

How to Boss Device Management with Endpoint Manager (aka Intune)
Changed forever by the global pandemic beginning in 2020, organizations have shifted to a very hybrid, disaggregated workforce. In addition, remote workers may now reside anywhere globally. As a result, managing endpoints is a big challenge facing organizations.
Microsoft’s Endpoint Manager, formerly Intune, is a modern, cloud-based solution that allows businesses to manage devices anywhere, no matter where they may be located and from any network, without traditional management constraints. So what is Microsoft Endpoint Manager? How is it used, and what capabilities does it provide modern enterprise organizations? That’s what we’re talking about here. Let’s get started.
Modern Challenges Facing Organizations Today
One of the challenges for organizations has been rethinking traditional IT tasks such as end-user support and endpoint management. No longer are all employees located directly on the corporate LAN to connect to conventional solutions for endpoint management. With the shift to cloud technologies for communication, collaboration, and business productivity, organizations must adopt cloud technologies to successfully manage endpoints from any network or location.
Traditional endpoint management and monitoring architecture require direct connectivity to the corporate LAN due to the network architecture needed for conventional monitoring and endpoint management solutions. As you can see below, traditional endpoint management and monitoring solutions were architected to exist on the same corporate network as the endpoints they managed or use VPN connections from remote clients for management.
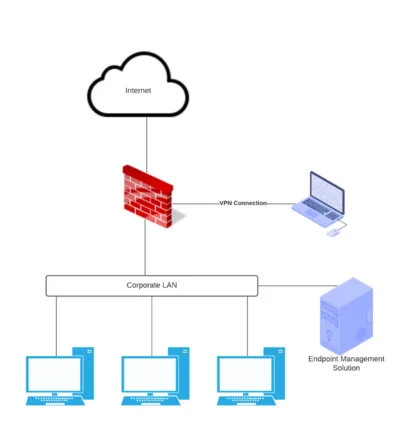
As we look at the architecture of corporate environments since the shift to a hybrid workforce, environments more closely resemble the following. As shown, the endpoints are no longer directly connected to the corporate LAN. These exist out on the Internet, relative to the enterprise datacenter.
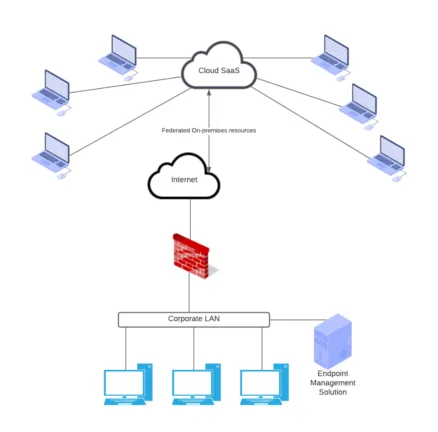
As you can see, traditional solutions no longer provide the robust tooling, flexibility, and connectivity diversity for managing endpoints that may exist in remote sites and home networks of remote employees.
What is Microsoft Endpoint Manager (aka Intune)?
Microsoft Intune is part of the overall Microsoft Endpoint Manager solution. What’s more, it’s cloud-based, meaning as long as an endpoint has connectivity to the Internet, the Intune solution can manage it. It provides several different components that allow organizations to carry out effective management, including:
- Cloud infrastructure
- Cloud-based mobile device management (MDM)
- Cloud-based mobile application management (MAM)
- Cloud-based PC management
Pinpointing in on the mobile device management (MDM) functionality, Microsoft’s Intune platform allows businesses to manage many types of devices. These include desktops, laptops, tablets, and phones. In addition, the devices can be corporate-owned or “bring your own device” (BYOD) devices.
Corporate-owned devices receive the complete set of MDM policies and controls, including controls over settings, features, and security. Administrators configure the settings and security policies needed to meet compliance and governance policies decided upon for their organization. Users enrol their devices in Intune and receive the policies as assigned, based on identity and other factors. Examples of the controls and security protocols that can be enforced include:
- Password
- PIN
- VPN connections
- Threat protection
When fully managed, administrators can also:
- Inventory devices accessing organization resources
- Block jailbroken devices
- Enforce security and health standards for enrolled devices
- Push and enrol certificates on devices
- Pull reports of user and device compliance
- Wipe the device if it is lost or stolen
When using BYOD to access corporate resources, Microsoft Intune allows organizations to protect the business data access from the BYOD device while not infringing on the personal data and activities carried out on the user device. This management capability allows organizations to use a multitude of different devices without the need to use corporate devices in every situation. BYOD may be required as well when contractors or other third parties are involved in projects that require interacting with sanctioned business data while at the same time using their own devices for other clients and activities.
