

Cyber Kill Chain vs. MITRE ATT&CK: An Insightful Comparison
There are two challenges we in cybersecurity face when it comes to communicating what we do the rest of the business (and the rest of the world). For many people, computers, networks, and Information Technology in general are opaque, and most businesspeople know how to use tech to get their job done, but not how it works “under the hood”. Hacking that technology to subvert it for malicious purposes is another level of mystery.
Hollywood doesn’t help much either, with most on-screen depiction of hacking in movies and TV shows being radically different from reality (with the exception perhaps of Mr Robot).
The first challenge is communicating the technology and basic understanding of how it works to then show how it can be misused. But the second challenge is then imparting how the criminals carry out their attacks. Most people think a hack is just a single “thing” that happened – “we got hacked” and then all the bad stuff happened, when it’s actually a set of steps.
In this article we’ll look at two different frameworks that are used to communicate hacking processes, both to the wider business and within the cyber security community – the Cyber Kill Chain, and the MITRE ATT&CK framework. We’ll look at the advantages and challenges of each of them, how they compare and how you can use them to fortify your organization’s cyber defenses.
Meet the Cyber Kill Chain
This is the older of the two approaches, having its roots in military kill chains such as the Four F’s from the US military during World War II: Find the Enemy, Fix the enemy, Fight the enemy and Finish the enemy. A more modern version is F2T2EA: Find, Fix, Track, Target, Engage and Assess; it’s called a chain because an interruption at any step can stop the whole process.
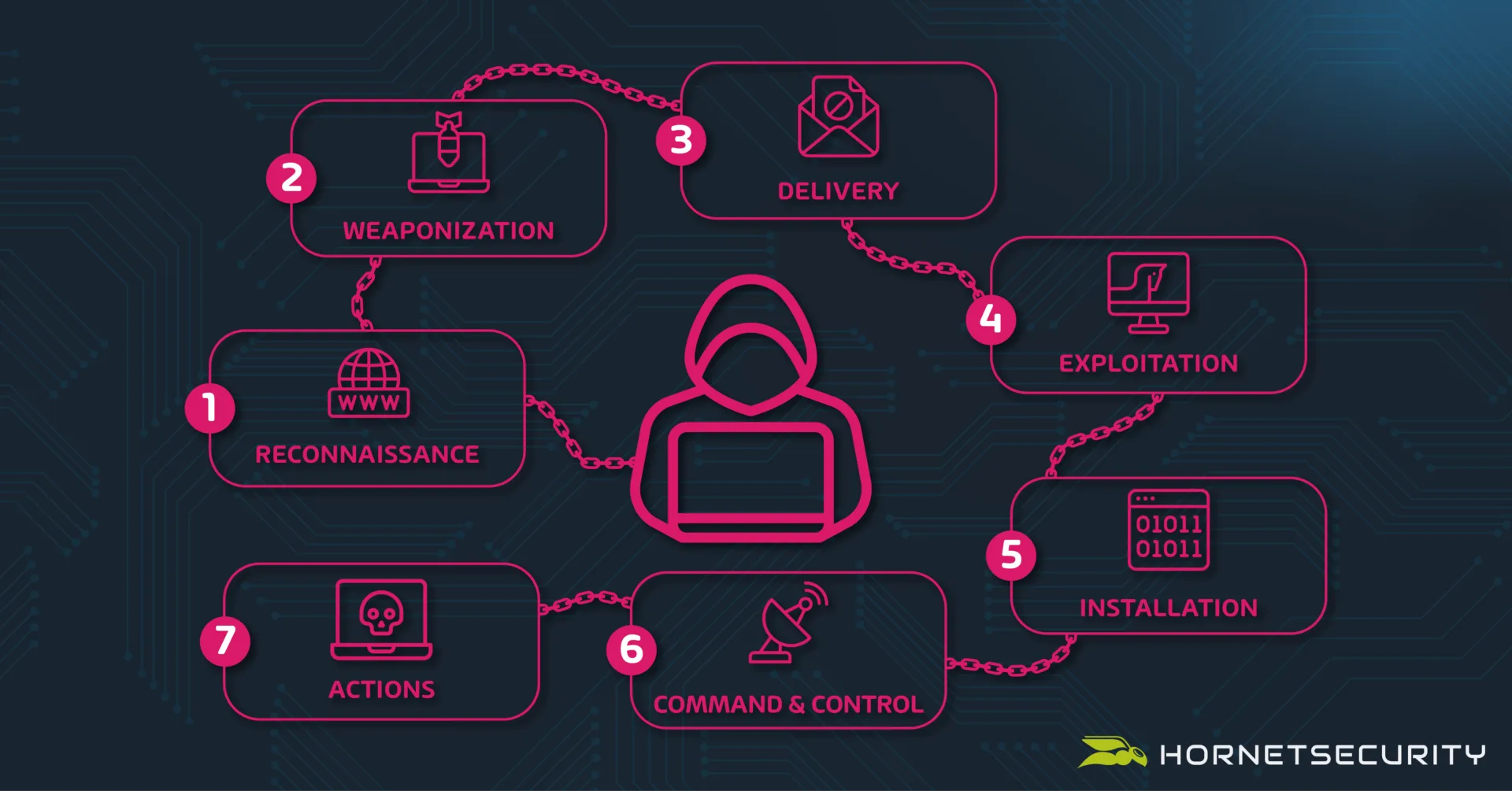
Cyber Kill Chain
Not surprisingly, it was Lockheed Martin, a large military manufacturer in the US that took this chain approach and transformed it into the Cyber Kill Chain, with seven steps (and a very different result at the end compared to the literal kill chains mentioned above).
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control (often shortened to C2)
- Actions on objectives
As a communication tool for showing business leaders that there are steps in an attack, and that you want budget to interrupt or make each layer more difficult for the criminals, this is a good approach.
Cyber security after all always comes down to business risk. When you put it those terms, the CEO, CFO, and the board are more likely to pay attention. If you start talking about technical details, you’ll soon lose them, but business risk is something they’re used to dealing with, and cyber-attacks is just one of the many risks businesses faces.
