

Monthly Threat Report March 2024: A Busy Cybersecurity News Cycle with High-Impact Events
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of February.
Executive Summary
- There was a very slight decrease in the amount of email threats this month. That said, the email security landscape remains dangerous.
- PDF, HTML, and Archive files were the top three most used file types in email for the delivery of malicious payloads during the data period.
- Mining, Manufacturing, and Media organizations were the most targeted industry verticals during the last month, according to our data.
- Top impersonated brands in email attacks during this data period were Fedex, DHL, and Facebook.
- The well known Lockbit ransomware group was heavily impacted by international law enforcement, and has seemingly made a return days later. It remains to be seen if the group is still as impactful as before the law enforcement crackdown.
- A critical CVSS 10 vulnerability in the popular MSP tool ScreenConnect from Connectwise is already seeing exploit in the wild. An URGENTLY needed patch is available for those organizations running ScreenConnect On-Prem
- A ransomware attack on Optum/Change Healthcare has brought patient healthcare services within the US to a grinding halt.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for February 2024 compared to January 2024.
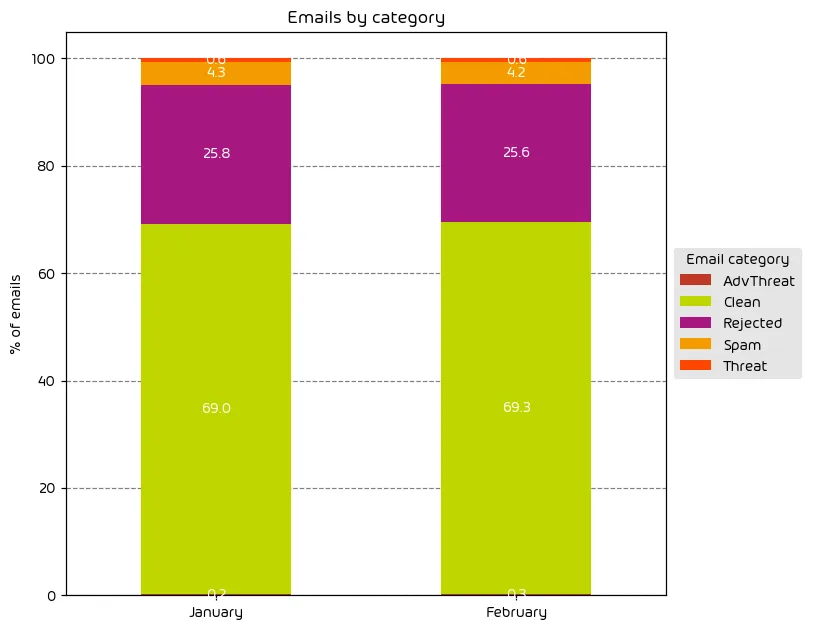
Overall there was little change in the overall threat-landscape during this data period when compared with last month. Overall threats are slightly down, but the danger level of the email security ecosystem remains at a high level.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
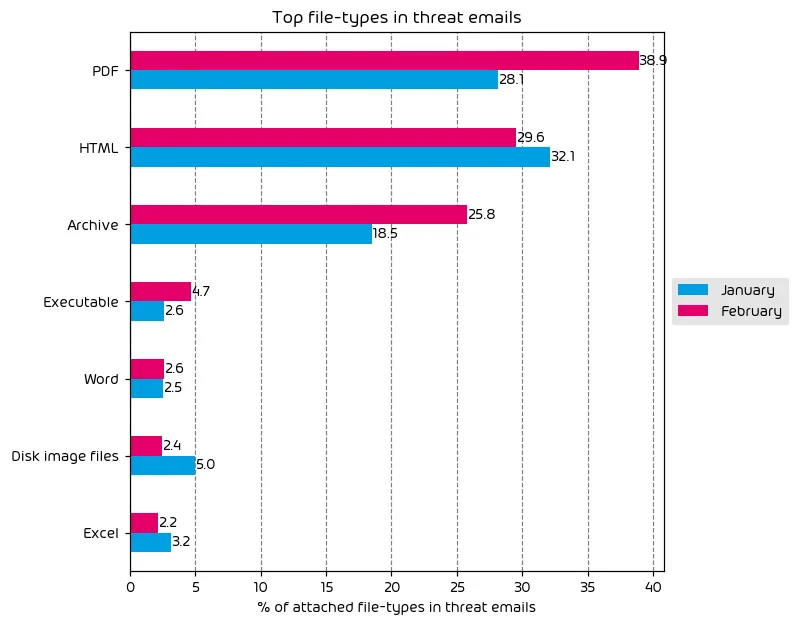
Threat actors notably use email attachments as one possible method to get their malicious payload on an end-user’s machine. Thus, this is an important metric that we track from month to month which provides insight into threat trends.
