

Monthly Threat Report January 2025: A New Year to Fend off New Attacks
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Review focuses on data from Q4 of 2024. As a reminder we moved away from monthly data reviews sometime ago in favor of quarterly reviews. This allowed us to provide commentary on larger movements in the security landscape as opposed to month-to-month.
Executive Summary
- The number of email based attacks increased in Q4 2024 vs Q3 2024.
- Archives, PDFs, and HTML files were the most popular types used by threat actors for the delivery of malicious payloads.
- DOCX and XLSX files saw a noted decrease in usage by threat actors after a surprising increase in Q3 of 2024.
- The education sector saw a noted increase in the amount of email based threats and has moved it’s way up to the top three most targeted industries for this data period.
- The top three targeted sectors during this data period are Mining, Entertainment, and Education.
- DocuSign is the top most impersonated brand during the data period.
- DocuSign, PayPal, and Intuit all saw a 3X increase in the use of their brand by threat actors to launch impersonation attacks.
- There were many attacks on telecom organizations in the US as well as in the UK during the month of December.
- Critical Infrastructure in Costa Rica was targeted and impacted during the month of December.
- The report covers a number of predictions and recommendations for the coming months given the current threat landscape.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for Q4 of 2024 compared to Q3 of 2024.
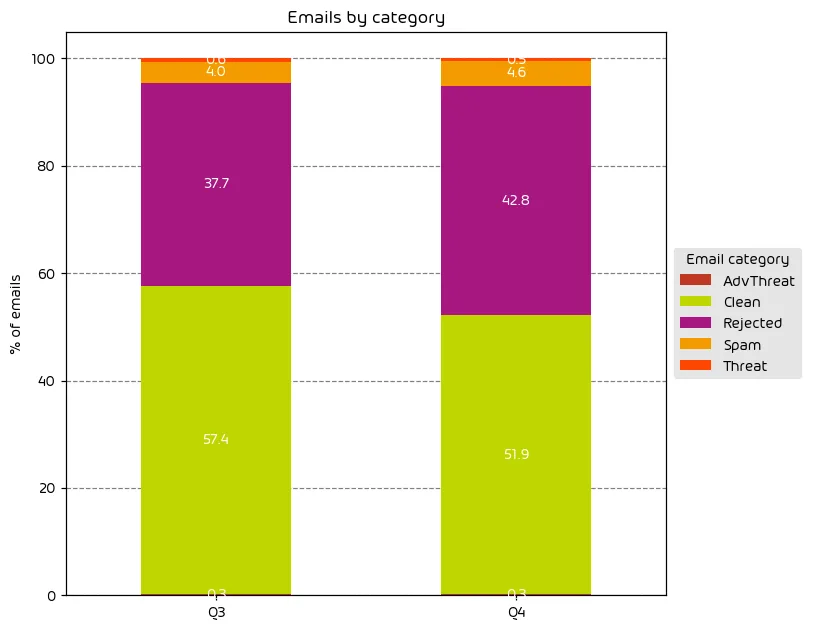
As is the norm for Q4 in any given year we observed a noted increase in nearly all attack categories during the final quarter of the year. This is primarily due to the winter holidays and the increase in online shopping and communications. Threat actors look to capitalize on this increased digital usage and inject themselves into communication streams around product shopping and delivery.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
