

Understanding Supply Chain Attacks and Protecting Your Business
Modern businesses are interconnected in a global, digital world. Even smaller businesses that only operate in one country or area are dependent on parts, components or services from a huge range of suppliers. Large organizations have a correspondingly huge, interconnected web of dependencies, both that they rely on for their operations, and that their customers in turn rely on them for.
Notwithstanding the move by some countries to isolate themselves from the rest of the global digital world, for most of us this is the reality we must deal with. And this interdependency, which is many layers deep brings business risk.
In this article we’ll look at this challenge overall, then dive deeper into specifics in the IT sphere and look at what supply chain attacks are, where your vulnerabilities are and give examples of recent attacks. We’ll then look at how your can protect yourself, where user awareness training fits in and how Hornetsecurity can help you secure your supply chain.
What is a supply chain attack?
A supply chain attack, also known as supply chain phishing, occurs when a cybercriminal targets a trusted vendor (company or platform) to carry out cyberattacks throughout the supply chain. In such instances, they might introduce malware to shared systems or cleverly launch phishing attacks through the vendor, exploiting their trust.
In the cyber security space, we tend to focus on software vulnerabilities in your supply chain but if you take a step back, understanding that any part or service that goes into your business being able to operate is a potential supply chain attack.
Buying parts from overseas manufacturers to integrate into the devices you build in your factory? Those parts could be tampered with, made from inferior materials or not work as expected, especially if they’re electronics.
Think about all the raw material, parts or software that go into your business being able to do what it does, and think about all those supply chains – what would happen to your business if they were interrupted? What would happen if they were maliciously used against you?
Any moderately successful business today has already learnt how to manage supply chain risks that aren’t malicious, parts arriving late or not at all, not working properly etc. In this article we’ll focus on the other side of supply chains, when someone intentionally uses them against you to cause your organization harm.
Rather than attacking the organization they’re after, criminals will infiltrate a business that the organization depends on and through them attack the target. An example could be compromising an IT Managed Service Provider (MSP) and using their access attacking their clients.
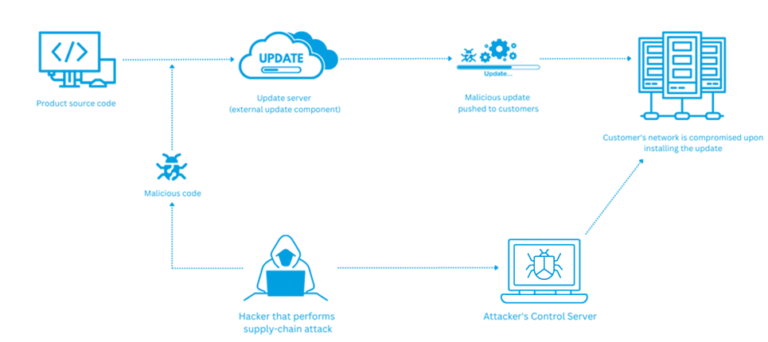
The four phases of a supply chain attack
A supply chain attack can occur through one of the most common methods, phishing. Phishing is a malicious practice used by hackers to deceive individuals into opening malicious links or attachments, with the aim of tricking them into revealing sensitive data.
There are four phases of how a supply chain attack occurs, including compromising the vendor, injecting malicious code, distributing it to customers, and data theft. Here is the flow:
- Compromising the vendor. Hackers compromise vendors by exploiting third-party dependencies and external update components.
- Injecting malicious code. Hackers inject malicious code into an external component used for distributing updates. The code acts as a backdoor to connect to remote machines.
- Distributing it to customers. The injected update will be distributed to customers’ sites in the next update cycle.
- Data theft. Now, when the update is distributed, attackers can access remote systems and make compromises and data theft.
This is the process that applies to any software or hardware supply-chain attack.
