

Detecting and Preventing Password Spraying Attacks
Passwords are common ways of logging into the system, service, or application. They are typically used in combination with usernames to confirm user identity and gain access to target systems. Even though many of us know passwords should be strong and frequently changed, we don’t always follow the best practices until it is too late.There are several mistakes that lead to password attacks including weak passwords, password reuse, lack of policies, and others. Using the same password on multiple systems is problematic and opens the door for password spraying attacks.
In this article, we will discuss password spraying attacks, talk about the process, compare it to credentials stuffing and brute force attacks, and give you some tips on how to strengthen your credentials.
What is a password-spraying attack?
In 2018, an Iranian hacker group compromised six terabytes of sensitive documents from Citrix using password-spraying attacks. They deployed commonly used passwords across different devices, gaining access to systems and potentially introducing ransomware.
A password-spraying attack is a type of attack where attackers attempt to access a target device or system by using the most common passwords. Practically saying, an attacker takes a common password, e.g. „pass@123“ and spray it across multiple devices, systems, and application.
If the attempt is not successful, attackers would take a different password and repeat the process until they gain access to the target systems.
Some of the common passwords are password1, a1b2c3, qwerty, 1q2w3e4r, 1qaz2wsx, and others. The list of common passwords can be easily found on the Internet.
Password Spraying vs. Credential Stuffing vs. Brute Force Attacks
There are different types of password attacks, including password spraying, credentials stuffing, and brute force attacks. Sometimes they might look like exact types of attacks, but they are not. We already clarified password spraying, and we can move to the next one; credential stuffing.
Credential stuffing is a type of attack where attackers try to use valid breached credentials to access different applications. Practically, an attacker would obtain the list of breached (stolen) passwords from the Internet with valid usernames and passwords and attempt to log in to the target system.
Credential stuffing attacks rely on users using the same password for multiple different targets. In January 2023, 35,000 PayPal accounts were hacked using a credentials-stuffing attack.
On the other hand, brute force attacks are a method of using a list of different passwords to get into the system. Practically, an attacker would take a list of passwords and use them against the target one by one. These lists of passwords are available on the Internet and include millions of different combinations for different targets.
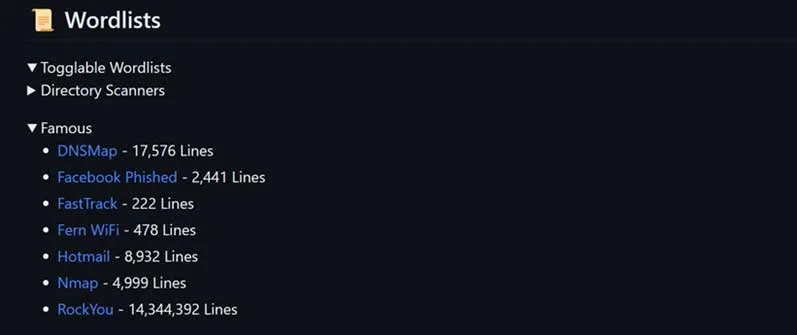
In the screenshot below, you can see there are 8932 potential passwords for Hotmail accounts, 2441 passwords for Facebook, and some other examples.
How Password Spraying Attacks Are Carried Out
Password spraying attack is a 4-steps process. Firstly, an attacker identifies the potential target, user, or organization. He does it based on varied reasons including motivations, opportunities, reputation, profit, and others.
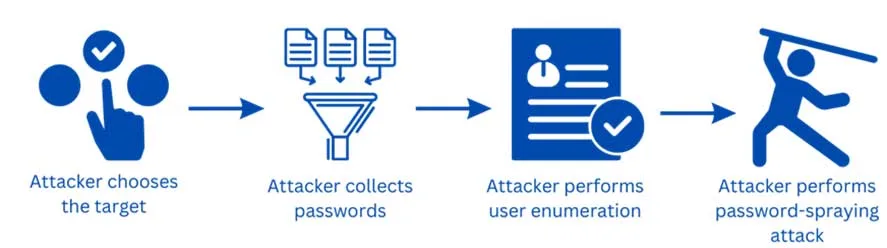
Once the attacker chooses the target, he or she collects the password list on the internet. Password lists can include common passwords, dictionary words, or previously breached passwords.
In the third step, an attacker performs user enumeration as part of the initial stage in the cyber kill chain and attempts to use a valid username, potentially facilitating the deployment of a computer worm.
Today, it is not that difficult to find potential SSO accounts, because much information is available on social media, forums, and different channels. Unfortunately, there are also companies who are selling our data to third parties.
In the fourth step, an attacker executes password-spraying attacks and tries to log in to different systems, services, and applications using a single username and multiple passwords, and vice versa. These usernames and passwords are based on step two.
During the process of a password spraying attack, an attacker is often intentionally making delays to avoid account lockout and being detected by IDS (Intrusion Detection System). Also, attackers perform monitoring to see the result of the attack.
In the last step, if attackers (we hope not) access the target system, they perform malicious activities such as installing malware, stealing data, spyware, encrypting files, and others.
How to Detect Password Spraying Attacks
Strong IT security is a must.
In the first place, you should ensure that end users are well-trained and understand the importance of a strong password policy. You can achieve that through ongoing cybersecurity training.
Our Security Awareness Service helps you train your users and keep them engaged with the different security simulations. That includes phishing attacks spread via phishing email, SMS, or QR code scams, social engineering, supply chain attacks, and different attacks. This is one of the ways attackers are stealing credentials, and then gaining access to a system or exposing them online.
Monitoring and logging are some of the best proactive ways to detect password-spraying attacks. They help to detect failed login attempts and inform the IT Administrator accordingly. For example, if there are 5 unsuccessful login attempts, the password policy locks out the user account, and the network monitoring solution triggers an alarm to the IT Administrator.
