

From Passwords to Passkeys: Security Benefits and Implementation Tips
Introduction
Passwords. We all hate them. If only there was a technology that could take away the pain and angst of having to create, remember and store passwords. Importantly, it would still need to protect us from the nasty denizens that lurk all over the Internet. This technology needs to be scalable, user-friendly, and backed by industry stalwarts such as Intel, Amazon and Microsoft…. Well, it has already been developed, it’s here and you’ve probably already seen glimpses of it in Microsoft Entra.
Microsoft has made great strides and invested heavily in improving authentication mechanisms in Entra with support for FIDO-based security keys available since 2018. In 2021, Microsoft introduced password-less signing in using a security key for commercial customers too. That was truly a seminal moment that revolutionized the way we think about passwords and offered a tantalizing glimpse into a future without them. Back then, the effective security that passwords provided was already on a downward trend due to the increasing length and complexity needed to keep up with thwarting attacks, and the frustrating experience of password management. Although physical security keys have been around for about 10 years as a form of MFA, they were mainly used by hardcore security enthusiasts.
We’ve seen an increase recently in internet services and applications supporting the WebAuthN standard needed for passkeys, and thus the proliferation of using passkeys with services such as banks and online stores. Based on data available from BuiltWith, they reported an exponential rise in the use of WebAuthN, now available on close to 1.5 million websites, a strong indication that the uptake and use of passkeys has entered the mainstream.
Benefits of Passkeys in Microsoft Entra
Despite many attempts to breathe life into passwords, they are inherently flawed for many reasons, one of which is the inverse relationship between their complexity and usability. Put simply, the more complex we choose our passwords to be, the less useable, friendly, and practical they become. Show of hands please, who amongst us hasn’t written down and stored their password at least once on a notepad? Another fundamental recommendation is to use unique passwords for every site, so that when a low security site is compromised, criminals can’t just take the leaked usernames and passwords and use them to sign in on other sites.
However, studies also show that reuse of passwords across sites by users is incredibly common, again highlighting the risks inherent in bad password hygiene. Attackers rely on poor password management and according to Finance Online, 81% of company data breaches are caused by poor passwords. This is why many security experts now recommend that business owners, employees, and individuals move away from passwords and toward passkeys.
Here are some sobering password management statistics reported by Finance Online:

Passkeys are about to make the life of criminals a whole lot more difficult by eliminating the need for passwords entirely! What’s more, passkeys are phishing resistant and use public key cryptography to store the private key on your device, while the public key is stored by the service provider.
Phishing resistant for passkeys and FIDO2 hardware keys refers to the fact that the login credentials are only released when the right website is accessed. In a traditional phishing attack, criminals trick a user (via a phishing email or other type of social engineering) to visit a site that looks like the legitimate sign-in page for a service such as Microsoft 365, but is actually fake and under the control of the attackers. This type of attack won’t work for passkeys, because even if the user doesn’t spot the spelling error in the URL, the passkey will know that this isn’t the correct site, and thus refuse to release the credential.
When biometric access to laptops and mobile phones were introduced, this was seen as something quite unique. Now, though, it has become a ubiquitous experience, long embraced for the delightful convenient experience of swiping our fingers, touching a surface, or simply showing our face to access personal and corporate devices.
All these extra conveniences ultimately provide a better user experience and enhanced protection, such as eliminating password reuse, as every passkey is unique. Thus, the risk of re-using the same, and often weak, passwords for multiple services is negated. Another advantage of a passkey is the removal of the “password fatigue” experienced from generating and managing complex passwords. In fact, talking about the user experience, passkeys provide a much faster authentication experience when using biometric authentication, just smile or swipe!
I mentioned earlier that Microsoft have had skin in this game since 2018, and since then, have worked on different ways that passkeys can be baked into Entra. The increased availability of internet services which support WebAuthn mentioned before means that users can use Windows Hello’s biometric technology to log into these services using a passkey instead of a website. This isn’t limited to just Windows Hello, but also for the other platforms that support biometric authentication, like iOS, MacOS and Android. This flexibility provides a consistent and secure authentication method across entire Entra ecosystem, irrespective of the device or operating system.
