

WannaCry: No harm for Hornetsecurity customers
Hornetsecurity ATP deflects global ransomware attack from the first malicious email
WannaCry has caused severe damage in more than 150 countries: The woldwide attacks, in which for example the British National Health Service, the car manufacturer Renault and some systems of Germany’s railway company Deutsche Bahn have fallen victim, took advantage of several weaknesses at once. However, Hornetsecurity Advanced Threat Protection was able to detect and prevent the dangerous ransomware attack from the first email onward.
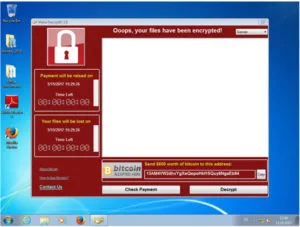
WannaCry is a ransom software that is distributed via email. Activated on a local device, the malware starts encrypting the stored data. After that, the user is being asked to pay a certain ransom in order to receive the decryption key, a procedure which security experts advise not to do. WannaCry uses an exploit, that initially has been developed by the NSA and made public by a hacker group called “Shadow Brokers”.
The success of WannaCry comes from the fact that it uses a weakness in Microsoft’s „Server Message Block (SMB) Protocol“. Through this, it spreads quickly and infects other systems, which lead to the high worldwide distribution rate. WannaCry is exploiting the old Windows XP operating system, as this is still in use but Microsoft stopped providing security updates for. With the emergence of WannaCry, the company quickly changed that and distributed a patch.
Hornetsecurity Advanced Threat Protection (ATP) detected the zero-day ransomware from its first appearance by using a dynamic pattern analysis in its sandbox and put the malware into quarantine. Additional analyses revealed that WannaCry installs a DOUBLEPULSAR Backdoor variant which then plants malicious code onto the local device. After that, the program encrypts various files and adds the file ending .wncry to them, for example finance.xlsx into finance.xlsx.wncry. This renders the files useless. At the same time the infected hosts become part of a botnet, which is being commanded by a TOR network.
Hornetsecurity recommends the following procedures to protect yourself from an infection. Companies and private users still using Windows XP should immediately use the patch provided by Microsoft and update their system. Even more effective is the installation of a more recent operating system with active security updates (at least MS17-010). Also, companies should adapt their firewalls so that incoming SMB traffic on port 445 as well as outgoing TOR traffic will be blocked. Additionally, the security specialists from Hornetsecurity recommend to thoroughly check emails containing invoices or other attachments (office, script or executable files) and to scan them using a virus check. With the URL rewriting and URL scanning engines Hornetsecurity ATP offers a service for in-depth URL analysis in emails – for an all-around protection from new dangers.
