
Hornetsecurity Q3 2024 Ransomware Attacks Survey
Ransomware Attacks Are Decreasing, but Recovery Is Becoming More Challenging, the Hornetsecurity Q3 2024 Ransomware Attacks Survey Finds
Key Takeaways from the Q3 2024 Hornetsecurity Ransomware Attacks Survey
- 18.6% of respondents reported that their organization had been the victim of a ransomware attack in 2024, continuing a downward trend from previous years.
- 16.3% of ransomware victims paid the ransom to recover their data, a sharp increase compared to 6.9% in 2023.
- 14% of respondents whose organization suffered a ransomware attack reported that their backup storage was also compromised.
- 52.3% of ransomware attacks were caused by email/phishing attempts, making it the most consistent attack vector over the years.
- 55.8% of ransomware attacks targeted small organizations with 1-50 employees, with 1 in 5 of those organizations opting to pay the ransom.
- 32.6% of ransomware victims were unsure if their data had been exfiltrated during the attack.
- 81.3% of organizations provide training to end users on how to recognize and prevent ransomware attacks.
- 52.2% of respondents expressed a need for more ‘time-friendly’ end-user training.
- 27.4% of respondents would invest in upskilling their IT department if given an additional security budget.
- 66.9% of respondents reported that the availability of generative AI has increased their concerns about becoming a ransomware target.
- 9.8% of respondents were unaware that Microsoft 365 data could be impacted by ransomware, a significant improvement from previous years.
- 54.6% of organizations have purchased ransomware insurance, a significant rise from 42.2% in 2023.
About the 2024 Ransomware Attacks Survey
Ransomware remains one of the most pressing threats to organizations worldwide. To stay on top of these developments, the Hornetsecurity team regularly conducts surveys to track trends and gather insights from IT professionals.
In this year’s ransomware attacks survey, we expanded our scope to explore not only the frequency and impact of ransomware but also how organizations are adapting their defenses to cope with these sophisticated threats.
Last year, our survey revealed that six in ten respondents were ‘very’ to ‘extremely’ concerned about ransomware attacks, and this concern persists in 2024 as ransomware attacks become more difficult to recover from. With 502 respondents participating this year, the survey results shed light on both progress and ongoing challenges in ransomware protection.
Over the past four years, the percentage of organizations that reported being victims of ransomware attacks has fluctuated, with a notable drop to 18.6% in 2024, the lowest since the survey began in 2021.
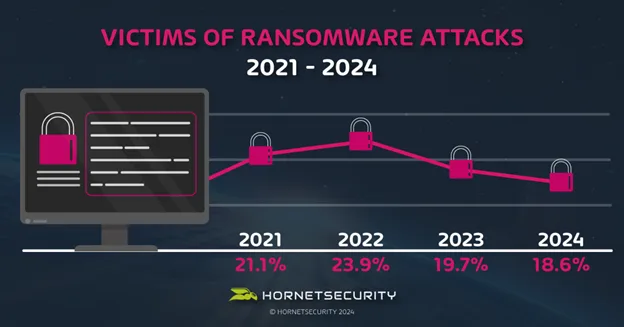
However, the data also shows a concerning rise in the complexity of these attacks. More organizations are now forced to pay a ransom to recover their data, with the percentage jumping to 16.3% in 2024 compared to 6.9% in 2023.
Ransomware is a particularly dangerous form of malware that encrypts a victim’s files or entire systems, leaving them inaccessible. Cybercriminals then demand a ransom, often in cryptocurrency, in exchange for the decryption key needed to regain access to the data.
These attacks can lead to severe consequences, including significant financial losses, operational disruption, and long-term reputational damage to businesses.
This year, our 500+ survey respondents offered valuable insights into the most common attack vectors, such as email/phishing, and the tools being used to combat ransomware, such as endpoint detection software, backup solutions, and end-user security training.
As ransomware tactics continue to evolve, organizations must remain vigilant, investing in advanced protection strategies and disaster recovery solutions to mitigate the impact of these increasingly sophisticated threats.
16.3% of Ransomware Victims Paid the Ransom, and 14% Had Backup Storage Affected
A significant 16.3% of respondents who were victims of ransomware in 2024 reported paying the ransom to recover their data—a sharp rise from previous years, where the percentage hovered below 10%.
This sharp increase highlights the growing desperation among organizations to regain access to their critical data, especially as the sophistication of ransomware attacks continues to evolve. More attackers are encrypting not just primary systems but also targeting backups, which traditionally served as a company’s final safety net.
This is accompanied by another worrying statistic: 14% of ransomware victims reported their backup storage was also affected during the attack, either encrypted or rendered inaccessible. This significantly limits an organization’s ability to recover data through traditional means, increasing their reliance on ransom payments.

