

How to Air-Gap and Isolate Your Backups
In this article, following on from How to Secure and Protect Backup Data, we look at how to isolate your backups using air-gapping, firewall, performing risk analysis for your backup strategy, encrypting backups for additional protection and round off with some frequently asked questions.
Shielding Backup Systems With Firewalls
Your backup application should have the ability to reach out to other systems, but almost nothing needs to reach into its system. You can put up barriers to external access easily using firewalls. Every modern operating system includes a native firewall. Several third parties provide add-on software firewalls.
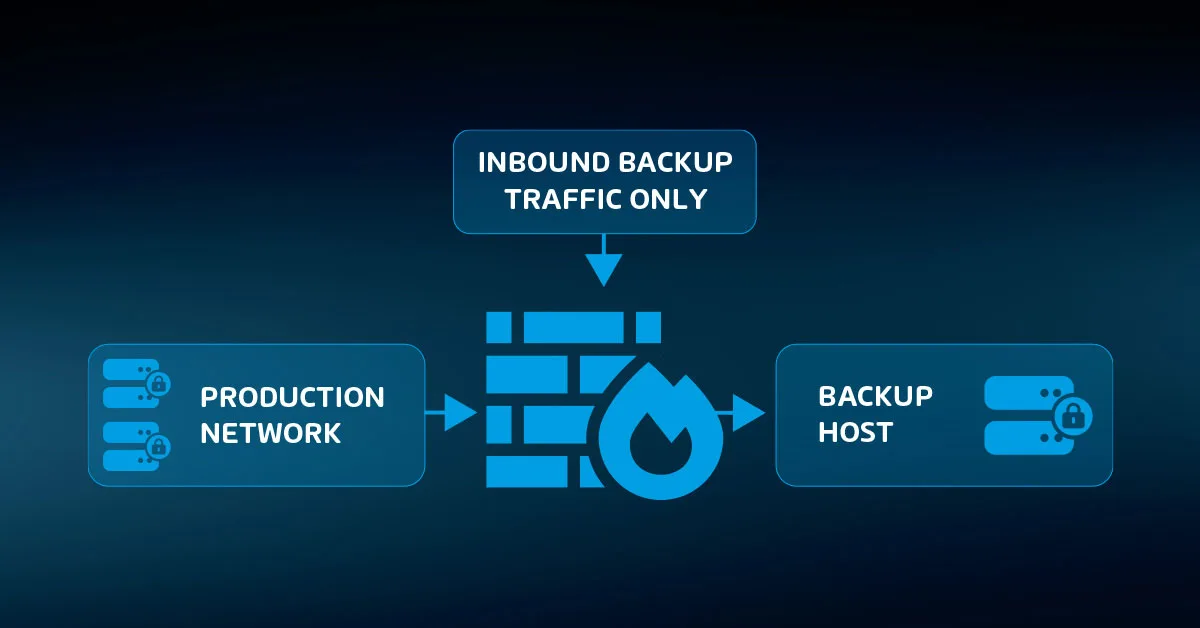
Your antimalware software might include a firewall module. Hardware firewalls bolster software firewalls immensely. Most smaller organizations typically employ them only at the perimeter, but they can add substantial security to your internal networks as well. Even inexpensive devices provide isolation and protection.
You can also configure routers and switches with VLANs or network address translation to provide additional isolation layers.
Air-Gapping for Isolation
Among all the methods of isolating, air-gapping represents the strongest. It can even stand in for immutability solutions. However, it also requires the most effort to implement. Before choosing this route, take the time to understand its ramifications. It should not be undertaken on a whim or without input from executive decision makers.
The simplest description of air-gapping is that there is no remote connectivity into a given system. A most extreme example is offline root certification authorities. Administrators create them, publish their public keys and revocation lists, then take them offline and disconnect them. Some even take extra steps, such as removing their hard drives and placing them in locked storage.
To access such a system, a human must perform manual steps that involve physical actions and security measures.
You cannot realistically apply such a drastic procedure to your backup system. However, it serves as a beginning. Start there and add the minimum elements to make the backup operational. Backup servers need to be powered on and have some way to retrieve data from and push restores to their targets, but nothing else.
