

7 Most Common Cyber Security Vulnerabilities in 2023
Keeping up to date with the world of information security and cybersecurity threats can feel like being a spectator in an endless sports match played across the Internet between rival teams, each constantly scoring points against each other. In this game, though, it isn’t the Yankees slugging baseballs against the Cubbies, instead the bad actors are the red team hackers looking to exploit security vulnerabilities or network vulnerabilities to gain access against the blue team defenders trying to prevent a security breach. The red team attempt to “score” by exploiting vulnerabilities using methods such as phishing attempts or social engineering and the blue team defend themselves using various security tools to stop this enemy from scoring a proverbial home run using malicious software.
In fact, to take this metaphor a step further, it’s often the case that instead of players playing against each other in the same country, we have nation-states “playing” against other nation-states.
In this article, we’ll share the 7 most common vulnerabilities and touch briefly upon what measures and controls we, as cybersecurity professionals, can implement to protect that which matters most to our business. But before we begin, there is an essential first step you need to take before tackling the vulnerabilities threat actors seek to exploit.
Making a plan
When considering the number of network security vulnerabilities that organizations may have, as well as the potential risk and exposure that comes with it, it can be quite daunting and that’s just from those that we know of!
Many cybersecurity professionals suffer from “paralysis by analysis,” or put simply “freak out”, when trying to figure out what vulnerability to address first.
If you look through advisories from organizations like OWASP, NIST, CISA, and various NCSC (National Cybersecurity Centers) around the world, the vulnerabilities in their advisories are often different. This might seem odd at first, but it’s all about context. For example, the top vulnerabilities in OWASP are web application vulnerabilities, whereas the vulnerabilities on CISA’s website, concern infrastructure. To illustrate this point, we reviewed the “top threats” from around 15 different websites and sources and found that although there were common vulnerabilities between some, not a single list on one site matched another.
When looking at network vulnerabilities that affect you or the organization you work for, these need to be in that context. What are the crown jewels of your business that you must safeguard? This is a critical step when making informed decisions as to which vulnerabilities present the largest amount of risk.
In order to tackle this challenge, we suggest using a risk-based approach, where you determine the priority in which to address these security vulnerabilities or network security vulnerabilities based on those that reduce the most amount of risk with the least amount of effort.
There are however common and “low-hanging” fruit vulnerabilities that we will share with you.
1. Zero-day vulnerabilities
Staying on top of and addressing known vulnerabilities can be an onerous process, but what about those vulnerabilities which you or your vendor don’t know about? Welcome to the hazardous world of zero-day vulnerabilities.
In simple terms, a zero-day vulnerability is referred to as “zero-day” because the vendor will have had “0” days to address the vulnerability due to not being aware of it and not having a patch to fix it. The exploit that it relates to is similarly referred to as a zero-day exploit.
This is a software vulnerability which malicious actors take advantage of to access sensitive data, steal data or depending on the extent of this exploit, can use it as a point from which to scan your internal network using a vulnerability scanner and locate other security vulnerabilities.
Mitigating against a zero-day vulnerability is particularly challenging as you are basically blind to this being exploited. In terms of mitigation though, this is where a comprehensive defence-in-depth strategy is your best friend, which includes a regular cadence of patching software security vulnerabilities, reliable security controls and monitoring tools to look for indicators of compromise across your entire network, to detect attempts by an unauthorized user to gain access.
2. Out of date or unpatched software
Related to zero-days and something mentioned in the previous paragraph is the often-overlooked and under-invested critically important practise of keeping operating systems and software patched with the latest security patches. This practise is also important when thinking about your overall risk management framework. It can take some discipline to ensure you are minimizing the amount of instances of outdated software, but in the long-run it’s incredibly important for your organization’s safety.
It’s not only IT Professionals in the organisation who need to stay on top of this, software developers do too. As part of their role, they are regularly installing dev tools, so developing and ensuring a good cadence of patching by them is important. Keeping your hardware and software programs patched and up-to-date shouldn’t be thought of only in this context but as part of a unified approach. If an attacker manages to breach your network using one of many available methods, one of the first things they’ll do is scan your network assets.
Having a process for updating software and patching it with a regular cadence reduces your risk. If a threat actor is able to gain access to your network, they’ll will search your entire network and exploit all types of network vulnerabilities they can locate.
