

How to Prevent a Data Breach by Training Your Employees
When a data breach happens, there are disastrous consequences affecting us as individuals or corporations. The digital world is vulnerable, and data breaches serve as a reminder that we must continually work towards stronger security measures.
Due to data breaches, many vendors and service providers who were hacked lost their customers, and numerous reputations were destroyed. It’s really painful when someone gains unauthorized access to our data in an unethical manner.
In this article, we’re going to cover data breaches, the different ways they can happen, and how you can protect your infrastructure from those sneaky hackers. So buckle up and get ready for some valuable insights.
Let’s first clarify some basics.
What Is a Data Breach?
A data breach is a threat to your infrastructure. It occurs when your data is compromised by malicious individuals or groups, commonly known as hackers or attackers. They use various techniques to gain unauthorized access to your infrastructure and compromise your data, either by destroying it, exposing it, or stealing it.
They do it for fun, to gain financial gains, or to feel challenged. Any reason you can imagine is unethical, and we should all come together to fight against it.
In June 2021, LinkedIn discovered that 700 million user accounts had been posted on a dark web forum, affecting over 90% of their customer base at that time. LinkedIn didn’t do it; someone else gained unauthorized access and leaked the information. This is what we call a data breach.
Data breaches occur around the clock, and if you believe that you are adequately secured or not a target because you are too small, you are mistaken.
Organizations need to ensure that they have strong security measures in place, ranging from the physical layer (physical server) to the application layer (web application).
How Do Data Breaches Happen
Data breaches can occur through various methods, and they are always initiated by attackers. In this section, we will provide a list of common data breaches that can happen anywhere. They include hacking, malware, insider threats, physical threats, third-party breaches, social engineering, phishing, weak password, misconfigured systems, and unsecured networks.
Hacking attacks involve attackers attempting to identify vulnerable systems, hardware, and services to exploit them. Once they successfully exploit a vulnerability, they gain unauthorized access to our infrastructure. To prevent such attacks, it is important to ensure that we have up-to-date systems and security policies in place to mitigate potential vulnerabilities and protect our infrastructure from unauthorized access.
Malware attacks occur when someone injects ransomware into our systems, encrypting our data and demanding payment to decrypt it. This is an ongoing cycle, and it is generally recommended not to pay the ransom but instead have proper backups in place, ideally immutable backups.
Insider threats refer to risks that arise from individuals or groups within the organization. They can take various forms, including physical or data theft, sabotage, unauthorized access, or careless behavior. To mitigate these risks, it is crucial to implement security measures that limit access to the principle of least privilege and block individuals from carrying out malicious actions.
Physical theft can occur as insider theft or external theft. To mitigate the risks, it is important to ensure that our disks and infrastructure are encrypted, and we should also implement physical security access controls and procedures.
Third-party breaches refer to attacks that do not occur directly but instead target partnerships with external vendors, suppliers, contractors, or service providers. It is crucial to ensure the strength of our partnerships and the security practices of our partners. We should ensure that third-party systems are fully patched and up to date.
Social Engineering is all about manipulating people to gain access to systems or information. In some other articles, we mentioned Kevin Mitnick. What he did was gain access to a banking system by compromising people and convincing them that he was IT support.
They believed him and gave him access to the system. He managed to hack them without using any technology. It is both scary and impressive at the same time.
Phishing is also a form of social engineering. It involves tricking people into opening links that lead to confirming their identity, password, credit card details, bank accounts, and other sensitive information. We all receive phishing emails in our inboxes. One of the best ways to fight against it is by knowing how to distinguish between legitimate and illegitimate emails.
Weak Passwords. There are plenty of websites on the internet that show default passwords for certain systems, hardware, and applications. So, the first rule is to change the default password to a stronger password. However, this is not the end of the game. IT teams should enforce policies to make their passwords stronger.
For example, implementing MFA (multi-factor authentication), enforcing password history, account lockouts in case of failed login attempts, password expiration, complexity requirements, and a minimum password length (e.g., 10 characters including both lowercase and uppercase letters, numbers, and special characters such as #, /, !, =, ), (, $, &.