The targeting of backup storage not only cripples immediate recovery efforts but also underscores the need for more secure, layered backup strategies, such as immutable backups or air-gapped storage, to mitigate this growing threat.
These figures indicate that ransomware attackers are getting better at understanding and circumventing traditional defense mechanisms, putting more pressure on organizations to rethink their approach to backup and data recovery solutions.
Without robust and isolated backup systems, companies may find themselves more vulnerable than ever to ransom demands.
Email/Phishing Attacks Remain the Most Common Ransomware Entry Point

Email and phishing attacks continue to dominate as the primary entry point for ransomware, with just over half of all ransomware incidents in 2024 originating from these methods.
Phishing attacks typically involve tricking employees into clicking on malicious links or opening infected attachments that enable ransomware to be deployed within the network. These attacks often bypass traditional security measures by exploiting human error—employees unknowingly download malware or provide credentials that give attackers access to critical systems.
As attackers refine their techniques, phishing emails are becoming more sophisticated, often mimicking legitimate communications, making it harder for users to distinguish between authentic and fraudulent emails.
In 2022, phishing and email-related attacks accounted for 58.6% of ransomware incidents, a number that slightly decreased to 51.7% in 2023 before rising again to 52.3% in 2024. Despite these small fluctuations, email and phishing remain the most consistent and effective attack vectors for cybercriminals seeking to breach organizations’ defenses.
Small Organizations Are the Most Vulnerable to Ransomware, With 55.8% of Attacks Targeting Companies of 1-50 Employees

Small organizations, particularly those with 1-50 employees, remain a prime target for ransomware attacks, often due to limited resources and weaker cybersecurity infrastructures.
In the 2024 survey, 55.8% of reported ransomware incidents affected small businesses, underscoring their vulnerability. Cybercriminals are acutely aware that these companies are less likely to have sophisticated security measures in place, making them easier targets compared to larger organizations with dedicated cybersecurity teams and tools.
The financial impact of these attacks on small businesses is particularly concerning. Of the small businesses that were targeted, 1 in 5 ended up paying the ransom to recover their data.
Among those who paid, 60% handed over ransom amounts ranging between $10,000 and $100,000. The remaining victims paid less than $10,000, but even these smaller sums can be devastating for businesses operating on tight budgets. These payments can severely strain a company’s financial health, forcing them to divert funds away from growth initiatives, employee salaries, or operational needs.
Nearly 1 in 10 Organizations Don’t Know How Their Systems Were Infiltrated

A significant challenge in ransomware prevention and recovery is the inability of some organizations to pinpoint how their systems were breached.
In 2024, nearly 1 in 10 respondents reported that they did not know how ransomware had infiltrated their systems. This “unknown” factor presents a serious obstacle for organizations attempting to strengthen their cybersecurity measures and prevent future attacks.
When the attack vector remains unidentified, organizations are left in the dark about where their vulnerabilities lie, which hampers their ability to implement targeted security improvements.
Without this knowledge, businesses may not know whether the breach occurred due to a phishing email, a compromised network, or an insider threat. As a result, they are unable to close the security gaps that allowed the ransomware to penetrate in the first place, leaving them exposed to repeat attacks.
The lack of clarity around attack vectors also complicates post-attack analysis and recovery. Without a clear understanding of how the system was infiltrated, it becomes more difficult to develop effective incident response strategies, secure compromised systems, and restore operations.
Moreover, it can delay the implementation of preventive measures, which is critical in today’s environment where ransomware threats continue to evolve and become more sophisticated.
1 in 3 Ransomware Victims Are Unaware If Their Data Was Exfiltrated