This can be a challenging and burdening task, but there are many tools available which can automate this process. The key is to be aware of this risk and design a process to mitigate against it.
3. Missing or poor data encryption
Underscoring the methods we use to keep our organizations data network safe and secure is the CIA triad model in information security. Since we’re talking about encryption, let us focus on the “C” for Confidentiality, which in this context is how to keep your organization’s data private, only allowing authorised users to access or modify data.
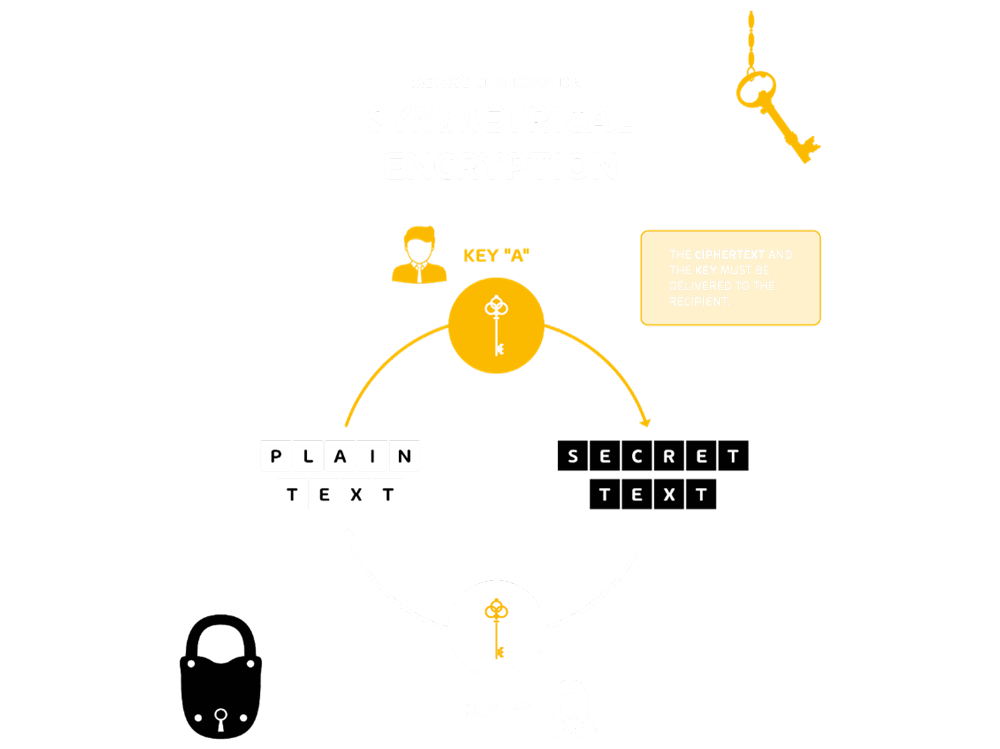
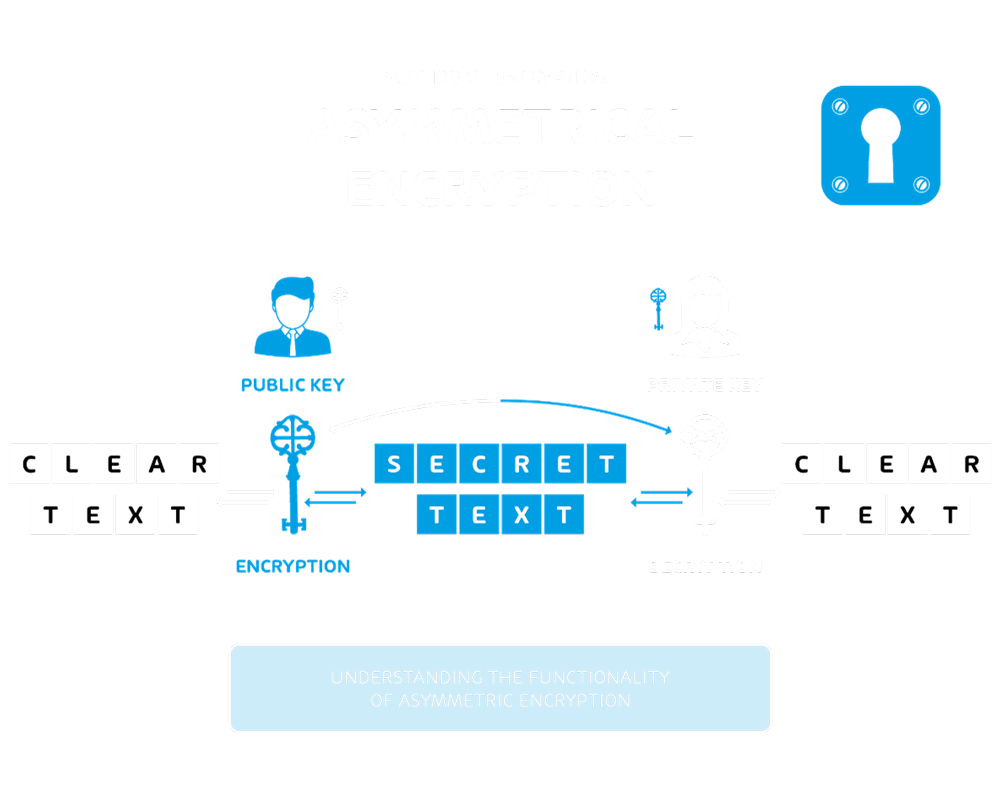
Data encryption, as a topic, is incredibly complex, but the infographics below are a good method of illustrating how data at rest and data in transit is typically encrypted
Data at rest – Symmetric encryption
Data in transit – Asymmetric encryption
Data breaches are unfortunately very common and it’s all too often that after a breach occurs and valuable data is obtained, we learn that some or all of this data was not encrypted. And even in those instances where it is encrypted, it was implemented poorly. Not all cryptographic algorithms are created equal, far from it in fact. If you currently use, or come across DES, 3DES, ECB, or RC4 for example, replace these with stronger algorithms immediately!
Encryption is necessary for data at rest and data in transit, by encrypting it when it is in these states. When at rest, this includes encrypting the data held on removable storage, servers (including and especially database servers), user endpoint devices and operating systems. Crucially, the keys used for the encryption must be adequately protected. Ensuring all data in the organization is encrypted is critical and a significant security risk which you must ensure is mitigated.
4. System misconfiguration
Raise your hand if you’ve ever installed new software application, then found that everything works as it should and considered your job done? The risk of following this practise at home is, well, pretty low. However, if you’re doing that for a business, reviewing the vendor’s default settings or not can be the difference between introducing new security vulnerability and having a breach, or not. This is a good time to use the zero-trust mantra: “trust nothing, verify everything.” Granted, this isn’t a typical scenario when you think about zero-trust, but that mantra is valid: you shouldn’t trust the vendor has shipped the application securely configured by default, you need to verify that.
