

Email Threat Review June 2021
Summary
In this installment of our monthly email threat review, we present an overview of the email-based threats observed in June 2021 and compare them to the previous month’s threats.
The report provides insights into:
- Unwanted emails by category
- File types used in attacks
- Industry Email Threat Index
- Attack techniques
- Impersonated company brands and organizations
- Highlighted threat email campaigns
- Ransomleaks
- Special events
Unwanted emails by category
The following table shows the distribution of unwanted emails by category.
| Email category | % |
| Rejected | 84.05 |
| Spam | 11.57 |
| Threat | 3.41 |
| AdvThreat | 0.94 |
| Content | 0.03 |
The following time histogram shows the email volume per category per day.

Around 2021-06-13, we registered a large spike in rejected emails. Based on a significant text overlap, we can attribute this to a German-language sextortion scam campaign we observed in previous months.
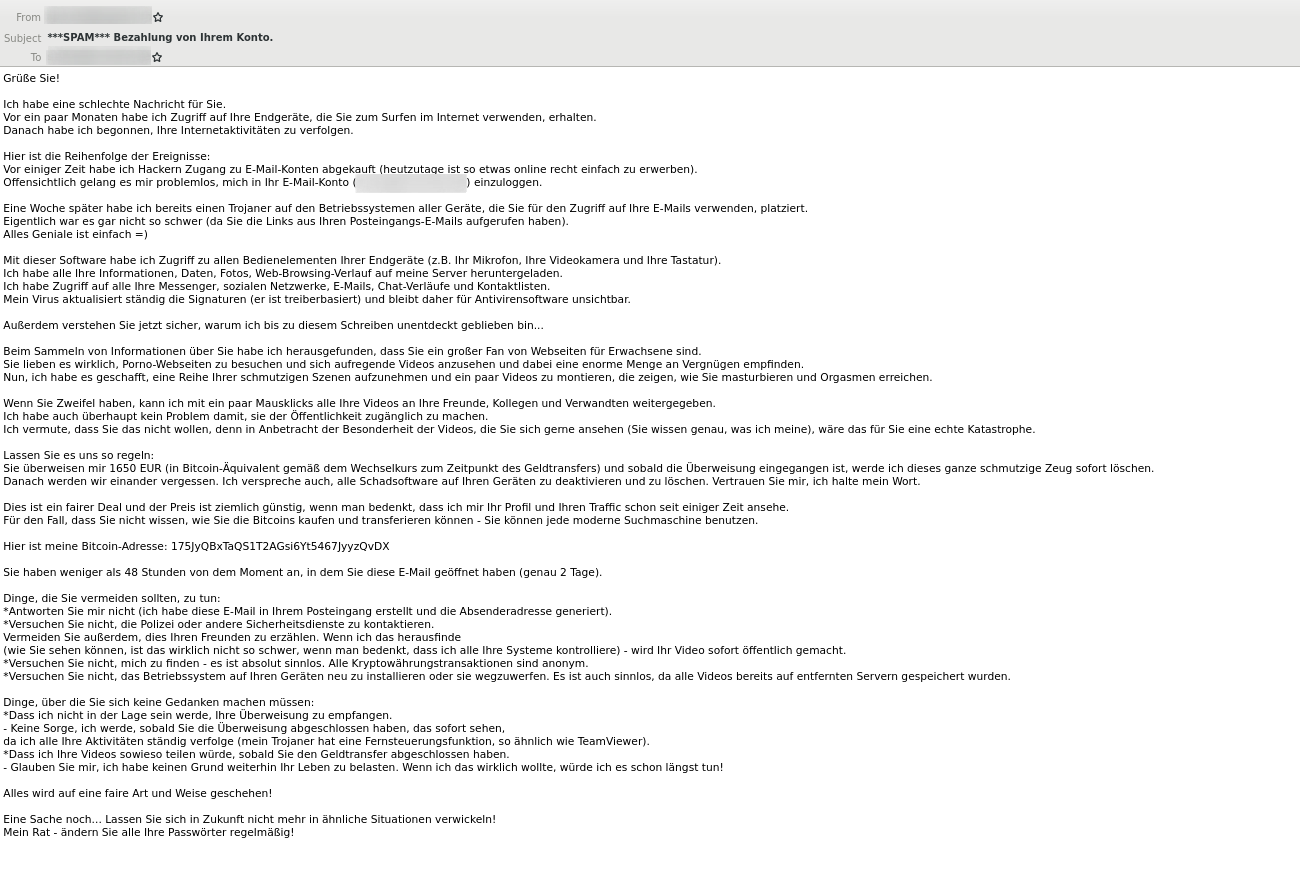
As of writing, the campaign netted the criminals US$ 4,351 in BTC. Therefore the campaign is most likely profitable and thus will most likely return next month.