Misconfigured systems refer to a system that is not properly configured without applying vendor or best practices. Misconfigured Systems are weak systems that hackers can easily compromise and gain access to. Some examples include unpatched systems, hardware, and applications; misconfigured SSL/TLS; inconsistent backup and recovery procedures; and others.
Unsecured networks are related to misconfigured systems. Unsecured networks are characterized by open Wi-Fi networks, weak encryption such as WEP, using default passwords, the absence of firewall rules, undefined access controls, and the lack of security systems such as IDS (Intrusion Detection System) and IPS (Intrusion Prevention System).
These are just a few examples, and it’s essential to maintain strong cybersecurity practices to protect against data breaches.
What Is Considered the Most Significant Data Breach of All Time?
If you ask any company that has been affected by a data breach, all of them would say it is the worst security breach one could imagine, and they would all be right. When it affects you, regardless of the size of your business, experiencing a data breach can be extremely painful and disruptive.
However, there are certain data breaches that have impacted millions of customers.
In 2013, Yahoo was attacked, resulting in the compromise of the personal information of more than 3 billion users. Attackers stole personal information, including names, birth dates, phone numbers, and passwords.
In 2017, Equifax, a credit reporting agency, was attacked by hackers who successfully exposed over 147 million customer records.
In 2019, hackers exploited Capital One’s firewall, leading to the exposure of over 100 million customer accounts. The breach involved the unauthorized access of approximately 140 thousand of Social Security Numbers (SSNs) and 80 thousand bank account numbers.
This is just to name a few.
The Importance of Employee Training in Data Breach Prevention
According to World Economic Forum – The Global Risks Report 2022, 95% of all cyber security breaches are caused by human error.
When it comes to cybersecurity, people make two types of common mistakes: soft-skilled errors and decision-based errors. Soft-skilled errors happen when someone doesn’t have enough technical know-how, experience, or skills while working on IT infrastructure or security-related activities. This falls into the responsibility of IT Teams.
Decision-based errors, also known as poor decisions, occur when individuals make choices that compromise cybersecurity. These mistakes can involve various actions, such as falling for social engineering and phishing tactics, or mistakenly sending emails to the wrong recipients. Typically, these errors are committed by end-users who lack security awareness.
How can data breaches be prevented?
Not-trained employees are vulnerable employees. The key to preventing data breaches is being proactive. It means staying educated, being aware, and taking security seriously.
Security is a shared responsibility that extends from IT teams and spreads throughout the organization. IT teams enforce security policies and procedures, and once those are in place, continuous education of employees becomes crucial.
Therefore, training end users about social engineering, phishing, password rules, and proper network connections is essential.
What is the importance of preventing data breaches?
The question to this answer is straightforward. The goal is to prevent attackers from compromising our data, protecting our reputation, ensuring a safe environment, increasing customer satisfaction, fostering loyalty, and maintaining smooth business operations.
Does the GDPR prevent data breaches?
One of the questions that arises regarding data breaches and GDPR is how they are related to each other. While the GDPR doesn’t directly prevent data breaches, it regulates the processes of handling personal and company data to ensure the implementation of security measures.
What are Recommended Data Breach Prevention Tools
First, it starts with the security equipment you use. Then, it extends to how you configure it, and finally, how your employees and end users are trained.
If you work in IT, you should ensure that you are running firewalls, intrusion prevention systems (IPS), intrusion detection systems (IDS), data loss prevention (DLP) solutions, endpoint protection, encryption tools, security information and event management (SIEM) systems, vulnerability assessment, and penetration testing (VAPT) tools, monitoring and logging solutions, backup and recovery mechanisms, and employee security training.
On top of that, we recommend you explore Hornetsecurity’s security toolkit. Here’s why:
Why Hornetsecurity Is Your Ultimate Solution to Help You Deter Potential Data Breach Risks
Security awareness training is a valuable tool in mitigating data breaches, minimizing human errors, safeguarding sensitive data, preventing unauthorized system changes, averting inadvertent actions, and ensuring effective information security protection.
At Hornetsecurity, we offer comprehensive security solutions that include fully automated awareness benchmarking, spear phishing simulation, and e-training. Our aim is to empower and protect your employees against cyber threats by providing them with the necessary tools and knowledge to enhance their security awareness.

