
Subdomains Takeover: Universities as a Threat Vector
Report overview
For several months now, Hornetsecurity has been thoroughly investigating an attack used on a massive scale by attackers: Subdomain takeover used in spam campaigns. This technique was first observed by Hornetsecurity in June 2022. More specifically, we are monitoring this technique with a focus on universities, as we have found that they are the most frequent target of a gang of spammers we have been tracking for some years. We are working with the targeted entities to help them correct these security flaws, fight spam, and improve security in cyberspace in general, whether for our customers, partners or beyond.
What is a subdomain takeover?
Subdomain takeover occurs when an attacker succeeds in gaining control of a subdomain of a specific domain. Typically, this occurs when the subdomain has a canonical name (CNAME) in its Domain Name System (DNS) records, but no host provides content for this subdomain. A subdomain takeover happens in the case of a resource that has been deprovisioned but has retained a CNAME in its DNS entries. After a certain period, the CNAME expires, and an attacker takes control by purchasing the domain name corresponding to the CNAME. The hacker can then use this asset to carry out malicious actions.
We will focus on the vulnerability, but other attacks can also occur, such as cross-site scripting, cookie theft, data theft, etc.
This is a serious vulnerability that needs to be addressed quickly and effectively.
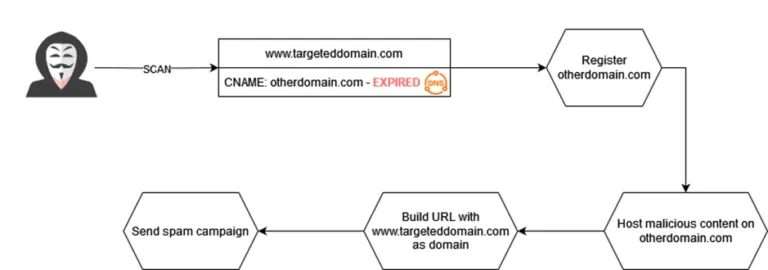
Here is an example timeline of events with fictitious domain names:
- An organization buys the domain “targeteddomain.com”.
- The organization adds the CNAME “otherdomain.com” to its website “www.targeteddomain.com”.
- The organization downgrades “targeteddomain.com” but forgets to delete the linked CNAME. At some point, the CNAME “otherdomain.com” expires.
- A threat actor detects the expiration and performs a registration for the domain name of the CNAME: “otherdomain.com”
- Since “targeteddomain.com” is always listed as the CNAME of “otherdomain.com”, the attacker will be able to perform malicious actions on behalf of “targeteddomain.com”.
Following is a real example of DNS record of an overtaken CNAME (Subdomains are redacted):
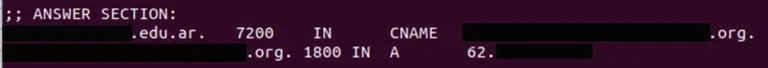
In this screenshot, we can see that the domain “xxx.edu.ar” has the CNAME “xxx.org” and this CNAME is resolving through the IP address “62.xx.xx.xx”.
At the time of the investigation, and by consulting the WHOIS, we can see that the main domain and the CNAME do not belong to the same organization. The CNAME linked to the domain “xxx.edu.ar” has been compromised by a hacker. In this case, the attacker hosted malicious content on “xxx.org” and sent URLs using the domain “xxx.edu.ar” in spam campaigns.
What can an attacker do?
If a hacker can take control of a subdomain belonging to a legitimate organization, they may be able to carry out certain attacks, such as stealing cookies belonging to the main domain, enabling them to perform session hijacking on the main domain. They may also be able to perform cross-site scripting or access protected/confidential content belonging to the legitimate organization.
These vulnerabilities have been public knowledge for years. Our incident response team has noted a recent upsurge in these attacks, which aim to transmit spam content with the primary goal of making money. We have seen numerous subdomain takeover attacks carried out against well-known and reputed universities all over the world (France, USA, Korea, Japan, Canada, UK…). The attackers want to take advantage of the important level of trust of the domain organization linked to the now malicious CNAME. In our case, the attacker will take advantage of a university’s reputation to avoid being blocked by security software during malicious e-mail campaigns.