With BYOD Intune policies, administrators can allow users to retain control of the devices while allowing Intune app protection policies that require multi-factor authentication (MFA) to access their business data housed in email or Microsoft Teams.
Endpoint Manager Licensing
Most licenses that include Microsoft Intune also grant the rights to use Microsoft Endpoint Configuration Manager as long as the subscription remains active. Intune is included in the following licenses:
- Microsoft 365 E5
- Microsoft 365 E3
- Enterprise Mobility + Security E5
- Enterprise Mobility + Security E3
- Microsoft 365 Business Premium
- Microsoft 365 F1
- Microsoft 365 F3
- Microsoft 365 Government G5
- Microsoft 365 Government G3
- Intune for Education
Intune for Education is included in the following licenses:
- Microsoft 365 Education A5
- Microsoft 365 Education A3
Which Operating Systems are Supported by Microsoft Endpoint Intune?
While Microsoft Endpoint Manager supports a wide range of devices and operating systems, it is good to understand the operating system requirements with the solution. Microsoft Endpoint Manager supports the following operating systems for management with MDM: Microsoft:
- Windows 11 (Home, S, Pro, Education, and Enterprise editions) – ***Note*** – There are a few known issues with Windows 11 at the moment and Microsoft Intune. Currently, multi-app kiosk mode isn’t supported, and there are limitations with customized start and taskbar experiences.
- Surface Hub
- Windows 10 (Home, S, Pro, Education, and Enterprise versions)
- Windows 10 and Windows 11 Cloud PCs on Windows 365
- Windows 10 Enterprise 2019 LTSC
- Windows 10 IoT Enterprise (x86, x64)
- Windows Holographic for Business
- Windows 10 Teams (Surface Hub)
- Windows 10 version 1709 (RS3) and later, Windows 8.1 RT, PCs running Windows 8.1 (Sustaining mode)
Apple
- Apple iOS 13.0 and later
- Apple iPadOS 13.0 and later
- macOS 10.15 and later
- Android 6.0 and later (including Samsung KNOX Standard 2.4 and higher)
- Android enterprise
You can read further details on specific operating system support for Microsoft Endpoint Manager here: Operating systems and browsers supported by Microsoft Intune | Microsoft Docs
Windows 10 Microsoft Intune enrollment walkthrough
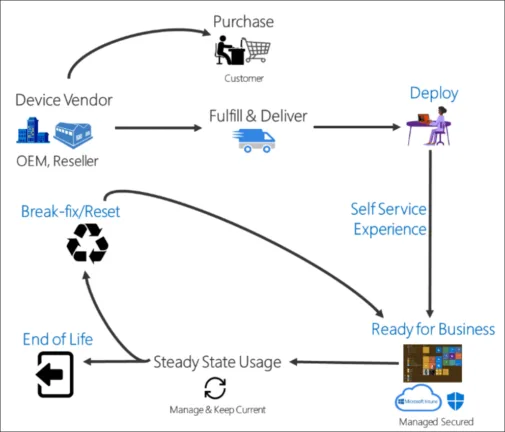
Let’s look at how to enrol Windows 10 in Microsoft Intune using the Company Portal app found in the Microsoft Store. For most Windows devices, organizations will use a combination of Autopilot and the Company Portal. With Windows Autopilot, device provisioning is simplified. It offers the ability to give new devices to end-users without building and maintaining custom operating system images that have traditionally been required.
Windows AutoPilot provisions the devices, and then Microsoft Intune manages policies, profiles, security settings, applications, and other tasks. Autopilot is a collection of technologies used to set up and pre-configure new devices and gets these ready for production use.
Autopilot can also be used to reset, repurpose, and recover devices, enabling IT to manage and provision end-user devices without any on-premises infrastructure. Once a machine is deployed with AutoPilot, devices can be managed with:
- Microsoft Intune
- Windows Update for Business
- Microsoft Endpoint Configuration Manager
- Other similar tools
It provides a workflow similar to the following:
What is the purpose of the Microsoft Intune Company Portal?
The Company Portal apps for Windows, IOS, and Android, allow users to access company data and do common tasks. These tasks include:
- Enrolling devices
- Installing apps
- Locating information
You can also customize the available self-service actions shown to the end-users in the Company Portal. Admins can prevent unintended device actions. You can configure these settings in the Administration > Customization section.
