
IT Pro Tuesday
FREE TOOLS & ADVICE EVERY WEEK
JOIN THOUSANDS OF IT PROS AND GET 5+ NEW FREE TOOLS, TIPS, HIGH-QUALITY ARTICLES, AND OTHER HAND-PICKED CONTENT TO YOUR INBOX EVERY TUESDAY
Welcome back to IT Pro Tuesday!
We’re looking for your favorite tips and tools we can share with the community… those that help you do your job better and more easily. Please share your suggestions on the IT Pro Tuesday subreddit, and we’ll be featuring them in the coming weeks.
Now on to this week’s list!
Top 5 IT Tools as of April 15th
Malware No More Tool
As a sysadmin, YARA empowers you to spot and categorize malware efficiently by crafting specific rules based on distinct patterns. It’s a go-to for keeping our systems secure!

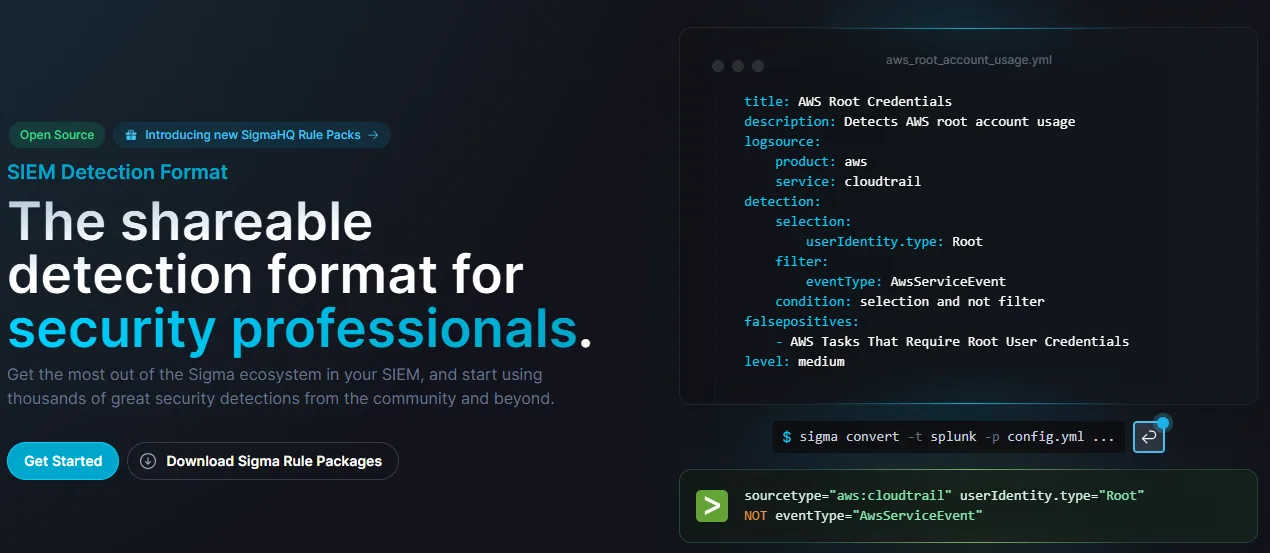
Bringing Clarity to Chaos with a Versatile Log Management Tool
With Sigma, any sysadmin can effortlessly develop detection rules that capture crucial log events. Sharing and collaborating on security insights has never been easier, making your job much more streamlined while enhancing team communication and response times.
Cyber Defense Command Center Tool
That’s correct, OpenCTI allows you to manage cyber threat intelligence seamlessly. Storing and integrating crucial information about threats keeps your defenses sharp and ready for any potential incidents. Don’t wait for problems to arise—take proactive steps to prevent them now!

The New Age of Web Servers
Running on H2O has transformed our web server performance. Its speed and efficiency mean lighter loads and happier users—an essential upgrade that we’re proud to have implemented.