To make maintenance easier, the system should have some way of sending notifications to administrators. With all of that configured, you can function without any way to access the backup server remotely. So, you can set it up to only allow access from a physical console.
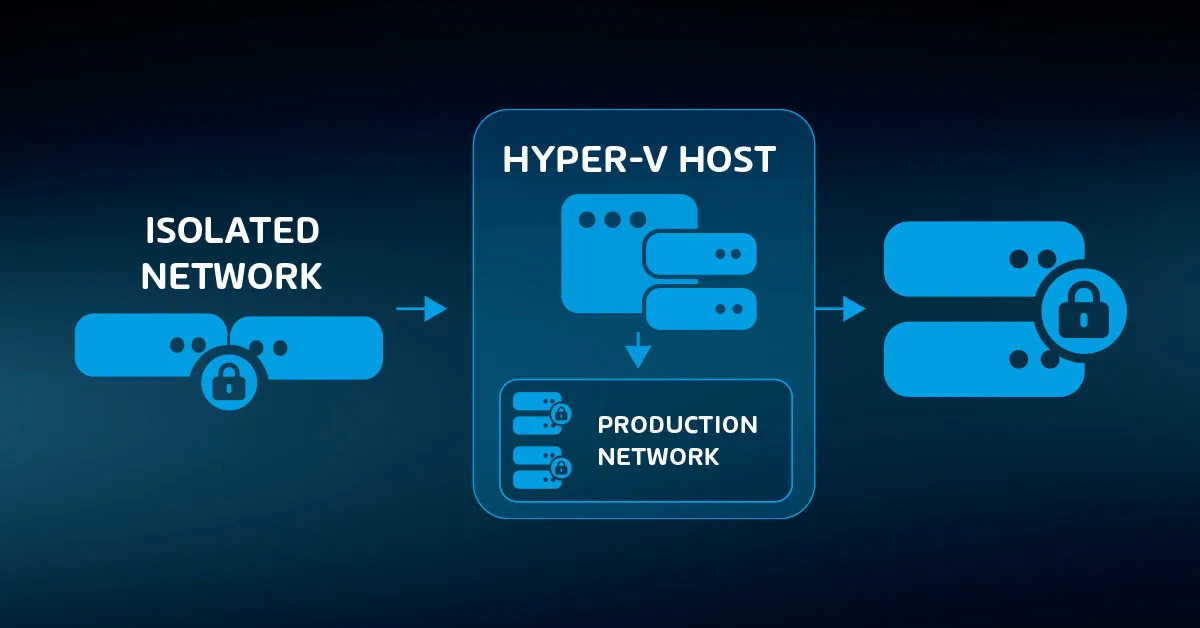
The more that you use virtualization in your environment, the easier it is to implement air-gapping. You can configure the hypervisor and backup in one network and everything else in another. If they have no overlap or interconnect, then you have created a proper air gap.
You may even choose to go so far as to create an Active Directory domain just to hold these systems. That way, you can benefit from centralized management without connecting your production network to your management network.
The greatest risk with an air-gapped system is its enormous inconvenience. Preventing remote connections includes blocking valid administrative duties, too. It makes patching very difficult. It has no ability to transfer data to a remote location either, which means that you lose replication capability. You have only two choices: cope with these restrictions or do something that breaks the air-gapping.
A poorly air-gapped system is more vulnerable than one that was designed from the start to participate on the network. If you cannot commit to a completely disconnected system into perpetuity, then connect your backup system and build defenses around it.
Caring for Offline Data
The cold data that lives on data tapes and detached hard drives often does not get the protection that it deserves. Usually, IT departments start out with a protocol to care for them, but over time, they lose diligence. We covered encryption in an earlier section, which can serve as a last-ditch safeguard. However, you must make every effort to prevent unauthorized access.
Technological advances, reduced costs, and increased convenience have made fully online backup systems viable. Today, you can easily replicate backup data to geographically remote locations without an exorbitant investment.
However, the ever-growing threat of ransomware means that you must periodically create offline copies. In the past, that could only mean data that was completely inaccessible by any automated means.