In 2024, a concerning 32.6% of ransomware victims admitted they were unsure whether any of their data had been exfiltrated during the attack. This uncertainty is indicative of the growing complexity of ransomware operations and highlights significant gaps in many organizations’ ability to monitor and protect their data integrity, both during and after an incident.
Ransomware attacks have evolved beyond simply encrypting data for ransom. Increasingly, attackers are not only locking down systems but also stealing sensitive information to leverage for additional extortion, known as “double extortion.”
In these cases, the cybercriminals demand a ransom not only to unlock the systems but also to prevent the public release or sale of exfiltrated data. The fact that nearly one-third of victims are unaware whether their data was stolen indicates that many organizations still lack the necessary tools and protocols to track data movement and detect unauthorized access.
This knowledge gap can be devastating. If organizations are unable to determine whether data has been exfiltrated, they may underestimate the full scope of the attack.
Failure to identify data theft could lead to prolonged exposure of sensitive information, reputational damage, legal liabilities, and potential non-compliance with data protection regulations like GDPR or CCPA.
81.3% of Organizations Provide End-User Training on Ransomware Prevention

End-user training has emerged as a cornerstone of organizational defenses against ransomware.
In 2024, 81.3% of organizations reported that they provide their employees with training on how to recognize and flag potential ransomware attacks.
This marks a steady improvement in overall employee preparedness, highlighting the growing awareness of the importance of empowering staff to act as the first line of defense against cyber threats.
Given that phishing and social engineering attacks remain common ransomware entry points, equipping employees with the knowledge and skills to identify these threats is critical. Through effective training programs, employees can learn to recognize suspicious emails, avoid clicking on malicious links, and report any unusual activity.
In addition to spotting phishing attempts, end-user training also teaches employees about broader cybersecurity hygiene, such as creating strong passwords, avoiding the use of unsecured devices, and adhering to company protocols around sensitive data handling.
The goal is not just to prevent ransomware from gaining a foothold but to instill a culture of security awareness that permeates the entire organization.
However, the effectiveness of these programs depends heavily on how they are implemented. Continuous training and regular updates are essential, as the tactics used by cybercriminals are constantly evolving.
Organizations that invest in keeping their training programs up to date ensure that their employees remain alert to the latest threats, from spear-phishing schemes to advanced social engineering tactics.
Organizations Seek More ‘Time-Friendly’ Ransomware Training Programs

While the majority of organizations now offer end-user training on ransomware prevention, a significant number are seeking ways to make these programs more efficient.
In 2024, 52.2% of organizations indicated that their current training programs could be improved by making them more ‘time-friendly,’ pointing to the ongoing challenge of balancing thoroughness with time efficiency in cybersecurity education.
The need for time-friendly training stems from the fact that employees are often inundated with various tasks, making it difficult to allocate extended periods for cybersecurity education. Traditional training sessions, which can be lengthy and information-heavy, risk overwhelming employees, leading to decreased engagement and retention.
As a result, organizations are looking for ways to streamline these programs without compromising the quality or effectiveness of the content.
One solution gaining popularity is the adoption of microlearning modules—short, focused training sessions that cover specific topics in digestible segments.
By breaking down complex cybersecurity concepts into smaller, easily manageable lessons, employees can absorb the material more effectively while minimizing disruption to their regular work schedules. Microlearning also allows for more frequent refreshers, ensuring that the content remains top of mind without requiring extensive time commitments.
Upskilling the IT Department Is a Top Priority for Increased Security Budgets

In 2024, when asked where they would allocate additional IT security budgets, 27.4% of respondents prioritized the upskilling of their IT departments. This growing emphasis on IT department training reflects a broad recognition that well-equipped and knowledgeable IT teams are essential in combating increasingly sophisticated ransomware attacks.
As ransomware threats evolve, IT teams need more than just basic cybersecurity knowledge. They must be adept at handling advanced security protocols, threat detection, and incident response, all while keeping up with the latest ransomware tactics.
Upskilling IT staff ensures organizations remain agile and resilient in the face of these challenges. With specialized training, IT professionals can better identify vulnerabilities, deploy cutting-edge security tools, and develop stronger disaster recovery plans tailored to modern threats.
Furthermore, investing in the professional development of IT teams can lead to more proactive security measures. Rather than relying solely on automated tools or outsourced solutions, highly skilled IT personnel are capable of analyzing potential risks in real time and responding quickly to any breaches or signs of ransomware infiltration.
Their expertise becomes especially critical in cases where rapid response is the difference between containing a breach and experiencing widespread system compromise.
The Rise of Generative AI Sparks Increased Fear of Ransomware Attacks