- Hide Remove button on corporate Windows devices
- Hide Reset button on corporate Windows devices
- Hide Remove button on corporate iOS/iPadOS devices
- Hide Reset button on corporate iOS/iPadOS devices
Users also have access to self-service device actions from the Company Portal application. Available self-service device actions include:
- Retire – Removes the device from Intune Management. In the company portal app and website, this shows as Remove.
- Wipe – This action initiates a device reset. On the company portal website, this is shown as Reset or Factory Reset in the iOS/iPadOS Company Portal App.
- Rename – This action changes the device name that the user can see in the Company Portal. It does not change the local device name, only the listing in the Company Portal.
- Sync – This action initiates a device check-in with the Intune service. This shows as Check Status in the Company Portal.
- Remote Lock – This locks the device, requiring a PIN to unlock it
- Reset Passcode – This action is used to reset the device passcode. On iOS/iPadOS devices, the passcode will be removed and the end-user will be required to enter a new code in settings. On supported Android devices, a new passcode is generated by Intune and temporarily displayed in the Company Portal.
- Key Recovery – This action is used to recover a personal recovery key for encrypted macOS devices from the Company Portal website.
Company Portal app configuration
In the Microsoft Store, you will want to download and install the Company Portal app.
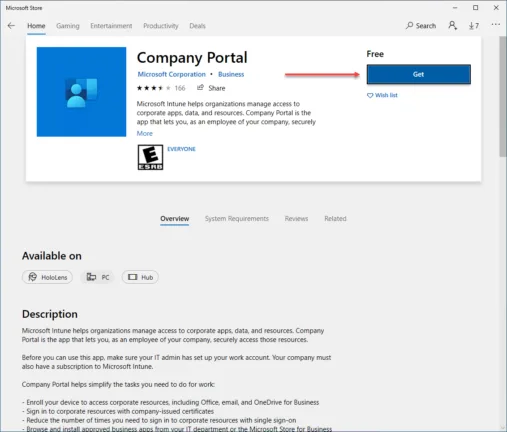
Once the Company Portal app is installed, log in with your Microsoft 365 credentials to enrol the device for management.
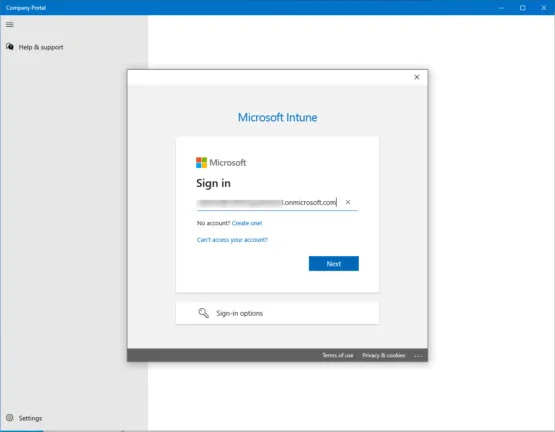
Select the checkbox to Allow my organization to manage my device.
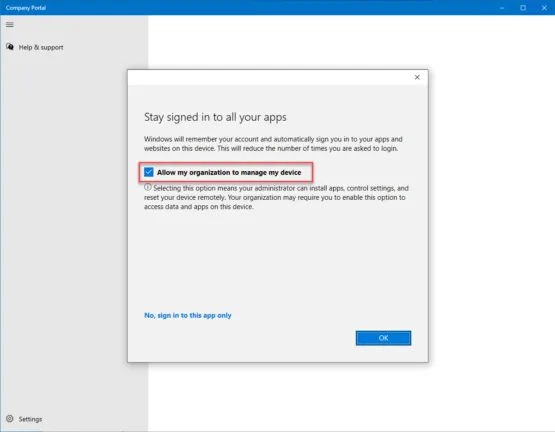
The login to the Microsoft 365 account is complete. Click Done.
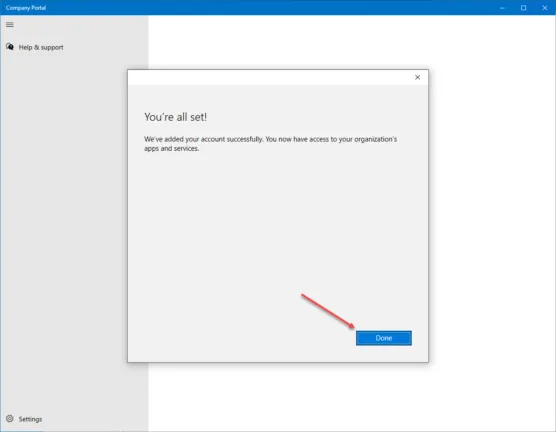
You will see a message that the device is not set up for corporate use. Click the message to begin the configuration of the device for corporate use.
