

Security Concerns of Hidden Permissions in SharePoint
SharePoint is a stalwart of collaboration and file sharing in Microsoft 365 which started its life as SharePoint server back in 2001. Most organizations use SharePoint online as hosted by Microsoft and it’s become a “plumbing” technology – something that’s fundamental, sits in the background and most people don’t take any notice of it, until it stops working properly.
This is even more evident in how SharePoint is used in Microsoft 365, you probably have SharePoint sites for various teams, departments, or countries, but SharePoint sites are also used as the backend file storage for everyone’s OneDrive for Business file storage. And when you share files and folders in Teams – guess what, that storage is also backed by SharePoint. So, not only do you need to govern the data stored in SharePoint sites, but also in these other locations, and as we’ll show you – governing data access in SharePoint is hard to do.
The heritage has a downside, starting life as on-premises piece of software and now running as a hosted service brings with it some serious security baggage. In this article we’ll show you the lack of permission visibility that can lead to security risks, and how hidden groups and hidden users make this situation even worse. Furthermore, custom permission levels can have disastrous consequences when it comes to assigning rights, and the manual management of user access is a recipe for security mistakes. Finally – custom document libraries can be an attackers’ hidden haven.
In other words – your SharePoint environment might already be infiltrated by an attacker, and you wouldn’t know it. At the very least, your permissions are likely not aligned with “least privilege”, one of the tenets of Zero Trust.
Most CISOs and security professionals are focused on the “loud” threats such as ransomware, but it’s important to be aware that there are many other avenues attackers take, and an attacker who’s been able to compromise a single user account might quietly watch the vendor invoice document folder in SharePoint for example. Gathering these documents, they may be able to change payment details in a classic Business Email Compromise attack (in this case without the email vector).
The Visibility Gap
We’ll focus most of this article on the Documents folder in your SharePoint sites – this is what most sites are used for – file sharing.
A fundamental difference, compared to traditional file shares, is that there’s no folder tree hierarchy that you can see. You can create subfolders in subfolders and so forth, and put files into any of the folders, but there’s no easy way to visualize the hierarchy, and you must click into each folder to see what’s stored in there.
To actually see which user accounts, groups or external guest users have been granted permissions to each folder (and each file, as they can have different permissions) means you must click on the object – then go to Manage Access to see who has access.
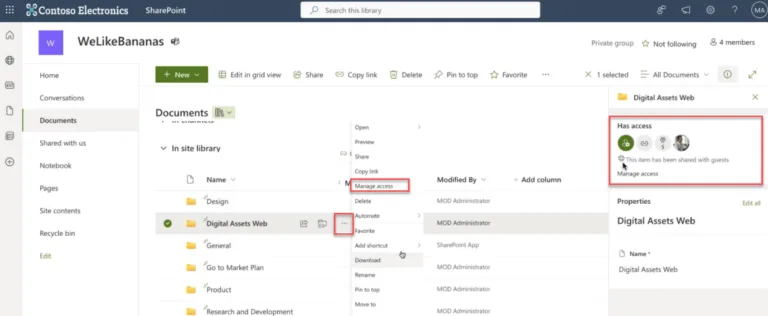
The second challenge is that while you can see the names of the groups that have been granted permissions on a particular folder, you can’t see the user accounts that are members of those groups in the Manage Access dialog. Clicking on a group name doesn’t bring up the members, in fact it does nothing.
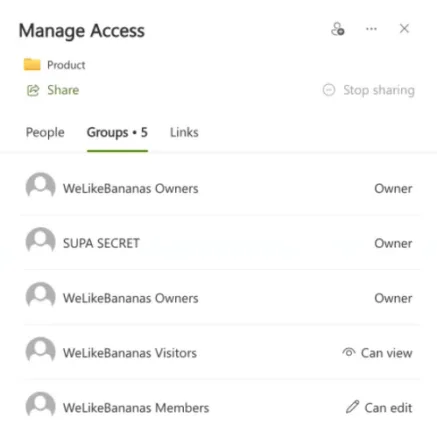
To determine the user accounts in a group requires a visit to either the Microsoft 365 admin center (https://admin.microsoft.com) or the Entra ID portal (https://entra.microsoft.com). Administrators will have access to these portals but if you’re a department manager, who is the owner of a SharePoint Team site, trying to ascertain who’s got access to what document folders in a SharePoint team site means you can’t complete this task without contacting the IT department.