The emergence of generative AI has significantly heightened concerns about ransomware in 2024, with 66.9% of respondents reporting that the availability of this technology has made them more fearful of becoming a ransomware target.
Generative AI, which can create highly realistic and convincing content, is being increasingly leveraged by cybercriminals to craft more sophisticated phishing schemes and execute complex social engineering attacks.
This technology allows attackers to automate and scale their efforts with unprecedented precision. AI-generated phishing emails, for example, can be tailored to mimic the tone, style, and even personal details of legitimate communications, making them far more difficult for users to detect.
As a result, traditional defenses that rely on identifying obvious signs of malicious activity, such as poorly worded emails or unfamiliar addresses, are becoming less effective. Phishing schemes powered by AI can deceive even the most vigilant employees, increasing the likelihood of a successful ransomware deployment.
Additionally, generative AI can be used to exploit system vulnerabilities more effectively, creating malware that adapts to its environment and circumvents standard security protocols. This adaptability presents a growing challenge for organizations, as it requires them to invest in more advanced, AI-driven security solutions to keep pace with the evolving threat landscape.
Awareness of Microsoft 365 Vulnerability to Ransomware Is Improving
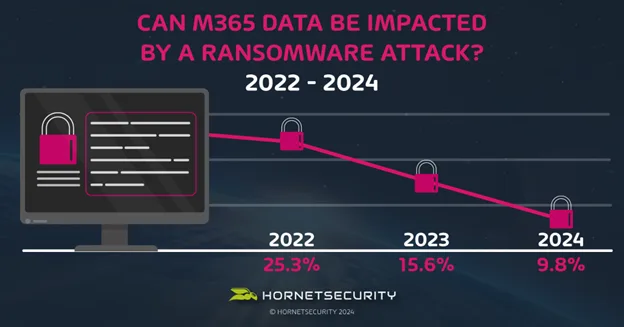
In 2024, awareness of Microsoft 365’s vulnerability to ransomware has continued to improve, with only 9.8% of respondents stating that they didn’t know or didn’t think Microsoft 365 data could be affected by a ransomware attack.
This marks a significant improvement from 2023, when 15.6% of respondents were unaware of the risk, and an even more substantial leap from 2022 when 25.3% of respondents held the same view. This steady decline in unawareness highlights the growing effectiveness of educational efforts aimed at emphasizing the potential threat ransomware poses to cloud-based services like Microsoft 365.
The progression over the years demonstrates a positive trend in cybersecurity awareness, as more organizations recognize that cloud environments are not immune to ransomware.
The initial lack of understanding in 2022 reflects the early stages of cloud adoption for many businesses, where the focus was more on the convenience and functionality of platforms like Microsoft 365 rather than on their security vulnerabilities.
However, as ransomware attacks targeting cloud services have become more prominent, businesses have become increasingly aware of the need to protect their data within these systems.
By 2023, educational campaigns and growing public awareness had led to a significant reduction in the number of organizations underestimating the risks to Microsoft 365, bringing the figure down to 15.6%. By 2024, this figure had dropped further to 9.8%, demonstrating that organizations are becoming more proactive in implementing security measures to safeguard their cloud-based environments.
54.6% of Organizations Have Purchased Ransomware Insurance Policies

