

How will Microsoft Entra Change your Identity Security?
Out of the blue, and after the Build conference, Microsoft released a “new” service called Entra. In this article, we’ll look at what it is, why you should care, and how it will change how you do identity security.
Many security pundits have said many times over the last few years: “Identity is the new perimeter,” “Identity is the new firewall,” and strong identity authentication is a cornerstone of a Zero trust strategy. Certainly, Azure Active Directory (AAD), as Microsoft’s central identity directory, has been adapting more security features over the last few years, and indeed, AAD is one-third of Entra.
The second part is Microsoft Entra Permissions Management (MEPM? EPM?), based on the recent CloudKnox acquisition, and finally, there’s Microsoft Entra Verified ID for decentralized identities.
Let’s dig into what each of these offers and why you should consider using them.
Incidentally, if you’re wondering about the name, it’s an allusion to Entrance / gaining entry, and it ties in with two other name changes a little while ago – all the privacy-focused services in Microsoft 365 are now under the “Priva” name, and all the compliance features are under the Purview name.
Microsoft Entra Permissions Management
This cloud-based service is a Cloud Infrastructure Entitlement Management (CIEM) solution. It’s multi-cloud and can be connected to Azure’s, AWS’s, and GCP’s cloud identity and permissions systems. The basic premise is that there are so many permissions (40,000 across the three clouds, according to Microsoft) that tracking them manually is impossible to ensure that each assignment is privileged.
Instead, EPM (I’m going to stick with that) gives you a Permissions Creep Index (PCI), showing you the difference between assigned and used permissions for each user account, workload, or group. You can then easily right-size permissions to the required ones, lowering the gap between assigned and used permissions. There’s also an option to request permissions for those one-off situations where an administrator needs higher permissions for a particular task.
I set it up for one of my clients (who only uses Azure), and it’s fairly straightforward to start with. Obviously, it’ll appeal to larger businesses with many administrators, especially when they’re using two or three clouds. The problem EPM helps address is definitely an issue (ever heard of a breach of a cloud instance due to lax permissions?), and it’s nearly impossible to do manually. Having this automated tool gives you a visual way to see the gap between granted and used permissions, and that’s very helpful:
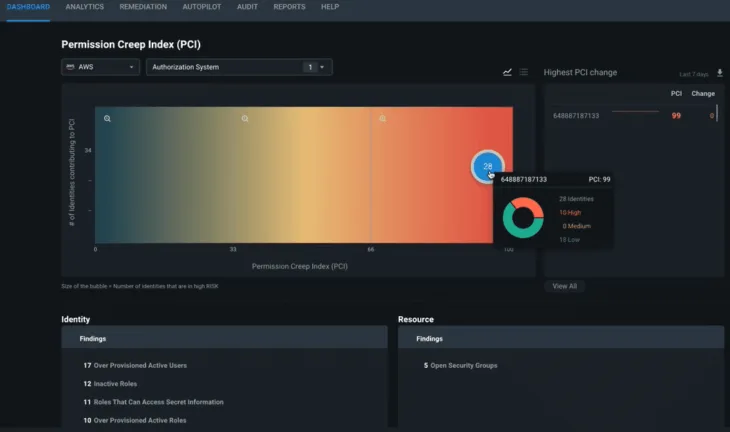
Permission Creep Index heatmapEPM is free during the preview – note that it’s not GDPR compliant at the moment and hence is not available in the EU, something that Microsoft will fix before it becomes generally available.