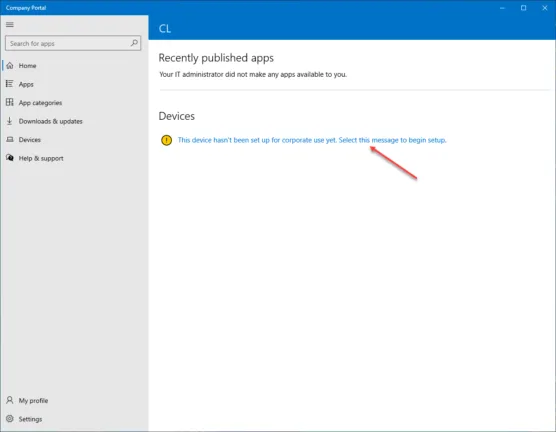
You will want to connect the device to work. Click Next.
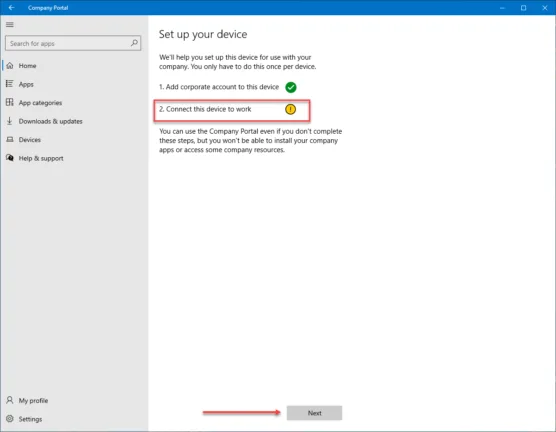
Beginning the process to connect this device to your work environment. Click the Connect button.
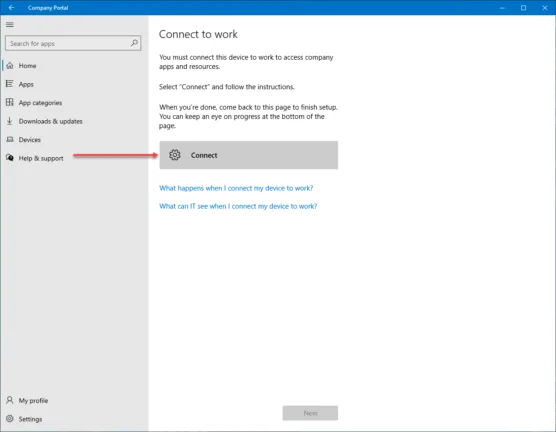
The login field will be prepopulated with the user you logged in with earlier.
After logging in, you will see the process for setting up the device begin.
After a few moments, the device will be connected to “work.”
The device is not set up for management and is ready to receive policies, applications, and other resources defined by the Intune administrator.
Grouping Users and Devices in Microsoft Endpoint Manager
With Microsoft Endpoint Manager, devices enrolled into Intune are added as objects inside Microsoft Azure Active Directory. Enrolled devices can be managed and grouped using Azure Active Directory constructs, including Azure Active Directory groups.
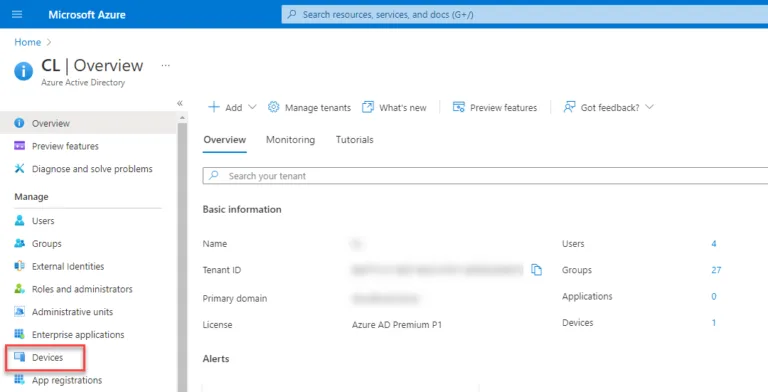
The “win10intune” machine enrolled above using the Company Portal app is displayed in the Devices blade for Azure Active Directory.