That is still the safest option. However, you can take advantage of modern technology to create alternative approaches. You could manually upload backup data to a location that requires two-factor authentication, for instance.
Whatever measures you put in place, ensure that they isolate the remote site in such a way that no compromise of your online backup system or password vault will put offline data at risk.
Putting It in Action
Think of security as a continual process, not a one-time event. We will cover the hardware portions in the next article on deployment. This portion will cover these security actions:
- Perform a risk analysis;
- Set policies for software-level/media redundancy;
- Establish backup encryption policy;
- Determine practices and policies for creating and protecting offline data.
You saw the concepts behind these activities throughout this chapter. Now you must put them into practice.
Risk analysis activities
Much of risk analysis involves asking questions. You should gather input from multiple sources. Usually, one person does not have the visibility to know all likely risks. You can use formal meetings, informal queries, or any other approach that works for your organization. Categorize and list what everyone comes up with. Share them with key stakeholders, as they might bring up other ideas. Some starting thoughts:
- Internal vs. external categories;
- Malicious vs. accidental damage;
- Targeted risks (e.g. employee data, client data, account numbers, etc.);
- Equipment failures;
- Weather;
- Electrical outages.
You must keep this list up to date with an explanation of how your solution mitigates each. One of the best things you can do to protect your company is to train your employees with the Security Awareness Service.

Creating backup redundancy policies
You will need to have made your software and hardware selections before you can craft your redundancy approach. The features and media types used in your systems will have great influence on your decisions. However, your primary goal must be to create sufficient standalone copies to survive loss or damage.
To qualify as “standalone”, a backup copy must not require any other backup data to exist in order for you to restore it. Furthermore, to provide security, the copy must only exist in an offline, disconnected state. Due to the inconvenience of offline backups, you can either build a schedule that mixes online with the occasional offline complete backup, or you can set a special schedule for offline backups.
You also need to plan for how long these offline copies will exist. The cost, longevity, and ease of storing the media tends to have the greatest control over that. If possible, simply keep them until you can no longer restore from them. Reality often dictates otherwise. If you can schedule full backups, then you might come up with a schedule such as:
- Monthly: full, offline
- Weekly: full, online
Some modern backup software that relies heavily on deduplication technology does not allow for scheduled full backups. Instead, these depend on other policies to set the oldest possible backup and calculate deduplication from that point forward.
Therefore, they consider full backups to be special, so you will need to perform them manually. The inconvenience of such backups, especially for an already busy IT department, will likely prevent their weekly occurrence. Create a palatable policy that balances the security of multiple full copies against the ease of creating and storing them.
Establishing an encryption policy
You will need to build your backup encryption policy around the way that your backup hardware or software utilizes encryption. Most software requires a single secret key for encryption. You have three major points for this type:
- Where will you store the key?
- Who will have access to the key?
- How will you ensure that the key will survive catastrophe?
Remember to include the loss of your backup encryption key in your risk analysis! The location of your key directly dictates access. Since you need it to remain available in the event of a total loss, then your best option is likely a cloud-based password vault.
There are multiple software companies that provide such services. Microsoft’s Azure has a “Key Vault” product and Amazon Web Services offers “AWS Secrets Manager”. Find the solution that works for your organization.
Any backup created with a particular encryption key will always need that key. So, if you change the key, you still need to keep a historical record for as long as a key has protected data.
Your hardware may offer some encryption capabilities. These features are manufacturer dependent. You will need to learn how it works before you can create a policy. If you prefer, you can simply use the software’s protection and forgo hardware-level encryption.
Shielding backup with physical and network protections
Leverage your infrastructure and network systems to build a layer of protection around your backup systems easily and efficiently. You will need to defend at layers one, two, and three.