During this data period we observed a significant increase in the amount of malicious PDF files, and archive files. These are two file types that are adaptable and available to open on just about every platform on the planet, which drives their popularity amongst attackers. We also observed an increase in the amount of executable files as well. That all said, PDF, HTML, and Archive files remain in the top three slots during this data period.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
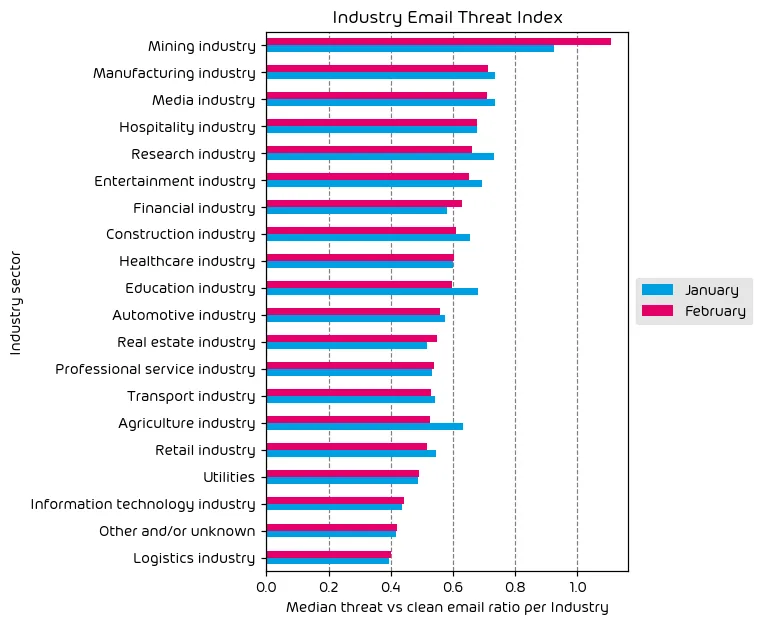
The Mining, Manufacturing, and Media verticals remain in the top three slots this month as the most targeted industries. We see the media industry as being heavily targeted in the coming year as threat actors will look to spread disinformation with large elections coming up within the next 10 months. Manufacturing and Mining continue to be a frequent target due to the fact that many organizations in these verticals have enough capital that they’re an enticing target. Additionally, there is a large subset of these organizations that don’t operate in heavily regulated sectors, and as a result are unlikely to have increased budgets for stronger security measures.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
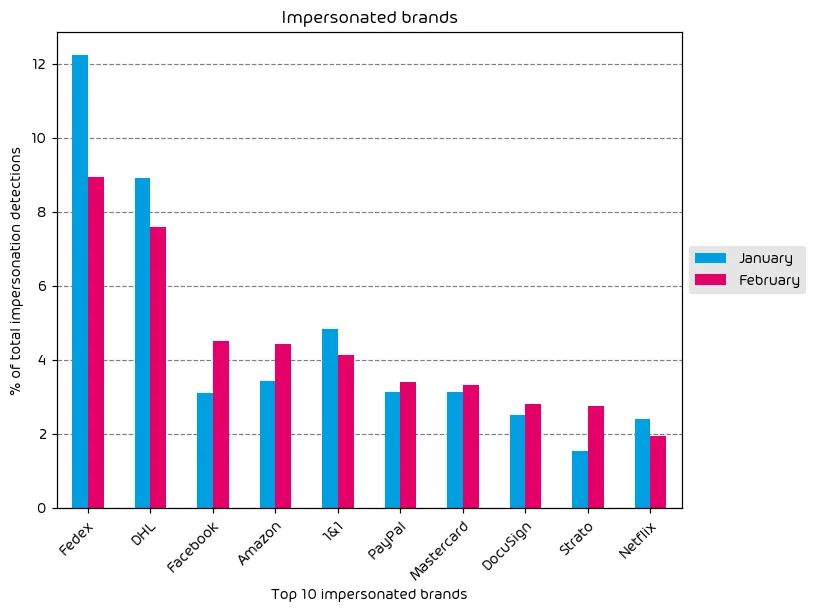
Fedex, DHL, and Facebook were the top 3 most impersonated brands in email attacks during the data period for this report. For DHL, and Fedex, it’s quite common to see shipping brands high on the list of brand impersonation attempts simply due to the fact that there is a high volume of emails associated with both of these brands. This includes shipping notices, delivery notifications, etc. That said, we did see a noted decrease in these occurrences during the last month. Facebook, along with Amazon saw noted increases in brand impersonation attempts.
Also of note are the small increases in brand impersonation attempts for Mastercard, Paypal, and DocuSign. This is common as we approach tax season for some countries, including the US.
Major Incidents and Industry Events
The Takedown and Reemergence of Lockbit
The well known ransomware group Lockbit was heavily disrupted by international law enforcement agencies during the month of February. Multiple known Lockbit associates are in custody and as a part of this effort, law enforcement came into the possession of more than 1000 decryption keys.
