

BazarLoader Campaign with Fake Termination Emails
Summary
Hornetsecurity has observed a malicious email campaign distributing the BazarLoader using termination as a lure. The campaign uses a link to Google Docs from where the BazarLoader malware executable is downloaded.
Background
BazarLoader is a new malware loader attributed to a threat actor with a close relation to the TrickBot malware. The loader is also aptly named KEGTAP, as in device used to open a beer keg3, because it is used to “open” the network of victims for follow up malware in order to move laterally on the network and eventually deploy ransomware.
Technical Analysis
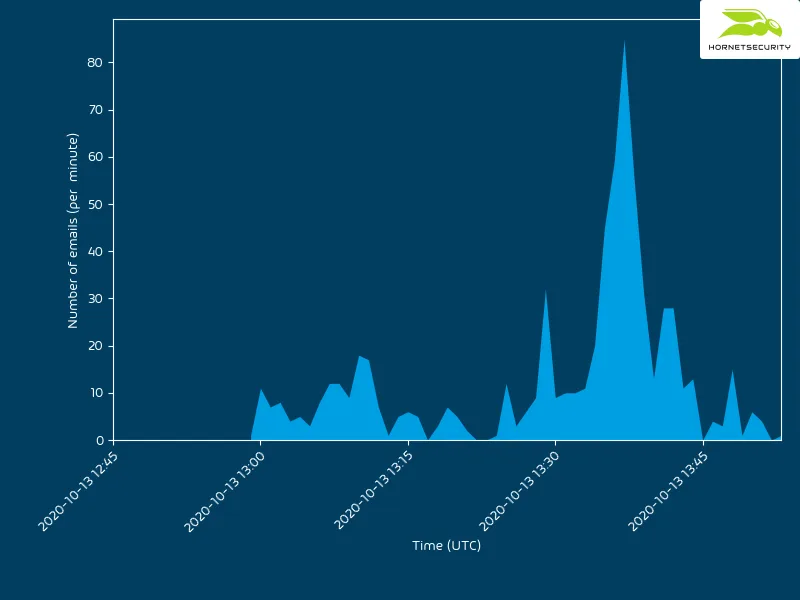
On 2020-10-13 at exactly 13:00 UTC Hornetsecurity registered the first emails of the new BazarLoader campaign:
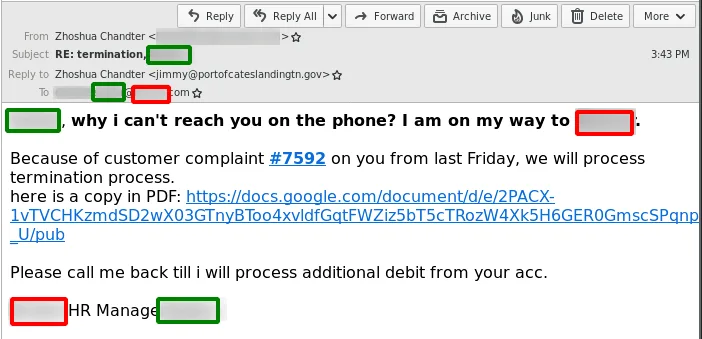
The emails use a termination lure:
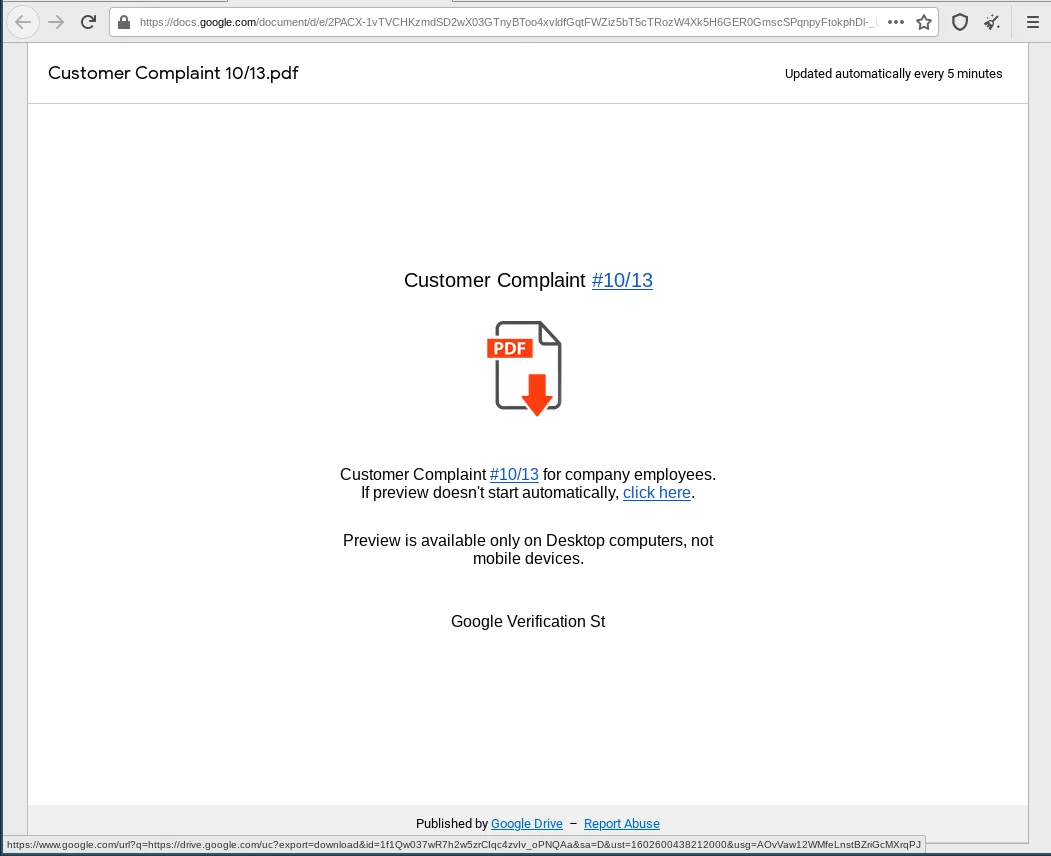
The URL in the email is a legitimate Google Doc URL:
From their all links lead to the BazarLoader executable (Report10-13.exe).
When executed, BazarLoader will use OpenNIC Public DNS Servers to resolve a .bazar domain generated via domain generation algorithm (DGA). The .bazar domain is not a regular TLD but rather an alternative DNS TLD of the decentralized EmerDNS blockchain DNS system.
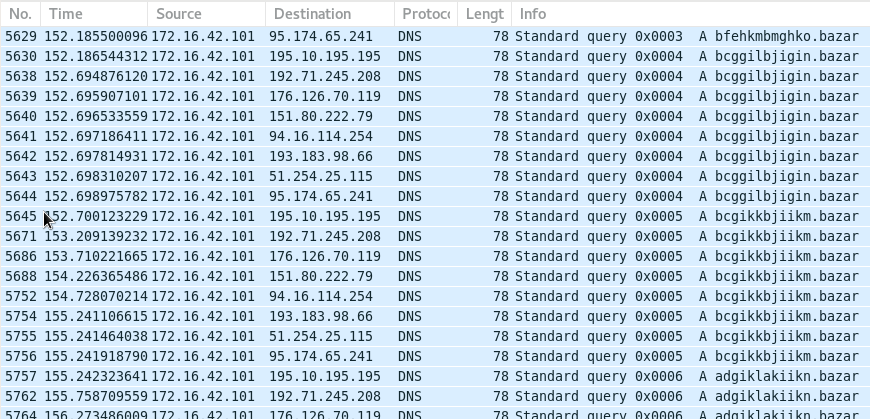