Even more troubling (thanks to the SharePoint server heritage mentioned above) is that there is a group type in SharePoint itself, that is not visible in the Microsoft 365 admin center or the Entra ID portal, only in the SharePoint admin center (again, which ordinary users don’t have access to). If there are nested groups inside one of these groups you might have to track down those groups in one of the three mentioned admin centers. Finally, if you grant permissions to a group which has one user and one group inside of it, it’ll tell you that you’re granting permissions to two people, when in fact there could be hundreds of user accounts inside the nested group.
Hornetsecurity’s 365 Permission Manager thoroughly fixes these visibility problems, showing you all the users that have permissions to a site, folder, or file, as well as if those permissions are inherited from the site, or are unique to that object. It also surfaces external sharing, either where it has been shared with specific people outside your organization, or where an anonymous link has been created.
Another innovative feature is the ability to see SharePoint / OneDrive for Business sites “through the eyes” of a selected user – exactly which sites / folders / documents does this user account have access to? This is useful during a forensic investigation (what data did the attacker who compromised this account have access to?), insider risk cases (what’s the blast radius of this malicious employee?), and data governance (do our permissions match our data access policies?).
Permission Levels
SharePoint Online provides four levels of access permissions to folders and files: Owner, Can edit, Can View and Can’t Download (=view but not save files locally). However, SharePoint Server had and still has a more comprehensive model – with multiple built-in permissions levels, as well as the ability to create custom permission levels.
The first issue that this leads to is that when you check permissions granted on an object, the UI will “round off” to the closest permission level granted, Design for example is a legacy level that grants more permissions than Edit, but this is shown as Edit in the UI.
Much scarier, however, is the ability to create custom permission levels with the same name as a built in one – such as “read”. This level could be granted every available permission (definitely not just read). Not only does that lead to the situation where a casual check of permissions granted would lead you to assume that a group or user only has read access but if you do decide to investigate why there are two permission levels called read / Read, it turns out that the UI will show you the built-in permission level, not your custom one. If a custom permissions level has the same name as a built in one, the URL in SharePoint isn’t case sensitive, and thus will show you the built in one.
365 Permission Manager will surface these custom permission levels, bringing visibility and governance to your entire SharePoint Online estate, it also allows you to use built-in or create customized policies that you can apply across different types of sites. This then shows you where sites are deviating from your policy intent and allows you to remediate permissions with a single click.
Site vs Document Library Permissions
Another risk is that you can set custom permissions on the Document library, that are different to the overall Site permissions.
Once granted, when an audit is done, these permissions are visible, but can’t be changed in the UI.
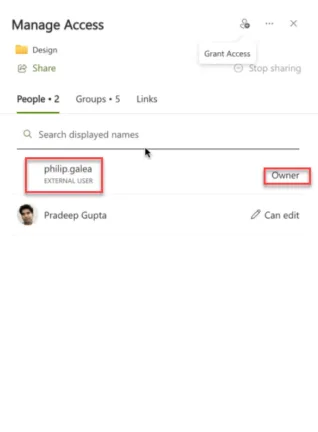
Again, 365 Permission Manager will find these discrepancies, surface them as deviations from your policies, and prioritize their remediation in the handy To Do list.
Hidden Document Libraries
Normally a SharePoint site has a single Documents folder, but you can create other ones. Furthermore, you can hide it from the site’s navigation (so no one else knows it is there), and you can remove everyone else’s permissions from it, only granting yourself access. This will in effect create an exfiltration channel, where the attacker can copy sensitive documents from the site into their custom Document library, perhaps even returning on a regular basis to capture the latest versions of files, and then downloading them to their machine.
