
Cryptography
From the beginnings of encryption to the present day — The history of cryptography and a look into the future.
Today, encryption is mainly thought of as an IT term, because data, e-mails, computers etc. are encrypted. But that was not always so. Encryption actually has its origins back in the year 480, but of course at that time, there was no IT that needed to be encrypted. And until a few years ago, encryption was primarily used in espionage or in top-secret government communications.
Table of Contents
What is Cryptography?
Data breaches in large companies have made headlines around the world, and they are increasingly becoming a fixture in the news. But with them, companies are becoming more aware of the need to protect sensitive data from third-party interference, and that contributes to a growing business interest in encryption. The Ponemon Institute has seen a steady increase in the implementation of encryption strategies in companies for the last 14 years.
Further, legal regulations (especially within Europe) force companies to use encryption. An important driver here is the General Data Protection Regulation (GDPR) that came into force in May 2018. Personal data must be encrypted as soon as it is transmitted over the Internet or stored in the cloud. Encrypted communication was hardly thought of a few years ago, but now it has become trendy.
However, since encryption is not an invention of modern times—for example, the Roman general Gaius Julius Caesar exchanged encrypted messages with his military leaders—let’s take a look back into the past in order to better understand today’s cryptography .
Steganography – Historical Obfuscation
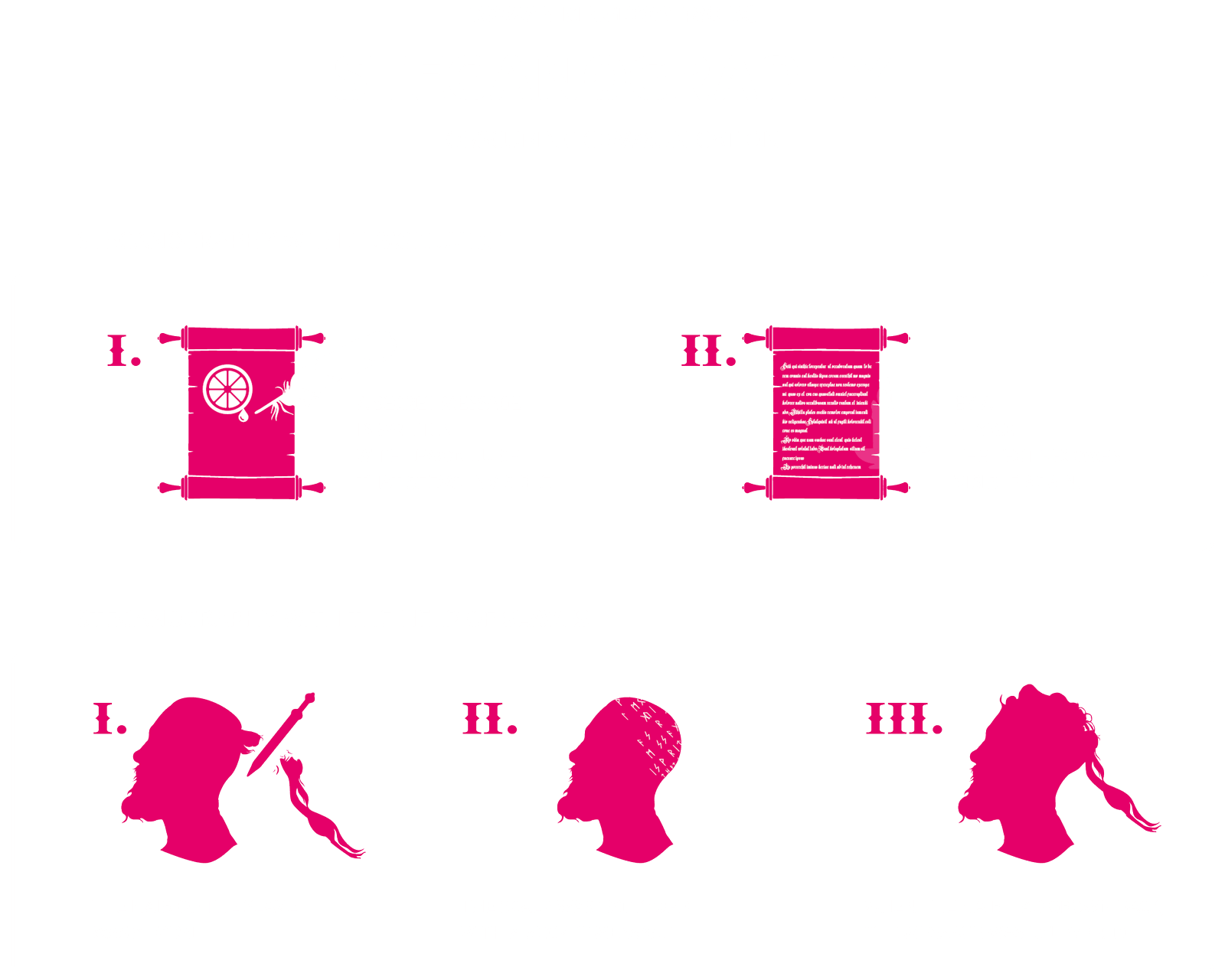
The year is 480, and Roman generals vie for rule of the Roman kingdom. Intrigue, murders and other fraudulent activities need to be planned and carried out. But how can an attack plan be sent undetected to the contractor?
Have you ever heard of lemon juice on parchment? It is an example of a classic secret communication method. The text is written on the parchment using lemon juice. After the lemon juice has dried, the parchment gives the impression of a blank page. But the recipient of the message can still decrypt the message very easily by holding a candle behind the parchment to make the lemon juice visible and read the message.
Another ancient method was to shave the hair from a slave’s head, tattoo the message on the back of the head and wait until the hair grew back in order to send the message to the rightful recipient. Without question, this was a radical means of communication and obviously was not suitable for urgent messages.
Such methods as these belong to steganography, which must be clearly differentiated from cryptography. Steganography is based on the fact that an outsider does not even notice that two communication partners are communicating with each other.
Caesar Cipher
In contrast to steganography, cryptographic communication between two or more communication partners can be visible and still remains protected. Only the message is unreadable by outsiders because of the encryption.
Let’s stay in Rome and dive into the world of the Gauls and Romans.
A popular encryption technique was developed by a historically well-known personality: Gaius Julius Caesar. The famouse Roman emperor communicated with his military leaders in encrypted messages, known today as the Caesar cipher. Neither unauthorized persons nor the enemy, in this case the Gauls, knew how to decipher the news. But over time, this encryption method could be cracked with fairly simple means.