Azure Active Directory
Take a deep breath; your cheese is about to be moved –the Azure AD portal will disappear (I suspect). It’ll be replaced with the new Entra portal:
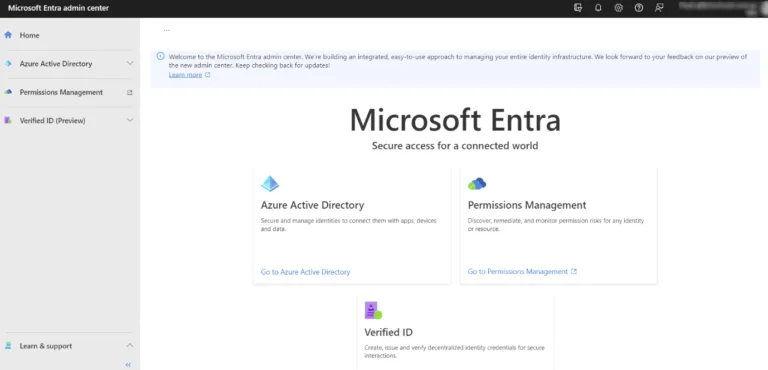
Microsoft Entra portalCurrently, this portal is in preview, but eventually, it’ll be the home for all identity-based UI actions. On the left, we have the three pillars of Entra, starting with AAD. Predictably, there are a lot more blades under AAD, which mirror most of the options in the current portal (legacy? classic?).
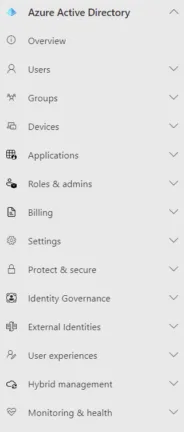
Azure Active Directory MenuAlthough it’ll take some time to re-learn where everything is, I do feel like this is a cleaner and more logical layout (although that’s often true when you make something new, and then as more features are added over time, more menu options shows up and it gets messy again).
If you’re used to the current Azure AD portal, there are no real surprises here. The External identities area, for instance, has links to the new Cross-tenant access settings and External collaboration settings. Once you open one of these blades, the menu layout is the same as in the AAD portal. Interestingly, Sign-in, Audit and Provisioning logs are now under Monitoring & health, and under Hybrid management, we find Azure AD Connect Health monitoring, including Active Directory DC monitoring.
Active Directory monitoring in the Entra portalAnother recent addition to Entra is protection for workload identities. Until now, there’s been a strong focus on user identity (MFA, passwordless) but less on application/automation/service, i.e., workload identity. This was brought into sharp focus in the SolarWinds hack, as the Russians used these types of identities to compromise their victims further. Sometimes, you’ll see these types of identities being referred to as non-human, which always makes me think of Klingons and Vulcans, but that’s probably just me.
For user identities, we have Identity Protection in Azure AD (Premium P2) which identifies anomalous behavior of user accounts and each sign-in (using Machine Learning). This is now extended to workload identities as well. Furthermore, we have Access Reviews where group owners or the users themselves regularly attest that they still need particular permission; again, this is now available for applications (by designated reviewers). Finally, Conditional Access is also available for workload identities.
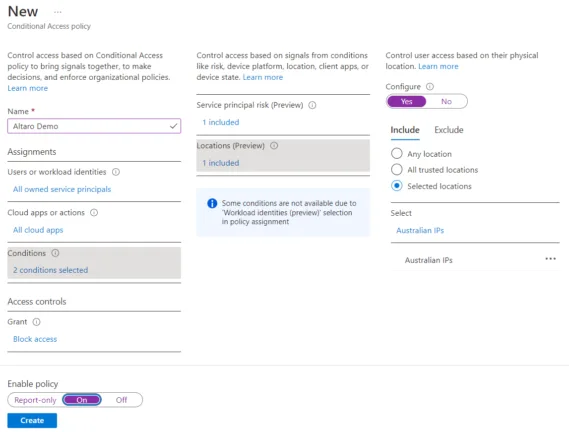
Conditional Access Policy for workload identitiesThere’s another preview currently for Lifecycle workflow, which manages the whole lifecycle of joining an organization, changing roles, and then eventually leaving through entitlement management.
Verified ID
This is possibly the part of Entra that will have the most impact on your work as an IT Pro going forward (it’s also in preview at the moment). It’s the result of a technology that Microsoft has been discussing for a few years now – decentralized identity.
