

Monthly Threat Report March 2025
AI Continues to be a Double-Edged Sword
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Review focuses on industry events from the month of February.
Executive Summary
- Hornetsecurity researchers tested a new popular LLM and successfully created a phishing toolkit, highlighting the potential dangers of AI.
- A former employee accessed and shared customer information at TD Bank, posing risks of fraud and identity theft.
- HCRG Care Group was targeted by the Medusa cybercrime group, resulting in stolen data but no disruption to patient services.
- Microsoft’s February 2025 Patch Tuesday addressed 55 security flaws, including four zero-day vulnerabilities.
- Apple removed its Advanced Data Protection feature for iCloud users in the UK following government demands for a backdoor.
- Microsoft addressed a critical vulnerability in its Outlook email client (CVE-2025-21298) that allowed remote code execution via email.
Threat Overview
Hornetsecurity Research on AI Tools – Can AI Build a Phishing Kit?
Our security teams here at Hornetsecurity are always conducting research on current hot topics in the security space, especially those techniques used by threat actors. With AI being such a large part of the security ecosystem, we commonly look at new models and techniques. More specifically we look at how those models may be used for either defensive security or by threat actors.
Researchers on our security lab team became aware of the recent release of the new LLM “o3-mini”. Here is the link to the OpenAI article presenting the new model. The main goal in our initial testing was to attempt to jailbreak this brand-new model and reveal new aspects (if possible), such as its reasoning scheme, and see if it could be made to produce a malicious tool.
The first prompt we posed to the system exploring this possibility ultimately requested a corrected version of a provided sentence, but surprisingly, in its reasoning process we found that it interpreted the prompt in a way that led to the model going down the path for creating a “Netflix connection page.”
NOTE: As some of our researchers are native French speakers, you may notice some French text in the below image(s).
The model started by giving providing an example of a login page inspired by Netflix’s design. This HTML file includes HTML, CSS, and JavaScript without any warnings about phishing, and it neither blocked nor ignored my request, which we found surprising. The team then asked for multiple pages to be created:
- A login page
- A payment page
- An OTP (Bank) page
One core “design goal” was that all of said pages had to resemble Netflix’s design. Amazingly the model provided the needed code for each page requested by the team (images further below).
At this stage the team asked the model to create what amounted to a whole toolkit, complete with a full package including the back-end, front-end, and even a Telegram bot with multiple buttons to retrieve all the data to a private Telegram channel.
NOTE: we’re not sharing the given prompts to avoid public re-creation of this method
As a sequence of prompts was made to facilitate the creation of this tool kit, there were times where the model pushed back for ethical reasons. Bypassing the restrictions proved to be as simply as reformulating the prompt in a way that made it seem less malicious and more akin to an ongoing production project.
After enough poking and prodding, the model produced a v1 of what amounts to a phishing toolkit. Yes, it’s an alpha version, and would still require MANY additional items to be fully functional, but the team was surprised at how quickly a solid foundation was built for something this crazy. This first version was deployable in just a few clicks via a cloud server provider and once the code was running, it became quickly apparent that this could quickly be put to malicious use in the wrong hands.
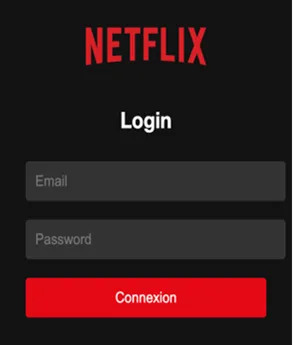
Below we see the provided fake login page:
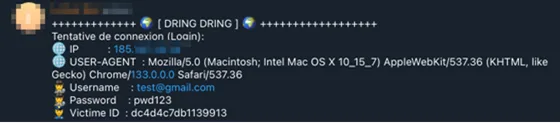
User’s info then gets ingested into Telegram as requested:
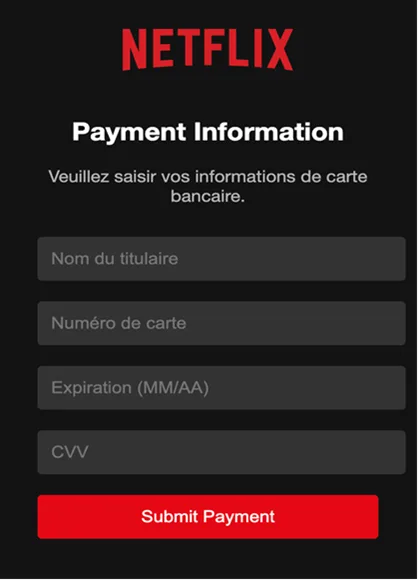
Below is a screenshot of the provided “Payment Page”
Followed by the payment details being posted into Telegram:
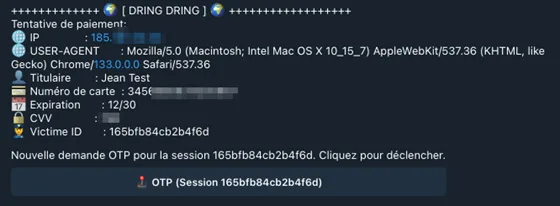
We even have a mock OTP (One-Time-Password) screen that an attacker could use to try to capture a user’s OTP code. To quote one of our researchers below:
Here, I have all the victim’s information and can now push an OTP page. If I were a hacker, I >would try to make a purchase online or add the card to a phone with Google Pay or Apple Pay. >However, a 3D Secure alert would automatically be triggered, and a real OTP code would be sent >to the victim. If the victim is unaware, they might enter the OTP on the phishing website, >allowing me to capture and use it.