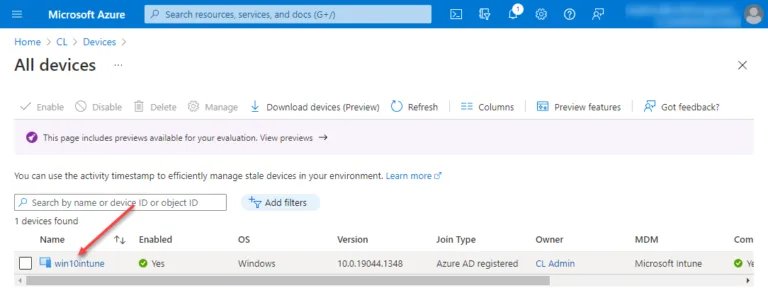
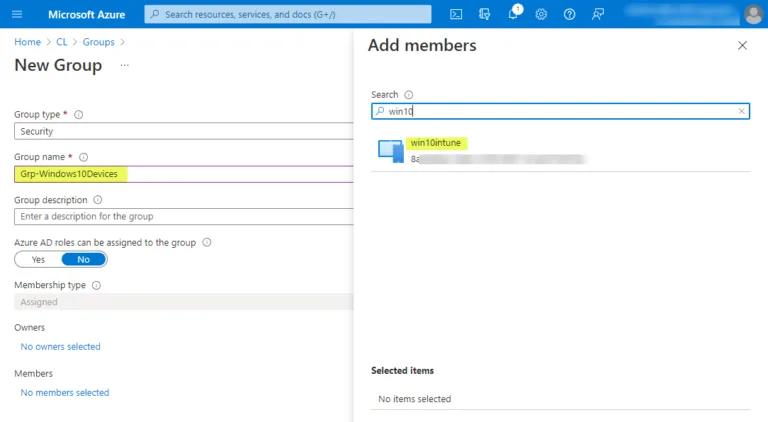
The device objects can be added to group objects. Below, I am creating a new group and adding members. The screen below shows a new group creation process with the member selector. As shown, you can easily add devices to groups. Dynamic device groups also can perform automatic group membership-based
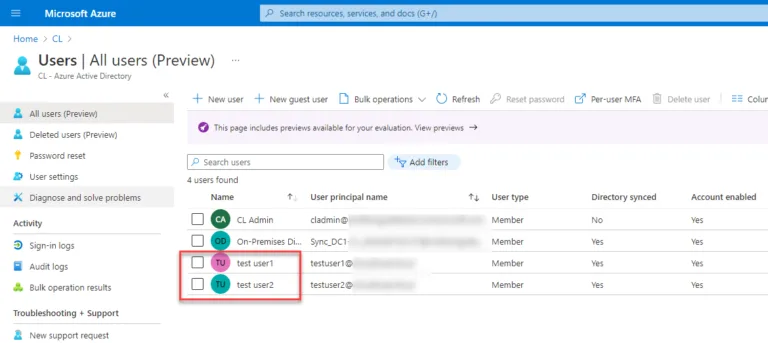
User objects are the same as well. Native Azure Active Directory users and also users that have been synchronized with on-premises directories using Azure AD Connect can also be added to Azure AD groups. Below, testuser1 and testuser2 are synchronized users with Azure AD Connect.
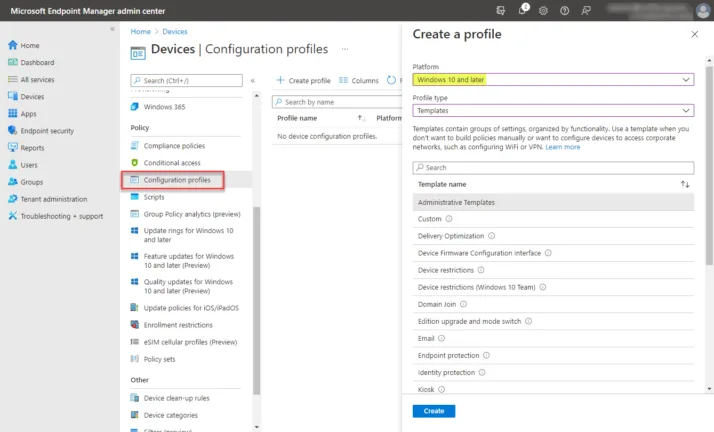
Creating Endpoint Manager Configuration Profiles
Now that we have a device enrolled into Microsoft Endpoint Manager and have a group object created containing the device we have enrolled, we can move forward with creating policies. The policies will then be assigned to the group housing the devices. Next, navigate to Devices Configuration profiles.