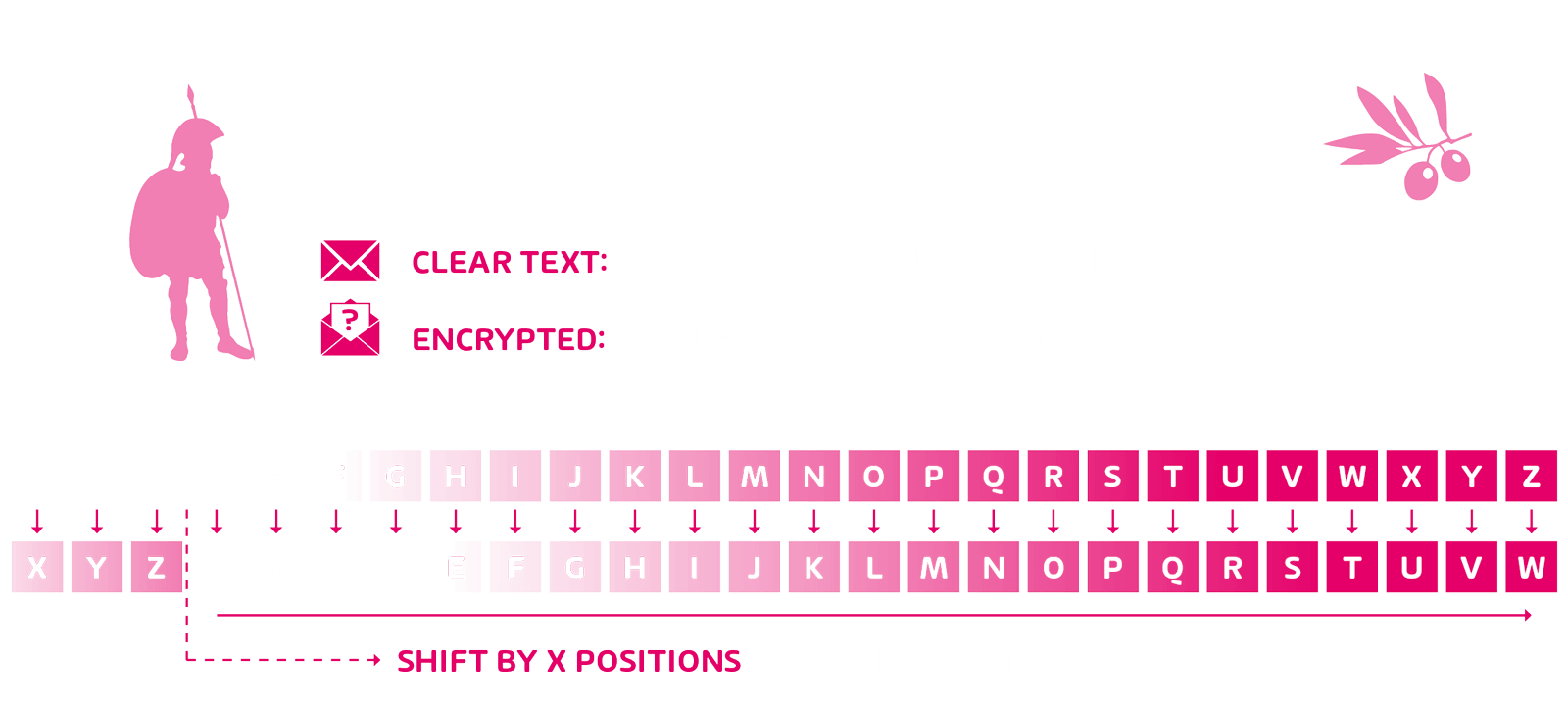
The Caesar cipher is a simple symmetrical encryption method based on a substitution. This means that every letter used in the message is replaced by a new letter. The replacement letter results from a letter offset within the alphabet that is determined in advance, e.g. a shift of three places. “Thank you” then becomes “Gdqnh.” A cipher disk was often used for decryption in order not to have to constantly go through the alphabet. With this type of encryption, the recipient only had to be informed of the offset as a secret key in advance.
An unauthorized person could not decode the message without the key. But if he has dealt with the cipher before, it is easy to decrypt any message within 25 attempts, since you need to check the alphabet at most once to discover the correct letter offset. Today’s computers would take less than a second to do this.
The Caesar cipher is therefore no longer considered secure and has been replaced by newer methods.
All aboard, we are off to France in the 16th century!
Vigenère Cipher
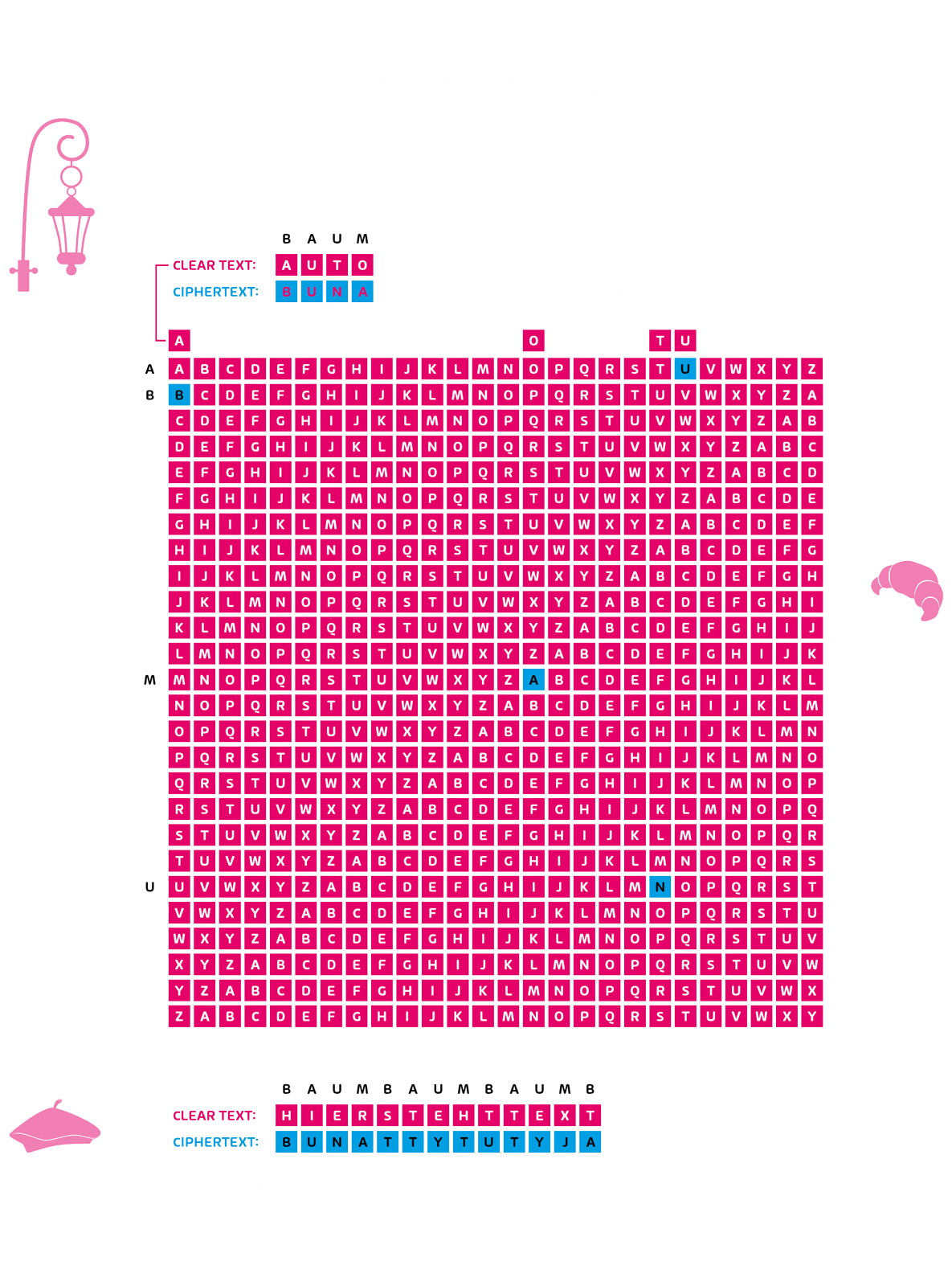
One of the methods that replaced the Caesar cipher as a secure alternative was that of the French diplomat and cryptographer Blaise de Vigenère in the 16th century, also known as the Vigenère cipher. It is comparable to the Caesar cipher and is also based on the substitution of letters, but several ciphertext alphabets are used.
How many alphabets are used is determined by a key. Instead of a number, a keyword is chosen here, which is written under the message. The keyword determines the letter offset for each letter. The first letter of the key word determines the alphabet for the first letter of the plain text, the second letter of the key word determines the alphabet for the second plain text letter.
Example of Vigenère Encryption
Keyword: gift | Message: We’re giving Tom a voucher for his birthday
CM’WX MQABTO YHS I AHAKMXX NTK NQX UOZYAJID
GIFT GIFT GIFT GIFT
The “G” provides a letter offset by seven letters, since the “G” is in the seventh position in the alphabet. The “I” is offset by five letters and so on. This is how the “WE” becomes “CM”.
The security of this encryption method is strongly related to the key length and whether the key is used repeatedly. The keyword from our example is therefore not especially secure.
But after a few years, this encryption method also proved to be decipherable. Next, we’ll look at another encryption method that was considered unbreakable for a long time.