You can also create user baseline behaviour and learn information about login time, location, IPs, and patterns. Based on certain anomalies, for example, trigger CAPTCHA if there is a high number of login attempts from a single IP.
In case there is unusual behaviour in your organization, your SIEM (Security Information and Event Management) will pick it up.
You can also implement IDS (Intrusion Detection System) and Web Application Firewall (WAF) to detect and prevent malicious traffic from coming to your network.
How to Prevent Password Spraying
There are several ways that can help personal and business users to prevent password spraying attacks. Firstly, IT Administrators should ensure that different password policies are enforced in the organization. Some of the common password policies are as follows.
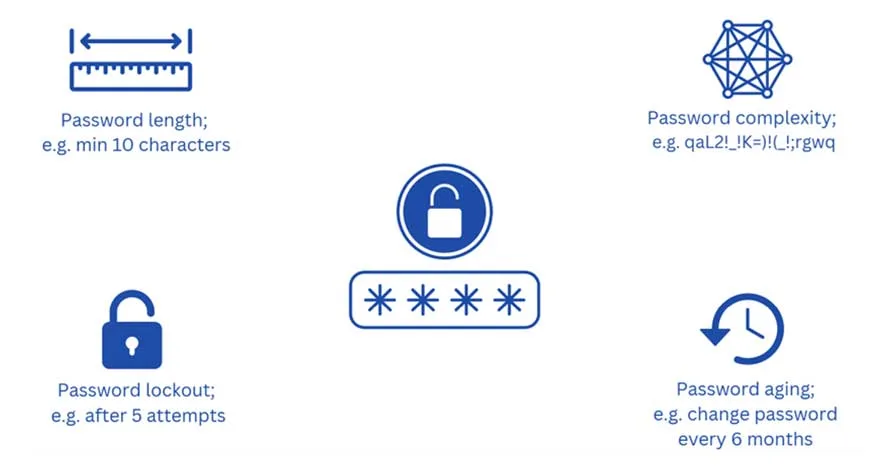
Password length
Password length policy defines a minimum number of characters for your password. For example, according to Microsoft a strong password is at least 12 characters long, but 14 or more is better.
Password complexity
Password complexity policy requires passwords with a combination of lowercase, uppercase, numbers, and special characters. A long and complex password is difficult to hack.
Password history policy
Password history policy prevents users from reusing their old password. This is important since old passwords might be leaked on malicious sites.
Password aging policy
Password aging policy requires changing passwords at regular intervals, for example, every 6 months.
Account lockout policy
Account lockout policy temporarily locks out an account after X amount of unsuccessfully login attempts.
MFA – multi-factor authentication
On top of the strong password, you should also implement multi-factor authentication (MFA). Multi-factor authentication provides additional layers of security such as PIN, biometric authentication, or physical device.
One of the next levels of the protection is implementation of password-less authentication. These includes FIDO (Fast Identity Online) keys and biometric solution such as Windows Hello for Business. This and more information you can find in our Cyber Security Report.
If your business services are exposed to the Internet, you should implement CAPTCHAs. CAPTCHAs help to distinguish humans from machines, and they help prevent boots from trying different passwords on the target system or the service.
How Password Spraying Affects Business
Many organizations are using SSO (Single Sign On) for different systems, and they are one of the potential targets for password spraying attacks. If an attacker gets to the password of any service, they can execute a password spraying attack and try to access other relevant systems and services. This can cause a lot of trouble to the organization, its data integrity, and its reputation.
There are a few negative effects on companies that are victims of password-spraying attacks. If accounts are compromised, there is a high probability, that attackers compromised the data. That leads to data breaches, loss of intellectual property, financial loss, reputation damage, operational disruption, and legal issues.
It is crucial to implement the abovementioned password policies to ensure password safety.
To properly protect your cyber environment, use Hornetsecurity Security Awareness Service, Spam & Malware Protection, and Advanced Threat Protection to secure your critical data.
We work hard perpetually to give our customers confidence in their Email Encryption, and Email Archiving strategies.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
We encourage you to check our ransomware attacks survey.
Conclusion
Passwords in combination with usernames help us to confirm user identity and login to the target systems. When an attacker gain access to the target device, they often lead to data breaches.
There are different password attacks including password spraying attack, credentials stuffing and brute force attack. Password spraying attack includes using commonly known password and spraying them across the devices in the organization. This is what differentiates password-spraying attacks from brute-force attacks.
There are different ways to protect your targets against password spraying attacks including strong password policies such as password length, password complexity, password history, password aging, and account lockout policy. On top of that, using multi-factor authentication (MFA) and password-less authentication is highly recommended.
Additionally, implementing CAPTCHA to differentiate humans from machines helps to avoid bots executing password attacks.
This article is about password spraying attacks, the back-end process, and how to stay safe.
FAQ
An example of a password-spraying attack is when the attacker uses one password (such as Hack#666) against multiple accounts on a given application. This is performed to evade account lockouts, which generally result from an attempt to brute force a single account with an array of passwords.
The success rate of password spraying is estimated to be approximately 1% for accounts without password protection in place.
Password spraying effects are as follows:
– compromises accounts;
– data breaches;
– unauthorized access;
– account lockouts;
– resource consumption;
– legal consequences.
If the victim uses the same password for multiple accounts, a successful spraying attack grants the attacker access to all those accounts.
SSO and federated authentication systems are particularly vulnerable to these attacks since a single password can provide access to multiple assets or accounts. In such cases, a compromised account can quickly compromise various systems and business accounts, making these attacks highly damaging.