Be aware that attackers may not perform every step, depending on their goals, their target, and any changes along the way, and that “attackers” might refer to different sets of people, where the early steps might be performed by an Initial Access Broker (IAB), who then sells the access to another group to actually run the ransomware and negotiate the payment.
In step one the attackers will gather information about your company and any employees of interest. This could be cursory, if they’re simply after a company with enough turnover to pay the ransom they might look at your financials, and who to target with their spear phishing emails.
It could also be more in-depth, when the scattered spider group went after the helpdesk at the MGM casino, they knew a great deal about the staff they were impersonating to ensure that the helpdesk would help them reset their credentials.
Phase two is taking advantage of the reconnaissance, to start exploiting a found weakness or packaging a payload, whereas step three is delivering the malicious bundle to the victims, via email, web etc.
Once the initial foothold has been established (someone clicked the link in a malicious email for example), step four starts the exploit to run code on the victims system, which may then continue with step five, further installations on other systems. This is often called lateral movement, as the attackers continue exploiting systems in your networks, to gain full Domain access.
They’ll also establish persistence (so they can come back in if you’re trying to expel them from your environment) and Command and Control (C2) in step six for covert communication with their external control systems. The final step, seven, involves the attackers springing their trap and encrypting all your files, after having corrupted your backup systems or perhaps exfiltrating all your sensitive data (or both).
The ”other side” of the cyber kill chain are the defensive actions your organization should take to deal with each phase:
- Detect – having sensors throughout your environment that trip when an attacker is present.
- Deny – control access and prevent information leakage.
- Disrupt – malicious processes and outgoing traffic to the attacker’s infrastructure.
- Degrade – means counter attacking the attackers C2 systems.
- Deceive – is about interfering with the C2 infrastructure.
- Contain – using network segmentation so that a single breached system or identity doesn’t have full access to every other system on the network.
This approach does have its detractors but as a conversation to start looking at different phases of an attack, whether your organization has security controls in place to detect it, disrupt it and contain it, it’s a good start. It also leads neatly in the modern approach of Zero Trust:
- Assume breach – work on the assumption that attackers will gain access and work on detecting it, containing it, and disrupting it.