Enigma Code and the Turing Machine
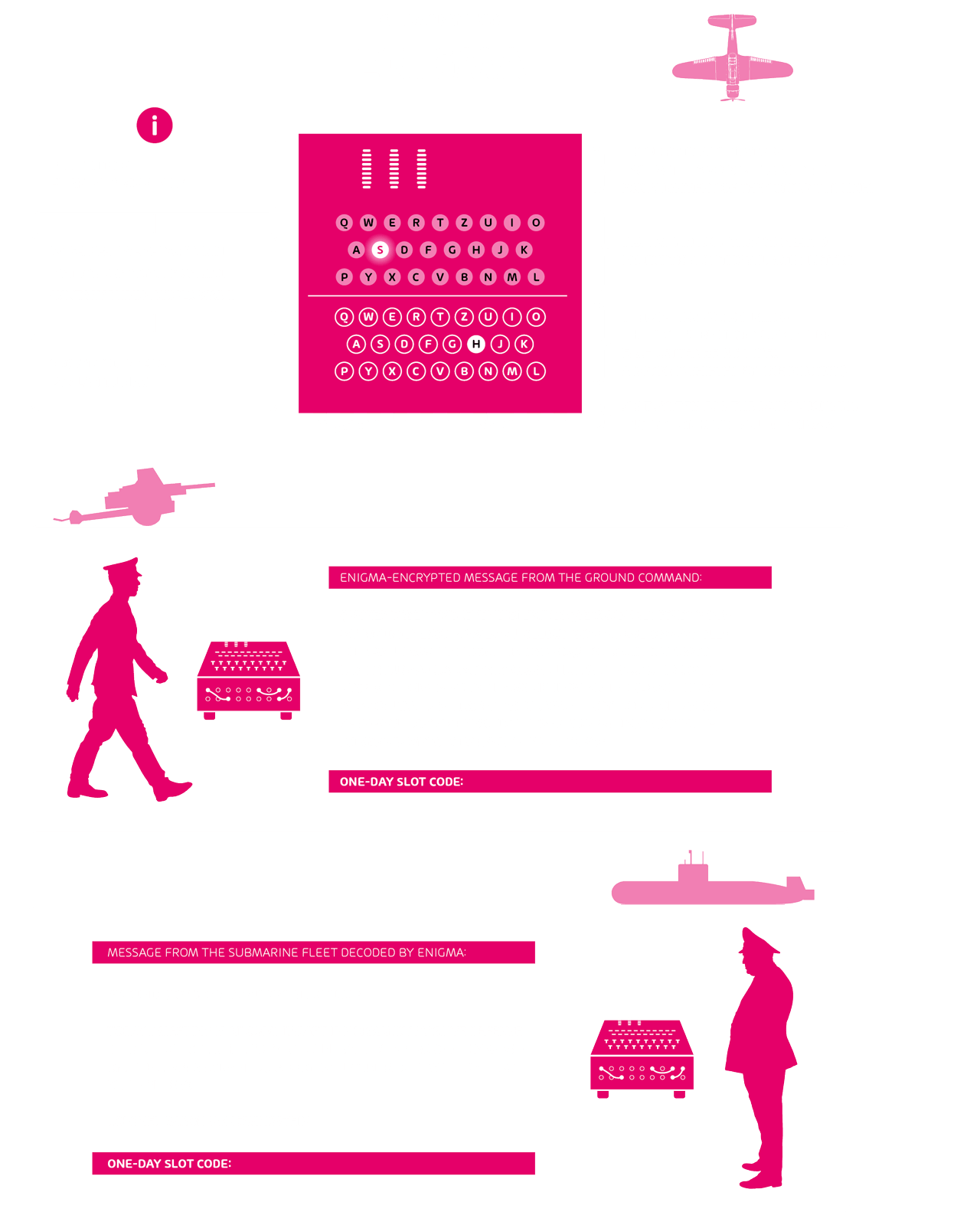
Our next stop is Germany in the 1930s. As already described with the Caesar cipher, encryption methods were primarily used in a military context. It is therefore hardly surprising that Germany also relied on encrypted communication during the Second World War. The special thing about this method was that it was encrypted and decrypted using a machine. The encryption key was changed every day so it would no longer be valid after 24 hours. The machine we’re talking about is Enigma.
The Enigma machine for routine encryption and decryption was invented by Arthur Scherbius in 1918. The basic working principle goes back to the years of the First World War. World War I is considered to be the first war in which cryptography was used systematically. During the war and the years that followed, the first machines were developed that offered significantly higher security than the manual methods. Enigma was offered for sale after its manufacture but met with very little interest from both business and government agencies. It was not until 1933 that the Enigma became part of the standard equipment of the National Socialists under Hitler. But how exactly does this wonderful machine work?
At first glance, it is reminiscent of a classic typewriter. But a rather complicated system is hidden inside. To put it simply, the operating principle is based on simple electrical circuits, each of which connects a letter key on the keypad with an electric lamp that lights up a letter on the display. However, the “A” is not linked to the “A” of the display, as all the reels are interlaced according to a certain system. The message can only be decrypted if the recipient knows all the settings of the sending Enigma.
Sounds like insurmountable encryption, doesn’t it? But it too was cracked by a British computer scientist in 1941. Alan Turing declared war on Enigma and actually won it with the “Turing machine” he developed. Historians claim that this ended World War II prematurely and saved millions of lives.
Principles of Modern Cryptography
As you have now learned at our various stations, even systems whose encryption algorithm was known only to the receiver and sender could be cracked. But this was exactly the problem. A principle of modern cryptography, also known as Kerckhoff’s principle, therefore states that the security of a (symmetric) encryption method is based on the security of the key rather than on the secrecy of the algorithm. It is therefore recommended to use public algorithms that have already been sufficiently analyzed.
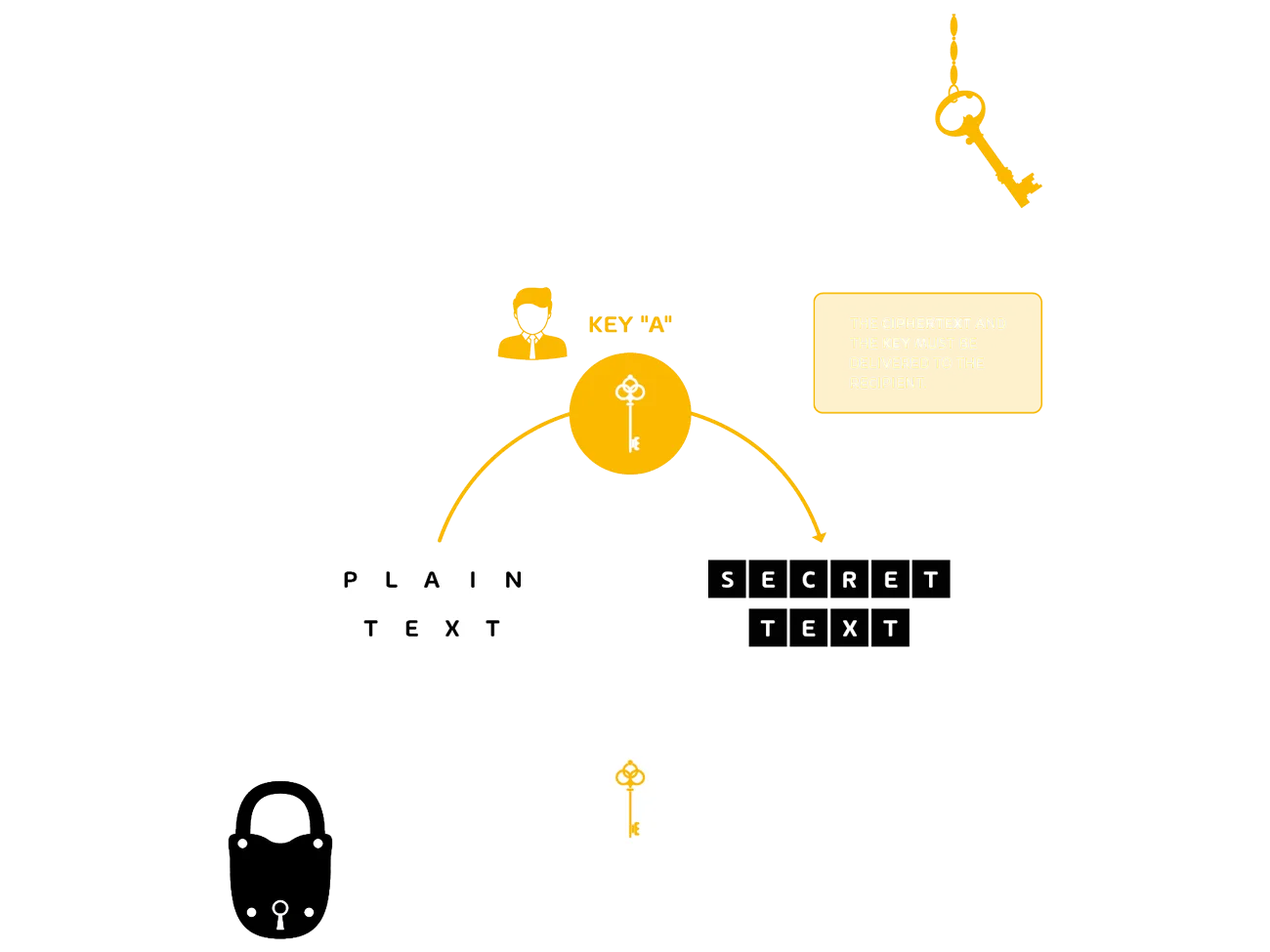
Symetric Encryption: Encryption and Decryption of Information
There are infinite possibilities to encrypt messages or data. This brings us to our first stop. All visited stations from the first article have one thing in common: They are all based on the same encryption method, the symmetric encryption.
