

Customer Fail Story: Fail With Phishing Simulations – Or Celebrate Successes
Cybercrime has evolved: Through smuggled ransomware and following public shaming, companies are blackmailed to pay ransom or to hand over sensitive information. For many companies it is therefore more important than ever to increase security awareness. However, a lot of things can go wrong.
In order to be best prepared for the activities of cyber criminals, you as an IT security officer need one thing over all: independent and responsible colleagues who approach attempted attacks with a vigilant eye and take the topic of IT security seriously. However, the effort to ensure such awareness can be immense. Phishing simulations have established themselves as a cost-effective and powerful tool for this purpose since the early 2010s.
We see the positive effect every day: through phishing simulations – if well done – employees become aware of their own responsibility regarding to information security and instinctively act correctly in critical situations.
But phishing simulations can also go wrong, they can even have a negative effect on the security awareness of employees – we as a cyber security company have already noticed this at one time or another. The reasons for this can be found in unfavourable decisions made by the companies, for example, regarding to communication with employees or for the technical preparation of the measure.
We have summarized our experiences with the companies and everything that can go wrong during a phishing test for you here in the customer fail story of the fictitious Spigrin AG, its CEO, Udo Simmer, and its information security officer, Phillip Segert. Would you have considered all aspects for a successful phishing simulation?
Phishing simulation at Spigrin AG – a short story of failure
‘Spigrin AG is a leading company in the electrical and optical connection technology. It is our innovations that make us competitive in the world market. Working with us means working for an international company that develops these innovative products with committed and goal-oriented employees.’
Security has always been an important corporate goal for Udo Simmer, managing director of Spigrin AG. Together with his security officer, Phillip Segert, he has invested a lot of time and money in technical security measures in the “NextGen” category. They confidently say: ‘Our IT is secure.’
But now Phillip Segert is alarmed: Phishing mails from some business partners have managed to get past the spam filter. Numerous employees have become victims of perfidious attacks as a result. An expert advises Phillip to test the security awareness of his colleagues – after all, it would be dramatic if so much effort had been put into IT security systems and then the employees were used as a gateway for cyber attacks.
Phillip understands that. Together with his boss Udo, he decides to test how well their almost 700 employees in the various locations react to phishing e-mails.
Phillip is a handyman. A small tool is quickly programmed that sends fake phishing mails with high performance and counts clicks accordingly. He sends out his first phishing e-mail, …but nobody clicks. “‘This can’t be…?’ Phillip obviously forgot to adjust the e-mail filter – his mail was not designed to overcome the SPAM filter and got stuck.
‘Damn it,’ Phillip says, ‘I’ll just get a contractor who can design something like that.’ He installs and configures a free tool and sets up the whitelisting according to the instructions. During the preparation time, however, it is noticeable: real-world attacks are starting to pile up. Phillips’ settings have made it easier for real attackers to get through the filters. Phillip quickly reconfigures the whitelisting so that it only points to the sending IP address, bringing the security systems back to the same level of effectiveness as before the whitelisting.
Note: A whitelisting should always refer exclusively to the IP address of the sending e-mail server.
Now Phillip would like to really challenge his colleagues. He is organizing a competition in the IT department for the “best” phishing e-mail. The winner is an e-mail on behalf of the management with a link to the upcoming moving out. After a click, the employees are shown an error message – after all, nobody should notice and get around. Phillip sends the e-mail to all employees: 70% – that is, over 450 employees – fall for the e-mail.
