

Monthly Threat Report September 2023: The Demise of Qakbot?
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of August.
Executive Summary
- Our data shows that there was a slight decrease in threats for this report’s data period.
- HTML files continue to be the most common file type used to deliver malicious payloads. This was correlated with a continued decrease in the use of malicious PDF and archive files, likely due to the disruption of Qakbot.
- The entertainment and mining verticals were the most targeted industries over the past month
- DHL continues to be the most impersonated brand in phishing attacks, with noted increases in Netflix, Mastercard, and others.
- The FBI’s disruption of the Qakbot botnet will cause associated threat actors to use other botnets on the dark web.
- Microsoft has yet to release more details regarding the Storm-0558 breach, and the US Government has taken steps to investigate the situation.
- A French government agency and a software vendor in the gaming space both had breaches that accounted for the PII of roughly 14 million individuals being stolen by threat actors.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for August 2023 compared to July 2023.
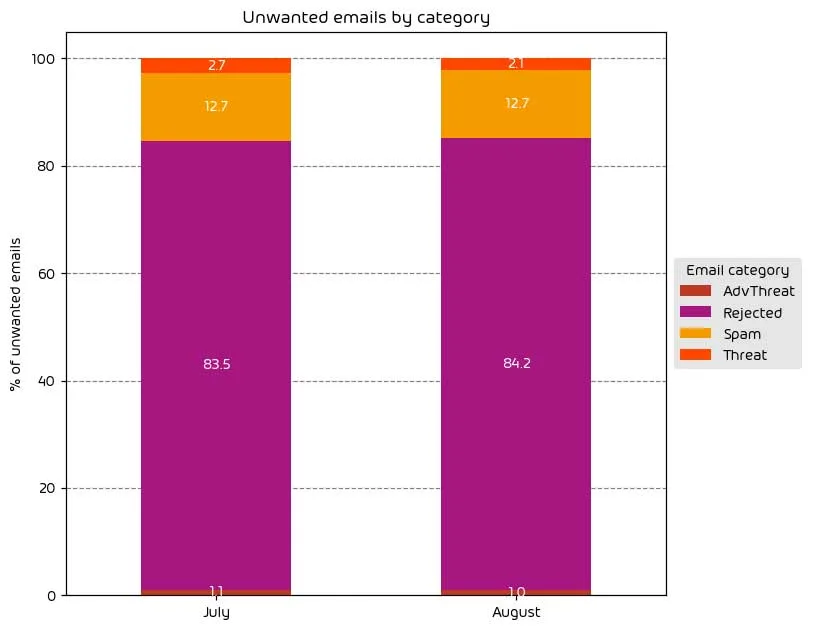
This month saw a negligible decrease in messages in the “Threat” and “AdvThreat” categories compared with July’s data. As a result, there was a slight increase in the “Rejected” emails for this data period.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File Types Used in Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
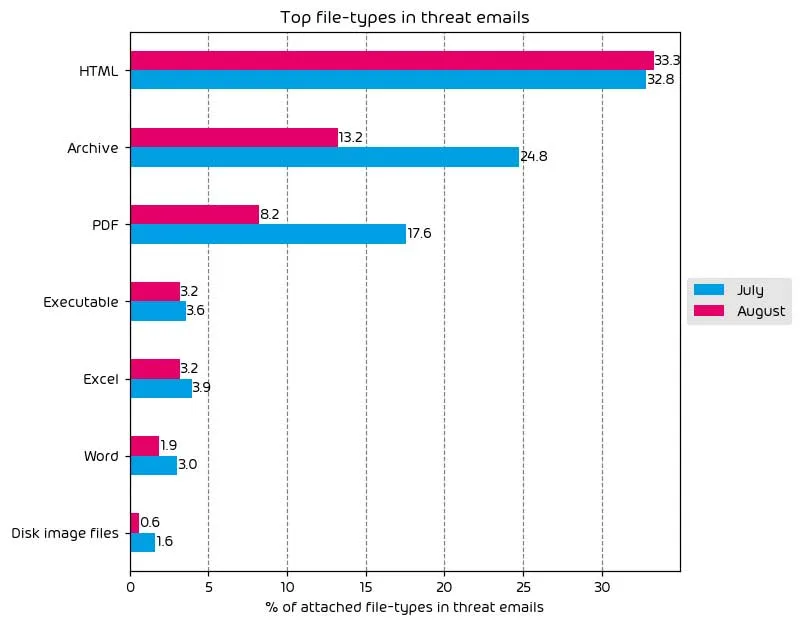
HTML files continued to see an increased trend in usage from previous months, while there has been a significant reduction in malicious PDF files and archive files. This can likely be attributed to the disruption of the Qakbot Botnet by the FBI because Qakbot frequently used PDFs as a means to infect new machines.