Methodology
The listed email categories correspond to the email categories listed in the Email Live Tracking of Hornetsecurity’s Control Panel. So our users are already familiar with them. For others, the categories are:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Content | These emails have an invalid attachment. The administrators define in the Content Control module which attachments are invalid. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File types used in attacks
The following table shows the distribution of file types used in attacks.
| File type (used in malicious emails) | % |
| Archive | 29.0 |
| HTML | 16.9 |
| 15.0 | |
| Other | 13.0 |
| Executable | 11.0 |
| Excel | 6.9 |
| Disk image files | 4.4 |
| Word | 3.6 |
| Powerpoint | 0.1 |
| 0.0 | |
| Script file | 0.0 |
| LNK file | 0.0 |
The following time histogram shows the email volume per file type used in attacks per 7 days.

Between 2021-06-07 and 2021-06-10, Hornetsecurity detected a rise in executable email attachments. We can attribute this to a malspam campaign containing a Nanocore RAT executable dropping Agent Tesla in an archive attached to the email.
Industry Email Threat Index
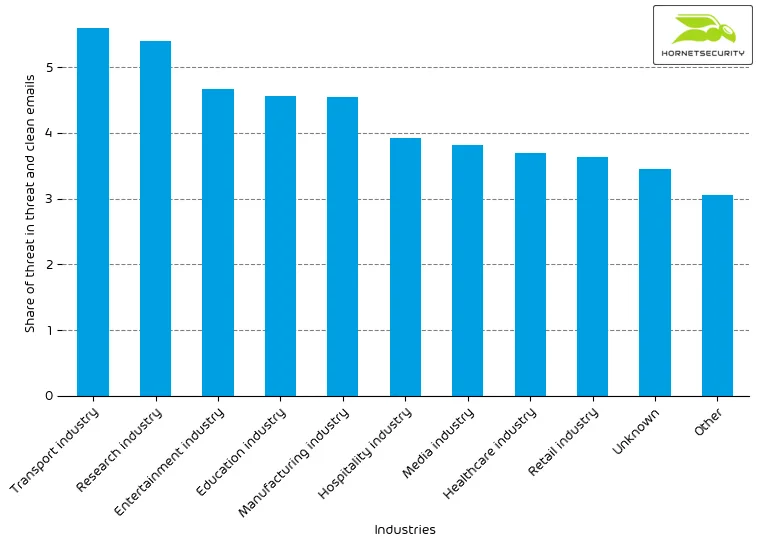
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to clean emails received (in median) by each industry.
| Industries | Share of threat in threat and clean emails |
| Transport industry | 5.6 |
| Research industry | 5.4 |
| Entertainment industry | 4.7 |
| Education industry | 4.6 |
| Manufacturing industry | 4.5 |
| Hospitality industry | 3.9 |
| Media industry | 3.8 |
| Healthcare industry | 3.7 |
| Retail industry | 3.6 |
| Unknown | 3.4 |
The following bar chart visualizes the email-based threat posed to each industry.