Implementation Strategies for Entra ID Passkeys
That old saying “if you fail to plan, you plan to fail” is core to so many projects or initiatives and implementing passkeys in Entra ID is no different. There are key considerations and requirements that must first be checked before you can really kick into this. Many of which will depend on elements such as the organization’s overall information security maturity level, and where they are at on their FIDO/FIDO2 journey.
Foundational to this is having MFA enabled for all users, that’s number one. A gotcha that you also must take into consideration is the operating system used by mobile users and the software installed and used for authentication, before enabling passkeys. While Android allows multiple password software applications (e.g. 1Password, Microsoft Authenticator) to co-exist when using passkeys, Apple only permits a single application, which in this case can only be Microsoft Authenticator. Important to note here is that if users will be using their laptop to sign into a service that supports passkeys, Bluetooth needs to be enabled on both the mobile device and the laptop.
Next, you’ll need to decide whether you want to go down the “device-bound” passkey or a “syncable passkey” path. Device-bound passkeys are generally how passkeys have been used to date, in which they are literally bound to the device on which they are created. For example, a physical key like a Yubikey, or the laptop/mobile device on which you store the passkey. “Syncable” passkeys on the other hand, are synchronized across multiple devices using cloud, provide better usability, manageability, and deployment benefits due to their flexibility. It’s a trade-off of security versus convenience.
While it’s early days for passkey adoption in businesses, for any organization that needs high security, syncable passkeys stored in consumer accounts such as Apple, Google or Microsoft’s cloud aren’t going to be acceptable as you’ve got limited control over them, especially when someone leaves the enterprise. All this magic happens in the “Authentication Methods” blade in the Microsoft Entra admin Center. The first step is to select the “FIDO2 security key” policy, select which users will be included in this policy, and include the AAGUID for each supported passkey, both physical security keys as well as software-based ones like Microsoft Authenticator.
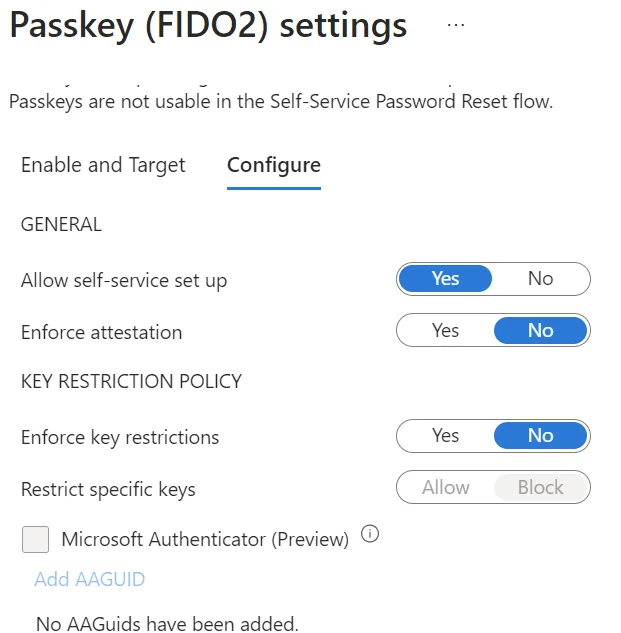
On the user side, this now becomes a new option for users to select as their authentication method:
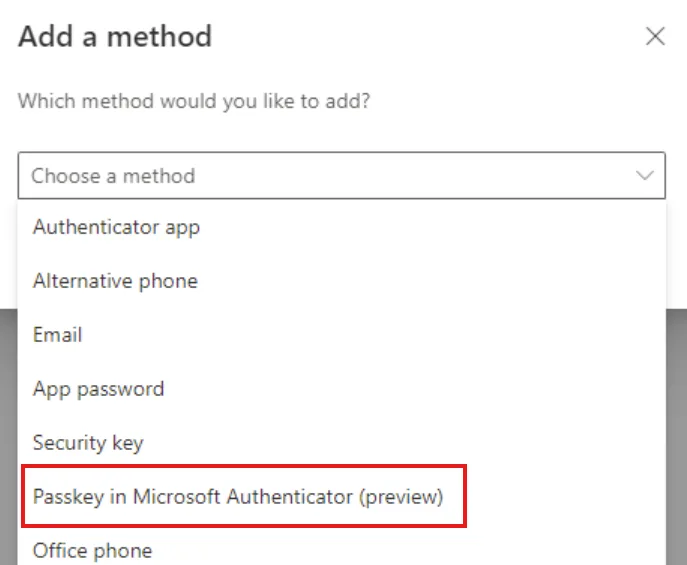
While there may be some resistance from users to making this change, the ease and use of this new authentication method really should just sell itself. As with any change such as this, running a pilot with a select group of users is strongly recommended. Especially if you get users from different business groups on board, you’ll have your passkey champions who, once they ‘get it’, will be singing the high praises for passkeys! It’s not often a technology that increases security, is also more convenient for users, but passkeys really are a better solution for everyone.