Configuration profiles allow configuring system settings, security configurations, and other settings. It is important to note if there is a conflict between configuration profiles and compliance policies, compliance policies take precedence over configuration profiles.
On the Devices > Configuration profiles screen, click to Create a profile to begin the process of creating a new configuration profile for Windows 10 devices. Under the platform, select Windows 10 and later. On the profile type, choose Templates. The templates option contains groups of settings organized by functionality. It makes it easy to have a “cookie-cutter” approach to predefined policies to keep from building these out manually.
It begins the Create Profile wizard. It will step you through the process of creating the configuration profile for the device. First, name the new configuration profile and click Next.
Next, you will have the opportunity to specify Configuration settings for your configuration profile. For those who have managed group policy, the configuration settings are eerily similar to what you would find with group policy settings templates.
You can define scope tags for your configuration profile.
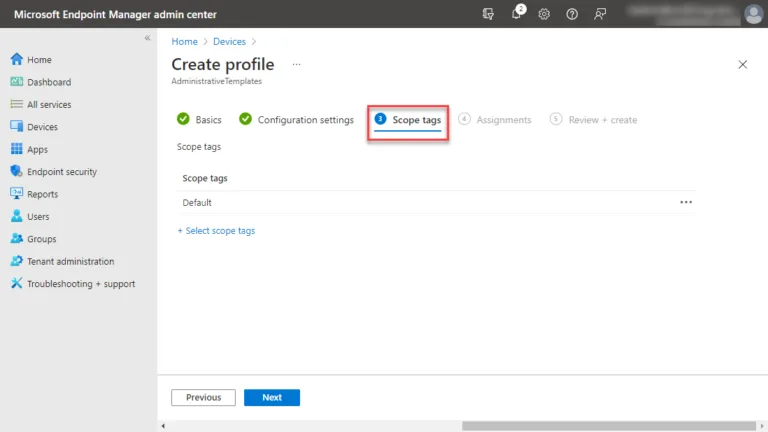
Next, on the Assignments screen, you assign the configuration profile to the specific group of devices you want to have received the configuration profile settings. Earlier, we created a group called Grp-Windows10Devices. This group will be the group targeted for the configuration profile.
Review and create the configuration profile.
Compliance policies
Compliance policies can be used in combination with conditional access to check to see if a device is compliant with certain policies or not. It is also a great way to report if certain settings are configured on end-user devices. An example would be to know which devices are encrypted using BitLocker.
When configuring a compliance policy, you will have the same wizardized experience to create and configure the policy.
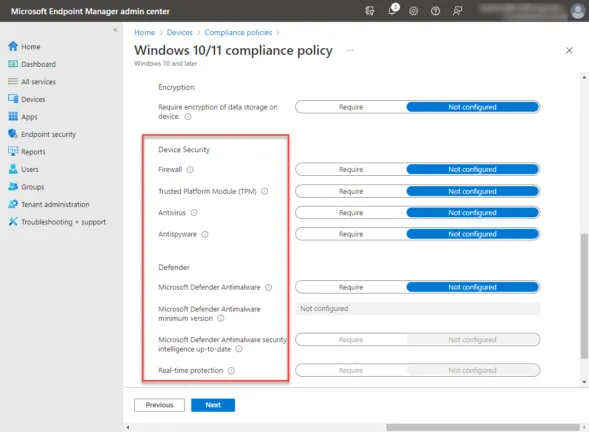
Scrolling down further reveals very useful compliance settings for controlling device security on the compliance settings screen. These include configuring:
- Firewall
- Trusted Platform Module (TPM)
- Antivirus
- Antispyware
- Defender
- Microsoft Defender Antimalware
- Microsoft Defender Antimalware minimum version
- Microsoft Defender Antimalware security intelligence up-to-date
- Real-time protection
Endpoint security with Endpoint Manager
Another really nice feature with Microsoft Intune is the Endpoint Security node. Admins can use the Endpoint Security Blade to configure device security specifically and manage security tasks for devices when those devices are at risk. Think of the Endpoint Security node as specialized configuration policies focused on security and mitigating risk. With Endpoint Security, you can:
- Review the security status of all managed devices – With the All Devices view, you can view device compliance from a high level. Also, you can view specific devices to understand which compliance policies aren’t met so you can resolve them.