The principle of symmetric encryption describes the encryption and decryption between sender and receiver with one and the same key. However, the key must first be passed to the recipient together with the encrypted message so that the recipient can read the message in plain text. This is similar to the messenger who used to travel from the sender with the message to the recipient to deliver it to him. Until the 1970s, only symmetrical encryption methods were used. A very well-known and widely used encryption method is the Data Encryption Standard (DES), which we will take a closer look at at our next station.
DES Encryption – The Data Encryption Standard
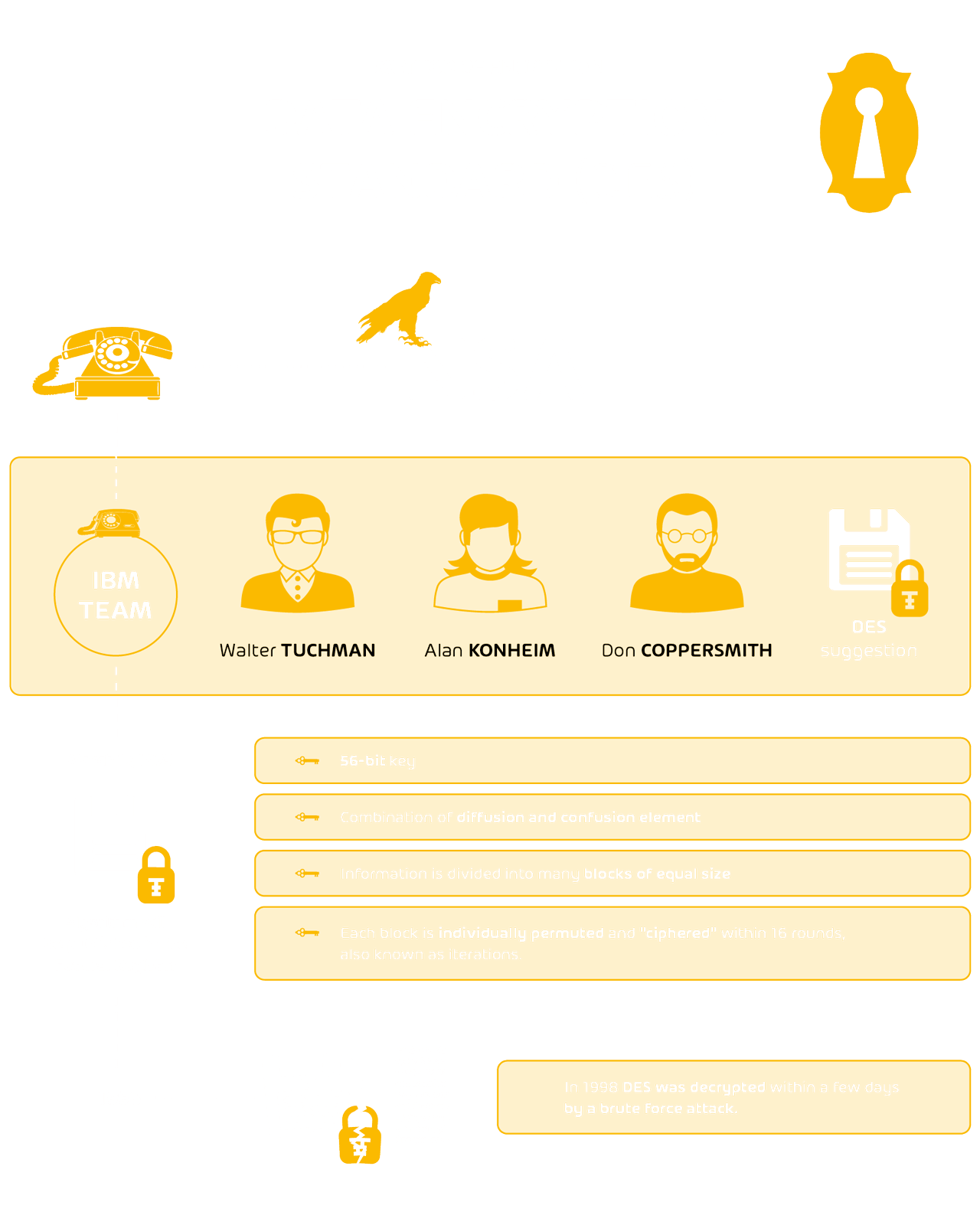
DES was developed in the 1970s after the NSA issued a call for tender to develop a uniform standard for the inter-agency encryption of confidential data.
An IBM development team led by Walter Tuchman, Don Coppersmith and Alan Konheim then submitted a promising proposal for a corresponding encryption procedure and was promptly commissioned. On March 17, 1975, the algorithm designed by IBM was published in the Federal Register and approved as an encryption standard just one year later.
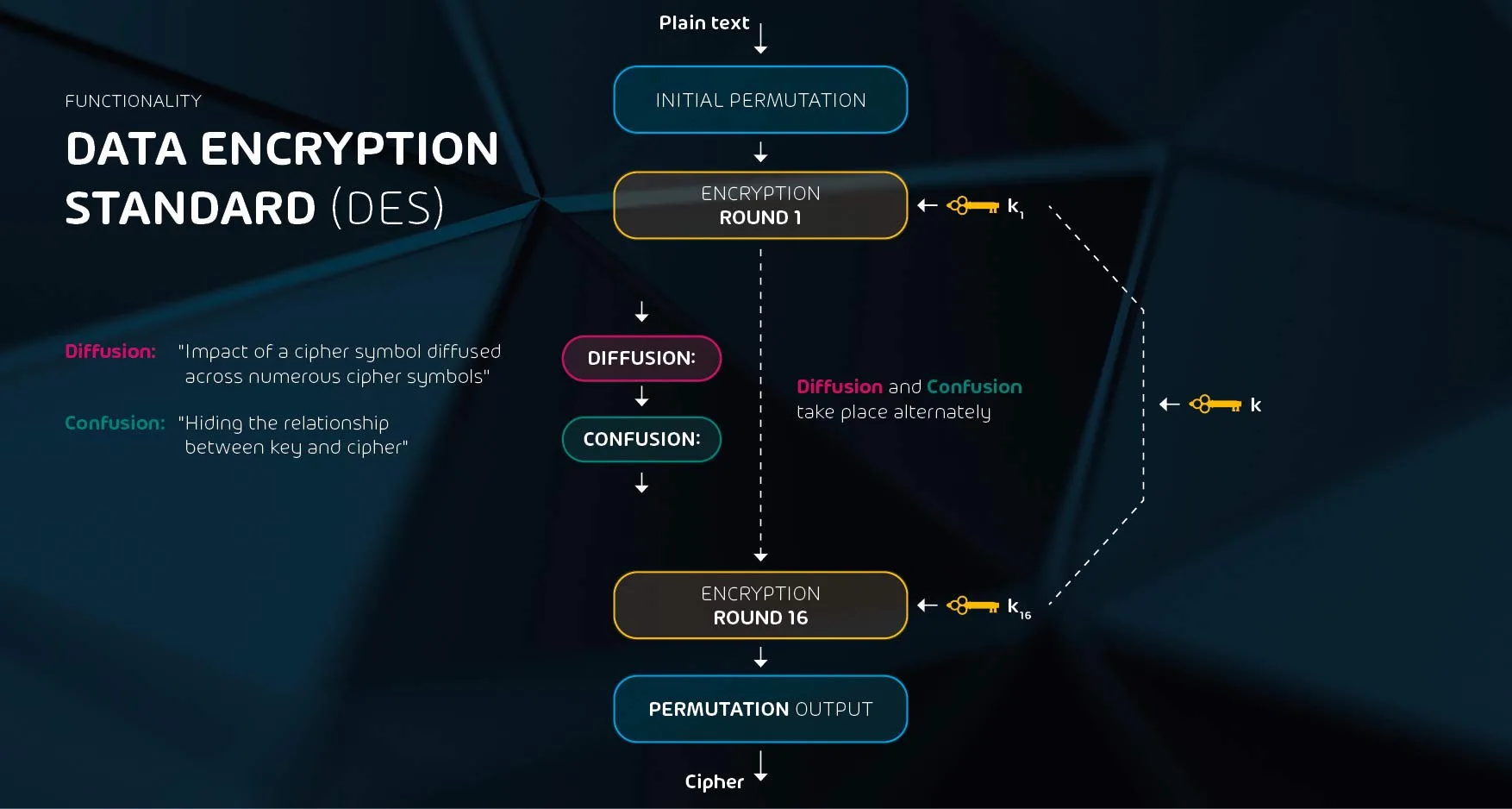
DES uses a 56-bit key and a combination of diffusion and confusion elements. The information to be encrypted is divided into many blocks of equal size. Each block is individually encrypted using a round key and “scrambled” in 16 rounds, also called iterations. In order to decrypt the message again, the blocks must be put back into the correct order.
