

The Dangerous Role of Human Error in Cybersecurity
As modern technology becomes increasingly more central to our personal and working life, the darker side of human error in cybersecurity is also becoming more noticeable.
Twenty years ago, some businesses could function without their IT technology for a day or two; today, a one-hour outage can be devastating for most organizations. And while SaaS apps and technology platforms overall are more reliable than they were 20 years ago, cyber security threats are a clear and present danger.
A good cybersecurity approach involves three pillars:
- People
- Process
- Technology
Primarily, in this article, we’ll focus on the first one, People. When your Technology protection layer fails and that phishing email shows up in users’ mailboxes, or when the Process defence fails as the finance department staff forgets to pick up the phone and verify a bank account change for an invoice – the People layer is your last bastion.
In this article, we’ll look at the different aspects of human error risks in cybersecurity and how to improve the “human firewalls” in your business.
Unveiling Human Error in Cybersecurity
A stunning fact is that 33% of companies aren’t providing any cybersecurity awareness training to their users, according to our recent survey of 925 IT Professionals. That same study also showed that 74% of remote workers have access to critical data, and given the prevalence of work-from-home arrangements across the world in the wake of the pandemic, combined, these facts are quite scary. There’s a high cost of a data breach, and as an old saying goes, an ounce of prevention is worth a pound of cure.
Here are some statistics from our free Cyber Security Report to ponder while you look at how to prevent human error in cybersecurity that you should include in your employee handbook and IT security training.
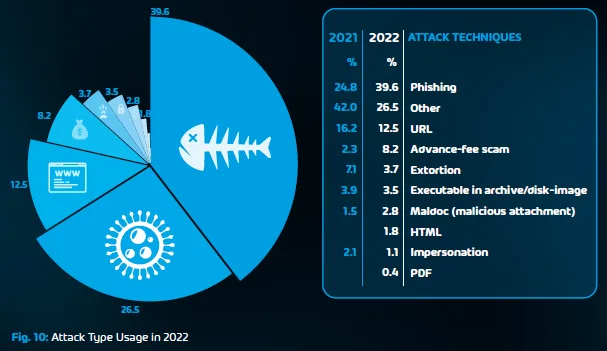
Common Human Errors in Cybersecurity
Not locking computers, smartphones and tablets
This is a basic cyber security hygiene step, and while most people and organizations enforce it for laptops, other devices are often forgotten. There should be no opportunity for a curious family member in a home office or a stranger in a café to casually access any device that stores business data.
Trusting public Wi-Fi
This is a common problem, especially for staff who travel regularly. I suspect it’s due to the invisible nature of the network. You’d notice if someone was hanging over your shoulder reading what’s on your screen, but of course, you can’t see what someone is looking at in an airport’s IT room. If you have staff travelling regularly, you must provide them with a strong and easy-to-use VPN solution if they have to use public Wi-Fi or an alternate method, such as tethering to a smartphone. This also goes for staff working in other public settings such as cafes.
Sharing work devices with family members
I suspect this has become increasingly common with the work-from-home movement, and this is one situation where sharing is definitely not caring; it’s scary.
Ignoring cyber security rules
This is very common, and while it’s easy for us security professionals to feel exasperated and not understand “why their priorities are so wrong”, this is a complete misunderstanding of how people work psychologically. Most people know that if they don’t hand in the report that’s due on Friday, they’re going to be in trouble with their boss. If they have to bypass some arcane rule about not emailing work documents using personal email or sharing spreadsheets with the rest of the team through personal cloud storage, that’s not going to get them into too much trouble. The challenge here is to change the company culture and help staff become capable defenders by making them understand the risks and the reason for the rules rather than as a hindrance imposed “from above”.
Weak passwords
This one is interesting because we’ve had an unhealthy focus on password quality for several decades now, thinking that adding special characters and exclamation marks at the end of our favourite password that we use on all sites makes it “better”. The truth is that most human-generated and remembered passwords aren’t a great defence, and in nearly all attacks, the quality of your password doesn’t matter. If an attacker tricks a user into entering their fantastic 24-character password on a fake login page or simply buys it online, that password’s complexity is immaterial. The best solution here is to use passwordless solutions, such as Biometrics, Passkeys, or FIDO 2 keys, and if that’s not an option yet, use MFA as an additional layer of identity verification.