These keys will potentially help victims of the group recover impacted data. While this was good news, days afterwards things took a turn. It appears that Lockbit has already re-emerged with new servers and new encryptors. It remains to be seen whether this group has been severely impacted or if they’ve simply shifted operations elsewhere in light of recent law enforcement actions.
CVSS 10 ConnectWise ScreenConnect Vulnerability
The industry is prepping for potentially large supply chain attack as security and IT teams race to patch a critical CVSS 10 bug in Connectwise ScreenConnect, which is a popular remote access software primarily used by managed service providers. CVE-2024-1709 is a easily exploited remote authentication bypass bug that showed signs of use in the wild quickly after the news became public. Thankfully, a fix has been released for those organizations running ScreenConnect on-prem, while those organization using the cloud-hosted version are already remediated.
This issue brings to light the question of whether it’s a good security practice to include remote access software on every managed endpoint. While the MSP model leans on remote support capabilities heavily we’ve seen time and again how supply chain attacks can have a domino effect on the entire industry when applications such as ScreenConnect are impacted. It’s likely we haven’t heard the last of the news regarding this incident.
Change Healthcare / Optum Cyberattack
One of the biggest news stories to hit in the last month was the ransomware attack on Optum / Change Healthcare, a subsidiary of UnitedHealth by the BlackCat Ransomware Gang. The attack has left one of the largest US healthcare payment and processing organizations frozen for more than a week now, impacting healthcare in the US, and preventing patients from filling much needed prescriptions. The attack includes the theft of 6TBs of sensitive healthcare data, and it even appears that UnitedHealth may have paid a $22 Million USD ransom to get things back up and running.
While this seems to be your standard ransomware attack with the initial reports stating the breach stemmed from the above mentioned ScreenConnect Vulnerability (claims now debunked), it was far from from the standard ransomware attack in it’s impact. In fact, this attack could be seen as something of an escalation to the scale of the Colonial Pipeline ransomware attack some years ago. It’s an escalation in the fact that instead of just a monetary or reputation impact, the impact of this attack has a clear and present impact on the healthcare wellbeing of people. It’s not a stretch to say that if it hasn’t happened yet, we’re likely to see patient deaths in relation to this attack due to a loss of access to medication for some patients.
This attack has also had the effect of highlighting some key failure points within the US healthcare system. If the temporary absence of one organization has a ripple effect throughout the entirety of the US health system, then that is what we would call in the tech world – “A single point of failure”. This has lead to a joint #stopransomware advisory from CISA, the FBI, and the US Dept. of Health and Human Services (HHS). Whether this will be enough to shock the US healthcare industry to action remains to be seen.
Finally the story get’s weirder in that the alleged group (BlackCat) behind the attack appears to have short-changed one of the affiliate “Partner” groups that helped launch the attack and now appears to be pretending that they’ve been shut down by “the feds”. It appears BlackCat has taken their payday and run for now.
Further applicable updates to this situation in next month’s report.
Predictions for the Coming Months
- Brand Impersonations for services like DocuSign are likely to increase moving into the Tax Season in the US.
- The Connectwise ScreenConnect Vulnerability will have a domino effect throughout the industry. Int he coming months and weeks we’re going to see a number of breached organizations impacted by this vulnerability.
- Further info will come out regarding the Optum/Change Healthcare breach, hopefully leading to some positive change in the healthcare system with regards to security posture and single points of failure.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Andy Syrewicze, Security Evangelist, on The Optum / Change Healthcare Breach:The situation with Change Healthcare is one of those cases where it becomes really clear that issues with our digital estates can have a very real and severe impact on human life. Yes, there’s no denying that the financial and reputation losses we see in your average ransomware attack are bad, but when I look at this attack, and the direct impact it has had on human wellbeing, it’s an entirely different scale. When the impact from an attack is the potential loss of life (due to loss of access to medication and health services in this case), the burden of defensive security starts to feel quite heavy. We can only hope that our lawmakers, executive leadership teams, and society will provide the resources necessary to fight this escalation in the future.
From Matt Frye, Head of Presales and Education, on the Seeming Ease of Recent Attacks:The ease of attacks is what has hit me in recent months, not only the availability of tools on the public internet, but also the SaaS availability of attack methods, (which is not new), These are a growing concern. The sheer amount of monthly data breaches shows that the arms race is escalating, and only by implementing a comprehensive cybersecurity strategy, alongside a comprehensive BCP can businesses help to mitigate the risks.
Monthly Recommendations from the Hornetsecurity Security Lab
- If you’re organization uses the On-Prem version of ScreenConnect from Connectwise, you’re URGENTLY advised to apply the latest update ASAP. Info can be found HERE.
- The high profile ransomware attack by BlackCat this month is a good reminder to reassess you disaster recovery plan if you haven’t in some time. Make sure to run though a full recovery test and insure that you’re protecting your backups from ransomware using a feature such as immutable storage.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.