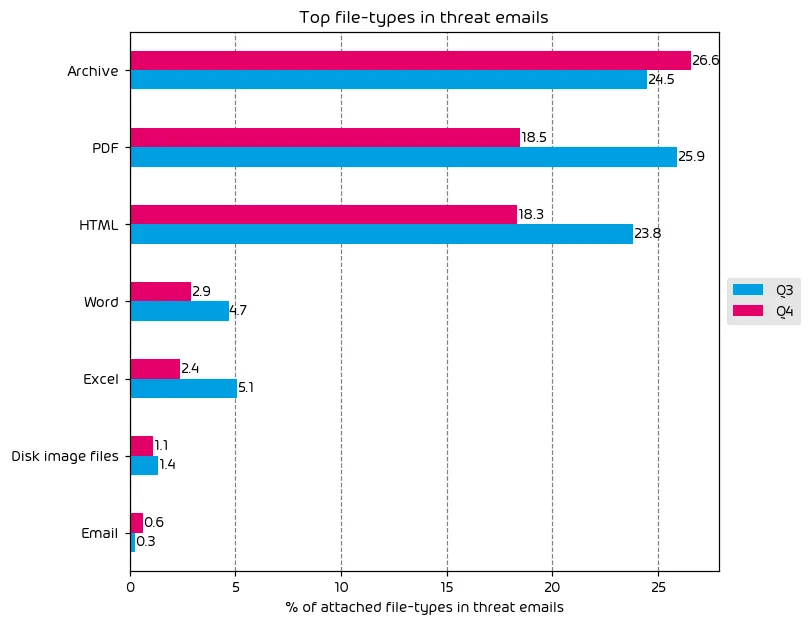
During Q4 of 2024 we noticed a slight increase in the usage of archive-type files for the delivery of malicious payloads. PDFs, and HTML files saw significant decrease in the amount of use while malicious office related files saw a decrease as well after a surprising increase in Q3.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
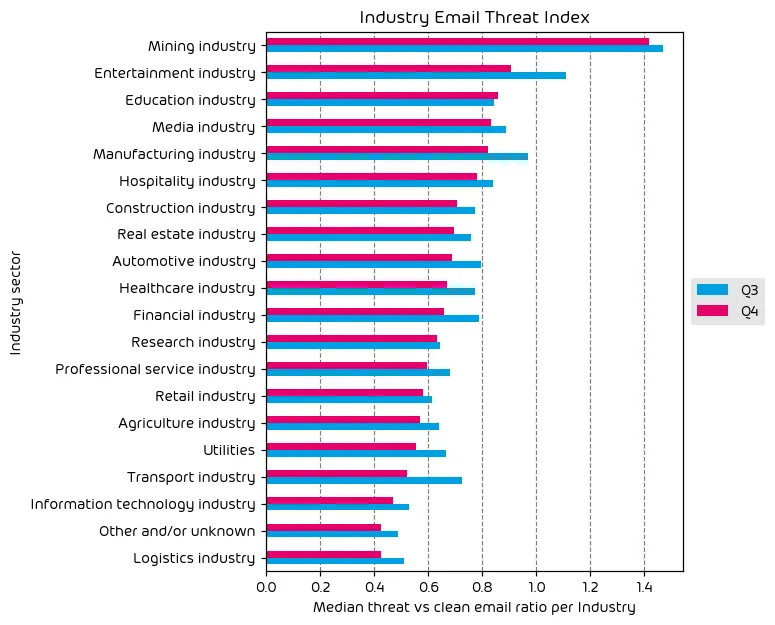
The email threat index saw a decrease for nearly all industries during Q4. The exception here was the education space. Which made it into the top three spots of most targeted industries. Educational institutions have increasingly come under attack in the recent past as many of them have small budgets to work with, and often lack effective security controls.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
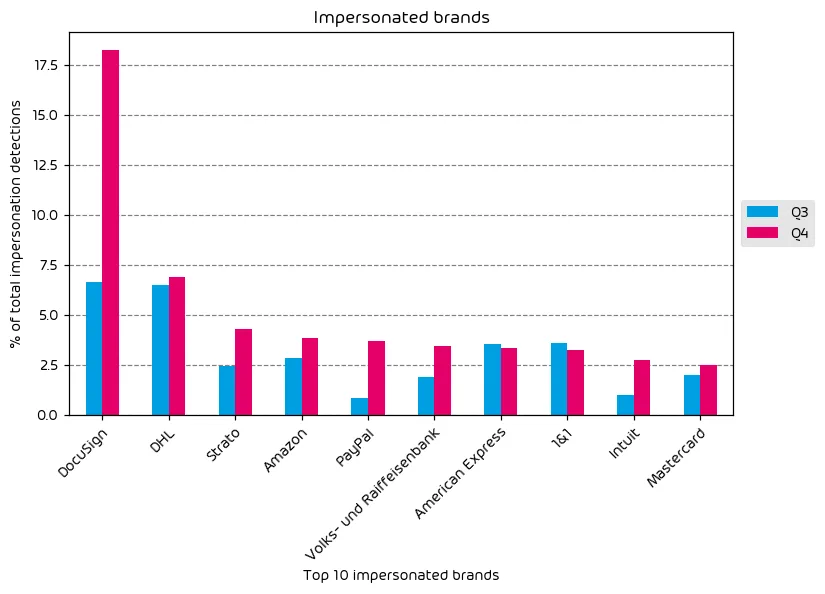
We have some interesting stats to look at in the impersonated data for the last quarter. As shown in the graph above, we observed that DocuSign, PayPal, and Intuit brand use in impersonation attacks nearly tripled. Typically this type of data indicates a targeted spam campaign using said brand of which we saw multiple said campaigns during Q4 of 2024.
If we look at the DocuSign campaigns specifically, there were, again, many of them. However, each campaign followed a predictable and similar attack pattern. Sender addresses were specific to each campaign and each lead victims to a URL. Said URL was either malicious for use of payload delivery or it lead the victim to a credential capturing form via a phishing kit. These campaigns were well-polished and formatted as shown in the screenshot below.
