

The Significance of Encrypted File Transfer for Data Security
In this article, we’re going to look at encrypted file transfers and why this is an important but often overlooked component of cyber security.
There are a few basic things in computer security that will never change, such as the need to protect your data against theft, failing hardware, human errors, and natural disasters.
There are three states your data can be in, stored on disks, cloud storage (or tape), referred to as “data at rest”, on the network being transferred from one system to another, “data in flight” and finally “data in use” when it’s being processed by the system. There are ways to protect your data in all three states, in this article we’ll look at encrypted file transfer and how it fits in with the data-in-flight paradigm.
To set the context, let’s cover data at rest first – in modern datacenters on-premises it’s likely that some physical storage is encrypted, in public clouds all physical storage is encrypted, and most laptops also come with full disk encryption enabled. BitLocker has been a native part of Windows for many years and is easy to manage.
The main risk that full disk encryption mitigates is physical theft of the disk or the device leading to loss of data. In other words, if you steal my laptop or pull a set of disks out of my servers, you can wipe them and sell them, but you can’t get to my data because you don’t have access to the decryption key.
Data in use is a much newer scenario, covered by Confidential Computing. The risk you’re mitigating here is theft or access to data while it’s being processed, for example by a rogue admin at a public cloud provider or a malicious database administrator in your company reading sensitive data. The building block of confidential computing are special versions of Intel or AMD processors that provide a Trusted Execution Environment (TEE) and encryption of parts of the memory.
If the code you want to run confidentially attests as your code that hasn’t been altered, keys are released and data processing takes place in the enclave, prohibiting access even from an administrator on the system. There are some predictions that just like encryption of data in transit is now taken as a given, in 10 years, Confidential Computing will be the norm for all systems.
Today the easiest way to access confidential computing is in public clouds, particularly Microsoft’s Azure, which is a leader in this space.
Encrypted File Transfer – Data in Flight
Whenever you want to transfer sensitive data files over an insecure or untrusted network you should use encrypted file transfer. Just like the example of data at rest above, if someone intercepts the file(s) during transit and they’re in clear text, they can simply read them.
But if they’re encrypted, all they’ll see is cipher text and your data stays private.
In some scenarios this is already the default, if you’re using a browser and connecting to almost any site on the internet, especially your bank or a site where you purchase goods, the connection will be encrypted.
This is the difference between the HTTP and the HTTPS protocol, where the S in the latter indicates that the site has a digital certificate, supporting a public/private key pair used to encrypt the traffic between your browser and the site. The same applies to your personal cloud storage, services like OneDrive for Business, Dropbox, Google Drive, etc. also use HTTPS to encrypt the upload and download of files to your device.
There are many other situations, however, where file transfers are a manual operation, and you need control over the encryption of the files.
There are a number of ways you can ensure secure file transfer, at the lowest level this involves selecting a protocol such as FTPS (Secure File Transfer Protocol) or SFTP encryption (SSH File Transfer Protocol). The former is the standard, unencrypted FTP protocol combined with TLS, the same encryption that’s used in HTTPS. These protocols have been around for many years and provide end-to-end encryption.
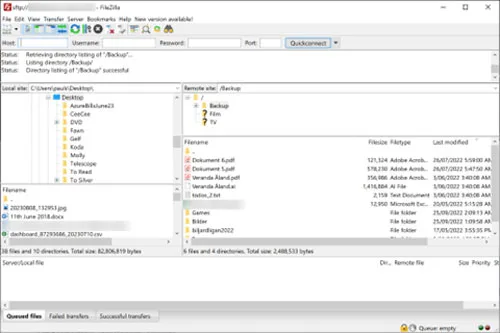
Behind the scenes, each file is encrypted before the file transfer and then decrypted on the receiving end. This also means, just as with any encryption system, that your data protection security now relies on good key management. Protecting the keys, and in the case of certificates, the private key is now paramount. That’s the basics of data protection for file sharing, perhaps for a once-off move of some data files, but beyond that, you’ll need to look at your business needs and what file transfer solution will work best for your situation. Here are some questions to investigate as you decide what IT security measures to take for your file transfer solutions.