Then the BazarLoader will download and install the BazarBackdoor1. This backdoor will be used to move laterally in the victim’s network in order to take over the domain controller. Eventually the intrusion is monetized by deploying the Ryuk2 ransomware.
Conclusion and Countermeasure
Because the payload download is hosted on the legitimate Google Docs site victims are more likely to click the link in the email then they would an obscure URL they are unfamiliar with. BazarLoader’s use of the EmerDNS blockchain DNS system makes it immune to current efforts by various security vendors to disrupt the operations of TrickBot.
Hornetsecurity’s Spam Filter Service and Malware Protection, already detects and quarantines the outlined threat emails.
References
- 1 https://malpedia.caad.fkie.fraunhofer.de/details/win.bazarbackdoor
- 2 https://malpedia.caad.fkie.fraunhofer.de/details/win.ryuk
- 3 https://en.wikipedia.org/wiki/Beer_tap#Portable_keg_tap
Indicators of Compromise (IOCs)
Hashes
| MD5 | Filename | Description |
9cd1f319f58c3979399c1779d5a34bc2 | Report10-13.exe | BazarLoader |
IPs
OpenNIC Public Servers used by the analyzed BazarLoader version:
195.10.195.195(53/udp)192.71.245.208(53/udp)172.126.70.119(53/udp)151.80.222.79(53/udp)94.16.114.254(53/udp)193.183.98.66(53/udp)51.254.25.115(53/udp)95.174.65.241(53/udp)
URLs
hxxps[:]//docs.google[.]com/document/d/e/2PACX-1vTVCHKzmdSD2wX03GTnyBToo4xvldfGqtFWZiz5bT5cTRozW4Xk5H6GER0GmscSPqnpyFtokphDl-_U/pub


