

Advanced Threat Protection for Evolving Email Threats
Email Security – The State of Play
On Monday morning, James in marketing at YOLO Pty Ltd sees an enticing email on his phone from a vendor that he does a lot of business with. It talks about the upcoming soccer finals being held in his city and offers two tickets for free as a thank you for being a great customer, along with a QR code link to a website to get the tickets.
James – a football fanatic – immediately scans the QR code, enters his work details and agrees to the application permissions screen that pops up.
Within a few minutes, attackers have used the OAuth permissions granted to them to gain full access to James’s Exchange Online inbox, a few hours later they’ve moved laterally from his account to others and within 24 hours they’ve obtained full access to YOLO’s entire network, with the ransomware attack following immediately after they’ve exfiltrated private corporate data for extortion and corrupted any backups they could access.
This is a fictional scenario but everything in it matches our Security Lab’s expert investigations, including the time spans.
If James had been protected by Hornetsecurity’s Advanced Threat Protection the malicious email would have been scanned, the QR code identified, the malicious form found, and the email would never had been delivered to James and his colleagues.
Email is by far the most common way attackers gain a foothold in your organization. And this is an ever-evolving arms race, the criminals (who are well funded and well organized) are always changing and improving their attacks, so yesterday’s defenses and yesterday’s technology are going to be bypassed.
To be protected and stay secure against new threats, you need Hornetsecurity next-gen technology in your corner, with new protections against novel attacks, such as malicious QR codes.
The news is often filled with headlines about Advanced Persistent Threats (APTs) and it seems that every organization that gets breached leads their PR response with “it was a very advanced attack”, the subtext being that it was really hard to defend against.
However, Hornetsecurity has produced many reports, along with others in the industry, showing that most successful attacks aren’t the result of some amazing, previously unknown attack vector – they’re the consequence of basic security hygiene failures, such as allowing phishing and spear phishing emails to end up in your users’ inboxes.
And not having a thorough and ongoing security awareness training program for all users, to strengthen the “human firewalls” throughout your business.
A variant is Business Email Compromise (BEC) where an attacker has compromised one user’s email account and monitors normal communications over a period of time, then inserts a request to change a bank account for a regular payment (to the attackers account) for example.
These examples are just scratching the surface. The real challenge is new and evolving threats. Attackers are always changing and improving their lures and attacks, and with their ill-gotten gains they can afford new technologies.
For example, just like marketing departments and app makers, they’ll A/B test different emails to see which wording and approach gets the most clicks. This approach is also being augmented by AI – where we use ChatGPT to improve the language in a presentation, they might use similar technologies to generate “psychologically appealing” email lures.
All of this is to say that you need a strong team, that’s ahead of the curve, to make sure your users don’t have to deal with these threats, and that’s where Hornetsecurity comes in.
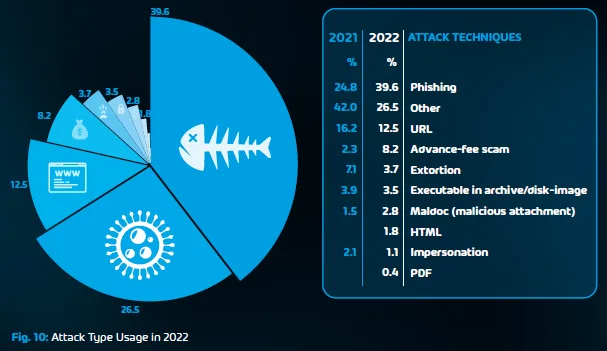
An analysis conducted by Hornetsecurity’s dedicated Security Lab of 25 billion business emails found that 40.5% were unwanted, and out of that portion, 94.5% were spam, and 5% malicious.
Social engineering is a large part of the threat landscape and email threats from 10 years ago that were filled with spelling and grammar mistakes and clearly fake, have been replaced with psychologically appealing, cunning text playing on human nature.
Brand impersonation is another part of the risk, with so many of the cues to assess trust we rely on when we first meet someone in the real world absent in emails, a message from a trusted brand is more likely to result in that unfortunate click.
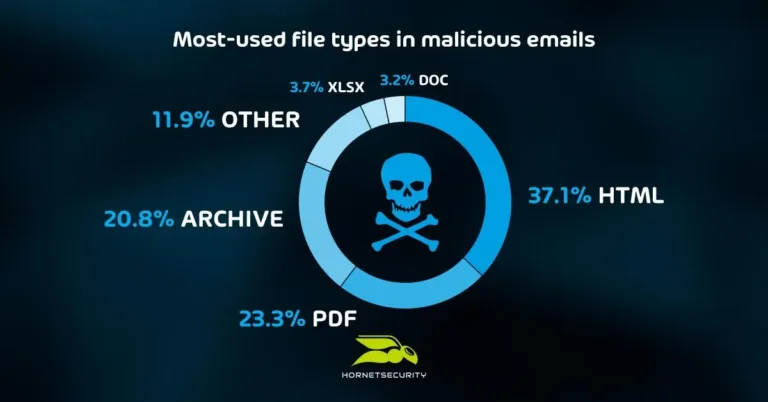
As we saw with James, that single click can lead to your business data being encrypted, your backups corrupted, and sensitive data you hold exfiltrated and threatened to be disclosed publicly.
There are many, many more varieties of email attacks and risks, our Cyber Security Report goes into much more depth.
Basic and Advanced Threat Protection
To mitigate the risks outlined above you need both basic and advanced email hygiene services. The basic approach, which every vendor provides, takes care of (most of) the spam so that your users don’t have to wade through enormous amounts of junk just to find their business emails.