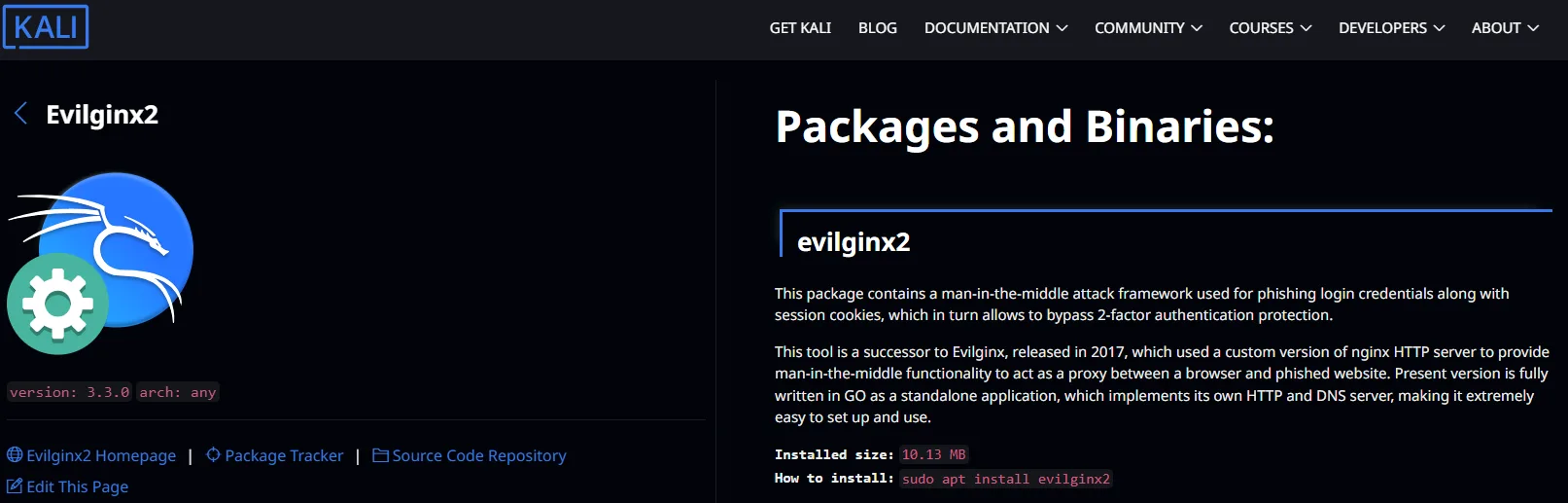
A Tool to Master Security Tests
Finally, we complete our list with Evilginx2, which is a chilling tool in every sysadmin arsenal, allowing you to simulate human-like interactions while bypassing security measures. It’s crucial for testing our defenses against sophisticated phishing attacks. Strongly say NO to any type of sophisticated cyber attack!
P.S. Bonus Free TOOLS/RESOURCES
With AutoHotkey, you can create scripts that range from simple to complex, which you can then compile. It allows you to perform a wide variety of tasks, from basic scripting to Robotic Process Automation (RPA), thanks to its capability to call complex functions. It’s also very user-friendly, making it accessible for beginners in scripting.
The cybersecurity subreddit (r/cybersecurity) offers valuable insights for sysadmins by fostering discussions on the latest threats, research, and news. It helps you stay informed about evolving security challenges, enabling proactive measures to effectively protect your systems and networks.
Dear IT-Professional,
The world of technology changes quickly. Staying ahead means having the right tools, insights, and strategies at your fingertips. That’s where IT Pro Tuesday comes in.
Every Tuesday, we deliver a curated selection of free resources, expert advice, must-read articles, and essential updates – all designed to help you work smarter, solve problems faster, and stay at the top of your game.
Whether you’re a seasoned IT professional or just looking to sharpen your skills, this newsletter ensures you never miss out on game-changing tools and insights.
Sign up now – it’s free, and it could be your smartest move this week!
Access to exclusive content
In addition to the free tools, you will also receive links to high-quality cybersecurity content, providing crucial insights to help you defend against the latest cyber threats. This includes free access to valuable resources such as articles, eBooks, detailed analyses, actionable recommendations, case studies, white papers, webinars, videos and more.
JOIN THOUSANDS OF IT PROS AND SIGN UP TODAY
Sign up now!
"*" indicates required fields
Access to exclusive content
In addition to the free tools, you will also receive links to high-quality cybersecurity content, providing crucial insights to help you defend against the latest cyber threats. This includes free access to valuable resources such as articles, eBooks, detailed analyses, actionable recommendations, case studies, white papers, webinars, videos and more.
Curious how the newsletter looks like? Have a sneak peek what to expect:
Note: we have no affiliation with any of the third-party tools or resources shared unless explicitly stated. We scour popular forums and online groups to identify the most highly recommended and rated resources from the IT community and from our own highly skilled team.
More about Hornetsecurity
What you can expect
As an expert in cloud security, we regularly inform our subscribers about the latest changes in IT security. This includes current blog posts, press releases, technical papers and other relevant security information.
Tracking and Transparency
We always strive to provide our website visitors and subscribers personalized information. We constantly improve our offerings and knowledge base, so that you have the best user experience possible while browsing our website.
Double-Opt-In / Opt-Out
After you register, we will send you a confirmation email. This notification includes a link to confirm receipt of Hornet News (Double-Opt-In). In addition, subscribers have the opportunity to cancel their free subscription at any time. At the end of each email you will find an unsubscribe link (Opt-Out).
Privacy Policy
Detailed information on the collection, storage, processing of information and the possibility of withdrawal can be found in our privacy policy.