Questions about the role of the NSA in this project arose many times. The NSA is said to have deliberately built in a back door so that they can read the encrypted information. The main reason for these suspicions were the discussions about the key length: IBM preferred a key length of 64 bits while the NSA considered a key length of 48 bits to be sufficient. The agreement was then reached on 56 bits.
Many questions were raised about the role of NSAs in this project. The NSA is said to have deliberately installed a back door so that they can read the encrypted information. The main reason for these suspicions was the discussion about the key length: IBM preferred a key length of 64 bits while the NSA considered a key length of 48 bits to be sufficient. The agreement was then reached on 56 bits.
DES was widely used in ATMs and was therefore considered a very secure encryption system. In 1998, however, “Deep Crack” succeeded in cracking the 56-bit key for the first time. The device was able to decrypt the DES algorithm within a few days using a brute force method. Today, this would be possible in a very short time. DES was therefore attested to be highly susceptible to brute force attacks.
In 2001 the Advanced Encryption Standard replaced DES as its successor. This brings us to our next station.
Advanced Encryption Standard Encryption (AES) – More Security
As DES had not been sufficiently protected against brute force attacks with its 56-bit key since the 1990s, the American Department of Commerce issued an invitation to tender for a successor algorithm on January 2, 1997. To ensure a certain level of security of the Advanced Encryption Standard, the algorithm had to meet certain criteria.
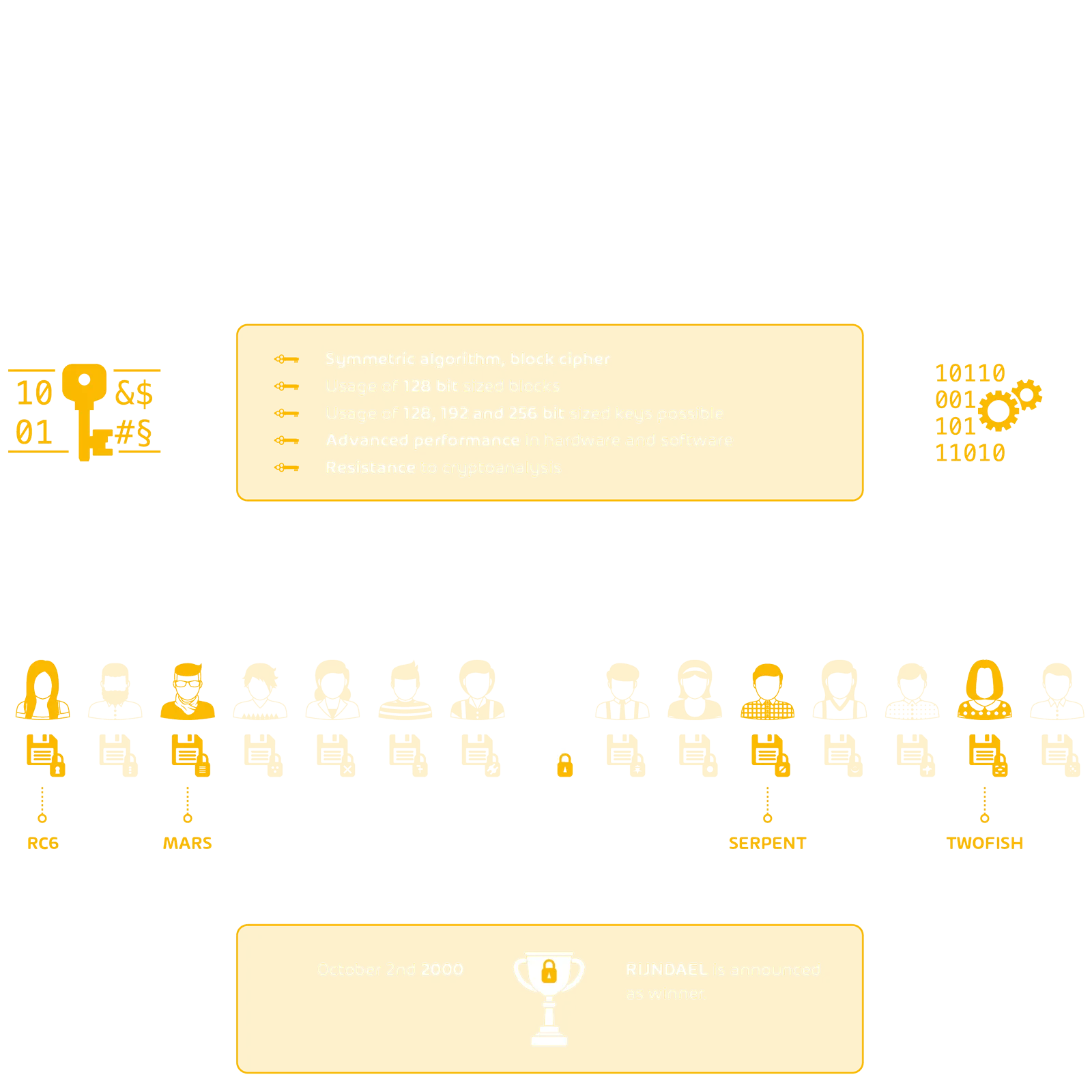
Selection criteria AES:
– Symmetric algorithm, block cipher
– Use of 128 bit long blocks
– 128, 192 and 256 bit long keys can be inserted
– Above-average performance in hardware and software
– Resistance to cryptanalysis
By the deadline of 15 June 1998, fifteen proposals had been submitted. Among the five best candidates were the algorithms MARS, RC6, Rijndael, Serpent and Twofish. Since all candidates met the required criteria, additional requirements were set up to select a winner. Since Rijndael convinced mainly by its simple software implementation, security and speed, the Belgian algorithm was announced as winner on October 02, 2000.
But the choice of the winner was not without controversy. Critics also saw weaknesses in the advantages of the structure and efficiency of the Rijndael algorithm. They argued that the simpler the structure of an algorithm is, the easier it is for hackers to understand and hack it. Practically relevant attacks, however, do not exist until today, which makes AES very secure. The use of AES encryption is widespread, for example in wireless LAN, VPNs, VoIP telephony or the encryption of files.
Asymmetric encryption with one key pair: It’s a match!
As already mentioned, DES and its successor AES are based on symmetric encryption. Another encryption method is asymmetric encryption. Unlike symmetric encryption, asymmetric encryption relies on two key pairs: the so-called private key and the public key. The sender encrypts his message with the public key of the recipient. The recipient, in turn, can only decrypt the message with his private key. The private key is, as the name suggests, private and remains stored on the recipient’s own devices as far as possible. This process ensures that only the legitimate recipient can decipher the message. Prominent encryption techniques that use asymmetric encryption are PGP and S/MIME.
