

Immutable Backups Explained – Why Are Immutable Backups Critical
Data is a business currency. If data becomes corrupted or infected by ransomware, the business may face significant disruptions or even potential failure. In June 2021, Fujifilm had to close down a section of its global network due to ransomware. Emails, phones, and services were non-operational. This is just one scenario among many unfortunate ones caused by bad actors.
According to the ransomware analysis we conducted in 2022, organizations targeted by ransomware attacks either lost data (14.1%) or had to pay a ransom to recover data (6.6%).
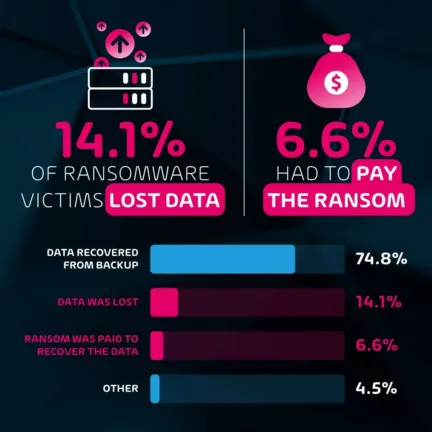
Even data in backups is not immune to the risk of being infected by the ransomware attack, especially when using mutable backups. On another hand, by using immutable backups in your backup environment, you can secure your backup data from altering, and keep data safe even in the case of a ransomware attack. Secured data can’t be encrypted or corrupted by ransomware on your systems.
Hornetsecurity’s acquisition of Altaro, the rapidly expanding global backup solutions provider in 2021, resulted in the introduction of this impactful offering.
This article is about immutable backups and how this technology can help organizations keep their data in data centers or the cloud far away from malware.
How Companies Prevent Data Loss Using Advanced Ransomware Protection
Ransomware attacks have been a threat since as early as 1989, which indicates that they are not a recent issue. However, in recent years it’s gone from a minor issue to a large threat for businesses of any size, mainly because of the large amounts of money involved and the “ease of payments” through cryptocurrency. If your data gets infected by ransomware, it becomes unusable, and the only way to unlock or recover it is by paying the hackers. No one can guarantee that if you pay, they will unlock it, or if they do unlock it, they won’t hack your network again. That sounds like a malicious never-ending loop. Doesn’t it?
Ransomware can originate from various sources and be delivered through different types of files. We analyzed over 25 billion emails and found that 39.6% of emails are flagged as phishing emails, which if not caught might lead to the first step of a compromise of your network.
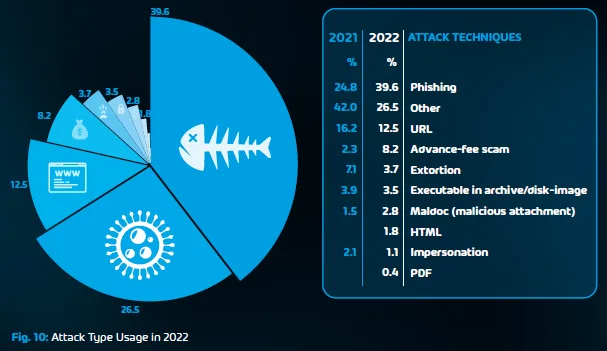
You can read all the details in our Cyber Security Report 2023: An In-depth Analysis of the Microsoft 365 Threat Landscape.
How can the risk be mitigated?
The risk is huge, and a recurring question is how to mitigate it. Organizations implement various methods to secure their systems and files against ransomware. These methods include endpoint security, advanced threat detection, and response, patch management, implementing multi-factor authentication (MFA), immutable backup, employee training and awareness, and others.
Combining these methods provides a promising defense against ransomware attack.
Let’s now unpack immutable backup which is the focus of this article.
What is immutable backup?
Ransomware attacks have evolved to the point where they can target and compromise backup data as well. According to a recent study 2022 Ransomware Attack Analysis conducted by Hornetsecurity, it was found that 15% of ransomware attacks were specifically aimed at compromising backups. That is concerning because we all rely on backups in case our data gets lost or corrupted.
No need to panic; there is a solution against ransomware backup attacks called immutability or immutable backups. Immutable backup refers to backup data that can’t be altered, deleted, overwritten, or modified. In terms of ransomware, immutable data (immutable copy) provide an additional layer of security, effectively blocking ransomware from altering or locking your backup files.
Immutable copies are stored in immutable storage, which together guarantees backup immutability while allowing organizations to secure their data and helps mitigate the risk of data corruption. Authenticated APIs are typically used to secure access to immutable data by requiring authentication credentials.
Immutable data can be used in any industry. For example, imagine how many problems immutable backup technology could solve by protecting critical medical, pharmaceutical, and scientific data in healthcare organizations.
