
IT Pro Tuesday
FREE TOOLS & ADVICE EVERY WEEK
JOIN THOUSANDS OF IT PROS AND GET 5+ NEW FREE TOOLS, TIPS, HIGH-QUALITY ARTICLES, AND OTHER HAND-PICKED CONTENT TO YOUR INBOX EVERY TUESDAY
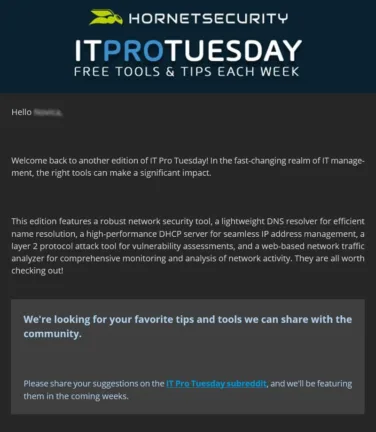
Welcome back to IT Pro Tuesday!
We’re looking for your favorite tips and tools we can share with the community… those that help you do your job better and more easily. Please share your suggestions on the IT Pro Tuesday subreddit, and we’ll be featuring them in the coming weeks.
Now on to this week’s list!
Top 5 IT Tools as of July 29th
Breaking Free from One-Size-Fits-All
We commence this edition with Rex, a framework that provides sysadmins with customizable automation options for local and remote tasks, recognizing their unique needs. This flexibility fosters personalized solutions, boosting efficiency and satisfaction in daily operations.
Enhancing Configuration Management
Salt Formulas enable sysadmins to easily manage configurations and deploy applications efficiently, facilitating effortless remote command execution and consistent infrastructure management.
Your Proven Command to Find Duplicate Files in Directories
Fdupes transforms the challenge of organizing your file system into a simple task, giving you clarity and easy access even among a sea of files. By eliminating duplicates, fdupes accelerates your backup processes and minimizes resource drain, making your life easier. Plus, it helps you reclaim valuable disk space for the apps and data that matter most, resulting in a more efficient workflow.
Backup Management Made Easy
With the ability to create multiple profiles in a single configuration file, sysadmins can easily implement tailored backup strategies for different needs. Resticprofile takes the hassle out of managing backups, allowing sysadmins to effortlessly create and modify profiles without memorizing complex commands.
Why TUF Should Be Your Go-To Update Framework
And finally, The Update Framework (TUF) should be your go-to framework because it enhances security for software updates by protecting against compromised repositories and signing keys, ensuring the integrity and reliability of deployed software.
P.S. Bonus Free TOOLS/RESOURCES
Let’s Debug provides a set of tests to help determine why you may not be able to issue a certificate for Let’s Encrypt. You enter the domain and validation method to identify problems with basic DNS setup, name servers, networking issues, rate limiting, CA policy issues, and common website misconfigurations.
CherryTree is a versatile notetaking application that resembles a hierarchical wiki, designed to help users effectively organize a wide array of information such as notes, bookmarks, and source code. With the added capability to prioritize information, CherryTree empowers users to manage their ideas and projects with ease and efficiency, making it an ideal tool for students, professionals, and anyone looking to keep their thoughts in order.
Dear IT-Professional,
The world of technology changes quickly. Staying ahead means having the right tools, insights, and strategies at your fingertips. That’s where IT Pro Tuesday comes in.
Every Tuesday, we deliver a curated selection of free resources, expert advice, must-read articles, and essential updates – all designed to help you work smarter, solve problems faster, and stay at the top of your game.
Whether you’re a seasoned IT professional or just looking to sharpen your skills, this newsletter ensures you never miss out on game-changing tools and insights.
Sign up now – it’s free, and it could be your smartest move this week!
Access to exclusive content
In addition to the free tools, you will also receive links to high-quality cybersecurity content, providing crucial insights to help you defend against the latest cyber threats. This includes free access to valuable resources such as articles, eBooks, detailed analyses, actionable recommendations, case studies, white papers, webinars, videos and more.
JOIN THOUSANDS OF IT PROS AND SIGN UP TODAY
Sign up now!
"*" indicates required fields
Access to exclusive content
In addition to the free tools, you will also receive links to high-quality cybersecurity content, providing crucial insights to help you defend against the latest cyber threats. This includes free access to valuable resources such as articles, eBooks, detailed analyses, actionable recommendations, case studies, white papers, webinars, videos and more.
Curious how the newsletter looks like? Have a sneak peek what to expect:
Note: we have no affiliation with any of the third-party tools or resources shared unless explicitly stated. We scour popular forums and online groups to identify the most highly recommended and rated resources from the IT community and from our own highly skilled team.
More about Hornetsecurity
What you can expect
As an expert in cloud security, we regularly inform our subscribers about the latest changes in IT security. This includes current blog posts, press releases, technical papers and other relevant security information.
Tracking and Transparency
We always strive to provide our website visitors and subscribers personalized information. We constantly improve our offerings and knowledge base, so that you have the best user experience possible while browsing our website.
Double-Opt-In / Opt-Out
After you register, we will send you a confirmation email. This notification includes a link to confirm receipt of Hornet News (Double-Opt-In). In addition, subscribers have the opportunity to cancel their free subscription at any time. At the end of each email you will find an unsubscribe link (Opt-Out).
Privacy Policy
Detailed information on the collection, storage, processing of information and the possibility of withdrawal can be found in our privacy policy.