By utilizing our security awareness service, your IT teams can conduct highly sophisticated spear phishing attack simulations. Our advanced engine offers various levels of difficulty, all of which can be conveniently controlled through a single user interface. With the results obtained, you can generate comprehensive reports that serve as a baseline for improvement.
Our security awareness service also enables targeted e-training for employees, delivering relevant content precisely when and where it is needed. Whether it’s minimal training for some or intensive training for key stakeholders, we cater to your specific requirements.
To ensure transparency and real-time monitoring, our service provides you with a security awareness health state, up-to-date statistics, and detailed ESI (Employee Security Index) reporting. Additionally, our customizable dashboard allows you to tailor the information and visuals to your preferences.
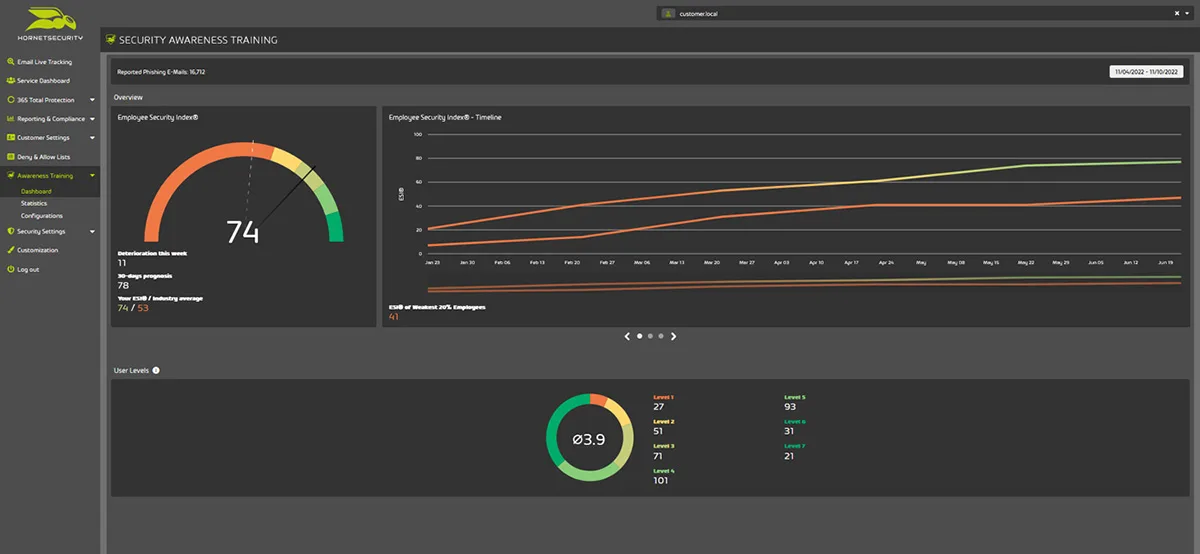
In addition, our services allow you to establish a dedicated security hub for your users, offering access to a wide range of training materials available in multiple languages and more. This proactive measure serves to minimize human error and prevent cybersecurity incidents caused by employee actions.
By providing your users with relevant resources and knowledge, we can significantly reduce the occurrence of employee security mistakes, decrease the risk of data leaks, and create a less hospitable environment for cyber criminals within your network.
You can learn more HERE.
We will be happy to show you a demo of our solution. Request it HERE.
Before we call it a day
To properly protect your cyber environment, use Hornetsecurity Advanced Threat Protection, and Security Awareness Service to secure your critical data.
We work hard perpetually to give our customers confidence in their Spam & Malware Protection, Email Encryption, and Email Archiving strategies.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
Since you began reading this article until the conclusion, thousands of attempts to breach networks have occurred. This non-stop activity is continuously triggered by attackers. When a data breach occurs, it results in the compromise of our data, which can have significant consequences such as financial losses, damage to our reputation, and a decrease in customer satisfaction.
There are different types of data breaches, including hacking attacks, malware attacks, social engineering, phishing, and more. Security is a shared responsibility. It is the responsibility of the IT department to implement secure measures and then train employees on how to handle them.
Training is not a one-time activity; it is an ongoing process.
At Hornetsecurity, we offer a comprehensive security awareness service that can assist you in securely staying ahead in the digital age.
