

Microsoft 365 Permissions and Copilot Security – a ticking time bomb for Security and Compliance
File sharing in business is one of those technologies that mostly happens “under the radar”. New SharePoint sites are spun up for projects or groups, or new Teams are created with lots of files shared.
This sharing can be both with internal users and external users. And mostly, no one thinks twice about it, until sensitive documents and data end up in the wrong hands.
In this article, we’ll look at the challenge of data governance, document sharing in Microsoft 365 and how it applies to compliance regulations and getting your business ready for Copilot for Microsoft 365 – all with the help of Hornetsecurity’s 365 Permission Manager.
The Dangers of Unmanaged File Permissions
As CISOs and IT admins know – file sharing, both with internal groups and external collaborators is designed to be as easy and frictionless as possible to cater for the reality of the modern, mobile, collaborative digital workplace.
From a compliance point of view however, this approach can be a ticking time bomb, plus there’s a new player on the scene that might accelerate the timer on that bomb – Copilot. Microsoft is keen to push the value of Copilot security for Microsoft 365 (at $360 USD per user, per year, you can’t pay per month) and here’s the rub – Copilot has access to the same documents as the user has.
Remember Delve? That was Microsoft’s earlier tech for suggesting documents to you, created by people you collaborated with that you might find valuable. Except sometimes business got a shock when they realized which documents were shared with different groups of people.
The Copilot situation is worse, because you won’t necessarily know which documents it has accessed to answer your prompt or create a new draft of a document for you.
Easy Sharing
Teams file sharing is possibly one of the most easily misunderstood avenues – when you share a file in a Teams channel, it’s actually stored in the team’s site in SharePoint. Whereas if you upload a file to a one-on-one or group chat, it’s stored in the Microsoft Teams Chat Files folder in your OneDrive for Business (which is actually a SharePoint site underneath the hood).
If you have a private channel, it gets its own, separate SharePoint site with a document library that only the members of the private channel have access to. So, the documents are all stored in various SharePoint sites, rather than in Teams itself.
And if you share a file with an external collaborator, depending on the settings your IT department has set in SharePoint online, this might send them an email with an invitation to create a guest account in your tenant.
If you’re a CISO, you’re probably concerned at this point. Business data is easily shared internally, possibly with staff that shouldn’t have access to it, and you have limited control over this sharing.
It’s also (likely) shared with external collaborators, and you don’t have a lot of insight into this sharing either. But you must thread carefully, a knee jerk reaction of locking down file sharing completely, with no external sharing and default tight permissions for internal sharing will just lead to users looking for an alternative way to get their job done.
Sensitive documents might then be shared via third party cloud storage, where you have even less visibility into the risks.
On the other hand, if you’re an IT admin, tasked with managing file sharing (on top of all your other duties) this can seem like an overwhelming challenge.
Where do you even begin? Even if you can produce reports on permissions granted, and files shared externally, you don’t know what’s oversharing and what’s legitimate business. You’ll have to work with various business departments to identify this, on a site-by-site basis.
Finally, if you’re an end user, understanding what control you have over sharing documents internally and externally (which will depend on the tenants configuration), and how you can inventory your own role in oversharing is near impossible to do with the built in tools.
Data Governance
Getting a handle on your current file sharing situation (in most businesses this is something that’s been part of the landscape for so long, that no one has the full overview to see just how bad it is), using the built in tools is challenging.
Auditing hundreds of sites manually is impossible, and even scripting PowerShell reports to gather the data is difficult.
Certainly, take a look at your current settings and the options you have in the SharePoint admin center which we covered in this article. But even if you tighten those settings today (they’re tenant wide), they only apply to new sharing, not existing shared sites, and files.
Remember that one of the tenets of Zero Trust (and it has been around long before that) is least privilege access. In other words, only give users access to the data they need to do their job, no more. And keep this up to date as they change roles in the organization or are promoted.
This rarely happens, instead people keep existing access and just accumulate more permissions. And inventorying exactly who’s got access to what documents is hard to do with the built-in tools.