- Deploy security baselines that establish best practice security configurations for devices – Intune includes security baselines for Windows devices and a wide range of applications, like Microsoft Defender for Endpoint and Microsoft Edge. These are pre-configured groups of Windows settings that help apply configurations recommended by the relevant security teams.
- Manage security configurations on devices through tightly focused policies – Each Endpoint security policy focuses on aspects of device security like antivirus, disk encryption, firewalls, and several areas made available through integration with Microsoft Defender for Endpoint.
- Establish device and user requirements through compliance policy – With compliance policies; you set the rules that devices and users must meet to be considered compliant. Rules can include OS versions, password requirements, device threat levels, and more.
- Gate access to corporate resources for both managed devices and unmanaged devices – When you integrate with Azure Active Directory (Azure AD) conditional access policies to enforce compliance policies, you can.
- Integrate Intune with your Microsoft Defender for Endpoint team – By integrating with Microsoft Defender for Endpoint you gain access to security tasks. These integrate Microsoft Defender for Endpoint and Intune together. This integration helps SecOps identify devices at risk and hand off detailed remediation steps to Intune admins.
What is the Difference Between Mobile Application Management and Mobile Device Management?
Microsoft Endpoint Manager allows organizations to protect business-critical data accessed by end-user devices using:
- Mobile Application Management (MAM)
- Mobile Device Management (MDM)
Mobile Application Management (MAM)
Mobile application management (MAM) is the component of Microsoft Endpoint Manager that allows controlling how all business-related data is accessed from end-user devices, such as Windows 10 & 11 PCs, and mobile devices like iPhones and Androids. In addition, MAM allows creating policies that help prevent data leakage and misuse of data to keep client devices aligned with compliance regulations and other governance initiatives. For example, you can prevent users from copying data between Office apps and personal applications. Finally, using MAM, organizations can also remove data from Office applications on personal devices used by end-user clients.
Mobile device management (MDM)
Using Microsoft Intune Mobile Device Management (MDM), businesses can configure policies that control various aspects of the configuration and security of end-user devices, such as Windows 10 & 11 PCs. For example, the control given by Endpoint Manager MDM allows complete control of the device and allows wiping data and resetting it to factory defaults if needed.
How Does Configuration Manager Work with Endpoint Manager?
Starting October 12, 2022, the endpoint management suite previously known as Microsoft Endpoint Manager will be known exclusively as Microsoft Intune. Henceforth, Microsoft Intune will denote cloud management, while on-premises management will be referred to as Microsoft Configuration Manager. It includes:
- Config Manager
- Intune
- Co-management
- Desktop Analytics
- Device Manage Admin console
Since all of the solutions above are now part of the Microsoft Intune solution, any Configuration Manager customer can now automatically use Intune to co-manage Windows devices with no license changes or additional costs. While they have changed the branding, the changes will help customers use the full capabilities of Endpoint Manager without traditional challenges.
Microsoft has purposely engineered the components of their Microsoft Intune solutions to work together seamlessly. Current Config Manager tasks and data are presented in the unified console of Endpoint Manager Devices. How should the different solutions be used together?
Customers have asked questions about which solution is the ultimate destination they should reach in their device management solution between Configuration Manager, Intune, and co-management. Is co-management a bridge or destination? Microsoft desires co-management to be the destination for customers.
Microsoft ideally wants customers to attach their Intune environment with their existing Configuration Manager deployments. Therefore, co-management allows attaching Microsoft 365 cloud intelligence to existing configuration solutions.
With the unified solution, customers can completely automate compatibility testing when upgrading to a new release of Windows. In addition, customers can test and deploy update patching much faster to bolster compliance much more quickly. Immediate actions can be taken on all devices using the Microsoft Intune solution.
Configuration Manager continues to function the same way it has functioned for customers. When referring to the on-premises component, Microsoft is calling the traditional Config Manager product Microsoft Intune Configuration Manager. If you are licensed for Microsoft Config Manager, you are automatically licensed to use Microsoft Intune to co-management your end-user devices.
What are the Native Google Options Available for Managing Android Devices?
While Microsoft Intune can manage Google devices and Microsoft endpoints, Google has its own native endpoint management solution called Google Endpoint Management. The solution provides both basic and advanced mobile security and app management as well as device management that can do the following:
- Set password requirements for mobile devices: Allows administrators to establish and enforce specific password policies for mobile devices, enhancing security by mandating strong authentication methods.