Dependencies Enabling Supply Chain Attacks
In IT the two main areas to focus on are hardware and software (including cloud services) vulnerabilities. When you buy computers, servers, storage, networking equipment, printers, surveillance cameras and so forth and you look inside you’ll see that they’re made up of components from dozens or hundreds of suppliers.
Any of those could be supplying the vendor you purchase from with malicious components, or they could have a vulnerability in them that’s found by criminals and then exploited.
Hardware dependencies
Physical machines are built with various hardware components manufactured by different vendors. Let’s imagine a server, it has a Dell motherboard, an Intel CPU, Broadcom and NVidia Ethernet adapters, and a Titanium power supply. These components all come from different vendors but are incorporated into a single physical unit. An attacker may target any of these hardware components and exploit them.
Examples include side channels attacks (Meltdown, Spectre, Ghostrace) that have plagued Intel, AMD and Qualcomm processors over the last few years, RowHammer and associated attacks on memory chips and BlackLotus bootkit attacks on the UEFI boot firmware of Windows PCs. These are not targeted at your organization but can be exploited by criminals to compromise your defenses, so you need to be aware of the risk.
While it’s unreasonable to expect run-of-the-mill businesses to inspect hardware they procure, if you’re a government or military contractor, handling highly sensitive information, hardware supply chain attacks are definitely something you need to include in your threat modeling.
Software dependencies
It’s been said that every business today is a tech business and it’s true. We all rely on software, whether it’s running on servers in our own datacenters, on our end user devices or we consume it as Software as a Service (SaaS) from the cloud. And unlike a physical hardware device that you can (at least theoretically) inspect to spot tampering, software isn’t something you can easily look at and see if it’s been interfered with.
If your organization has developers that write software, they will almost certainly rely on open-source software (OSS) components to build that software, for example, third-party frameworks and libraries. Modern software development is mostly integrating building blocks with some of your own business logic layered on top.
The risk here is that any of those blocks might be compromised, either on purpose to target your business specifically or more generally have vulnerabilities that can be used against you.
An attacker may compromise …
- source code repositories;
- compilers;
- Integrated Development Environments (IDEs);
- version control systems;
- package managers;
- build tools;
- Continuous Integration/Continuous Deployment (CI/CD) tools;
- testing tools;
- issue tracking systems;
- documentation tools;
- collaboration tools;
- code review tools, and others.
Hackers might also have compromised the software or hardware update mechanism, injecting a malicious piece of code, and pushing it to end users in the next update cycle.
As you can see, the potential weaknesses in all these layers are huge. If you’re not integrating continuous assessments of the safety of your underlying OSS and have processes for your developers to follow to update components regularly, you’re putting your business at risk.
Examples of Supply Chain Attacks
NHS Supply Chain Attack – 2024
A recent, horrific, attack was on the UK National Health Service (NHS) in June 2024. All the details are covered here, but in a nutshell, Synnovis which provides blood pathology testing and diagnostics was crippled by Qilin, a Russian ransomware gang.
They downloaded 400 GB of sensitive health data that they later made available publicly as Synnovis refused to pay the £40 million ransom. Over 6000 appointments / operations were disrupted. Criminals know that when people’s lives are at stake, victims are more likely to pay.
The NHS attack echoes the devastating attack on Change Healthcare in the US in February 2024 which interrupted patient care and medicine supply for months, costing billions overall.
The NHS attack is a prime example of a supply chain attack, none of NHS’s systems were compromised but one of the critical suppliers was unable to supply the service required, resulting in devastating impacts.
3CX in North Korea – 2023
A few years ago, a more widely targeted software supply chain attack by North Korean hackers was on the company 3CX, a supplier of video and voice calling software to businesses worldwide.
It turns out that this attack originated with the compromise of financial software company Trading Technologies whose application was running on a 3CX’s employee’s PC. So, one company’s application is compromised, which gains the attackers a foothold in the next organization, and through that business the compromised application update is distributed globally.