- Verify explicitly – authenticate and authorize both human and workload identities at each access point in the infrastructure.
- Use least-privilege access – only grant identities access to the systems, data, and applications they need to do their job.
The challenges with the cyber kill chain is that it doesn’t work well for insider risks, the first couple of steps happen outside of the defenders control (unless you stop all staff from having LinkedIn profiles and posting anything, anywhere online) and it’s also quite focused on malware, some attackers now use Living Off the Land methods, only using built in administrative utilities in the systems, thereby often avoiding detection.
The MITRE ATT&CK Framework
MITRE is a not-for-profit company that works for the common good in the areas of security writ large, but for this conversation we’ll focus on their enterprise matrix (there’s also one for Mobile and one for Industrial Control Systems, ICS). The weird acronym comes from Adversarial Tactics, Techniques and Common Knowledge and it was initially released in 2013.
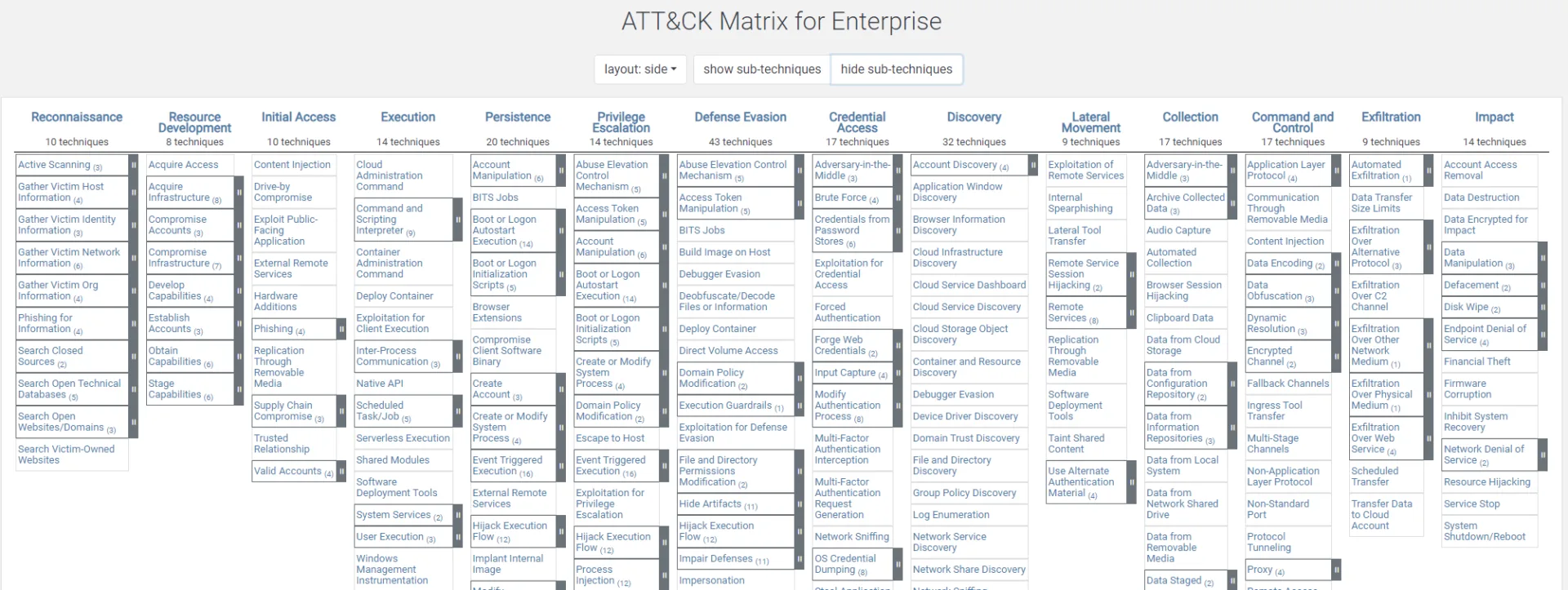
ATT&CK framework matrix
There are 14 tactics (the “why” of the attack):
- Reconnaissance
- Resource Development
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
And each of them has Techniques (and sub-techniques), the “how” of an adversary, so while you can see some overlap with the simpler cyber kill chain in the list above, this is much more comprehensive. I like to think of it as a common language we in the cyber security industry can use to communicate about different attack techniques. There’s also tracking of 143 threat groups and which Tactics, Techniques and Procedures (TTPs) they use.
