

Understanding the Adversary-in-the-Middle Attack – How It Works and How to Defend Against It
What Is an Adversary-in-the-Middle Attack?
An adversary-in-the-middle attack (formerly Man-in-the-middle, sometimes now referred to as Attacker-in-the-middle) is a type of cyber attack in which an attacker intercepts and relays messages between two parties who believe they are communicating with each other. Since most people are linked in some form almost constantly, the internet plays a massive role in modern life.
As a result, most public areas (such as cafes, restaurants, and transportation) are furnished with free public Wi-Fi so that everyone may check their emails, bank accounts, social media, or, more likely, play the newest hot mobile game. Many individuals are unaware that counting on access to free WiFi might not be wise.
Public WiFi, though convenient, allows attackers to exploit users’ devices or intercept traffic for data theft. This can be as simple as setting up a fake network and performing an “Adversary-in-the-Middle Attack”, where they monitor (sniff) connections.
Connecting to such a network and logging into an unencrypted site can expose credentials, but, fortunately, modern websites often use Transport Layer Security (TLS) for encrypted connections.
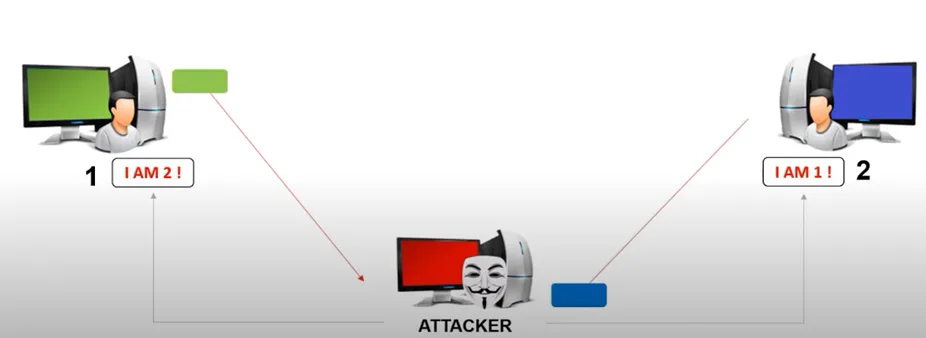
How Do AitM Attacks Work
AitM attacks hinge on a devious manipulation of trust. Essentially, attackers position themselves between two communicating parties, intercepting their interactions. This interception enables them to eavesdrop on conversations, access sensitive data, or alter the information exchanged. The process involves:
Interception
Attackers establish themselves as intermediaries, intercepting data traveling between victims and legitimate destinations.
Impersonation
Once in the middle, attackers can impersonate either party as legitimate senders or receivers.
Data manipulation
Attackers can modify data, inject malicious content, or withhold information to suit their malicious goals.
Key Concepts of an Adversary-in-the-Middle Attack
Adversary-in-the-middle attacks attempt to eavesdrop on and influence two parties’ communications, although the main motives include stealing sensitive data (passwords, financial info), eavesdropping on confidential conversations, injecting malicious content, and compromising transactions.
Malicious actors use the trust between victims and systems to exploit flaws and get unauthorized access to further their agenda.
There are numerous ways how the threat actor can “position” themselves between the communication of the trusting parties by employing various methods such as:
Interception
The most common, simple yet effective way when threat actors deploy access points that pose as a legit hotspot, and once users are connected, attackers intercept, manipulate, or monitor traffic, enabling eavesdropping, data theft, and data integrity.
Spoofing
Impersonating communication endpoints by spoofing ARP and DNS addresses, also called poisoning, to intercept and modify data:
- When the attacker sends phony Address Resolution Protocol (ARP) to reroute traffic through their system, packets that link their MAC address to a valid device’s IP address.
- Domain Name System (DNS) poisoning works by fooling your computer by modifying it into receiving false directions and navigating you to a false website owned by the attacker instead, which is similar to diverting traffic signs to the wrong location. Due to the phony website’s potential similarity to the actual one, you might not know that you’ve been rerouted, which can lead to data theft and security breaches.
SSL/TLS stripping
With SSL/TLS stripping, an HTTPS-safe connection is downgraded to a less secure encrypted HTTP connection, making the entire online connection insecure. ARP spoofing or creating a rogue access point could potentially let an attacker establish a position between you and the website you’re attempting to visit.
E-mail hijacking
E-mail hijacking in an AitM attack intercepts and alters email traffic by inserting themselves between your email client and server. They trick your client into a fake secure connection to manipulate or block emails, possibly stealing credentials.