- Wipe a user’s account from a device: Provides the ability to remotely erase a user’s account and associated data from a device, useful in cases of loss or theft.
- Manage apps for Android devices: Enables control over the installation, update, and removal of applications on Android devices to ensure compliance and security.
- Require admin approval for mobile devices: Implements a system where mobile devices must receive approval from an administrator before being used within the organization, ensuring device security and compliance.
- Recommend and manage IOS apps: Allows the management and recommendation of iOS applications, ensuring that only approved and secure apps are used on Apple devices.
- Standard and strong passcode enforcement: Enforces the use of either standard or more complex passcodes, enhancing the security of devices by preventing unauthorized access.
- Network management: Provides tools for overseeing and controlling how devices connect to and interact with network resources, ensuring secure and efficient use of network infrastructure.
- Android work profiles: Supports the creation of separate work profiles on Android devices, which help in segregating work and personal data for security and privacy.
- Approve devices: Facilitates a process for formally approving devices before they can access corporate resources, ensuring they meet security standards.
- Device audit log: Maintains a detailed log of activities and changes on devices, providing insights into usage patterns and potential security incidents.
- Report inactive company-owned devices: Offers the capability to identify and report devices that are not actively being used, helping to manage resources and security risks effectively.
- Private Android web apps: Allows for the management and deployment of private, custom web applications specifically for Android devices, offering tailored solutions for business needs.
- Computer security – Manages all company-owned devices, including mobile devices, laptops, and desktops, from your Google Workspace Admin console
Google Endpoint Management can manage macOS devices, whereas Intune is not compatible with macOS. One thing to note with Google Endpoint Management is it is not available for Business Plus or G Suite Business customers. It is only found in the Enterprise offering. Intune provides more robust features, as expected, for managing Windows devices and health compliance features that are not listed with Google Endpoint Management.
What are the Native Apple Options Available for Managing iOS and ipadOS Devices?
Apple has something called the Apple Platform Deployment. It is a native solution provided by Apple to deploy and manage Apple hardware, software, and services in your organization. With Apple Platform Deployment, businesses can:
- Lock and locate devices: Enables administrators to remotely lock Apple devices and pinpoint their location, useful for security and in cases of loss or theft.
- Wipe devices remotely: Allows for the remote erasure of all data on a device, ensuring sensitive information is protected if a device is lost or compromised.
- Activation lock: Prevents unauthorized use of a device by locking it and requiring Apple ID authentication for reactivation, enhancing device security.
- Enforce device policies: Empowers businesses to apply and enforce specific configuration and security policies across Apple devices within the organization.
- Use persistent tokens: Utilizes tokens that remain valid until revoked, facilitating continuous and secure access to services without the need for frequent re-authentication.
- Use built-in network security features: Leverages the inherent network security capabilities of Apple devices to protect data and communications.
- Manage certificates: Provides tools for managing digital certificates, enabling secure authentication and encrypted communication for devices.
- Perform user enrollment MDM information: Simplifies the process of enrolling users and their devices in Mobile Device Management (MDM) systems for efficient administration.
- Put restrictions in place for iPhone, iPad, Mac, Apple TV, and other supervised devices: Allows for the imposition of various restrictions on Apple devices to control and secure their usage in line with organizational policies.
Like much of the Apple ecosystem, Apple Platform Deployment only caters to Apple devices. As a result, it isn’t an MDM and MAM solution that organizations can use for multiple platforms and devices. Instead, it is specific to the Apple ecosystem. Here, Intune is a superior all-inclusive tool that can manage most devices used in the enterprise. Apple’s Platform Deployment is the better choice for the most robust features and capabilities for managing Apple hardware, software, applications, and services.
My Thoughts on Endpoint Manager
The modern distributed hybrid workforce has presented challenges for organizations with remote employees on different continents worldwide. Legacy solutions that depend on endpoints directly connected to corporate networks are cumbersome and don’t scale well.
Cloud-based mobile device management and mobile application management platforms answer many of the challenges organizations face today. Microsoft Intune is a robust platform for managing and controlling end-user devices, applications, and data.
Using Intune configuration profiles, compliance policies, and endpoint security, businesses have cloud-based tools that effectively manage corporate-owned devices and BYOD. Additionally, as the modern workforce is more disaggregated and remote than ever before, cloud-centric solutions provide the flexibility and toolsets needed for modern device management.