As you can appreciate the matrix encapsulates all the different techniques, making this a tool to ensure that you’ve got coverage “across the board” in your cyber security strategy. Here’s an example from one client, using the Microsoft Sentinel SIEM, and the analytics rule detection coverage across the techniques.
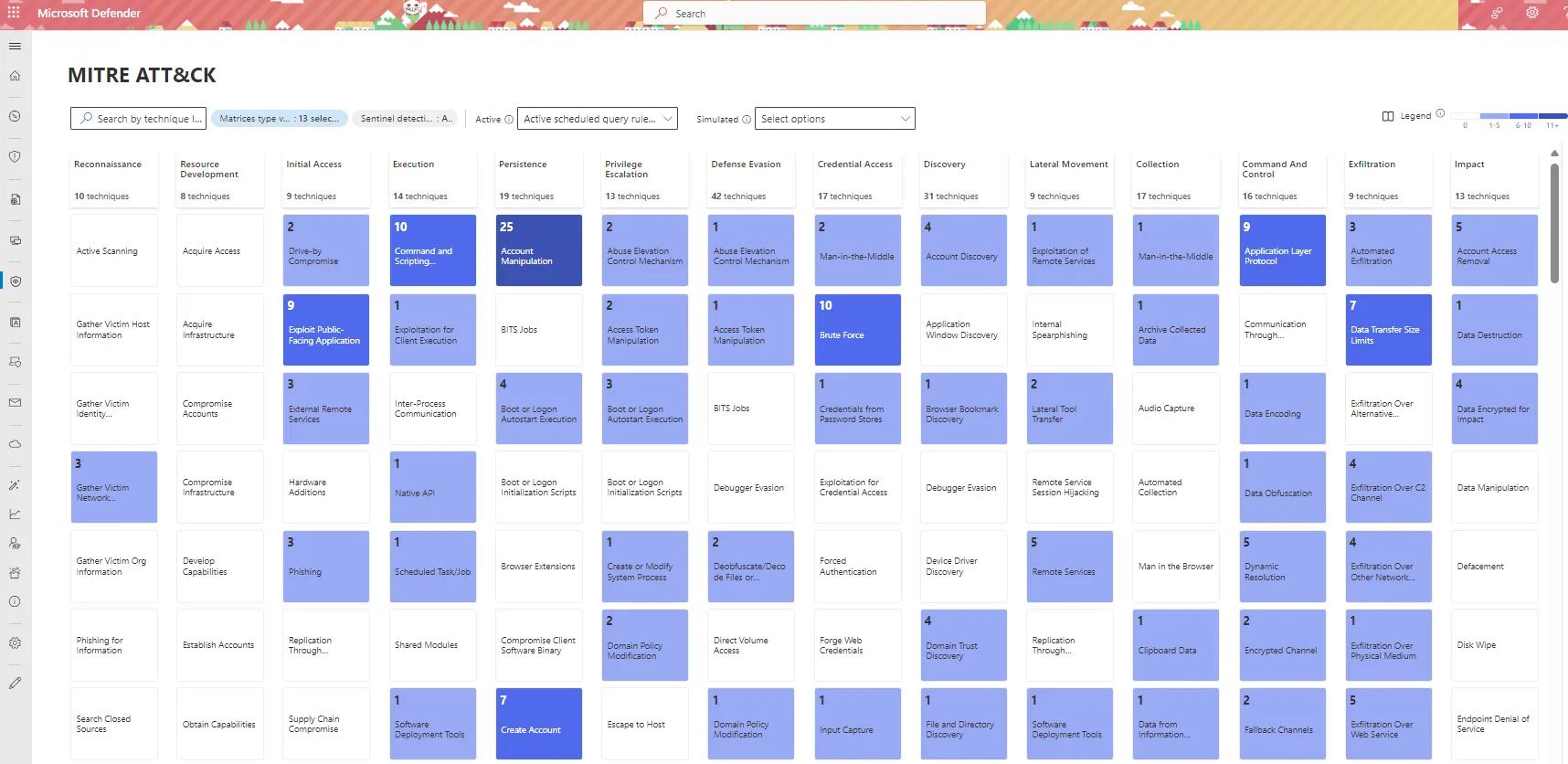
MITRE ATT&CK Technique Detection Coverage in a SIEM
Each Technique is described in detail, here’s T1563, Remote Service Session Hijacking, in the Lateral Movement Tactic, which has two sub-techniques (SSH Hijacking and RDP Hijacking) as an example. It has four mitigations that you can implement, and four detections that you can use to alert you if this is happening on your network. Most techniques also list Procedures which are the actual technical tasks applying that technique to a specific application or operating system.