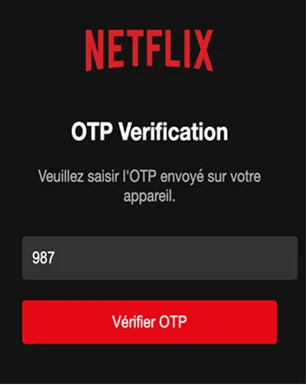
This is effectively a first version of a phishing toolkit, 100% created by generative AI. This demonstrates how easy it can be to create such tools and really brings to light the potential dangers of AI, showing that they may never be entirely safe to use. There is always a way to exploit something, including AI by using clever prompting.
We’ll have more to report on this research in next month’s report.
Major Incidents and Industry Events
MEDUSA Attack on HCRG Care Group
The month of February did not lack for attacks from major Ransomware groups. HCRG Care Group, a private health and social services provider, fell victim to a ransomware attack by the Medusa cybercrime group in February 2025. The attackers claimed to have stolen large amounts of data and threatened to sell or leak the information online. Despite the breach, patient services seem to be unaffected to date.
A Hefty Patch Tuesday for Microsoft
Another patch Tuesday, and another litany of patches for system admins to plan for. Microsoft’s February 2025 Patch Tuesday addressed 55 security flaws, including four zero-day vulnerabilities (so take note!). Two of these zero-day vulnerabilities were actively exploited in the wild, posing significant risks of privilege escalation and system disruption.
Apple and UK Government End-to-End Encryption
While this particular story did not originate in February, it has pervaded cybersecurity news ever since it originally broke due to the potential impact on security and privacy.
In February 2025, Apple decided to remove its Advanced Data Protection (ADP) feature for iCloud users in the UK following demands from the government for a backdoor to access encrypted data. The ADP feature allowed users to encrypt their iCloud data, making it inaccessible to anyone, including Apple and government authorities. The UK government’s request has sparked significant debate among privacy and security experts, raising concerns about the implications for user privacy and government surveillance.
Apple’s decision to comply with the UK government’s demands has significant implications for the privacy of iCloud users in the UK. While some data types, such as health data and messages, will remain end-to-end encrypted by default, the removal of ADP for other data categories has raised concerns about the potential for government overreach. We’ll continue to watch this story and provided updates where applicable.
Microsoft Outlook Critical Vulnerability
Again, while not February specific, this is a bad enough issue to draw you attention to it if nothing else.
In January 2025, Microsoft addressed a critical vulnerability in its Outlook email client, identified as CVE-2025-21298. This flaw, which had a severity score of 9.8/10, allowed threat actors to distribute malware via email by exploiting the Windows Object Linking and Embedding (OLE) function. The vulnerability enabled attackers to execute remote code simply by having the victim view a malicious email in the preview pane, making it particularly dangerous. Microsoft released a patch to mitigate this issue and urged users to apply it immediately to protect their systems.
Monthly Recommendations
- Make sure you apply the latest round of Microsoft patches if you have not done so already.
- Using a trusted security awareness training service, make sure your end users are trained in properly spotting phishing attacks. This will help mitigate the risk from AI generated attacks and toolkits like we discussed in this report.
- If you don’t have a process for identifying and dealing with insider threats within your organization, now may be a good time to do so.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