The adoption of ransomware insurance continues to grow significantly, with 54.6% of organizations surveyed in 2024 reporting that they have purchased a policy. This represents a notable increase from previous years, as 37.9% of respondents reported having ransomware insurance in 2022, rising to 42.2% in 2023.
The steady year-over-year growth highlights a shift in how businesses are approaching ransomware risk, increasingly recognizing the importance of transferring some of the financial burden through insurance coverage.
The sharp rise in ransomware insurance purchases reflects the growing realization that ransomware attacks can have devastating financial consequences. Organizations are facing not only ransom demands but also recovery costs, potential regulatory fines, and the impact of operational downtime.
As ransomware attacks have become more sophisticated and difficult to recover from, more companies are turning to insurance as a safeguard against these threats.
In many cases, ransomware insurance offers coverage for a wide range of attack-related costs, including ransom payments, legal fees, forensic investigations, and public relations efforts. With the growing complexity of ransomware tactics, such as double extortion schemes where attackers both encrypt and steal data, the financial risks have increased.
The rising uptake of insurance policies shows that businesses are actively seeking ways to mitigate these risks and ensure business continuity in the event of an attack.
However, purchasing ransomware insurance does not mean organizations can lower their defenses. Insurers are increasingly requiring businesses to meet stringent security standards before offering coverage, including robust backup solutions, employee training, and advanced cybersecurity protocols.
This trend is likely to encourage businesses to strengthen their cybersecurity measures even further, as those without proper safeguards may face higher premiums or be denied coverage altogether.
About the 2024 Hornetsecurity Ransomware Attacks Survey Respondents
Our 2024 ransomware attacks survey offers valuable insights into the demographics of the 502 IT professionals who participated. A significant portion of respondents, 52.2%, have accumulated over 21 years of experience in the IT industry, reflecting the presence of highly seasoned professionals.
In addition, 18.5% have 16-20 years of experience, while newer entrants to the industry (those with 1-5 years of experience) made up 7% of respondents. This spread of experience levels provides a comprehensive perspective on how different levels of expertise influence approaches to ransomware prevention and recovery.

In terms of job roles, 36.1% of respondents identified as Managed Service Providers (MSPs), a common role in the IT space responsible for managing external client IT services. System administrators made up 21.1%, while 13.7% were business owners who handle IT themselves. C-suite executives such as CIOs, CTOs, and CISOs accounted for 10.6%, showcasing a diverse range of participants with varying degrees of responsibility over IT decisions.
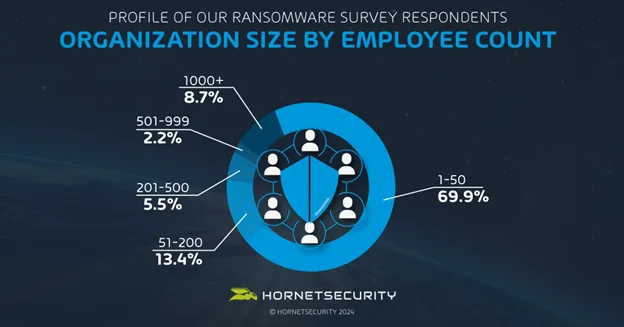
Regarding organizational size, the majority of participants (69.9%) work in small businesses with 1-50 employees. Mid-sized organizations with 51-200 employees represented 13.4%, while larger enterprises (1,000+ employees) accounted for 8.7% of respondents. This diversity in company size offers insights into how different-sized businesses are approaching ransomware threats.
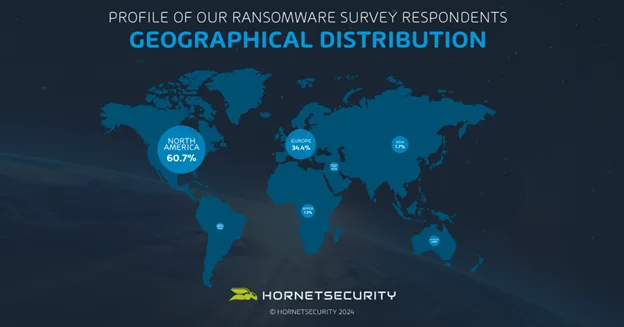
The geographical distribution of respondents further enriches the survey. The majority, 60.7%, are based in North America, followed by 34.4% in Europe. Other regions, including Asia, Africa, Australia, the Middle East, and South America, also contributed to the survey, though in smaller numbers. This international spread reflects the global nature of ransomware threats and how organizations across various regions are dealing with them.
Industries represented in the survey were dominated by Software and IT (49.9%), followed by other sectors such as Financial Services (5.9%), Engineering/Manufacturing (4.9%), Healthcare (4.9%), and Government/Public Administration (3.6%). The diversity of industries allows for a broader understanding of how different sectors are affected by and responding to ransomware attacks.