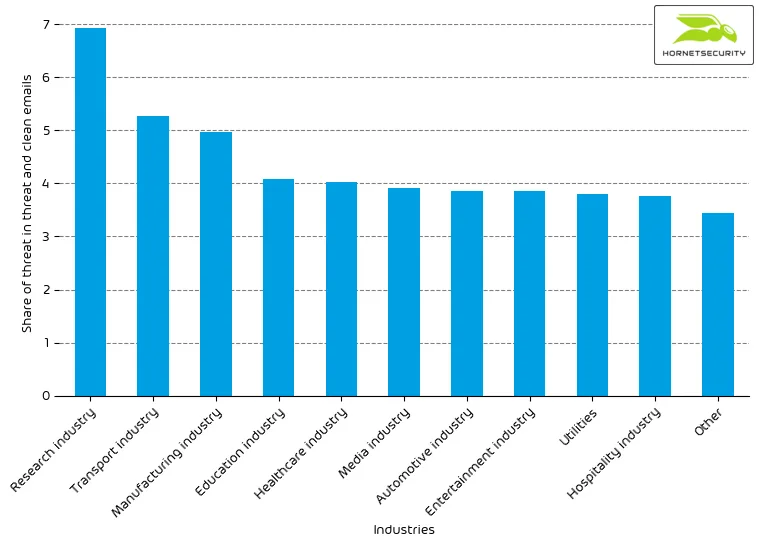
For comparison last month’s email-based threat index bar chart:
Methodology
Different (sized) organizations receive a different absolute number of emails. Thus, we calculated the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values overall organizations within the same industry to form the industry’s final threat score.
Attack techniques
The following table shows the attack technique used in attacks.
| Attack technique | % |
| Other | 50.8 |
| Phishing | 26.0 |
| URL | 9.4 |
| Extortion | 4.3 |
| Executable in archive/disk-image | 4.0 |
| Advance-fee scam | 2.4 |
| Impersonation | 2.2 |
| Maldoc | 1.0 |
| LNK | 0.0 |
The following time histogram shows the email volume per attack technique used per hour.
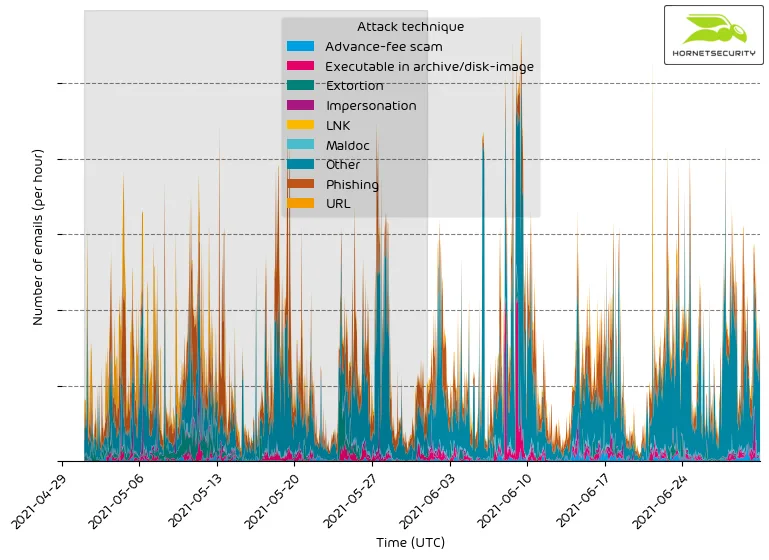
Between 2021-06-07 and 2021-06-10, there were elevated levels of executables in archives. This is due to the campaign, as mentioned earlier, delivering Nanocore RAT as executable in an archive file (e.g., “.7z”, “.Zip”).