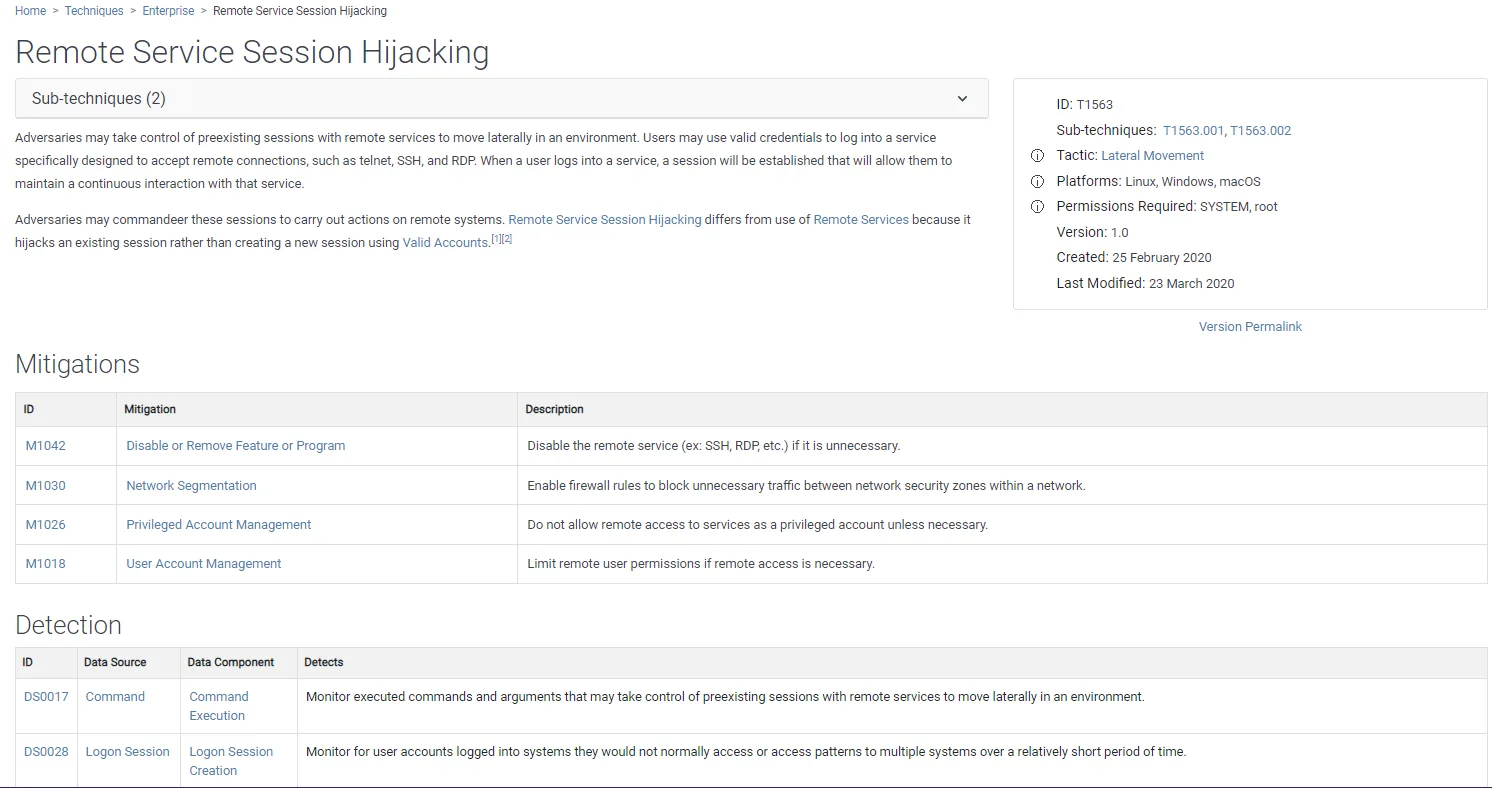
Technique T1563 Remote Service Session Hijacking
While the matrix is very useful, it can be overwhelming with so many techniques and procedures. It’s also important to avoid thinking of the matrix as a long list of mitigations / detections – even if you have a “tick in every box”, for every technique you can still be compromised. Remember – “Attackers think in graphs, defenders think in lists” (John Lambert), so just implementing long lists of security controls isn’t the right approach, instead use MITRE ATT&CK with the context of your business priorities and unique network environment to build cyber resilience.
Comparing the Cyber Kill Chain and MITRE ATT&CK
The two are related in that they describe the steps in different cyber-attacks, but they have different aims. The cyber kill chain is more generic and is an excellent introduction to the idea of hacking occurring in stages, and it’s a chain that you can interrupt with security controls. I find it very useful when communicating with non-IT and non-security people in business to get that basic understanding of the phases and how it works.
The ATT&CK matrix on the other hand is overwhelming for a non-technical audience (there are over 200 techniques) but is an excellent tool for understanding the technical steps attackers can take during a breach. And it can be used as a tool for evaluating coverage across the entire spectrum – “do we have detections for every technique in every tactic”, whilst not losing sight of the fact that even if you do, you may still be compromised.
It’s also interesting to see how these two fit into the larger landscape of regulatory framework that mandate certain cyber security controls, and other approaches such as the Center for Internet Security (CIS) benchmarks. CIS offers benchmarks for different operating systems, SaaS cloud services (including Microsoft 365) and IaaS / PaaS cloud platforms, and much more, for free.