We continue to see a decrease in the use of Excel and Word documents to deliver payloads. We continue to attribute this change to Microsoft’s decision to disable macros in Office applications by default, which is a positive change for the industry.
Other notable changes over the last month include a noticeable increase in malicious archive files and slight increases in the use of Excel files, Word docs, and executable files. With this in mind, we continue to attribute the current low usage of Office documents for payload delivery as a direct result of Microsoft’s decision to disable macros in Office applications by default.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
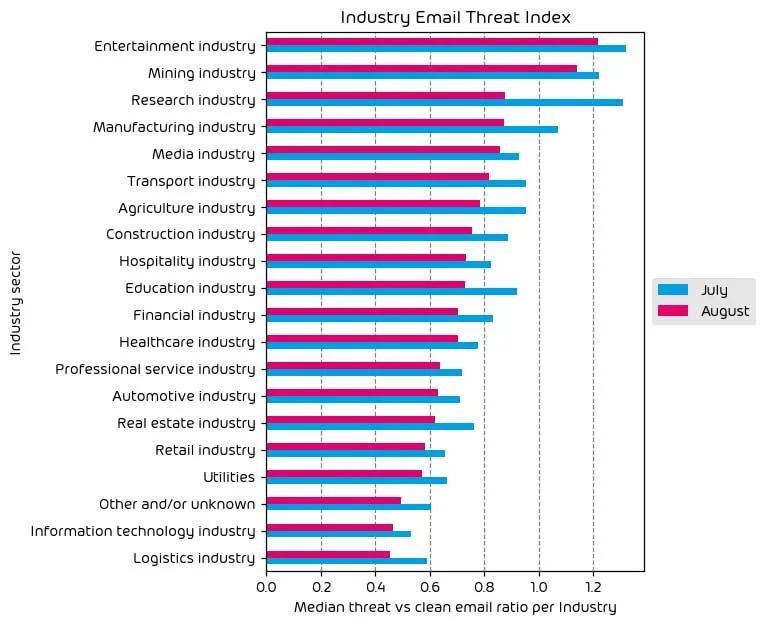
In a “reverse course” from the findings in our last report at the beginning of August, we saw a net decrease in the email threat index across all industry verticals during the month of August. This means fewer threats were targeted at businesses via email than the previous month. While we don’t see a specific reason behind this trend, it’s likely just a result of the usual ebb-and-flow of email-based threats throughout the summer months.
Regarding the top targeted industry, the entertainment sector remains in the number one spot from last month, with the Mining industry taking the second place. In a vast reduction compared to the previous report, we now see the research industry’s threat index coming in third place during the data period.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
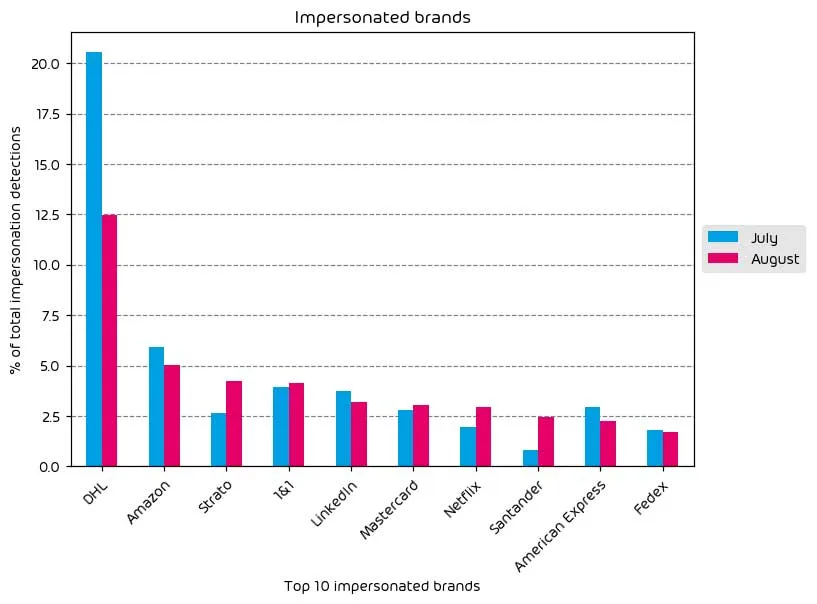
While there have been some changes this month compared with the previous data set, the top category areas for brand impersonation attacks remain roughly the same. Shipping companies, social media, and finance all continue to be popular brands for impersonation. This makes sense, given the value we place on these services as a society. Shipping is still increasing, social media continues to see heavy use, and finance will ALWAYS be a target area for threat actors.