Impersonated company brands and organizations
The following table shows which company brands our systems detected most in impersonation attacks.
| Impersonated brand or organization | % |
| DocuSign | 19.8 |
| Other | 15.9 |
| Deutsche Post / DHL | 15.7 |
| Amazon | 11.6 |
| PayPal | 8.6 |
| 5.9 | |
| Microsoft | 2.5 |
| O2 | 2.1 |
| HSBC | 2.0 |
| Santander | 1.9 |
The following time histogram shows the email volume for company brands detected in impersonation attacks per hour.
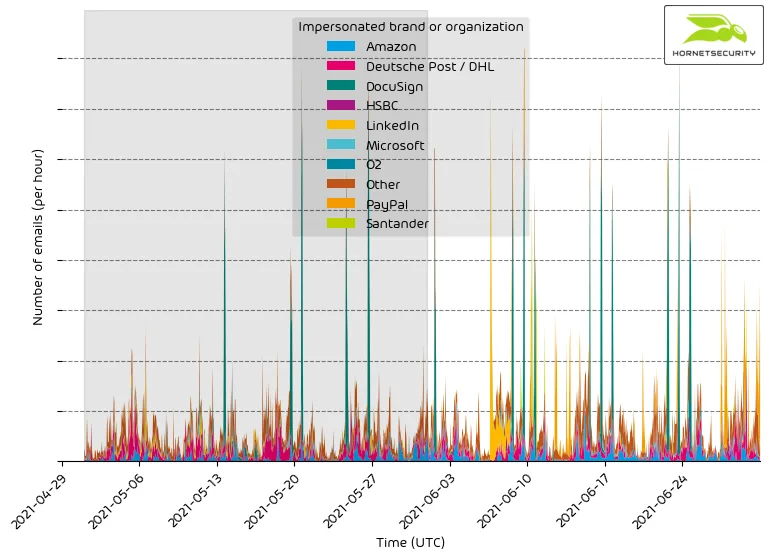
It’s a constant stream of phishing and other attacks impersonating big brands to entice recipients to open the emails.
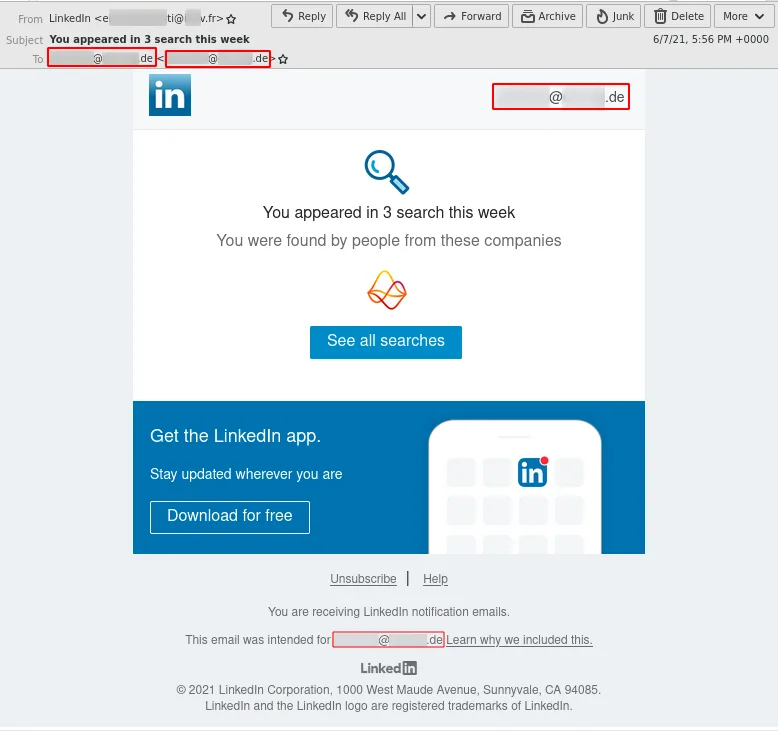
Starting on 2021-06-07, we observed a large-scale phishing campaign impersonating LinkedIn.
Highlighted threat email campaigns
In this section, we want to highlight some malspam campaigns of prominent, well-known threat actors.