It’ll also catch (some of) the malicious emails and attachments but given how central email communication is to business today – catching most isn’t good enough. You need the best protection possible, and that is Hornetsecurity’s Advanced Threat Protection – a next generation security service for Microsoft 365 that provides precise and comprehensive protection against all forms of malicious emails.
This cloud service provides excellent spam filtering and email security, for both incoming and outgoing emails, you don’t want to be the unwitting spreader of malicious emails because one of your users was compromised. Both malware and malicious URLs are spotted and blocked before they can do harm.
Advanced Threat Protection goes beyond these basic services to specifically catch ransomware emails and lures, spear phishing campaigns and CEO fraud. Behind the scenes we use AI-based Targeted Fraud Forensics to spot risks that others miss.
Advanced Threat Protection also catches forged email headers, a popular attack method to make an email appear to come from someone trustworthy, when in fact it doesn’t.
As for malicious email attachments, unless we’ve seen the file before and we know it’s benign (or malicious, in which case the email will be blocked outright), we use our proprietary Sandbox Engine to go through the steps a user would upon receiving the email, and then monitor very carefully what happens when the attachment is opened or executed, using over 500 behavioral analysis sensors.
These sensors detect attempts by the executable to detect if it’s running in a sandbox (a dead giveaway), and carefully monitors filesystem, processes, memory, and registry changes to catch evidence of a malicious payload. Filetypes such as executables, PDF, Office files and archive (ZIP etc.) are all identified and the engine looks at macros, embedded URLs, metadata, and JavaScript code.
If an email or attachment is identified as malicious after delivery, it’ll be automatically marked for deletion in the inboxes where it has already been delivered.
Like any good security solution, Advanced Threat Protection mostly does its work silently and provides your end users with clean inboxes but in situations where your attention is required such as when your organization is under targeted attack – Real Time alerts are issued to your administrators.
Hornetsecurity’s complete portfolio also includes email encryption to ensure that only the sender and recipients can read the contents of sensitive emails, handling encryption keys and certificate management behind the scenes for ease of use.
If you have regulatory requirements to keep all emails for extended periods of time (6 months to 10 years), legally compliant archiving is built in. It also allows you to import data from other email systems.
365 Total Protection also provides an easy-to-use signature and disclaimer feature that lets you create individual signatures based on Active Directory user information automatically.
QR codes – The criminal’s new best friend
A new, bleeding edge attack vector is malicious Quick Response (QR) codes and we’ve added scanning of these to keep your users safe. Remember James and his disastrous Monday?
Up until now, and in nearly all other email security solutions on the market, if the attackers included a QR code instead or a plain text link, it would have just been seen as a benign picture and not set off any alarms.
With Advanced Threat Protection, and the new QR Code Analyzer this gap has now been firmly closed.
QR codes are a very popular way for businesses worldwide to advertise and engage customers and potential buyers, “just scan this code and receive a $ 5 voucher on your first purchase”. It’s amazing to think they were invented all the way back in 1994 in Japan.
They are everywhere, this one for example takes you to Hornetsecurity’s homepage.

How popular are QR codes in marketing today? Bitly published a report filled with interesting statistics, but in summary, they saw 152% growth of their use in 2022, with Finance, Healthcare and Government Services seeing huge growth in 2022.
People are scanning QR codes more and they link to more diverse content, not just a single website. There are now QR codes that lead to coupons, events, social media content and marketing video content.
This means end users are becoming more and more accustomed to scanning QR codes and expecting “something good” at the end of it. This is a perfect opportunity for criminals to hide their malicious links in innocuous looking picture files and bypass protections – except if you have Advanced Threat Protection guarding you.
Our scanner looks for QR codes in GIF, JPEG, PNG, and BMP image files in emails and can extract both URLs and text from them, analyze them and only allows the email to be delivered if it’s benign.
There’s no configuration of the QR code scanner in Advanced Protection’s Control Panel, it’s simply turned on and protecting all your users, just like any good security service.
Secure Links
Speaking of scanning links, Advanced Threat Protection has had URL Rewriting and scanning for a long time, the new version is called Secure Links and uses a new engine.
Using Hornetsecurity’s secure web gateway it doesn’t just scan the links in emails, it also “visits” the website and recursively scans links to establish if the site presents a risk to your users, and of course blocking access if it does. Most importantly it’ll do the check at the time the user clicks the link, not just when the email was delivered.
Sometimes attackers will compromise a site but not change anything until after their emails have been delivered, making time of click protection paramount.
Security Awareness Service
No security service is perfect, there’s always a chance that something will slip through even the strongest net, so you need to add another layer of defense – your end users.
Hornetsecurity’s Security Awareness Service provides simulated phishing emails to train users to be wary, and not fall for lures, plus follow up short e-learning content to help cement the knowledge.
Unlike other solutions administration of the system is very lightweight and it’s mostly a “set and forget” solution, that uses an Employee Security Index to identify users most likely to click on links without hesitation and increase their training.
Mailbox Migration Tool
There’s no doubt that hosting your email inboxes in Exchange Online is more secure than hosting them on-premises, especially given several high-profile vulnerabilities that were exploited in 2021, 2022 and now in 2023. To assist with your migration, Hornetsecurity now offers an easy-to-use Mailbox Migration Tool.
Once your users are onboarded in Control Panel, a simple Azure AD Application is configured with OAuth permissions and you can start migrating mailboxes to the cloud, which could take some time, depending on the number of mailboxes and their size. Once they’re migrated you can enable 365 Total Protection for them.
Harness Next-Generation Security
Specifically designed for Microsoft 365, Hornetsecurity’s 365 Total Protection offers comprehensive protection for a wide range of Microsoft cloud services.
It is easy to set up, seamlessly integrates with your existing Microsoft 365 environment and is extremely intuitive to use. 365 Total Protection simplifies and strengthens your IT security management from the very start.