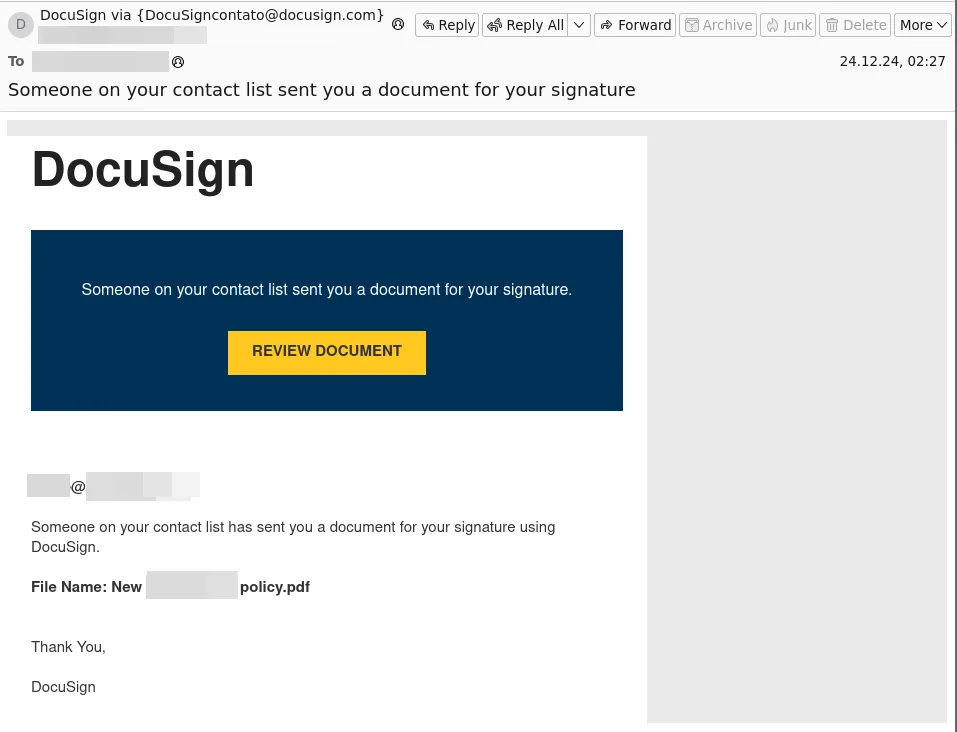
Also worth noting about these campaigns is that many of them made use of URL shorteners, such as t.co. This method is typically used by threat-actors to try and obfuscate where the link actually leads too. We continually observed this behavior during these particular campaigns, so we can surmise that attackers must be having some level of success with this style of attack.
Notable Incidents and Industry Events
Ransomware Attack on RECOPE
In December 2024, the Costa Rican state energy company, RECOPE, fell victim to a sophisticated ransomware attack that significantly disrupted its operations. The attackers managed to infiltrate the company’s network, encrypting critical data and demanding a hefty ransom for its release. As a result, RECOPE was forced to revert to manual operations, causing delays and operational inefficiencies. The Costa Rican government swiftly responded by enlisting the help of U.S. cybersecurity experts to mitigate the damage and restore normalcy. This incident underscores the growing threat to critical infrastructure and highlights the urgent need for robust cybersecurity measures and comprehensive incident response plans to safeguard essential services. We’re likely to see increased attacks on core infrastructure in the coming months as a result of the many conflicts happening in international relations right now. This is not to mention the ongoing and persistent threat from cyber criminal groups as well.
Data Breach at British Telcom (BT)
The telecommunications giant BT experienced a severe data breach in December 2024 and ransomware infection, which exposed sensitive customer information (500 GBs Worth!). The incident not only compromised the privacy of millions of customers but also raised serious concerns about the company’s data protection practices. In response, BT initiated a thorough investigation and implemented enhanced security protocols to prevent future breaches. This event is notable not only because of who the target is, but also the fact that the attack is Black Basta. This group has been highly active in the recent past. Here at Hornetsecurity we actually talked about them recently in regards to mail bombing attacks. This shows that the group is not only active, but motivated and knowledgeable. This will be a group that will be watched by the industry closely in the coming months.
US Telecom Sector Attacks
The telecommunications sector faced a major cyber threat in December 2025, with the China-linked hacking group Salt Typhoon launching coordinated attacks on major U.S. telecom companies, including AT&T and Verizon. These breaches appeared to be intended to access sensitive information related to foreign intelligence and high-profile customers in government and politics. The attacks, part of a broader campaign impacting a number of telecom firms, exposed significant vulnerabilities within the sector and underscored the critical importance of securing communication infrastructure. This incident, described as one of the most significant hacks of the U.S. telecommunications industry to date, prompted urgent calls for enhanced security measures and regulatory oversight to protect against future threats.
CISA has released more info on this attack to assist IT staff with hardening their systems.
Predictions for the Coming Months
- Increased Targeting of Critical Infrastructure: Expect more sophisticated cyberattacks on essential services like energy and transportation.
- Heightened Data Privacy Concerns: Stricter regulations and enhanced data protection measures will become crucial.
- Persistent Threats to the Healthcare Sector: Healthcare organizations will remain prime targets for cybercriminals.
- Evolution of Ransomware Tactics: Cybercriminals will continue to refine their ransomware techniques, including double extortion.
Monthly Recommendations
- Strengthen Incident Response Plans: It’s a new year and it’s time to check your security posture! Ensure your organization has a robust incident response plan in place. Regularly update and test these plans to quickly and effectively respond to cyber threats.
- Enhance Data Protection Measures: With a continuation of ransomware attacks over this reports data period, it’s serves as a reminder to take sometime to make sure your backups are as effective as they possibly can be. This includes leveraging features like immutable backup storage!
- Invest in Advanced Threat Protection: Attackers are increasingly getting more sophisticated, and so should you! Make sure you’ve got effective ATP scanning for incoming communications. This will allow you to detect advanced attacks before they start!
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.