As for compromised hardware supply chains the scariest example is Operation Grim Beeper where Israeli intelligence inserted explosives into pagers used by Hezbollah terrorists (in an effort to avoid tracking they’d switched from smartphones to older technology) and detonated them all simultaneously, followed the next day by a similar attack on their walkie talkies.
MOVEit exploit – 2023
British Airways, BBC, and UK pharmacies (along with nearly 500 other companies) suffered a supply chain attack after attackers exploited MOVEit, managed file transfer software. British Airways spokesperson confirmed it in one of their public statements told to The Register „We have been informed that we are one of the companies impacted by Zellis’ cybersecurity incident which occurred via one of their third-party suppliers called MOVEit.”
SolarWinds – 2020
Back in 2020 we had another huge supply chain attack, where the company SolarWinds was compromised by Russian intelligence, and an update for their Orion network monitor application was altered, giving them access to every organization that followed standard practice and patched their software regularly, so that when the new version was signed as an official SolarWinds update, it contained the malicious code.
Further infiltrations into many companies and government organisations followed.
We conducted an analysis of the impact of different malware activities and published it our annual Cyber Security Report.

How to Detect a Supply Chain Attack
Detecting a supply chain attack is a challenging process since it includes not only your product but also other third-party components that are not fully in your control.
Implement monitoring
Monitoring helps you stay proactive by detecting any suspicious activities, unauthorized access, and changes in your infrastructure.
If you’re developing software in-house, adopt Security Development Lifecycle (SDL) for your DevOps process. Deploy monitoring everywhere and centralize logs to a Security Information and Events Management (SIEM) solution.
If you utilize SIEM in your infrastructure, you will be able to collect logs from different systems and analyze them accordingly. By using monitoring and SIEM, you can detect patterns in anomaly behavior so that your Security Operations Center is aware when attacks occur.
If you’re a smaller organization, consider using a Managed Detection and Response (MDR) service to monitor security for you.
Analyze end-user behaviour
Additionally, monitoring and SIEM, help you to analyze end-user behavior, perform network traffic analysis, and anomaly detection, and assess all potential layers of your infrastructure.
Key Cybersecurity Measures to Protect against Supply Chain Attacks
Thinking about the different attacks listed in this article, transfer those lessons to your organization. Think of the five largest suppliers you rely on, what if one of them disappeared tomorrow?
How quickly would your business be impacted, and how long could you manage without them? And do you have contingency plans so you can be resilient and continue operating without them? Also, plan for the scenario where they don’t disappear but are used to attack you directly because of the access they have to your organization.
Establish cyber security hygiene
Start by making sure cyber security hygiene baseline steps have been taken; phishing resistant MFA for all authentication, regular patching of software based on a vulnerability / exposure management program and a comprehensive XDR platform in place protecting all avenues of access into your organization. Understand the principles of Zero Trust and build your strategy around them: Least Privilege Access, Assume Breach and Verify Explicitly.
Implement Digital Signature Verification
Digital Signature Verification will help you to maintain the authenticity and integrity of software components and updates through signatures and certificates.
Stay ahead of supply chain attacks
You should definitely collaborate with cybersecurity companies, professionals, and the wider community to stay informed about supply chain attacks. A great way to do that is to follow our security lab and get notified in our monthly threat report about rising cyber threats.
As you can see, there are various proactive approaches, and it takes utilizing all of them to stay safe and effectively mitigate potential risks from supply-chain attacks.
Raise security awareness
The best way to get trained in IT is by experiencing things firsthand. So, you should simulate supply chain attacks in your network and challenge your organization with security awareness training. This practice ensures that you are well-prepared, well-educated, and able to implement security testing and enhancements.
Investigate your suppliers
Once you’ve got “your own house in order” investigate your suppliers. You need to ensure that they follow the best security practice that helps guard against any type of attack. If that is not the case, hackers may take advantage of their weak security:
- What’s their security posture?
- Do they have ways to communicate risk or breaches that affect you in a timely manner?
- What regulations are they compliant with?