The targets: Universities
There may be a multitude of reasons for targeting universities:
- Most universities have a high reputation and are trusted by the public. Compromised university domains or email addresses are of high value for cybercriminals. For instance, the MOZ domain authority of “berkeley.edu” (UC Berkeley) is 92 out of 100, which is higher than the score of the IRS (Internal Revenue Service) US federal government agency domain (91/100).
- Universities carry out academic research and thus have a lot of valuable IP (Intellectual Property). More generally, authorities warn periodically of the risk of espionage in academia.
- Universities are notoriously understaffed to monitor and efficiently protect such a perimeter.
During our investigations, we noticed that many of the stolen subdomains were linked to time-limited university projects/events that have now ended. Stolen domains often contain a year and/or a mention of an event specific to the targeted university in their name.
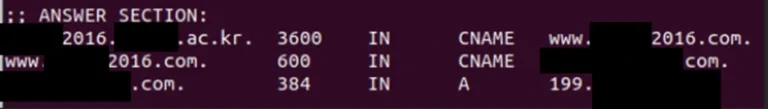
It is likely that once the project or event was over, the targeted university downgraded the domain and forgot to delete the linked CNAME. All the attackers had to do was re-register the subdomain under its own name once it had expired.
What are the consequences for the target?
One of the main dangers is that a subdomain of a trusted organization could be used in spam campaigns and can be used against its own users.

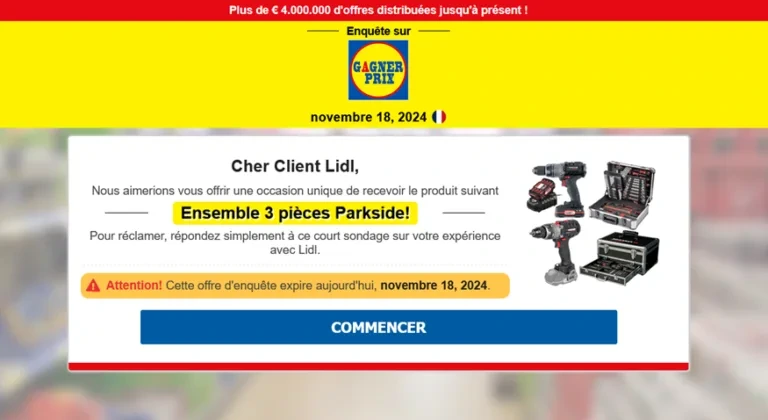
URL hosted on domains they trust can be very tricky for these users and greatly increases the likelihood of them falling into the trap, making them more inclined to click on the link.
The role of Hornetsecurity: Notify compromised organizations and protect organizations
At Hornetsecurity, we believe that cybersecurity is everyone’s business, and that no one should have to face it alone. That’s why we regularly contact entities (whether our customers/partners or external entities) to report security breaches. To date, we have sent over 160 security notifications concerning this vulnerability to targeted organizations. This also enables us to raise awareness of these issues and of cybersecurity in general. We have received a response for 19% of our notifications, and a correction has been made in 57% of these cases.
Additionally, our Spam and Malware Protection service, along with our cutting-edge Advanced Threat Protection technology play a critical role in identifying domains misused in email-borne attacks. Organizations protected by Hornetsecurity are well secured since we prevent such threats from reaching their users.
How to detect and prevent this security flaw?
DNS is often the blind spot in cybersecurity, and this is, in part, what allows this security flaw to be exploited on a massive scale. The best way to prevent a subdomain takeover is to remove unused (and therefore vulnerable) DNS entries. Ideally, to be truly effective and proactive, organizations should regularly check their subdomains and DNS entries. This would prevent many of these security vulnerabilities and their exploitation. It’s also worth mentioning that compromising an NS record presents a greater risk than other types, as it gives access to the entire DNS zone and domain.
Conclusion
In conclusion, this security flaw has been widely exploited, posing a significant risk to many entities. While most targeted organizations acted swiftly to address the issue, some failed to implement corrections even after being notified. Many others remained unaware of the flaw due to a lack of monitoring of their DNS records. To mitigate such risks, it is essential to regularly check your DNS records and actively monitor your services. Furthermore, responding promptly to security notifications is crucial to safeguarding your systems and data. Proactive vigilance is the key to staying ahead of potential threats.