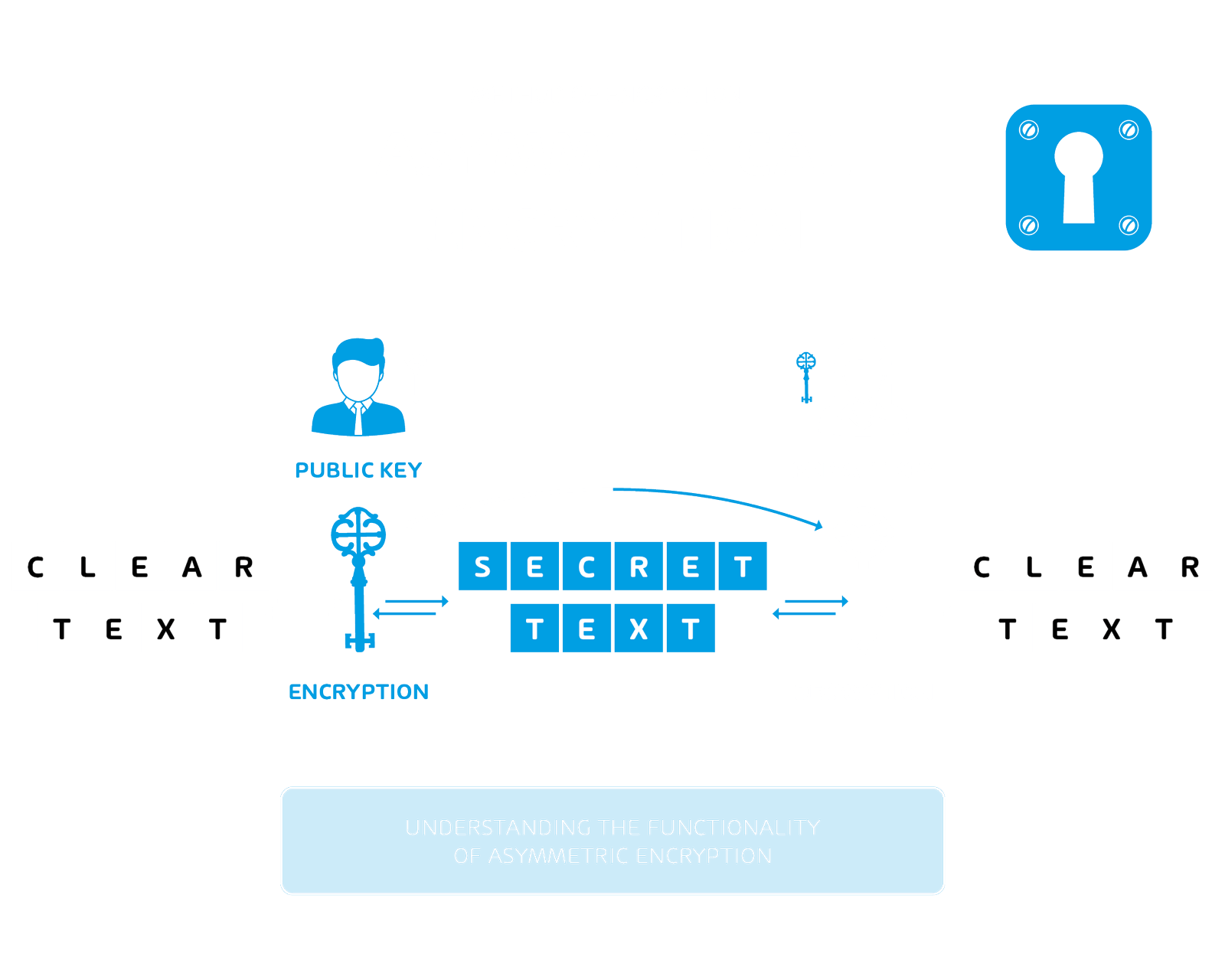
If a message is to be sent encrypted to a recipient, the recipient’s public key is required first. The public key can be characterized as a kind of “one-way key”, because it can only encrypt but not decrypt. A very common example to illustrate this is the mailbox in traditional letter dispatch: The sender knows the address of the recipient and can drop the letter in his mailbox. However, the recipient cannot get the letter out this way. Therefore, an additional key is needed to open the mailbox and then get the letter. Similarly, the recipient can only decrypt the message with his private key.
In 1974 Ralph Merkle took the first step towards the development of the asymmetric cryptosystem with the Merkles Puzzle, named after him. The first asymmetric encryption method was developed by cryptographers at MIT in 1977: the RSA method. However, this method is very susceptible to attacks, since it is deterministic, i.e. pre-determined, and thus easy to crack.
PGP (Pretty Good Privacy) encryption: Pretty good!
In the 1990s, the US Senate decided that a back door should be built into any encryption software or hardware. Pretty Good Privacy, PGP for short, was then specified by Philip Zimmermann in 1991. With the development he pursued the goal that all US citizens and citizens’ movements could exchange encrypted messages and avoid access by secret services.
Since the US export law prevented a license-free export of the PGP source code, it was typed as a book by more than 60 volunteers. At that time, the book was not subject to export restrictions and could therefore be legally exported from the USA to make the code known worldwide.
In 1997 PGP was bought by McAfee and integrated into their product portfolio. In 2002, the company abandoned the brand. The reason for this is said to have been the strong criticism of the non-disclosed source code of PGP. Until 2010, the newly founded PGP Corporation held all rights to PGP until it was sold to Symantec in 2010.
PGP is based on an encryption concept with two main functions: Encryption and signing of a message. As explained above, encryption uses a key pair. However, PGP does not encrypt the entire message asymmetrically, but only the session key used. The actual message is encrypted symmetrically. The reason for this hybrid encryption is the too high computational effort for a purely asymmetric encryption.
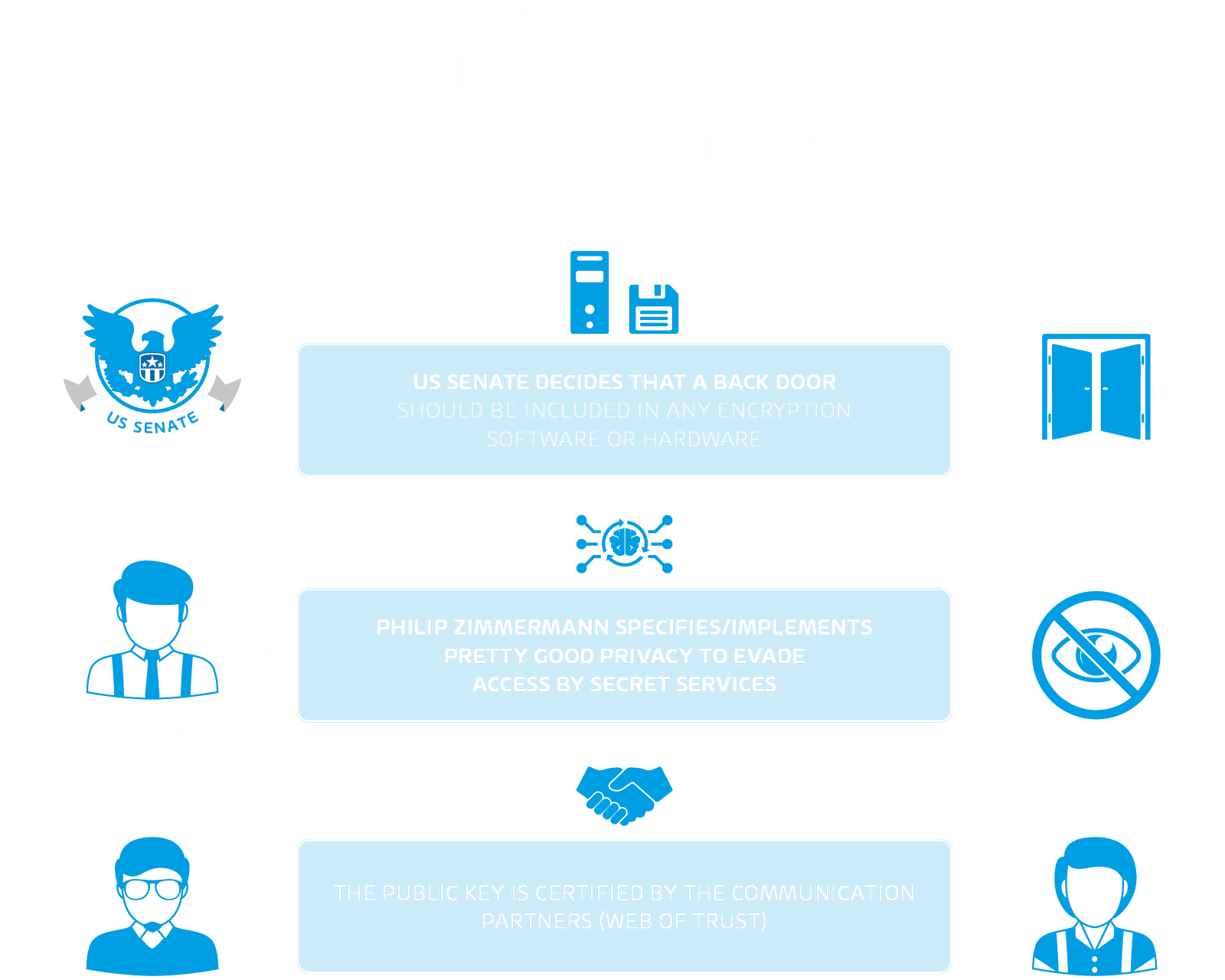
In addition to encryption, the public key can also be used for signature generation, which can be used to confirm the authenticity of the message. Thus, the authenticity, integrity and confidentiality of the message can be guaranteed. To achieve this, the public key must be authenticated with the private keys of the other communication partners. This procedure is also called Web of Trust (WoT). This type of trust model is advantageous if you want to remain anonymous. Prominent users of PGP encryption are therefore whistleblowers like Edward Snowden. The security of PGP is only guaranteed as long as the users keep their private keys secret.