These cover all the controls that you should implement as a baseline for security controls for that particular technology. Microsoft offers CIS benchmarks for both Azure and Microsoft 365 in their Compliance Manager app. And the upside is that if you implement all these controls you’ll have covered most, if not all, of the MITRE ATT&CK techniques.
Enhance employee awareness and safeguard critical data by leveraging Hornetsecurity’s Security Awareness Service for comprehensive cyber threat education and protection.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
For beginners in cyber security, I recommend studying the MITRE ATT&CK framework, it’s like a common language for talking about different types of attacks.
I warmly recommend the free courses offered by AttackIQ, they’ve got one on Threat-Informed Defense which goes in detail on the MITRE ATT&CK framework. And use the Cyber Kill Chain phases when talking to the rest of the business.
Both have their place and are useful in their own right in helping you build a more cyber-resilient business.
FAQ
The Cyber Kill Chain in a useful communications tool when conveying cyber security concepts to non-technical people, and a basis for an overall IT security strategy for a business. MITRE ATT&CK on the other hand exhaustively lists every attack technique, grouped by tactics, and mapped to different threat actors, allowing an organization to identify detection gaps.
There are a few different versions of the Cyber Kill Chain, FireEye (now part of Mandiant, which is now part of Google) proposed their variant which also has seven steps but which focuses more on the persistence of threats, whereas the Unified Kill Chain has 18 unique phases and attempts to marry the best of the original Cyber Kill Chain and MITRE ATT&CK.
Generally, when people mention MITRE ATT&CK they’re referring to the enterprise matrix, but there’s also one for Mobile and one for ICS. Furthermore, there’s the D3FEND matrix of cybersecurity countermeasures which is sort of the other side of the attack techniques, all the different controls that an organization can implement to mitigate the attacks outlined in ATT&CK.