- How do they secure the software they supply to you, or run it as a service you consume?
- Is it regularly tested by internal processes or external testing?
- Do they have a bug bounty program for their software?
- Do they regularly release patches for any vulnerabilities found?
And ultimately, you also need to be aware of your supplier’s suppliers, because there can be many different levels of suppliers for a single finished hardware (or software) product.
Today many software products are sold via marketplaces. Attackers might penetrate a marketplace and inject malicious code into the software before users download and install it on their network. Once installed, the network gets compromised.
Why Security Awareness is Crucial to Supply Chain Protection
The main lesson from the supply chain attack examples is resiliency. You need to build a company culture that’s resilient to interruptions, whether intentional supply chain attacks or any other disruptions that are common today.
Building a cyber resilient security culture isn’t easy and takes commitment, leading by example and time, but it’s possible, and frankly required in today’s increasingly dangerous world for businesses.
Our Security Awareness Service is a great place to start training your users to be vigilant when they receive messages. It’s built on an Employee Security Index (ESI) and tracks users’ actions over time, providing more training and more simulated phishing emails for staff that need it, building up vigilance in your staff, all automated, with very low administrative overhead.
How Hornetsecurity Can Help Secure Your Supply Chain
Our 365 Total Protection‘s comprehensive solution stack for managing email hygiene keeps your users safe from phishing, the number one attack vector attackers use. Pair this with a full breadth backup solution for your Hyper-V and VMware VMs on-premises or in the cloud, along with backup for your entire Microsoft 365 estate, optionally to immutable storage for strong protection against ransomware attacks.
Strengthen Your Defenses Against Supply Chain Cyber Attacks with Hornetsecurity
Supply chain attacks can severely impact your business, as seen with the NHS ransomware breach. Hornetsecurity’s Security Awareness Service is crucial for equipping your employees with the knowledge to recognize and avoid phishing and other social engineering threats. By enhancing your team’s awareness, you can significantly reduce your risk of falling victim to these attacks.

Request a demo today and discover how Hornetsecurity’s solutions can fortify your supply chain security!
Conclusion
Securing the supply chain is critical to prevent devastating cyber-attacks like the NHS breach. While technology and infrastructure improvements are important, proactive measures and employee awareness are equally vital.
By implementing the strategies provided, including assessing supply chain vulnerabilities and improving internal cybersecurity practices, organizations can significantly reduce the risk of cyber-attacks.
Hornetsecurity’s Security Awareness Service adds an essential layer of protection by training employees to identify and prevent threats, strengthening your overall security posture.
FAQ
A supply chain attack is a malicious attempt to compromise a business by infiltrating an organization that your business relies on for parts or services. Instead of attacking your organization directly, cybercriminals target a third party, such as a vendor or service provider, to gain access to your systems. For instance, if a Managed Service Provider (MSP) is compromised, attackers could use that access to infiltrate all of the MSP’s clients. Such attacks can lead to significant disruptions in your operations and, as seen in recent examples like the NHS incident, can have severe consequences for patient care and data security.
To protect against supply chain attacks, start with strong cybersecurity hygiene. Implement phishing-resistant multi-factor authentication, patch software regularly through a vulnerability management program, and invest in a comprehensive XDR platform to safeguard access points. Additionally, adopt the principles of Zero Trust: practice Least Privilege Access, assume that breaches might occur, and verify access requests explicitly. If you develop software in-house, integrate a Security Development Lifecycle (SDL) into your DevOps process and monitor your suppliers’ security practices closely.
User awareness training is crucial because a resilient company culture can help mitigate the risks associated with supply chain attacks. Employees need to be vigilant and equipped with the knowledge to recognize phishing attempts and other social engineering threats. Implementing a Security Awareness Service, which includes simulated phishing exercises and ongoing training, can help build this vigilance among staff. The goal is to foster a proactive attitude toward cybersecurity, ensuring that employees are aware of the risks and know how to respond appropriately.