Different regulations that you might have to comply with have varying approaches to controls around file sharing, in ISO 27001:2022, “Information security, cybersecurity and privacy protection” there’s A.8.12 Prevent the sharing of sensitive information within business communication platforms and under A.8.3 there’s Block access to files for specific users and Create and manage access reviews.
In HIPAA, the Health Insurance Portability and Accountability Act in the US, under § 164.308(a)(4) Standard: Access control you have Review user groups and applications with access to ePHI for example.
In the US, organizations doing business with the Department of Defense need to comply with CMMC, Cybersecurity Maturity Model Certification with a new version v2.0 in the works, here for example, SC.L2-3.13.16 has controls for Data at rest, and AU.L2-3.3.1 has System auditing.
As a last example, the CCPA, California Consumer Privacy Act, control 1798.150(a)(1) Data Security Breaches involves audit logging and Data Loss Prevention policies.
These are just a few examples, depending on where your business is located, and what vertical you’re in and the type of data you store and process, different regulations will apply.
What’s common across many of them is that you not only must control access to data with least privilege access, and audit access, often with regular access reviews – you must also be able to demonstrate to an auditor that you’re doing so. It’s not enough to say you are, you must collect and present evidence for how you’re doing it.
365 Permission Manager
What’s needed is a scalable tool that can span large tenants with thousands of SharePoint sites, which is easy to use and gives you a centralized management interface to apply policies, find deviations from those and remediate over permissioned access in bulk.
We looked at the basics of how 365 Permission Manager works here and this great video animation shows it visually. Instead of having to visit several different portals in Microsoft’s native tools, an IT administrator has a single console, and a single most important page – the To Do list.
This lists all the violations of the policies applied to every SharePoint Online site and let’s you remediate in bulk, as well as provide exceptions when there’s a business justification.
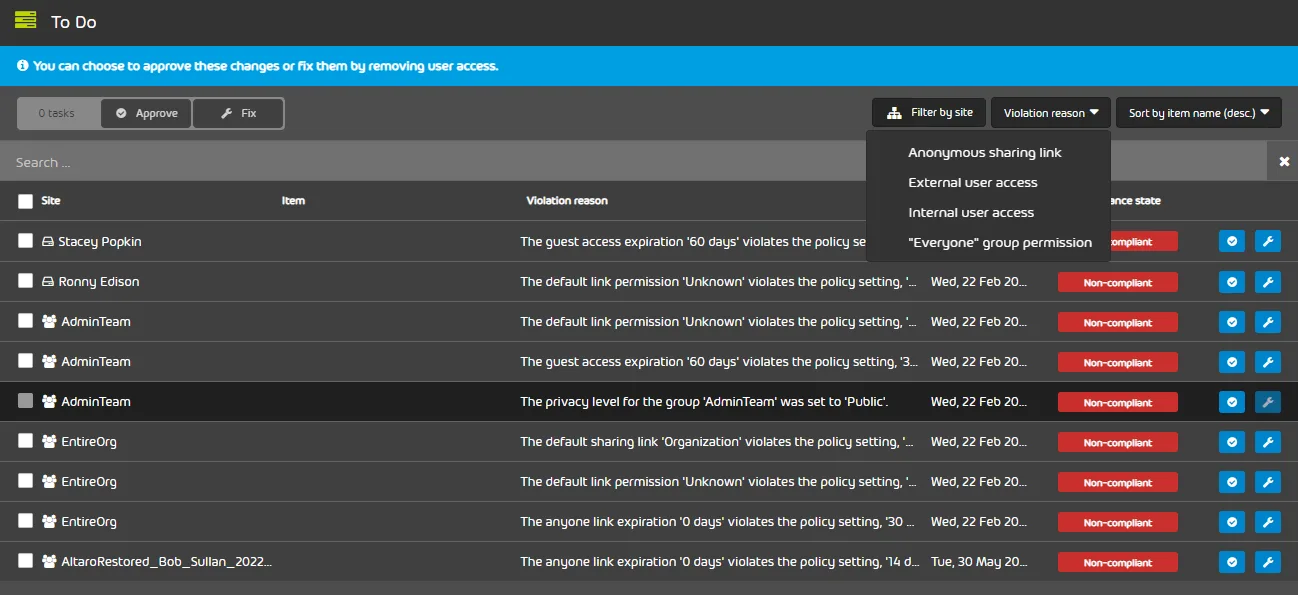
To do list – the IT administrators best friend
There are a number of built in compliance policies that you can apply to SharePoint sites, and you can also create your own customized ones.