The following time histogram shows the email volume for highlighted threat email campaigns per hour.
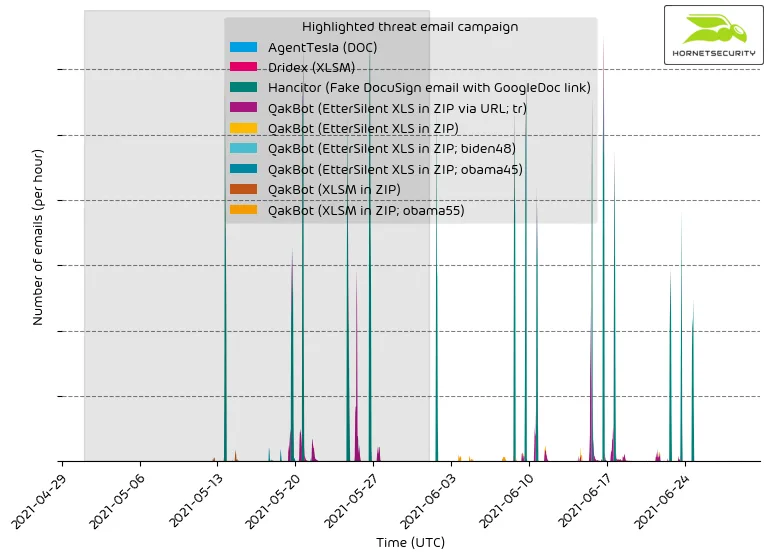
Please be advised that this does not contain all campaigns. The ranking, as well as volume figures, should therefore not be taken as a global ranking. We strive to expand this section of our reporting in the future.
While the Hancitor campaign overshadows all other campaigns w.r.t. to volume per hour, we can see that the QakBot malspam of botnet group tr we saw emerging last month has established itself as a reoccurring campaign. Such endless running campaigns are usually only observed by very low-quality malspam campaigns or by more sophisticated spammers such as the Emotet botnet.
Methodology
Hornetsecurity observes thousands of different threat email campaigns of varying threat actors ranging from very unsophisticated low-effort attacks to highly complex obfuscated attack schemes. Our highlighting includes only major sophisticated threat email campaigns.
Ransomleaks
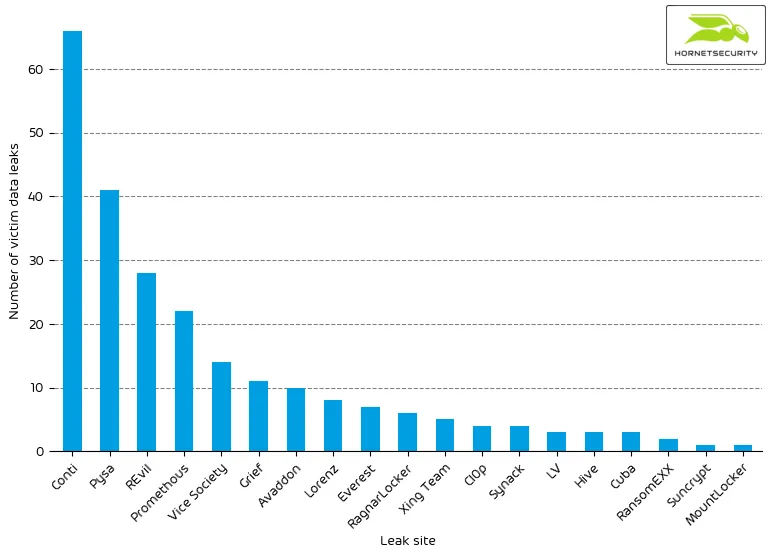
Sophisticated threat actors exfiltrate confidential data from their victim’s networks. Exfiltrated data is then used as a method to pressure their victims into paying a ransom. If the victim does not pay the ransom, the confidential data is being published by the threat actors on so-called leak sites that are often only reachable through the TOR network. This trend continued in June. We observed the following number of leaks on ransomware leak sites:
| Leak site | Number of victim data leaks |
| Conti | 66 |
| Pysa | 41 |
| REvil | 28 |
| Promethous | 22 |
| Vice Society | 14 |
| Grief | 11 |
| Avaddon | 10 |
| Lorenz | 8 |
| Everest | 7 |
| RagnarLocker | 6 |
| Xing Team | 5 |
| Cl0p | 4 |
| Synack | 4 |
| LV | 3 |
| Hive | 3 |
| Cuba | 3 |
| RansomEXX | 2 |
| Suncrypt | 1 |
| MountLocker | 1 |
The following bar chart visualizes the number of victim data leaks per leak site.