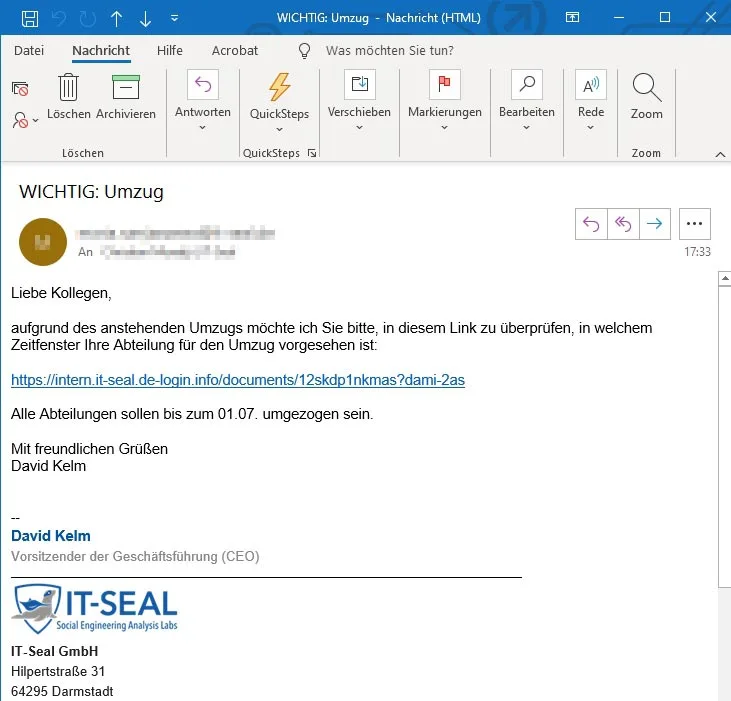
Phillip presents the result to his boss. He was shocked: ‘This can’t be true! I thought we were secure?!’ Phillip tries to calm him down: ‘That was the best phishing email we had. Most real attacks are much worse.’ But how are they supposed to classify such a result now?
Udo suggests to repeat the test with a more realistic phishing e-mail. In the second round a realistic attack is sent with an allegedly overflowing mailbox.
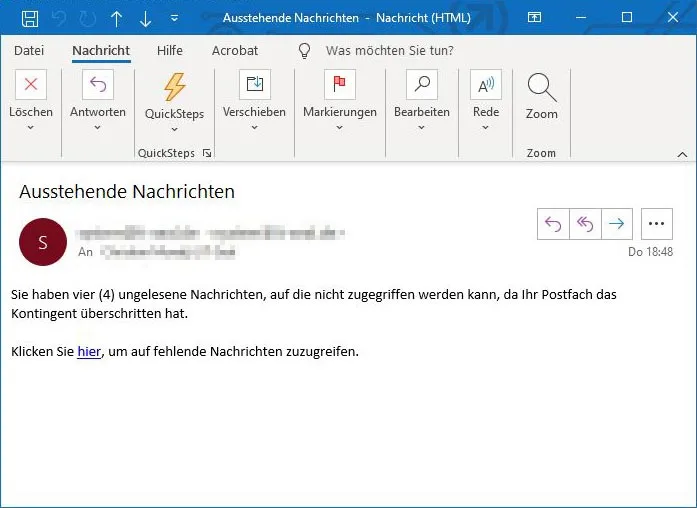
This time almost 20% of the employees click. Udo is now a bit more calm, but Phillip points out: ‘I have noticed that the colleagues have warned each other – in case of a real attack we are surely worse off.’
Remember: “Corridor radio” is good! In a secure company it is a powerful tool for employees to warn and support each other. However, a phishing simulation that only uses individual e-mails can quickly fail because of it. Sending many different phishing e-mails is more realistic and more meaningful. In this way, the effect of corridor radio on the results of the phishing simulation can be minimized.
Udo is completely unsettled: ‘How is the current situation?’ Even Phillip is confused and doesn’t know how to interpret the results. Even the first e-mail could be copied by an attacker with little effort, since the moving out was announced in advance and all information was available in the news and on the website. In addition, a real phishing e-mail that he found in his mailbox today has confused him: It came in response to one of his mails directly from a business partner! Thanks to his trained eye was he able to expose the e-mail. ‘The attacks just keep getting better and better!’ points out Phillip.