Immutable backup copies are unchangeable and can be restored to the production servers immediately in case of any issues with the data or ransomware.
The period of time for protecting immutable backup copies can vary depending on the specific requirements and policies of an organization. It may be set to a fixed duration, such as 30 days, or align with a regulatory or legal retention period.
Once the specified period elapses, the immutability of the weekly backup will be lost.
How are immutable backups different from mutable backups?
Mutable backups are conventional backup data stored on the backup storage that can be altered, modified, and overwritten. That also means that bad actors can access, change or delete user or company data if the system or network is compromised. There is no data security. Hackers can delete data and change their integrity. In most cases administrative accounts are required but in a succesful network compromise by an attacker, they compromise your entire Active Directory (or other identity system) and can effectively create any account, with any level of permissions they need.
From a security perspective, immutable backups should always be a priority.
Are immutable backups safe?
Generally, immutable backups provide an additional layer of security to your data, making them more secure. However, it is worth mentioning that the implementation of backup and storage should be done by following vendors’ best practices. Additionally, it is recommended to implement additional IT security measures for enhanced protection, such as requiring Multi Factor Authentication (MFA) for all administrative accounts.
Immutable storage guarantees instant protection of your data and ensures that your data cannot be modified by ransomware sent by bad actors.
What are examples of immutable backups?
There are several examples of achieving data immutability backups including WORM, backup storage (cloud, offline backups), and versioned backups.
Write-Once-Read-Many
WORM stands for Write-Once-Read-Many, which means that a backup copy can be created only once (write) and then becomes read-only. In other words, ransomware cannot alter backup files because of the storage mediums inbuilt immutability.
Immutable cloud storage
Immutable cloud storage is a type of storage that ensures data integrity and prevents any modifications or deletions. Practically speaking, the data saved to cloud storage is protected by backup immutability and can’t be changed.
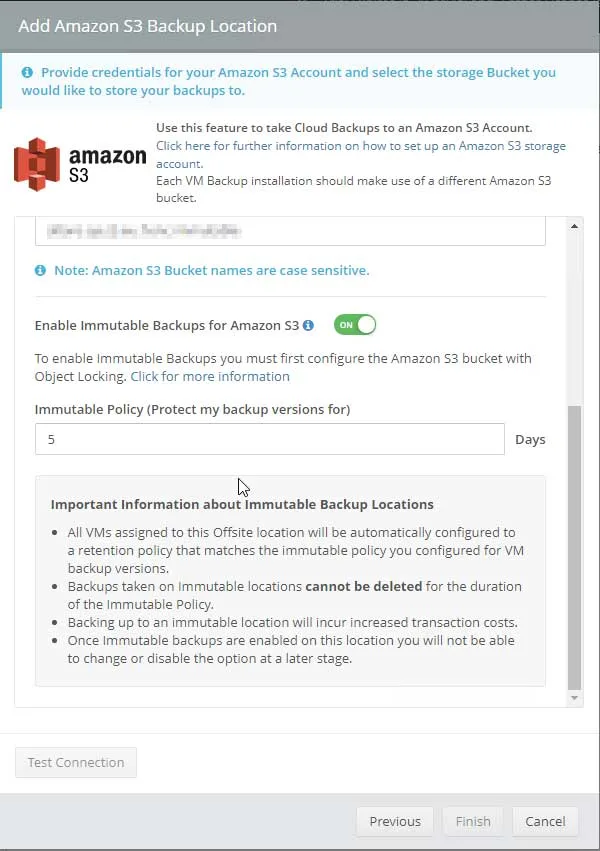
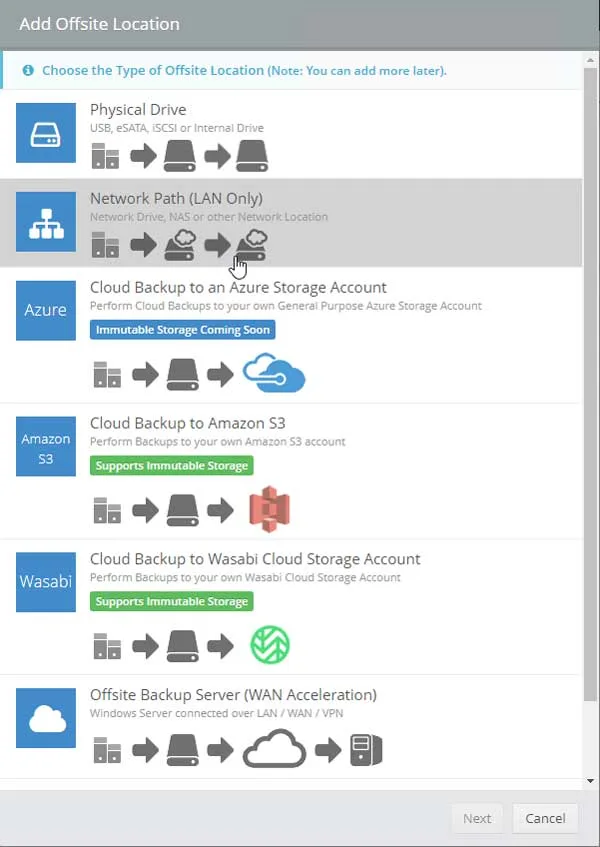
Immutable storage is a native cloud feature supported by many public vendors including, AWS, Wasabi, and Azure. Backup vendors rely on it by integrating their products with the public cloud.