- What’s the nature of the data in the files? Is it Personally Identifiable Information (PII), financial information, confidential data, or other sensitive information?
- Are the files being shared covered by a regulation that your organization must adhere to? If so, make sure that your chosen file transfer solution complies with the relevant regulation.
- How many files and are they large files?
- How frequent is the file sharing? Is it an hourly, daily, weekly or end-of-month process? Is it a regular pattern or does it change, depending on external circumstances?
- Are you transferring files from one location to another, such as every branch office uploading daily data feeds to a centralized location? Or are you sharing files, either privately with data consumers that you know and provide access to, or are you sharing files publicly?
- How automated do you need the process to be? Is it an irregular occurrence where you need manual control, or do you need automated managed file transfer?
Once you have established the business requirements for data sharing, you can start investigating secure file transfer solutions.
What Not to Do
At this point, many enterprises and small organizations look for a managed file transfer solution.
Put an appliance in each end, connect them and now you have a secure file transfer solution with very little management overhead. Except, based on industry experience over the last few years, these types of appliances, often brought to market many years ago, have an absolutely terrible track record of security.
In February 2023 a zero-day led to extensive data breaches. Before that Accelion’s FTA was compromised back in early 2021, and later in 2021, FileZen from Soliton suffered a similar fate.

And in current news, the MOVEit file transfer service vulnerability has resulted in the Cl0p criminal group stealing data from many high-profile organizations, over 600 at the time of writing.
This group “specializes” in secure file transfer service attacks and extorts their victims by threatening to release the data publicly unless paid. This is a variant of ransomware attacks, which you can read more about in our Ransomware attacks survey.
So, don’t trust your data sharing to one of these file transfer solutions, the risk is just too high.
There are many risks to manage in cyber security, our annual Cyber Security Report 2023 gives some great insights into the threat landscape and ways you can protect your business.
What to Do
If you want an enterprise-grade secure file transfer solution, open source or proprietary “do it yourself” options aren’t going to cut it. And as seen above, using an appliance to transfer files “securely” is going to be very, very risky.
A better approach is enlisting a SaaS platform for your secure file transfer needs. These are generally more modern (SaaS solutions are generally less than 5 years old, whereas many file transfer appliances gathering dust in your datacenter stopped receiving patches 5 years ago), are monitored by the vendor (so they’re more likely to catch an attack than you are on an appliance where you can’t install a monitoring agent) and will be patched much quicker by the vendor if a vulnerability is found.
Enhance employee awareness and safeguard critical data by leveraging Hornetsecurity’s Security Awareness Service for comprehensive cyber threat education and protection.
We work hard perpetually to give our customers confidence in their Spam & Malware Protection, Email Encryption, and Email Archiving strategies.
To keep up to date with the latest articles and practices, pay a visit of our Hornetsecurity blog now.
Conclusion
The importance of encrypted file transfers cannot be understated, both to protect against data breaches and prevent unauthorized access to the files in transit. As the last few years have shown, relying on a proprietary appliance is a recipe for disaster and selecting a frequently updated SaaS secure file transfer solution is preferable.
FAQ
In the most basic form, it’s encrypting files for data security, then transferring those files over an untrusted network and then decrypting it on the receiving end. While you can use strong protocols such as secure file transfer protocol (FTPS) or SSH File Transfer Protocol (SFTP) for ad-hoc transfers, you’ll need a SaaS-based secure file transfer solution in an enterprise.
Depending on the system you’re using you’ll define the files to transfer and then they’re sent to the receiving system(s).
Both secure file transfer protocol (FTPS) or SSH File Transfer Protocol (SFTP) provide good security but aren’t particularly user-friendly nor easy to configure for regular, scheduled secure file transfers.