Keep in mind: A phishing simulation should never consist of individual e-mails. Just because an e-mail has a perfect subject and timing, does not mean that you have a huge problem right away. Attacks should be realistically simulated and contain information from freely available sources that real cyber criminals would use for their phishing emails (OSINT). This is the only way to get a real impression of the situation and to prepare the employees for the attacks.
Phillip has now diversified the phishing mails and formulated them realistically. He feels his simulation is now well prepared for the challenges. Tamara, the head of IT support, knocks on his door: ‘Your phishing attacks are currently generating a huge amount of work for us in IT support – how are we supposed to deal with all the messages?’ Phillip hadn’t thought about this: He hadn’t given the employees or IT support any instructions on how to proceed in case of a detected phishing e-mail.
Keep in mind: IT support must always be informed in advance about a phishing simulation – they need guidance and support on how to deal with questions from employees.
Well-established and functioning reporting processes are important to give employees confidence in dealing with phishing emails. A report button, e.g. as an Outlook plug-in, can be helpful here.
Meanwhile Phillip and Udo are receiving more and more inquiries and complaints: Due to the lack of coordination in IT support, many employees have casually noticed that they are being audited by their company. They are annoyed and feel monitored – mistrust is spreading throughout the company.
A phishing simulation behind the back of the employees makes them feel insecure and creates mistrust – therefore, such a measure should always be announced in advance. It has proven to be a good idea to wait 2 weeks after the announcement before sending the first e-mail.
But what if the employees then click out of curiosity? To prevent employees from clicking, the announcement should already contain a phishing e-mail with a link and/or attachment that the employees can try out. This way, they can satisfy their curiosity and click through without any danger if an explanation page is placed behind it. They can then react correctly to a fake e-mail in their inbox.
Phillip and Udo decide to officially inform all employees about the phishing test. However, their announcement that a click on a phishing e-mail is being recorded causes great uncertainty. The employees now fear making mistakes – they would prefer not to open any e-mails at all.
Keep in mind: To celebrate successes advise your employees at the right moment (preferably at the “most teachable moment”) for the possibilities to improve. Use positive feedback to increase the identification and learning success of the measure, e.g. when the employee reports a suspicious e-mail to IT support. This increases the good feeling of being able to contribute something to the information security.
Guido Gans, Udo’s secretary, is angry. He received the first phishing e-mail about the company’s moving out, sent in Udo’s name. Actually, he was in charge of planning the move and now thinks that he was passed over by his boss. The atmosphere between them was already tense anyway and was further poisoned by this.
Keep in mind: Some employees have a problem with e-mails being sent in their name during the phishing simulation. Please inform the relevant employees in advance about this and give them the opportunity to reject to the use of their name.
Now the works council is getting involved. He noticted the phishing simulation and is threatening with consequences. After all, the IT department could see the behaviour of each individual person and use this information to monitor their behaviour and performance. The works council enforces that the data already recorded should be deleted and the results should not be used further.
Keep in mind: Get the works or staff council on board as early as possible and consider any questions that arise. Consent or a collective agreement is usually not legally required, but it can significantly ease the situation. The results of the phishing simulation should also be evaluated on a group basis – this protects the individual employee on the one hand, but on the other hand allows the results to be meaningful.
Conclusion: Better employee-friendly
Phillip and Udo had to learn the hard way when planning and carrying out their phishing test. But the experience has shaped them. But you can already foresee this now: The results of the simulation were critical. Phishing emails will still be a problem for the near future.
To best prepare employees and gain an accurate overview of security awareness within the company, Phillip turns to experts who know the typical pitfalls and can best advise him on implementing a phishing simulation.
Just like IT-Seal. What Phillip particularly appreciates about their solutions is the uncomplicated implementation as well as preparatory documents for communication with the works council and employees. Furthermore, the realistic attacks based on OSINT are important to him – only in this way can he prepare his employees and colleagues for the ever-increasing danger of perfidious phishing attacks.
We agree with him: Happy, responsible employees are the best protection against cyber attacks. Our employees of our customers no longer take the issue lightly, but seriously.