VM Backup V9 now supports immutable cloud storage which assures that data cannot be erased, modified, or deleted by anyone for a set period of time.
Offline backups
Offline backups refer to storage devices, such as external hard disks and tape backups, that were used for performing backups and then disconnected. These types of backups are considered immutable, meaning they cannot be altered or modified once they are disconnected. Offline storage, utilizing air-gapped systems, provides enhanced security for user data.
Versioned backups
Versioned backups mean creating different versions of files at different points in time. Each version is saved at that point in time, and it can’t be modified, meaning you can “roll back” to that point in time.
What to Look for in a Backup Provider That Supports Immutability
Immutability is not a feature that is automatically available in every backup solution. It is highly recommended to explore whether the immutable backup is supported and what other features are available to protect systems against ransomware attack.
When searching for a backup solution, you should consider several key criteria, including immutability as the main one. If supported, immutability should support different options to make your data protected against malware and ransomware, such as WORM (Write-Once-Read-Many) and version control. VM Backup supports both features in the latest release.
Other criteria are compliance, encryption, security, scalability, performance, integration, SLA, and customer satisfaction.
Also, you want to use a backup solution that meets regulatory data compliance and possesses relevant certification for data protection and cyber insurance.
Your data should be also encrypted with an advanced algorithm during network transfer and while at rest. From a security standpoint, you should be also able to create access control and IDS.
Your backup product should be able to scale without affecting the performance of your backup software, backup storage, network, and data protection.
If customer reviews speak positively for the backup software, that is probably one you should evaluate in your organization.
Hornetsecurity VM Backup V9: Unbreakable Immutable Backups
We at Hornetsecurity recently released a new version of VM Backup V9. If you are running your business workloads in your data center on VMware, Microsoft Hyper-V, or physical Windows Servers, not only that you can easily back up your VMs to an on-premise cloud location, but you can also perform an immutable backup.
VM Backup V9 helps IT Administrators to back up the organization’s data from production servers, regardless if they are standard files, virtual machines, or something else.
This has a positive impact on RTO (Recovery Time Objectives) and RPO (Recovery Point Objective).
A new version of VM Backup brings immutable backup as an advanced feature to protect your data against ransomware. It helps you to ensure the integrity of backup data through tamper-proof measures, adding a layer of security above the existing offsite storage functionality and ensuring efficient storage management and data retention without any complications.
To properly protect your virtualization environment and all the data, use Hornetsecurity VM Backup to securely back up and replicate your virtual machine.
For complete guidance, get our comprehensive Backup Bible, which serves as your indispensable resource containing invaluable information on backup and disaster recovery.
To keep up to date with the latest virtualization best practices, become a member of the Hornetsecurity blog now (it’s free).
Wrap Up
Data is critical aspect of any business. Backup is the last line of defense against malware and ransomware attacks. Ransomware attacks have significantly evolved to the point where they can easily target backups. In the conventional approach, known as mutable backup data, ransomware can alter and change the critical backup data, and compromise data integrity. This poses a high-security risk.
On the other hand, immutable backup is an advanced backup feature that can help you to protect your backup data against ransomware. How so? Immutable backup data stored on immutable storage can’t be altered, changed, overwritten, or modified. It is done by using different ways such as WORM (Write-Once-Read-Many/Read Only Access) and backup versioning.
The latest VM Backup V9 release provides immutable backup for Amazon S3, Wasabi, and Azure storage will follow soon. By using VM backup, you increase data security by protecting data from deleting and altering.
Immutable backups is must-have solution in your disaster recovery. This article covered details that can help you to understand immutable backups.
We have a bonus for you! We recently recorded a podcast called What Is Immutability and Why Do Ransomware Gangs Hate It? Don’t forget to watch it!

For complete guidance, get our comprehensive Backup Bible, which serves as your indispensable resource containing invaluable information on backup and disaster recovery.