Enhancing Security with Entra Passkeys
Phishing attacks continue to dominate the threat landscape at a relentless pace with often devastating results, as evidenced by the finding in the Hornet Security Cyber Security Report 2024: An In-depth Analysis of the Microsoft 365 Threat Landscape, which found that they account for more than 43% of all email-based attacks!
Passkeys are by design resistant to phishing attempts, and therefore ideally suited to bolster the security capabilities already offered through the support for FIDO2 authentication in Microsoft Entra. The recent announcement by Microsoft that Entra now supports device-bound keys in Microsoft Authenticator for iOS (minimum version 17.0) and Android (minimum version 14) and will appeal to organizations with more stringent security requirements.
Despite their secure design, Passkeys are not impervious to being compromised, and therefore, additional controls may be necessary for the specific attack vectors. For example, if a poorly protected mobile device with a passkey used to log into an online store is stolen, and full access is obtained, there’s little you can do to prevent the thief from logging into that store and making a purchase. As the adoption of passkeys rises, the focus shifts to optimizing how we secure the devices on which they are stored. In the case of mobile devices, there are a number of methods already available which could prevent access to the passkey, like using a PIN or biometric access to the device as well as access to the authentication software.
Laptops with a TPM (Trusted Platform Module) chips have been available for quite a long time, which means that obtaining the passkey from one of these requires serious determination and skills. By contrast, if you happen to be using an older laptop without a TPM chip, it’s vital to add secure access to the software in which the passkey is stored.
To properly protect your Microsoft 365 environment, use Hornetsecurity’s one-of-a-kind services:
- 365 Total Protection
- 365 Total Backup
- 365 Permission Manager
- 365 Total Protection Compliance & Awareness
- 365 Total Protection Enterprise Backup
To keep up with the latest Microsoft 365 articles and practices, visit our Hornetsecurity blog now.
Conclusion
Passkeys provide so many benefits to the entire security ecosystem that it’s difficult to squeeze them all into a few sentences. Their simplicity, the speed at which they can be used, and their phishing-resistant design make them an exceptionally attractive option for virtually everyone. This is particularly true for Microsoft Entra, where organizations need to start planning for their adoption, ensuring their environments are adequately prepared and using the communication channels and methods to ensure rapid and widespread adoption.
There’s a say that goes: “Security isn’t a diet, it’s a lifestyle.” Using passkeys instead of passwords is not a reason to pay any less attention and focus to constantly monitoring and alert for anomalous access to your environments and your devices. Ensuring all your devices are running the latest stable updates is important as it’s ever to been to mitigate against potential vulnerabilities.
As for any security awareness initiatives, the message needs to extend beyond users’ corporate devices to how they manage their personal security practices. By ensuring users are on the same journey and have access to the resources needed to use passkeys, the time investment to implement passkeys will realize significant operational efficiencies once never thought possible.
There are a lot of moving parts to Passkeys, especially in the world of Entra and I highly encourage you to check out this recent Hornet Security Podcast hosted by Andy Syrewicze with guest Jan Bakker where they do a deep dive into Passkeys, particularly in the context and world of Microsoft Entra.
FAQ
Passkeys are a modern authentication method that replaces traditional passwords with secure cryptographic keys. They improve security by eliminating password-related vulnerabilities such as phishing and password reuse, providing a more secure and user-friendly authentication experience.
Microsoft Entra facilitates passkey adoption by offering seamless integration with existing systems, providing tools to manage and deploy passkeys across your organization, and ensuring compatibility with various devices and platforms for a smooth transition to passwordless authentication.
Passkeys offer several benefits over traditional passwords, including enhanced security against phishing attacks, reduced risk of password theft, and a more convenient user experience. They also simplify the authentication process by removing the need to remember and manage multiple passwords.