That said, despite seeing a considerable reduction in DHL impersonation attempts during August, it remains the most impersonated brand BY FAR. Mastercard, Netflix, 1&1, Strato, and Santander all saw increases in brand impersonation attempts over the last month. Of particular note is a specific phishing attempt involving Netflix brand impersonation. The target is warned that their account has expired and that they should take action to extend their service “for free” for 90 days. Risk indicators for this attack are commonly the sender’s address (a Gmail address in the example below), and the associated link sends the user to a TinyURL address.

Major Incidents and Industry Events
As usual, there are several cybersecurity-related news items to discuss in this month’s report.
The Disruption of Qakbot
The most notable to discuss is the FBI’s disruption of the Qakbot Botnet. To quote the article:
The action represents the largest U.S.-led financial and technical disruption of a botnet infrastructure leveraged by cybercriminals to commit ransomware, financial fraud, and other cyber-enabled criminal activity.
For those who have followed Qakbot throughout its history, this really comes as no surprise. The FBI identified as many as 700,000 machines as having been infected by the Qakbot Malware. Of those, the FBI could use Qakbot’s software against itself because they sent uninstall signals to infected machines as part of the operation. Additionally, 9 million USD of cryptocurrency was seized as part of the operation.
To say this sounds like a resounding success would be an understatement. Qakbot is a botnet that threat actors have been using for years to launch attacks on various industry verticals and critical infrastructure, and it’s a botnet that we’ve kept a close eye on here at Hornetsecurity for some time as well. That said, there are two things to keep in mind:
- What new or existing botnet will threat actors turn to fill the gap left by Qakbot?
- Have all the command and control servers been taken down or been rendered ineffective by the FBI?
There are other botnets for threat actors to choose from, but only some have the reach and the capabilities that Qakbot did. Emotet malspam hasn’t been seen since April 2023, but knowing that botnet’s history and capabilities it’s possible we may see it emerge once again. It’s also entirely possible that a lesser known or completely new botnet will seek to fill the void as well. In either case we will continue to keep an eye on this space here at Hornetsecurity. If you’re interested in learning more about Emotet, we featured an episode on the Security Swarm Podcast. We’ve embedded the episode below if you’re interested:

Finally, regarding the question of whether or not we’ve seen the last of Qakbot? Botnets with the reach of Qakbot are challenging to eradicate. It looks like the FBI has dealt with the needed command and control servers, but time will tell if there are other dormant command and control servers out there. At the very least, Qakbot’s capabilities have been severely diminished.
More Data Breaches
It wouldn’t be a month in Cybersecurity without (at least) a data breach or two. Two worth noting, due to size, are PlayCyber Games and the French Government agency responsible for unemployment and financial aid both reported breaches that, when combined, accounted for nearly 14 million records containing PII.
Yes, breaches happen frequently, but governments worldwide are getting increasingly impatient regarding the private sector’s history of leaked data. The excuse of “An attack of unprecedented scale and sophistication” will only work so long, and as more individuals and agencies become impacted, the push to impose penalties and fines on negligent businesses will continue to rise, for example, it was reported near the end of 2022 that the Australian Government would be imposing harsher penalties for organizations that fail to take sufficient measure to protect customer data. More recently, it has been reported that the US government’s Cyber Security Review Board (CSRB) will be looking into Microsoft’s handling of the Storm-0558 fiasco that lead to the breach of multiple US government entities.
No organization likes the extra scrutiny from world governments, but the additional oversight can only be good in today’s cybersecurity ecosystem.
Microsoft Cloud – Storm-0558 Incident Update
September 8 Update
On September 6th, additional details regarding this attack were released by Microsoft. While the update does answer the question of how the consumer signing key was compromised, the remaining points and criticisms below, stand. The short of it is, a crash dump from the consumer signing system had been moved to a debugging environment and was subsequently involved in a compromise of an internal user account. One other item to note from this most recent announcement is this statement:
“Due to log retention policies, we don’t have logs with specific evidence of this exfiltration by this actor, but this was the most probable mechanism by which the actor acquired the key.”