We take a leap from PGP, developed in 1991, to 1999, the birth of another asymmetric encryption standard.
S/MIME – Encryption via certificates
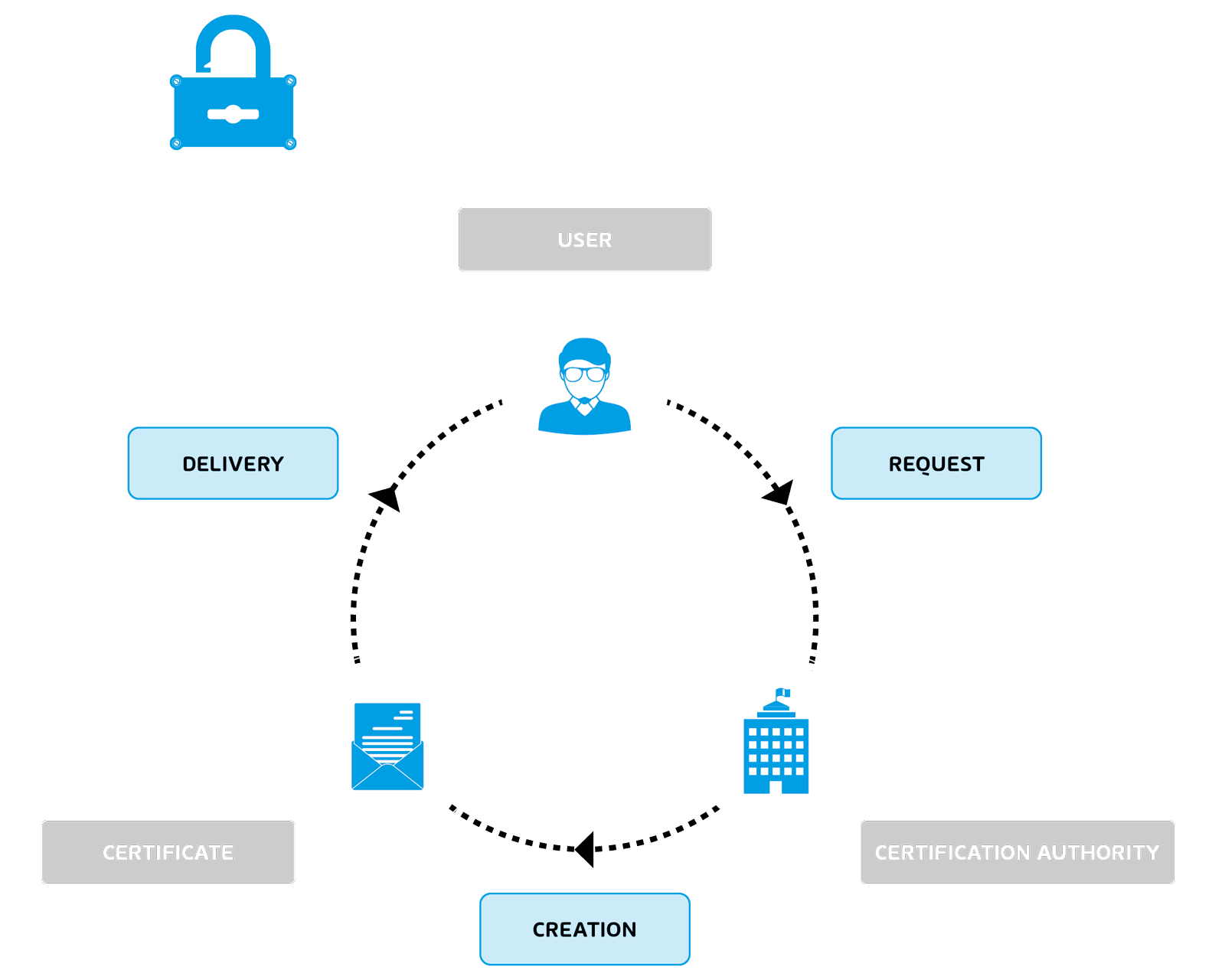
The encryption method, S/MIME, which was published in 1999, is also based on the main applications signing and encryption and is therefore similar to the way PGP works. However, if you want to encrypt and sign your e-mails with S/MIME, you have to register with an appropriate certificate authority and apply for a certificate. The authentication of the public key by the other communication partners, as is the case with PGP, is thus replaced here by a formal certificate. The communication partner can then see in the header information of the message from which certification authority the sender has received his certificate and, if necessary, have his identity confirmed via this authority. Companies in particular use S/MIME for their e-mail encryption.
Basically, both encryption methods are only secure as long as the private key is kept secret. In 2018, however, a research team from the University of Applied Sciences Münster, the Ruhr University Bochum and the University of Leuven published a document questioning the security of the encryption standards PGP and S/MIME and thus attracted attention. However, the research results did not focus on the protocols themselves, but rather on a weakness in mail clients such as Thunderbird, Apple Mail, etc. The topic was taken up in media reports worldwide under “Efail”. Also Hornetsecurity dedicated an own blog post to Efail.
Slowly but surely we want to leave the terrain of the different encryption methods and take a look at the next stations to see which attacks both encryption methods and the data traffic itself are exposed to.