Today, our identity is “owned” to a large extent by tech giants Google, Microsoft, Apple, and Facebook. For example, many users simply use an FB account to sign in to sites and services. But you’re not in control of your identity and can’t control exactly what data about you is being shared with various sites and services.
On the business side (where verified ID as part of Entra sits), consider the challenges of new hires joining your organization. How do you identify them, what documents do they need to show your HR department (and how do you do that in a work-from-home setting where they’re not physically present), and how do you authenticate those documents?
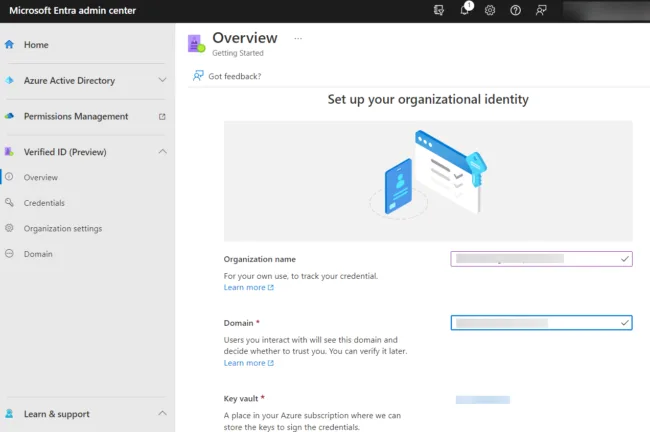
Setting up Verified ID in the Entra portalImagine if they had a verifiable identity that they could share with you, with exactly the right information you need (and no more), and that you could trust that identity because it’s cryptographically secured. That, in a nutshell, is a verifiable identity. There are many other scenarios, such as access to high-value resources and self-service account recovery, where a strong identity would be beneficial.
Microsoft has a click-through site that steps through an employee onboarding scenario, demonstrating the power of verifiable credentials and showing how much easier it is than today’s manual processes.
The current preview allows you to both issue and verify identities. The setup is fairly straightforward: you need to create an Azure KeyVault to store signing keys, etc., and you need to register an app in Azure AD.
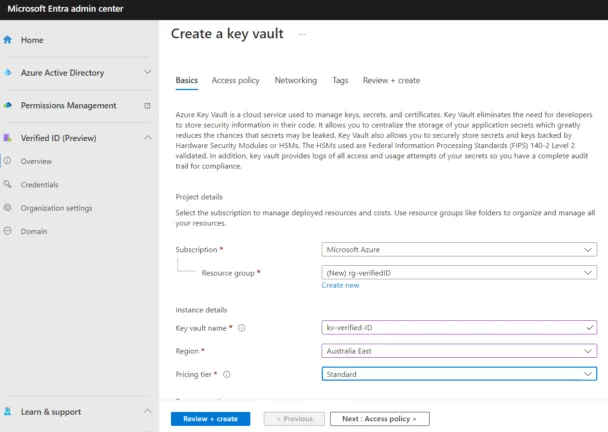
Create a key vault for verified IDSeveral verifiable credential organizations are currently supported, such as Acuant, Clear, Jumio, and others, covering 192 countries and over 6000 identification documents.
Conclusion
The cynic in me looks at this new portal and wonders if it’s a subtle way of “selling” the new CIEM solution – although the final licensing cost hasn’t been announced yet, we know it’s not going to be part of Microsoft 365 E5 or Azure AD Premium P2 licensing.
By moving everyone to the Entra portal, more users will be exposed to Permissionless’s Management, be curious as to what it can do, and eventually become paying customers. But maybe that’s too cynical a view. Maybe having one portal for identity, one for security, and one for compliance makes sense.
No matter what, Entra is here (at least in the preview). It’ll change some of your processes around workload identities, permissions management across clouds, and how you onboard new hires, plus other areas where decentralized identities will make your life easier. It’s exciting, and I can’t wait to see these services come out of preview so we can get a clearer picture of the licensing cost, scope, etc.