We added data collection for the following ransomware leak sites:
The leak site of the LV ransomware:
The LV ransomware re-purposes code of the REvil ransomware. The operators don’t seem to have access to REvil’s source code but have adapted an existing REvil ransomware binary by modifying strings in its binary code.1
The leak site of the Hive ransomware:
The Hive ransomware seems to be a new ransomware strain.
The leak site of the Vice Society ransomware:
Experts in the field of ransomware have concluded that Vice Society ransomware is identical to the HelloKitty ransomware.2
Special events
Because there have been several noteworthy events concerning the broader email threat landscape, we summarized them in this special section.
Avaddon ransomware releases decryption keys
On 2021-06-11, Avaddon released keys for over 2,934 victims.3 The Avaddon leak site listed only 186 victims that refused to pay the ransom. This means that Avaddon had 15-times more victims than published on their leak site. Under the assumption that the other ransomware operations have a similar ratio, the number of ransomware victims could be obtained by multiplying the number of victims on leak sites by 15.
Clop ransomware arrests
On 2021-06-16, the National Police of Ukraine announced they had arrested individuals suspected to have infected companies with the Clop ransomware.4 However, because the Clop ransomware operation continued running without interruption, it is assumed that the individuals arrested were only unimportant figures in the Clop ransomware operation, such as money mules, or sub-contractors.
We previously reported how the Clop ransomware is spread via malicious emails.
Gozi arrested
On 2021-06-29, the Office of the Attorney General of the Nation of Columbia has announced the arrest of one individual5 wanted by the U.S. since 20136 in connection with the Gozi malware. The individual operated a bulletproof host that helped cybercriminals distribute the Gozi malware and commit other cybercrimes, such as distributing malware including the Zeus Trojan and the SpyEye Trojan, initiating and executing distributed denial of service (DDoS) attacks, and transmitting spam.
TrickBot developer arrested
On 2021-06-15, the U.S. Department of Justice announced the arrest of a 55-year-old Latvian woman on multiple charges (19 counts of a 47-count indictment) for participating in the development of the TrickBot malware.7
We previously reported on how TrickBot is spread via malicious emails.
References
- 1 https://www.secureworks.com/research/lv-ransomware
- 2 https://twitter.com/demonslay335/status/1403109032014061568
- 3 https://twitter.com/BleepinComputer/status/1403387905096175617
- 4 https://www.npu.gov.ua/news/kiberzlochini/kiberpolicziya-vikrila-xakerske-ugrupovannya-u-rozpovsyudzhenni-virusu-shifruvalnika-ta-nanesenni-inozemnim-kompaniyam-piv-milyarda-dolariv-zbitkiv/
- 5 https://www.fiscalia.gov.co/colombia/asuntos-internacionales/cae-presunto-ciberdelincuente-senalado-de-afectar-con-un-virus-informatico-a-mas-de-un-millon-de-usuarios-en-estados-unidos-y-europa/
- 6 https://www.justice.gov/usao-sdny/pr/three-alleged-international-cyber-criminals-responsible-creating-and-distributing-virus
- 7 https://www.justice.gov/opa/pr/latvian-national-charged-alleged-role-transnational-cybercrime-organization