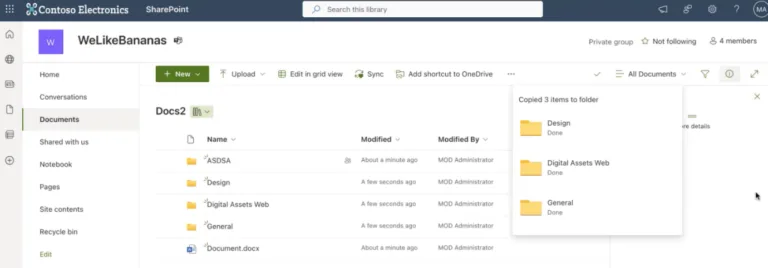
This is a huge risk in a compromised SharePoint site and of course 365 Permission Manager will surface custom, hidden, Document libraries, and their permissions for you to remediate.
There’s another very useful feature – the ability to revoke all access to SharePoint / OneDrive for Business data for an account. If you know that an account is compromised, manually revoking access across every location is extremely time consuming – 365 Permission Manager gives you a single button to do it.
To effortlessly manage Microsoft 365 permissions, enforce compliance policies, and monitor violations with ease, utilize Hornetsecurity’s 365 Permission Manager. Protect your Microsoft 365 environment and make admin tasks a breeze.
Conclusion
As with many Microsoft technologies, the focus on backwards compatibility has proven to be a strength when it comes to enterprises for decades. Imagine an organization with a large investment in SharePoint Server on-premises, with thousands of busy sites and Terabytes of data, migrating this to SharePoint online – this compatibility is a requirement.
However, it also has scary security implications – the reality today is that many businesses might be compromised, with bad actors exfiltrating data at will from your most precious intellectual property, with very little chance of discovery.
This is why any CISO who wants to apply comprehensive data governance to their SharePoint estate needs 365 Permission Manager.
I’ve been hacked! WHAT SHOULD I DO?
With Hornetsecurity’s 365 Permission Manager you can regain control of your SharePoint environment and protect your business immediately.
- Remove User Access Feature: With a single click, the Offboarding feature in 365 Permission Manager allows you to revoke access and stop a hacker immediately. This immediate action can prevent further unauthorized access and potential data breaches.
- The View as feature: Gain insight into what files a compromised user could access with the View as feature in 365 Permission Manager. This feature allows you to see SharePoint through a user’s eyes, helping you identify potential areas of unauthorized access and take corrective action.
- Generate Reports for Forensics: Understanding the extent of a security breach is crucial for effective remediation and compliance. With 365 Permission Manager, you can generate detailed reports for forensics, showing exactly what files a user had access to and the full permissions inside all SharePoint sites and OneDrive for Business locations. This information is invaluable for identifying the scope of the breach, assessing the damage, and implementing necessary security measures to prevent future incidents.
FAQ
Hidden permissions in SharePoint pose significant security risks because they can allow unauthorized access without the knowledge of administrators or users. Key issues include:
Lack of Visibility: SharePoint’s permission settings can be complex and opaque, making it difficult to see who has access to what. This includes hidden groups and users whose permissions are not easily visible.
Custom Permission Levels: Custom permissions can be misleading. For example, a permission level named “read” might actually have full access rights, leading to potential security breaches if not properly managed.
Hidden Document Libraries: Attackers can create hidden document libraries with exclusive access, enabling them to exfiltrate data without detection. These hidden libraries are not easily visible in the SharePoint navigation, making them a significant risk.
365 Permission Manager provides several features to enhance security and governance in SharePoint:
Visibility Enhancement: It displays all users, groups, and permissions for sites, folders, and files, including inherited and unique permissions. This comprehensive visibility helps in identifying and addressing hidden access issues.
Permission Management: It surfaces custom permission levels and discrepancies, allowing administrators to standardize permissions according to policy. This reduces the risk of misconfigured access rights.
Access Control: The tool offers the ability to revoke all access for a compromised account with a single click, ensuring quick response to security incidents and preventing further unauthorized access.
Hornetsecurity’s 365 Permission Manager enhances security by providing comprehensive visibility into all user permissions, managing and standardizing custom permission levels, and allowing for immediate revocation of access for compromised accounts. This ensures robust data governance and quick response to security incidents.