This is a fundamental difference between the native approach and 365 Permission Manager, instead of having a single tenant wide default for all sites, that you must then further customize for each site, you apply a policy to each site, out of a library that you have adapted to your business.
The concerned CISO we mentioned above, he’s going to love the three reports that’ll show Full Site Permissions, User & Group Access and External Access.
And end users are also involved, receiving regular emails if their sites are violating policy, with links to 365 Permission Manager to remedy issues.
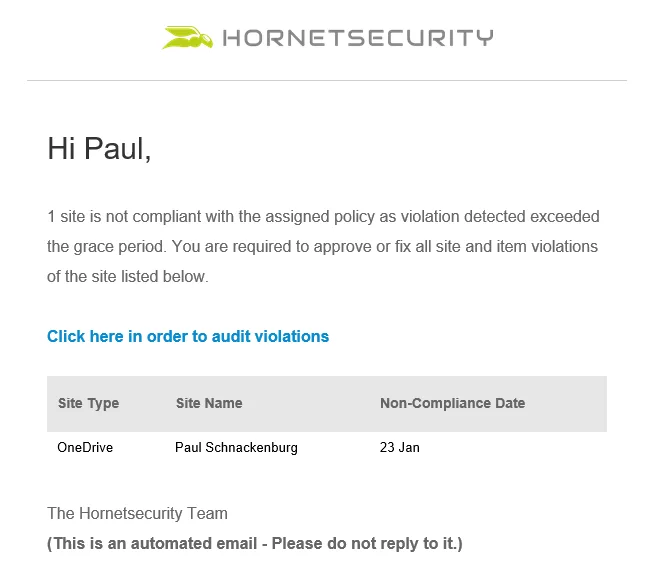
End user email notification
365 Permission Manager was initially built at Hornetsecurity to manage our own SharePoint file sharing challenges, and our CISO, Olaf Petry, loves having such a powerful tool, saying:
It is critical for a CISO to effectively oversee the company’s strategy and programs to ensure adequate protection of information assets and technologies, and yet this process can be very complicated. My peers often discuss what a great pain point it is for them. Hornetsecurity’s new 365 Permission Manager will set CISO’s minds at rest by enabling security and compliance managers and administrators to efficiently and easily control Microsoft 365 permissions, and help prevent critical data from getting into the wrong hands.
The ability to enter a username and see exactly what sites and documents a user has access to also really helps with preparing for an audit.
To effortlessly manage Microsoft 365 permissions, enforce compliance policies, and monitor violations with ease, utilize Hornetsecurity’s 365 Permission Manager. Protect your Microsoft 365 environment and make admin tasks a breeze.
Conclusion
Whether you’re working towards compliance with a regulation, preparing your business for users with Copilot for Microsoft 365 or just want to make sure sensitive data isn’t shared too widely, the answer is simple – 365 Permission Manager.
FAQ
Unmanaged file permissions pose a significant risk to data security and compliance. While file sharing is designed to facilitate collaboration, it can lead to sensitive documents ending up in the wrong hands. With the introduction of Copilot for Microsoft 365, the risks are further exacerbated, as it has access to the same documents as users, potentially compromising data privacy.
Teams file sharing, although convenient, adds complexity to data governance efforts. Files shared in Teams channels are stored in SharePoint sites, while those uploaded to chats are stored in OneDrive for Business. Managing permissions for these shared files, especially when collaborating with external users, can be daunting for IT administrators, leading to oversight and potential data breaches.
To address data governance and compliance challenges, businesses need effective tools like Hornetsecurity’s 365 Permission Manager. This tool offers centralized management of SharePoint permissions, allowing administrators to apply policies, identify violations, and remediate over-permissioned access. It provides customizable compliance policies, comprehensive reports, and end-user notifications to ensure data security and regulatory compliance.