Ensuring the settings for the software application are configured for secure use extends further than just reviewing the default application settings. Many Windows-based applications have multiple services configured to run automatically when Windows starts. Looking for and disabling unnecessary services is one of the low-hanging fruit which you should always tackle first. For those that are needed, do they all need to run automatically? Do they even all need to be constantly running? What type of account are they running under, local or network? These are the types of questions you must considering when configuring applications. If a bad actor has breached your network and is mapping it to see what software you have, they may use this attack vector to pivot and cause further damage. This is security hygiene you simply cannot ignore.
5. Insider threats
Often one of the most overlooked vulnerabilities to organizations is the enemy within. A disgruntled employee can be a very dangerous employee. Even more so if Privileged Access Management (PAM) is not well-known through security awareness training, or practised regularly throughout the business. Traditionally, insider threat has been thought of in the context of internal employees, however this could also be a vendor who spent time at or with your business and has a very strong familiarity with your infrastructure and network. Think about those contractors or vendors who worked on a long-term project which required them to be come intimately aware and familiar with your environment. One of the mitigations against this vulnerability is a finely-tuned, practised and monitored off-boarding process, so that when an employee does leave, their system login and all access is immediately removed. You should also ensure that when people change roles, their access level is appropriate for their new role and the previous access is removed if no longer required.
6. Phishing & Ransomware
Phishing and its multiple variations (e.g., spear-phishing, whaling, vishing, etc) continue to be one of the most significant and impactful threats to the enterprise and are unfortunately unique in that their impact is significant for both home users and businesses. As seen in the Cyber Security Report 2023, phishing was the most popular attack vector in 2022.