Amazingly, the needed logs had not been retained due to retention policies, so full verification of said exfiltration could not occur.
That all said, what other news is there in the Storm-0558 saga since our commentary last month? In terms of official disclosures from Microsoft, there has been nothing official since their statement back on July 11th except for a July 14 technical analysis of the attack and it’s actors. While the article does provide some helpful info on the attack, its also clear (from what the article DOESN’T say) that Microsoft wants to move on from this issue.
Two of the remaining core issues left unanswered are focused on the compromised consumer signing key and the fact that higher tier logging licenses were needed to identify the attack within Microsoft cloud services.
Regarding the signing key, Microsoft states, “The method by which the actor acquired the key is a matter of ongoing investigation.” When it comes to logging, Microsoft has stated on July 19th that, “Today we are expanding Microsoft’s cloud logging accessibility and flexibility even further. Over the coming months, we will include access to wider cloud security logs for our worldwide customers at no additional cost.”
This begs the question, why wasn’t this level of logging included to begin with? Should the logs needed to monitor their environments be kept from customers behind licensing paywalls? Regardless, when it comes to cloud-based systems used by millions of users worldwide, trust is important. Microsoft’s handling of this situation clearly brings trust to the fore, and this breach will continue to be a topic of debate in the security space for some time.
We’ll continue checking on this issue in future Monthly Threat Reports.
Predictions for the Coming Months
- All eyes remain on Microsoft concerning the Storm-0558 breach and what changes, if any, will result as an effect of the US Government investigation. While investigations of this type drag on for some time, we anticipate some actionable items as a result. We may see some additional news from Microsoft on this case as well, but more likely, any additional communication will be in reaction to government findings.
- We also see it likely for other botnets to see an uptick in traffic in the coming weeks and months. The dark web doesn’t stop, and former “customers” of Qakbot will need to get those services elsewhere. Emotet seems a possible candidate, but time will tell.
- Even though there was little to report on in terms of AI-related security news from the past few weeks, investments and grant programs aimed at bringing AI to defensive cybersecurity tools are likely to produce results in the near future. We’ve heard so much recently about how threat actors can use AI, and it will be nice to see what the security vendors in the industry do with AI capabilities as well!
Note: If you’d like an example of how security vendors can make use of AI in their toolkits, we also recorded an episode of The Security Swarm Podcast that focused on the use of AI in defensive tools as well as the Emotet episode mentioned earlier in this report.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Yvonne Bernard, CTO, on the FBI’s Disruption of Qakbot:
The FBI’s disruption of the Qakbot botnet is a remarkable and impressive milestone in authorities’ countermeasures against Cyber Threats. However, history (E.g. with Emotet) has shown that this does not necessarily last forever. So, we must closely monitor Qakbot’s potential return while also keeping an eye out for the emergence of new botnets or any existing botnet with increasing popularity in the next weeks, months and years.
From Jan Bartkowski, Team Lead Security Architecture & Engineering, on Recent Data Breaches:
The recent amount of data breaches shows that the arms race between attackers and defenders is in full play as always. And more often than we all would like to see, the attackers succeed by being a step ahead or – maybe more often – some companies being a step behind. This highlights the constant necessity for companies to continuously invest into their information security posture. A defense in depth is mandatory to (hopefully) prevent the worst case scenario from happening in case that a single security measure fails. This includes not only IT systems but also the human workforce as even the most technically skilled engineers aren’t immune to making mistakes as e.g. Lastpass and Microsoft had to realize.
Monthly Recommendations
- Now is an excellent time to read up on common botnet threats like Emotet. With one of the major players (Qakbot) being removed from the space, we will likely see varied and potentially unknown botnet activity in the coming months. Following security best practices and partnering with a Trusted Security Vendor with a proven track record of identifying botnet threats can help mitigate the potential risks.
- If you’re a Microsoft Cloud customer, stay up to date on the latest logging mechanisms and changes as announced by Microsoft. Microsoft has claimed the needed mitigations are in place. Still, identity logging will be critical to ensure no lingering damage from the Storm-0558 breach.
- Impersonated brands continue to change monthly, making it difficult to defend against these types of phishing attempts. Keeping end-users updated with next-gen phishing simulation training can help keep your organization safe.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.