Brute Force Attack – Trial and Error
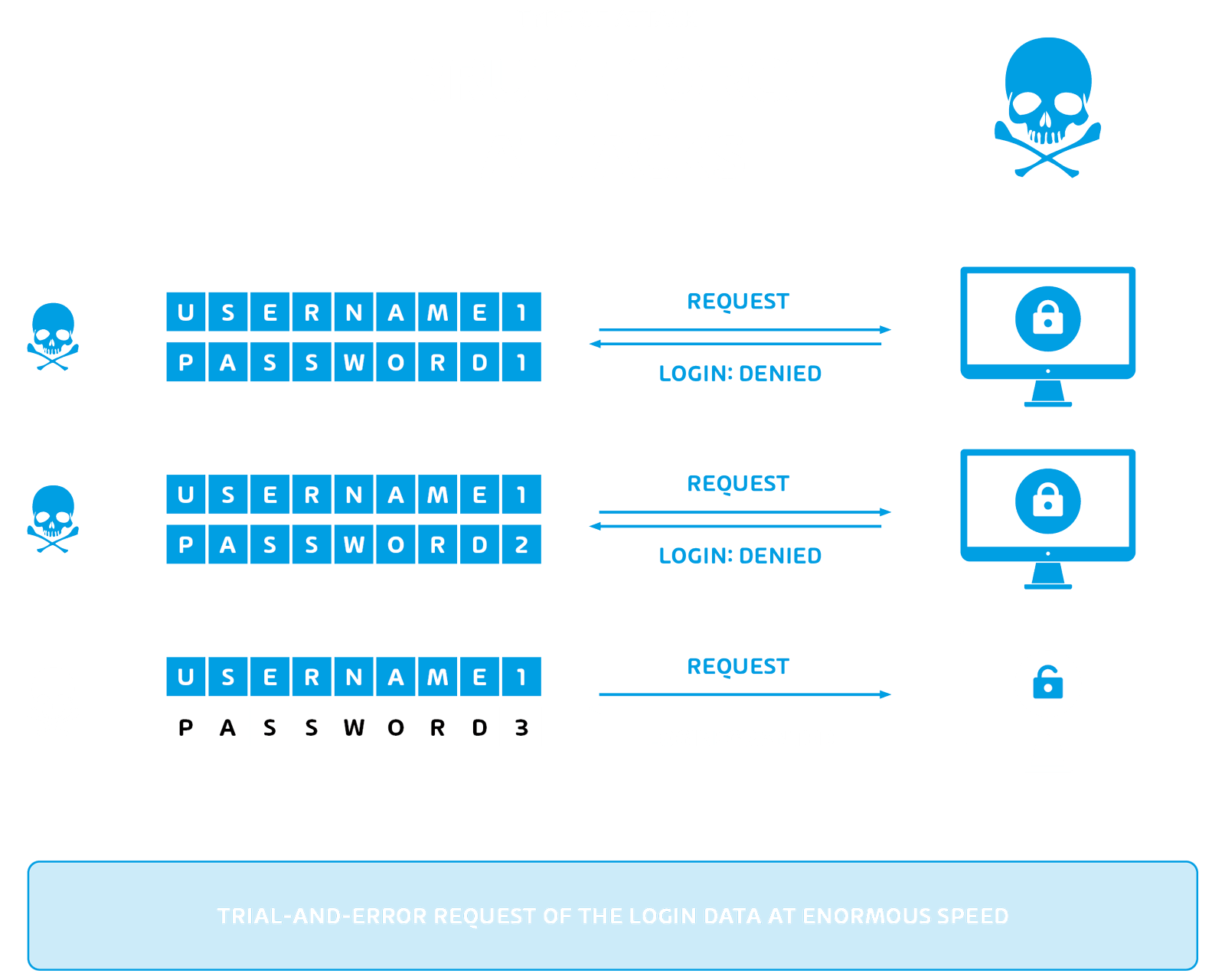
Brute force attacks are used to obtain information by means of the trial and error method. With the help of appropriate software, various combinations of characters can be tested within a short time in order to gain illegal access to the desired information. This method is often used for passwords, but also for deciphering ciphertext. In this complete key search, all possible key combinations are tested “exhaustively”.
As already explained in the last article, the DES encryption algorithm was cracked by means of a brute force attack, since with a key length of 56 bits “only” about 72 quadrillion combinations are possible. Thus, a brute force attack can be counteracted with modern encryption algorithms by using a sufficiently long key. It would be hopeless to start a brute force attack here, since the necessary computational effort would be too high. There are, however, mathematical attacks that considerably reduce the complexity of the key, such as the square root attack. In addition, there is another variant to secure these attacks, which you probably already know: after X failed login attempts on your smartphone, it is locked for a certain time.
Our next station is dedicated to an attack technique that can tap any data traffic and is therefore particularly dangerous.
Man-in-the-Middle Attacks – Undercover in the data stream
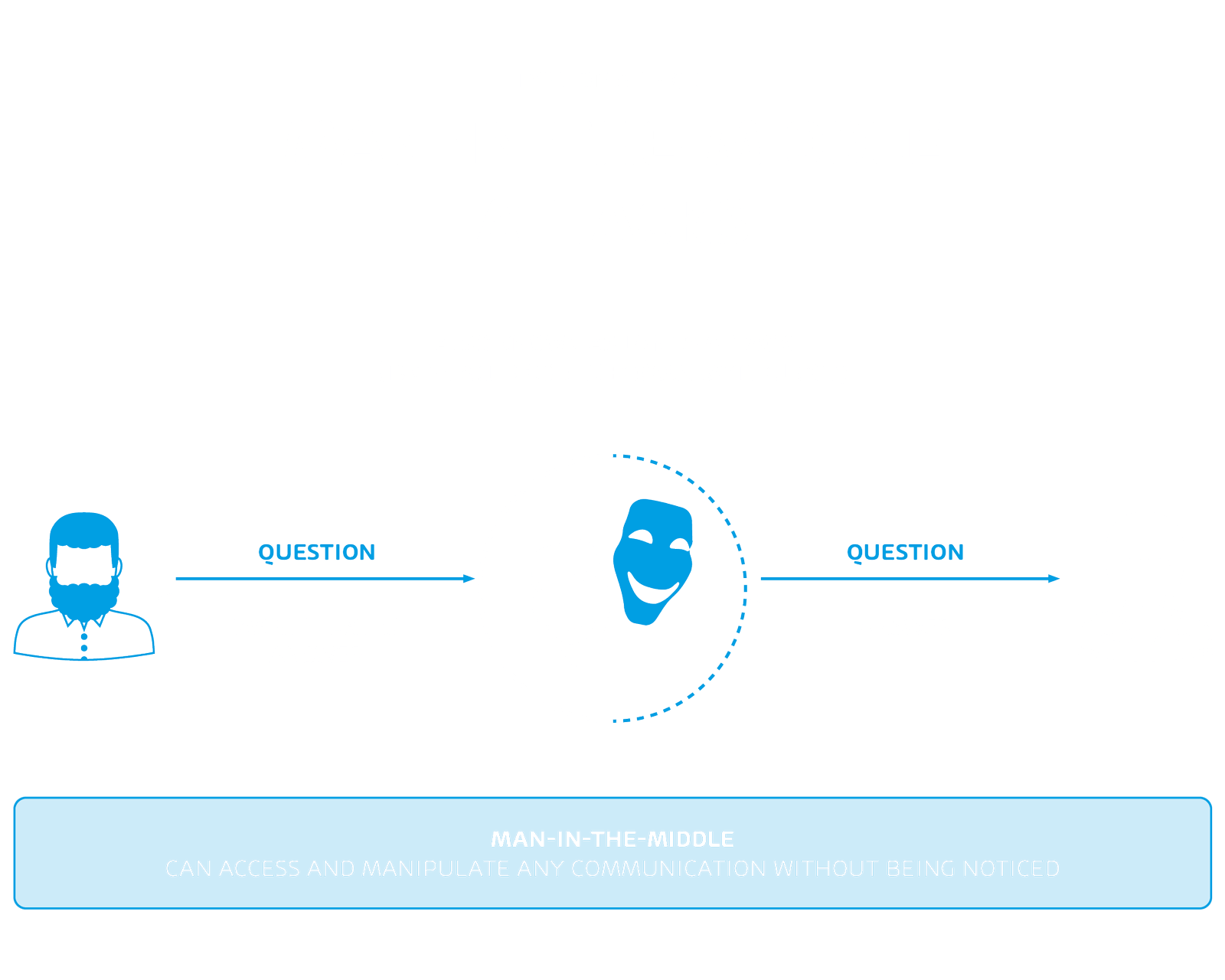
In a man-in-the-middle attack, also known as Janus attack (Roman mythology), a third party switches unnoticed between two communication partners. In doing so, he pretends to be the other’s actual counterpart. The aim of this attack is to view or even manipulate the data traffic at will. Depending on the area of application, the attack scenarios are manifold. A popular attack vector is, for example, an open WLAN network set up by the attacker, to which the victim connects. This allows the cybercriminal to read any data traffic while the victim is surfing the Internet recklessly. Encrypted e-mail communication can also be attacked using the same principle:
The attacker transmits his public key to the sender, but pretends that it is the public key of the legitimate recipient. The sender now encrypts the message with the public key, which is also available to the attacker, who decrypts it with his private key and can read and manipulate the message. To ensure that the communication partners are not aware of this, the message is encrypted by the attacker with the public key of the legitimate recipient and forwarded to him so that he can receive and decrypt the now manipulated message.
In order to avoid this kind of attack, the public keys should be checked for authenticity, for example by using appropriate certificates, as is the case with S/MIME.
Cryptography Future
We are at the end of our journey. We hope that you enjoyed this trip as well and that you were able to take some things with you. Finally, we would like to take a short look into the future. You will probably have read quite a bit about it in the media: quantum computers. They are the most powerful and fastest computers in the world. The question that arises here in this context Is our encryption today safe from quantum computers? What do you think?

Visit our knowledge base
Did you like our contribution from the knowledge base on cryptography? Then you can access the overview page of our knowledge database here. There you can learn more about topics like Trojans, Malware, Crypto Mining, IT Security, DDoS attacks, Cryptolocker Ransomware, Computer Worm, Brute Force Attacks, GoBD, Cyber Kill Chain and Emotet.