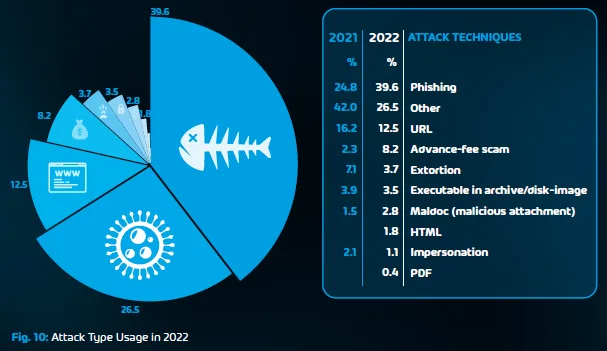
At its core, a phishing attack is done by sending a user an email impersonating their bank or another legitimate organization and often a cloud storage or messaging service. This social engineering technique uses wording suggestive of some type of urgency requiring an immediate response. Occasionally these emails, purporting to originate from a trusted sender, are poorly worded and easy to identify as being fake. There are, however, some that are very well composed and very difficult to detect as being fake. They rely on reaching the inbox of people who are not tech-savvy and easily influenced by the clever wording in these emails. The effort in composing and designing these emails is often minimal as they send out hundreds of thousands of these and all they need is a few people to fall for it to get a reward. A “simple” yet rewarding phishing attack for a bank login can result in someone’s entire bank balance being drained! Hornetsecurity employs a variety of powerful technologies, including Microsoft 365 Total Protection, to combat phishing attempts.
A successful phishing attack is often a platform for the attacker to gain a foothold and then pivot into ransomware. Although from an effort and reward point of view, businesses will almost always result in the largest payout, but stop for a moment and consider what you would do faced with the option of losing all your precious photos and videos forever. Worse yet, the decryption key isn’t always provided even if the ransomware is paid. As a result, businesses are refusing to pay ransomware.
Using multi factor authentication wherever possible is a good access control to mitigate against these, but it’s not bullet-proofed. This is where having an effective backup regime is crucial, particularly using the 3-2-1 strategy, where you have at least three copies of your backup in total. Two are stored locally (at your business or home) but on different devices or media and then at least one kept off-site. You’re only as good as your last backup!
To protect the organization and your users, fine-tuning the anti-spam features and a robust security awareness service is where you should focus your efforts.
7. Missing or weak authorization credentials
With all the innovation and technology available, it’s incredibly frustrating that we still find ourselves living a life controlled and managed by passwords. Microsoft introduced a fairly radical option earlier this year, allowing users to go passswordless!
We’d like to talk about missing or weak authorization credentials. Put simply, people using weak passwords. You know the feeling, when you’re buying something, registering for a social media account, or creating an account on a website requiring a password. Historically, most of these services would allow you to use a simple password like “123456”. If you are one of those people who do use that particular password, then you’re among the 1,526,537 people who also used it in 2022. If you thought using “password” was more secure, you’re in the company of almost 5 million others.
Suppliers of security and network equipment are often just as guilty, with admin/password as the default login combination. Worse still, credentials for the hardware appliance are frequently advertised on the supplier’s or manufacturer’s website, making an attacker’s life easier. They can simply look up the passwords on that site once they know what security appliance you’re using to secure your perimeter. Even if they can’t determine what device you have, they can guess your password using a technique known as a “dictionary attack,” in which an attacker uses a list of common words and phrases used by businesses and individuals, literally taken from a dictionary.
This is a situation where using multifactor authentication can really save you! One of the consequences of using weak passwords is that if an attacker has committed password theft and obtained the passwords for an organization using some other means, they use an attack method called “credential stuffing” in which they use the username and password credentials to see if they can gain unauthorized access to a service of that organization. The message here is clear: strong passwords are crucial.
Conclusion
As IT and cybersecurity professionals, we are uniquely placed and trusted to secure, defend and protect information security and devices against these attacks. These 7 common vulnerabilities covered and discussed here are a good starting point, but as indicated at the start of the article, it comes down to knowing what is most important to you, or your organization, which will inform your approach and the measure you put in place to secure and protect it.

