Spear Phishing – Malware From Your Boss
Spear phishing is considered one of the biggest cyber threats of 2018. How do criminals proceed to lure their target into the trap with tailor-made attacks? We explain what measures every internet user can take to make life difficult for the attackers.
Spear Phishing is considered to be one of the biggest cyber threats.
Spear phishing refers to tailor-made phishing attacks in which attackers attempt to exploit existing relationships of trust. Instead of attacking many people or institutions at the same time, the circle of targets is small: criminals prepare and execute spear phishing attacks individually, making it much more difficult to detect them. For example, they pretend to be your online payment service, email provider, or even a colleague, friend or boss. In this way, criminals are trying to steal sensitive data, retrieve passwords from counterfeit login portals or encrypt data and demand a ransom. This entails massive dangers for private individuals, but especially for companies. Attackers often use psychological tricks such as time pressure or curiosity, or exploit the helpfulness or obedience to authority of their victim.
Spear phishing attacks often follow a certain pattern:
Firstly, information is collected from freely accessible sources. These sources include social networks such as Facebook or Instagram, job portals such as Xing, LinkedIn or kununu, but also sources that are more difficult to control personally, such as news sites or the corporate website. For criminals, one thing is of particular interest: contacts. Who knows whom, which employees regularly exchange information, where do relationships of trust already exist? Information on the company’s position, past employers or interests is also used to make targeted phishing attacks as realistic as possible.
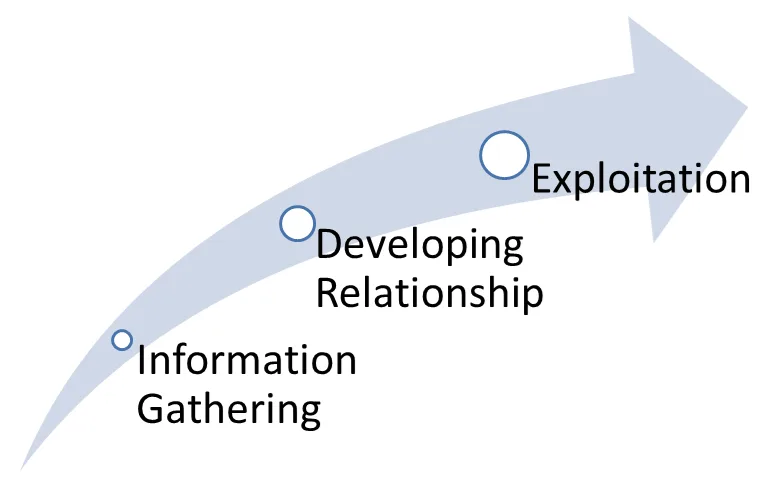
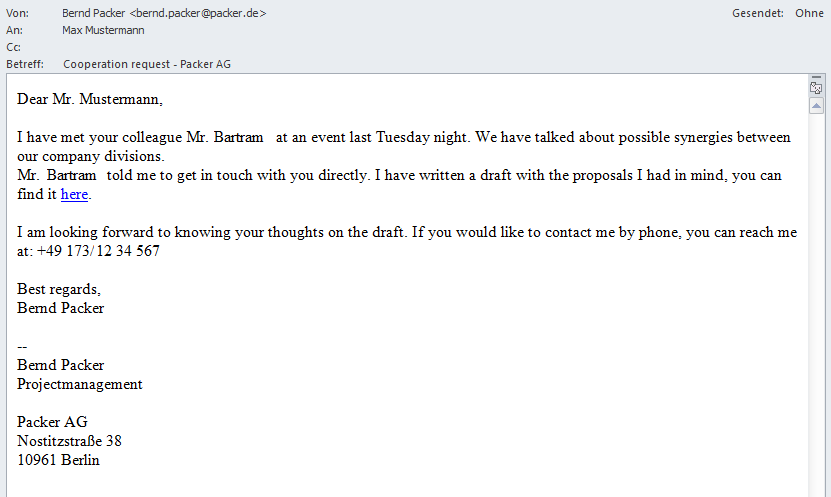
This part of the attack is called OSINT Nowadays, information about employees no longer has to be searched manually, but can be automatically collected, evaluated and used for attack scenarios. The next step of the attack is referred to as HUMINT (Human Intelligence): An attempt is made to establish a relationship of trust, e. g. by sending an email in the name of a real acquaintance. In most cases, the sender address of the email is as easy to forge as the sender address of a letter.
TECHINT Technical Intelligence) refers to the final step in which the relationship of trust is used to place a technical attack. Examples of this include sending links to infected websites or file attachments that unnoticedly execute malicious code when opened. Further information on how attackers proceed technically can be found in our whitepaper.
It can happen to anyone
Obviously, targeted attacks are particularly profitable when addressed to high-ranking representatives from business and politics. For phishing attacks on these “exceptionally large fish”, one also speaks of “whaling”. In principle, however, every employee in a company is at risk: For criminals, accessing a single computer on the network is often enough to cause extensive damage.
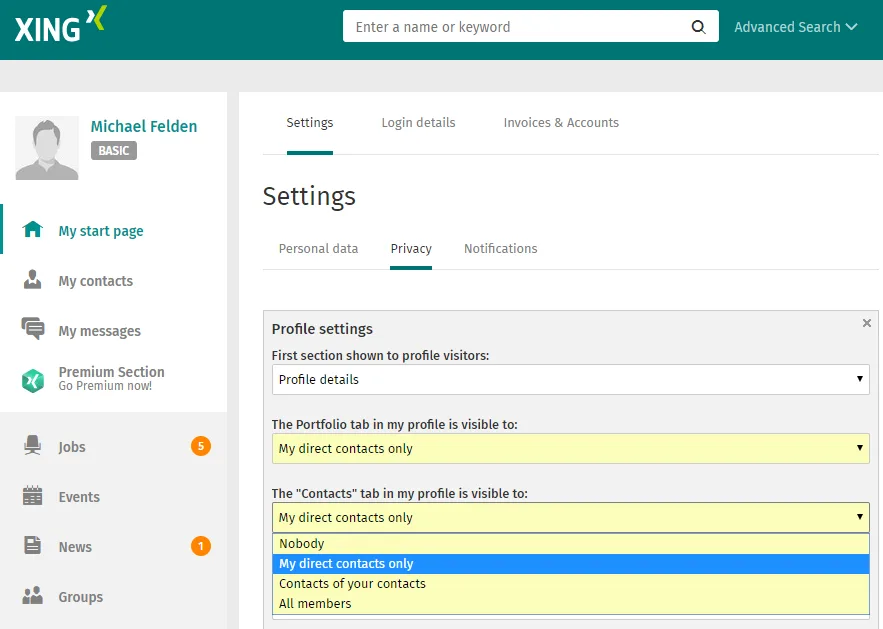
Data economy: How to give attackers a hard time.
Most people know that you shouldn’t share your Facebook photos with the public, but only with your friends. But what about job portals like Xing or LinkedIn? Especially on Xing, the default privacy settings are set in such a way that the contacts of a member can be viewed publicly. This may seem appropriate considering the network character of the portal, but at second glance it carries a great risk in terms of spear phishing attacks. Depending on whether you maintain a network of personal acquaintances on Xing or if you don’t check every contact request carefully, you should choose the privacy settings in such a way that only your contacts or just you, respectively, can view your contact list.