Implement layer one (physical) protections
- Place backup hosts and devices in secure locations
- Create a chain-of-custody process for backup media
- If possible and cost effective, do not directly share switching hardware between backup systems and other systems
Implement layer two (Ethernet) protections
- Establish a VLAN just for your backup systems, or
- Create a chain-of-custody process for backup media
- Use dedicated physical switches for your backup systems and connect them to the rest of your production network through a router
Implement layer three (TCP/IP) protections
- If you isolate with a VLAN or dedicated router, create an IP subnet just for backup
- Set up a firewall at the edge of the backup network that blocks all externally initiated ingress traffic
- Configure the software firewall on backup hosts with a similar configuration to the previous firewall
All, or most of the previous isolation techniques should fit within even modest budgets. For greater protection, you have additional options.
- Install intrusion prevention and detection solutions
- Configure network monitoring
Data moving into your backup network will fit easily recognizable patterns. With even a rudimentary monitoring system, you should have no trouble spotting suspicious traffic.
Adding immutability
If you use tape technology, then you have two immutability choices: you can manually activate the write-protection mechanism on your tapes, or you can purchase tapes specially built as WORM media. Establish a policy for which tapes to protect. Some tapes use a sliding write-protect tab that allows an operator to enable or disable protection.
If your organization employs them, the policy must clearly state expectations. As you work through the Defining Backup Schedules chapter, you will encounter natural times to set aside unwritable tapes.
Newer software-based solutions require upfront configuration work. Services, like Hornetsecurity VM Backup V9, depend on your cloud provider’s immutable storage offerings. In most cases, these require little configuration effort.
First, you set up the cloud storage. Next, decide between a policy that restricts changes to select accounts or one that prevents all changes. If you allow any changes, separate the accounts with modification privileges from those involved in routine backup operations. Otherwise, you lose the primary reason for immutable storage.
Finally, select a retention policy. That policy dictates when data becomes writable. Work with your cloud provider to discover other capabilities. Remember that your provider will happily provide you with multiple storage objects so that you can use a variety of configurations simultaneously. Make certain that everyone involved in backup operations understands these configurations and their implications.
Fully isolating backup systems
Perform a complete risk analysis before you even consider an air-gapped approach. If you do not face significantly high exposure threats from malicious actors it may be overkill. Complete isolation looks simple, but it presents substantial long-term challenges for administrators.
Review the discussion above and consult with executives, key stakeholders, and others in your IT department with deployment or maintenance responsibilities. Due to full isolation, this approach only works for hypervisor-based backups. To create an air-gapped backup system:
- Designate an IP subnet for your air-gapped network;
- Decide on a workgroup or management domain configuration;
- If you will use a management domain, create and configure it before proceeding;
- Connect your hypervisor and backup hosts to a physical network that has no uplink;
- Ensure that the physical network links that you use for virtual machines does not provide any layer two or layer three connectivity to the hypervisor’s management operating system;
- Create a policy and an accountability process for acquiring and applying software updates.
The only practical risks to a properly air-gapped system are internal actors and breakout attacks against your hypervisors or container hosts. It still makes some sense to use anti-malware software as well as intrusion prevention and detection systems.

It cannot connect to the Internet in any way. If you cannot permanently guarantee absolute isolation, then you should instead follow the steps in the previous section to allow your backups to participate on the network with adequate protections.
To properly protect your virtualization environment and all the data, use Hornetsecurity VM Backup to securely back up and replicate your virtual machine.
For complete guidance, get our comprehensive Backup Bible, which serves as your indispensable resource containing invaluable information on backup and disaster recovery.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
Robust encryption, access controls, and authentication measures should be integrated into backup systems to thwart potential attackers. It is essential to implement secure offsite storage and adopting immutable backups can offer an added layer of protection against ransomware attacks.
FAQ
Historically, air gapping has been associated mainly with tape backups. However, modern cloud backup solutions offer a virtual equivalent of the air-gapped tape concept, enhancing security and resilience.
The 3-2-1 backup strategy holds immense value. It entails maintaining a minimum of three data copies – two on local devices stored on different media and one off-site, ensuring robust data protection.
The concept of air gap in storage revolves around a backup and recovery strategy. It ensures that critical data remains offline and disconnected from the internet, reinforcing security.
Air gapping serves as a robust defense against ransomware threats. By isolating secondary or tertiary backup copies from the public domain, it effectively enhances data security and reduces ransomware risks.