Reusing passwords
As far as human error in cybersecurity, this is probably the riskiest one. Because the apps and services we use have multiplied exponentially in both our work and personal lives, many people use their favourite passwords for all sites. And when a poorly protected site is compromised, the bad guys take those same credentials and try them on Office 365, G-Suite etc., often with great success.
Sharing passwords with other staff members
This is still common and, of course, based on the two points above, a huge risk. Please, stop it.
Not changing passwords after a breach
If there’s a suspicion that there’s been a breach, every credential associated with it should be changed. And if it’s a domain-wide compromise, every user and application/workload password should be updated.
Post-It notices
Believe it or not, this still happens. Pick up a keyboard in an office, and you may find a conveniently “secret” password recorded. Again, here it’s so important to involve staff to help them understand why this is so dangerous.
Being helpful
This is probably one of the hardest lessons to get across; as humans, we’re innately helpful, and if someone’s stuck at the locked door (and looks like they belong), most people will help out and unlock the door or the locked computer. This is called social engineering and is a whole discipline within cyber security, whether done via email, over the phone, video conference or in person. Situational awareness and understanding of context will help here, as will regular physical penetration tests.
Falling for phishing emails
Most breaches today begin with a malicious email (e.g. phishing emails), and while a large proportion of internal communications in many businesses have switched from email to Teams/Slack or similar tools, email is still king when it comes to external communication.
And legitimate emails often contain links, making the rule “don’t click on links in emails” rather useless. Your defence should be multilayered; use a strong email hygiene solution to ensure that nearly all nefarious emails are kept out of users’ inboxes in the first place, but because no solution will catch 100%, when something slips through, train your users to spot fakes using Security Awareness Training.
Hornetsecurity’s Security Awareness Training has many great features, including quite funny and short videos, while its most important aspect is that it’s mostly set and forgotten. Staff who click on links will get targeted training, but others who don’t fall for the simulations will not be bothered very often, and it’s all managed by the system, which IT administrators much appreciate.
For an overall look at cybersecurity risks gained from analyzing 25 billion emails, see our free Cyber Security Report 2023.
To properly protect your employees against cyber threats, use Hornetsecurity Security Awareness Service as we work hard perpetually to give our customers confidence in their Spam & Malware Protection, Advanced Threat Protection, Email Encryption, and Email Archiving strategies.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
The risk to businesses today from organized crime and other bad actors cannot be understated. No business is too small or unimportant not to be a target. If you have money or essential information, there are bad guys out there who want it. And while Technology and Process defences are important, when they fail, your People are your last bastion against a breach.
You must continually train and strengthen your human firewalls at all levels of the business to manage human errors in cybersecurity and make your organization more cyber resilient.
FAQ
The most significant proportion of “successful” cyber security breaches start with a human error – clicking on a phishing link, not checking a change in bank account number (Business Email Compromise), entering credentials on a fake login page, storing documents outside company-approved systems etc. These failures put the organization at increased risk of compromise.
There are many types of human errors related to technology and IT systems, most related to our willingness to help others (thus the success of social engineering threats), missing cues such as misspelt domain or email names, bypassing company security rules “to get the job done” and many others.
In the largest sense, every successful penetration into an organization is due to human error. If your firewall has a zero-day vulnerability and bad actors exploit it, that’s due to a failure by the human who wrote the software. And if your CFO sends an email with a picture of his corporate credit card (because he knows typing out the number will be caught by your DLP solution) and this compromises the organization, this is a human error. Only by changing company culture, training your users regularly, and making cyber resiliency a core part of “how you do business” can you minimize human error in cyber security.
Password reuse is one; having a single “favourite” password used across sites and apps for convenience increases the risk immensely when any of those sites are compromised. Second, is clicking on phishing links or attachments in emails, the most common initial vector for ransomware attacks and other breaches.

