients” – which is generally speaking not actually a risk, as most MSSP don’t want to take over the IT responsibility as well.
Offering MSSP services in-house
Another option is to build out in-house capacity to offer more MSSP services and sell these to your clients as an additional revenue stream, and again there’s a spectrum from just adding strong incident response capacity, to a full blown 24×7 SOC with expert threat hunters for example. A third alternative is to pivot, and stop offering MSP services, focusing exclusively on MSSP offerings, or standing up a separate company to do exactly that.
As a practical example of this gradient, incident response for a compromised user identity and device at a client from an MSP includes invalidating all sessions, resetting password and possibly checking MFA methods, plus re-imaging the endpoint.
An MSSP might go much deeper and investigate logs and processes to identify exactly how the initial attack occurred (digital forensics), any lateral movement to other systems and services in the network, possible locations for hidden access persistence, and if the attackers have compromised the UEFI of the endpoint (which would survive the re-image). If your MSSP services include incident response, be sure to clarify exactly what you’re offering.
Things to bear in mind
No matter where you land on the gradient (and it’ll change over time) there are two important stakeholders to communicate with. The first are your clients who might think you’re already taking care of security for them, they need to be educated about what your MSP side of the business does, and what this new MSSP side will do.
The second is the legal side, you need to clearly define your SLAs and responsibilities in your contracts, clarifying exactly who’s responsible for what. After all, if a user at a client clicks a malicious link in a personal Gmail inbox from their work device or inserts a USB stick with malware that bypasses your defenses there’s every chance that the client will have a breach.
If you’ve sold them on an expensive “managed cyber security plan” they might think they’re invincible and no cyber security attack will ever bother them again and thus blame you.
Steps to Successfully Transition from MSP to MSSP
If you’re looking at the option to build out your own cyber security services and transition your MSP to an MSSP, let’s look at the steps you should take.
- Start by inventorying your current service offerings, how you market them, what they include, and which components are cyber security related. Then look at what additional services you’d like to bring to your existing and new clients as a MSSP and how to package and price these.
- The next step is to skill up your existing staff to deliver these services or hire new staff with the required experience. Don’t underestimate the time, effort and cost included in this step, especially if you’re looking to staff a 24×7 SOC, given the fierce competition for capable security analysts.
- Finally start communicating with your clients about your additional cybersecurity service offers and bring them onboard. If, on the other hand, you’re truly transitioning from MSP to MSSP, and stopping your MSP service offerings, you need to have a good relationship with another MSP that you can recommend to your existing clients.
Take the Next Step in Your Evolution to MSSP
Don’t let the complexity of cybersecurity threats hold your business back. With 365 Multi-Tenant Manager for MSPs, you can seamlessly transition from MSP to MSSP, enhancing your service portfolio and safeguarding your clients.
Request a demo today to discover how 365 Multi-Tenant Manager can revolutionize your security service management and help you stay a step ahead of cyber threats.


Unlock the Secrets to Effortless MSP Growth!
Ready to overcome the challenges of scaling your MSP? Download our MSP Playbook and discover proven strategies to streamline onboarding, automate tasks, enhance security, and standardize operations. Don’t let manual processes and compliance stress hold you back—start working smarter today!
Conclusion
Hornetsecurity offers a comprehensive set of products for MSP / MSSPs.
They’ve specifically developed their comprehensive 365 Total Protection offering which offers an all-in-one solution for M365 security, including email security, backup, compliance, and security awareness training. This unified suite simplifies security management, reduces risk and safeguards your clients’ data and communications, ensuring business continuity.
And it’s designed to integrate seamlessly with M365 to provide much-needed layers of additional security and data protection and offers value to both IT administrators and end users.
Alongside that, Hornetsecurity’s 365 Multi-Tenant Manager (MTM) ensures settings consistency throughout your customer base. This is an important feature for MSSP users looking for a streamlined approach to managing Microsoft 365. MTM automates administrative tasks for configuring settings across many tenants, as well as letting you define standard settings which can be re-evaluated on a scheduled basis, minimizing configuration drift.
Plus, a central console makes management easy and convenient, giving the perfect blend of data privacy and ease of use. Via the control center, IT employees can switch directly from email to backup management and more. This option makes monitoring, controlling, and optimizing filters and configurations much easier. An absolute MUST for MSSPs.
There’s no question that the increasing volume and complexity of cyber security attacks requires a better approach and as outlined here, transitioning your MSP to an MSSP might just capitalize on this situation.