They can forward or alter emails, leaving recipients unaware. To protect against this, use encrypted email protocols, be cautious on public Wi-Fi, update software, and use strong passwords.
Session hijacking
A distinct session that identifies the user on the server is formed when users connect to a server. Threat actors could sniff and access this session token when visiting websites that don’t use encryption or unsecured protocol like HTTP, allowing them to view data on a web application while posing as users.
MFA bypass
A more recent type of AITM is where criminals use an AITM kit to set up a fake login page, and then trick users to visit it (through an email or IM phishing email for example). Normally this type of attack should fail as in addition to entering a username and password, the user should perform another multi factor authentication step, such as approving a notification from a smartphone app, or enter a six digit code sent in a text message.
However, this type of AITM attack seamlessly monitors the MFA challenge, then grabs the users response code and passes that onto the real login site. The end result is that the user is no wiser to the fact that they were compromised, while the attacker now has full access to the users account.
How to Defend Against Adversary-in-the-Middle Attacks
Even though there are a lot of potential attack vectors for AITM attacks, hardening your organization will greatly diminish this type of threat.
Avoid phishing emails
Phishing emails are a common way for attackers to carry out AitM attacks. Phishing emails are designed to look like legitimate emails from a reputable source, such as a bank or an e-commerce website. They often contain a link to a fake website that looks like the real one. When you enter your login credentials or other sensitive information, the attacker can intercept it.
Be cautious of emails from unknown senders, and always verify the authenticity of emails before clicking on any links.
Encryption
One of the best techniques to stop AitM attacks is encryption. Your communication is protected by encryption from being intercepted and read by an adversary. Use secure email and messaging services, and always browse the web using HTTPS.
Today, HTTPS is frequently used by default on websites, adding an extra layer of protection. Use a virtual private network (VPN) to encrypt your communication when connecting to a public Wi-Fi network.
Verify SSL/TLS certificates
Before visiting a website, ensure the SSL/TLS certificate is still in good standing. Websites may be encrypted and authenticated using SSL/TLS certificates. If a website’s certificate is not current, a MitM attack may be underway. Verify that the website’s URL starts with “https://” rather than “http://” by looking at it.
Additionally, check for a lock iconin the address bar of your web browser, which denotes the presence of a working SSL/TLS certificate on the website. Today this is a red flag, most sites use HTTPS, especially as you can use free certificates from Let’s Encrypt and others.
Use secure Wi-Fi networks
Steer clear of insecure Wi-Fi networks wherever possible, especially in public areas like hotels, airports, and cafés. Unsecured Wi-Fi networks are susceptible to AitM attacks because anybody may eavesdrop on communications between networked devices.
Use a secure Wi-Fi or cellular network that needs a password instead. If you must use public Wi-Fi, encrypt your communication with a VPN.
One important factor is how you handle your employees, as over 95% of attacks that are happening are where the human element gets exploited. Being aware of the dangers and potential attack vectors threat actors use can be a great advantage in reducing the chance of being a victim of a AITM attack.
The ultimate way is to educate your employees about the dangers with a cyber security awareness service to protect your critical data.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
AitM attacks pose a severe risk to online communication and can potentially cause sensitive data theft, financial loss, and reputational harm. AitM attacks must be prevented by using precautions such as encryption, checking SSL/TLS certificates, and staying away from insecure Wi-Fi networks.
You may lessen your chance of being a victim of a AitM attack by exercising caution and adhering to recommended practices.
FAQ
An adversary-in-the-middle (AITM) attack occurs when a perpetrator inserts himself into a dialogue between a user and an application to either listen in on the discussion or to mimic one of the parties, giving the impression that regular information flow is taking place.
Adversary-in-the-middle (AitM) attacks may show symptoms like unexpected SSL certificate warnings, sudden HTTPS-to-HTTP changes, frequent authentication requests, unusual network behavior, unsolicited device pairing, missing security indicators, SSL certificate mismatches, and unfamiliar devices on networks.
Unexplained redirects to HTTPS sites, authentication prompts, or slow network speed can signal potential AitM activity.
An extremely sophisticated piece of cyber espionage malware called Flame, also known as Flamer or Skywiper, was found in 2012. It was probably created by a nation-state and was aimed toward the Middle East, particularly Iran, Israel, and the surrounding nations.
The flame could enter computers through USB sticks, network shares, and email attachments while utilizing several vulnerabilities because of its complexity and modular architecture. It spreads over networks, gathering information from emails, instant messages, and documents while staying covert and encrypted to avoid being discovered.
Instructions were given, and its command and control servers received stolen data. If necessary, Flame’s self-destruct function removed all traces.

